Kill chain (military): Difference between revisions
No edit summary |
|||
| Line 34: | Line 34: | ||
[[File:Intrusion Kill Chain - v2.png|thumb|right|350px|Intrusion kill chain for information security<ref name=Senate>[http://www.public.navy.mil/spawar/Press/Documents/Publications/03.26.15_USSenate.pdf U.S. Senate-Committee on Commerce, Science, and Transportation-A "Kill Chain" Analysis of the 2013 Target Data Breach-March 26, 2014] {{webarchive|url=https://web.archive.org/web/20161006082550/http://www.public.navy.mil/spawar/Press/Documents/Publications/03.26.15_USSenate.pdf |date=October 6, 2016 }}</ref>]] |
[[File:Intrusion Kill Chain - v2.png|thumb|right|350px|Intrusion kill chain for information security<ref name=Senate>[http://www.public.navy.mil/spawar/Press/Documents/Publications/03.26.15_USSenate.pdf U.S. Senate-Committee on Commerce, Science, and Transportation-A "Kill Chain" Analysis of the 2013 Target Data Breach-March 26, 2014] {{webarchive|url=https://web.archive.org/web/20161006082550/http://www.public.navy.mil/spawar/Press/Documents/Publications/03.26.15_USSenate.pdf |date=October 6, 2016 }}</ref>]] |
||
Computer scientists at Lockheed-Martin corporation described a new "intrusion kill chain" framework or model to defend computer networks in 2011.<ref name=Lockheed/> They wrote that attacks may occur in |
Computer scientists at Lockheed-Martin corporation described a new "intrusion kill chain" framework or model to defend computer networks in 2011.<ref name=Lockheed/> They wrote that attacks may occur in phases and can be disrupted through controls established at each phase. Since then, the "cyber kill chain™" has been adopted by data security organizations to define phases of cyber-attacks.<ref>{{Cite web|url=http://www.networkworld.com/article/3104542/security/why-the-cyber-kill-chain-needs-an-upgradesecurity-pros-need-to-focus-more-on-catching-attackers-aft.html|title=Why the ‘cyber kill chain’ needs an upgrade|last=Greene|first=Tim|access-date=2016-08-19}}</ref> |
||
A cyber kill chain reveals the |
A cyber kill chain reveals the phases of a cyber attack: from early reconnaissance to the goal of data exfiltration.<ref>{{Cite web|url=https://blog.varonis.com/the-cyber-kill-chain-or-how-i-learned-to-stop-worrying-and-love-data-breaches/|title=The Cyber Kill Chain or: how I learned to stop worrying and love data breaches|date=2016-06-20|language=en-US|access-date=2016-08-19}}</ref> The kill chain can also be used as a management tool to help continuously improve network defense. According to Lockheed Martin, threats must progress through several phases in the model, including: |
||
# Reconnaissance: Intruder selects target, researches it, and attempts to identify vulnerabilities in the target network. |
# Reconnaissance: Intruder selects target, researches it, and attempts to identify vulnerabilities in the target network. |
||
| Line 46: | Line 46: | ||
# Actions on Objective: Intruder takes action to achieve their goals, such as data exfiltration, data destruction, or encryption for ransom. |
# Actions on Objective: Intruder takes action to achieve their goals, such as data exfiltration, data destruction, or encryption for ransom. |
||
Defensive courses of action can be taken against these phases:<ref>http://gauss.ececs.uc.edu/Courses/c6055/pdf/attackpatterns.pdf</ref> |
|||
*Detect: determine whether an attacker is poking around |
*Detect: determine whether an attacker is poking around |
||
*Deny: prevent information disclosure and unauthorized access |
*Deny: prevent information disclosure and unauthorized access |
||
Revision as of 12:05, 15 October 2018
It has been suggested that this article should be split into a new article titled Kill chain (computer security). (discuss) (March 2017) |
The term kill chain was originally used as a military concept related to the structure of an attack; consisting of target identification, force dispatch to target, decision and order to attack the target, and finally the destruction of the target.[1] Conversely, the idea of "breaking" an opponent's kill chain is a method of defense or preemptive action.[2] More recently, Lockheed Martin adapted this concept to information security, using it as a method for modeling intrusions on a computer network.[3] This model has seen some adoption in the information security community.[4] However, acceptance is not universal, with critics pointing to what they believe are fundamental flaws in the model.[5]
The military kill chain
F2T2EA
One military kill chain model is the "F2T2EA", which includes the following phases:
- Find: Locate the target.
- Fix: Fix their location; or make it difficult for them to move.
- Track: Monitor their movement.
- Target: Select an appropriate weapon or asset to use on the target to create desired effects.
- Engage: Apply the weapon to the target.
- Assess: Evaluate effects of the attack, including any intelligence gathered at the location.
This is an integrated, end-to-end process described as a "chain" because an interruption at any stage can interrupt the entire process.[6]
North Korean nuclear capability
A new American military contingency plan called "Kill Chain" is reportedly the first step in a new strategy to use satellite imagery to identify North Korean launch sites, nuclear facilities and manufacturing capability and destroy them pre-emptively if a conflict seems imminent. The plan was mentioned in a joint statement by the United States and South Korea.[7][8]
Previous terminology
The "Four Fs" is a military term used in the United States military, especially during World War II.
Designed to be easy to remember, the "Four Fs" are as follows:
- Find the enemy – Locate the enemy
- Fix the enemy – Pin them down with suppressing fire
- Fight the enemy – Engage the enemy in combat or flank the enemy – Send soldiers to the enemy's sides or rear
- Finish the enemy – Eliminate all enemy combatants
The cyber kill chain
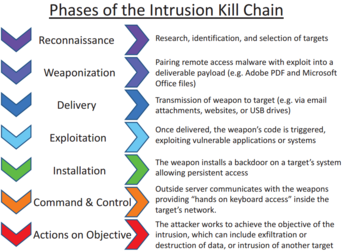
Computer scientists at Lockheed-Martin corporation described a new "intrusion kill chain" framework or model to defend computer networks in 2011.[6] They wrote that attacks may occur in phases and can be disrupted through controls established at each phase. Since then, the "cyber kill chain™" has been adopted by data security organizations to define phases of cyber-attacks.[10]
A cyber kill chain reveals the phases of a cyber attack: from early reconnaissance to the goal of data exfiltration.[11] The kill chain can also be used as a management tool to help continuously improve network defense. According to Lockheed Martin, threats must progress through several phases in the model, including:
- Reconnaissance: Intruder selects target, researches it, and attempts to identify vulnerabilities in the target network.
- Weaponization: Intruder creates remote access malware weapon, such as a virus or worm, tailored to one or more vulnerabilities.
- Delivery: Intruder transmits weapon to target (e.g., via e-mail attachments, websites or USB drives)
- Exploitation: Malware weapon's program code triggers, which takes action on target network to exploit vulnerability.
- Installation: Malware weapon installs access point (e.g., "backdoor") usable by intruder.
- Command and Control: Malware enables intruder to have "hands on the keyboard" persistent access to target network.
- Actions on Objective: Intruder takes action to achieve their goals, such as data exfiltration, data destruction, or encryption for ransom.
Defensive courses of action can be taken against these phases:[12]
- Detect: determine whether an attacker is poking around
- Deny: prevent information disclosure and unauthorized access
- Disrupt: stop or change outbound traffic (to attacker)
- Degrade: counter-attack command and control
- Deceive: interfere with command and control
- Contain: network segmentation changes
A U.S. Senate investigation of the 2013 Target Corporation data breach included analysis based on the Lockheed-Martin kill chain framework. It identified several stages where controls did not prevent or detect progression of the attack.[9]
Critiques of the traditional cyber kill chain
Among the critiques of Lockheed Martin's cyber kill chain model as threat assessment and prevention tool is that the first phases happen outside the defended network, making it difficult to identify or defend against actions at these stages. [13] Similarly, this methodology is said to reinforce traditional perimeter-based and malware-prevention based defensive strategies. [14] Others have noted that the traditional cyber kill chain isn't suitable to model the insider threat. [15] This is particularly troublesome given the inevitability of successful attacks that breach the internal network perimeter, which is why organizations "need to develop a strategy for dealing with attackers inside the firewall. They need to think of every attacker as [a] potential insider”. [16]
Unification of the cyber kill chain
A unified version of the kill chain was developed to overcome common critiques against the traditional cyber kill chain, by uniting and extending Lockheed Martin’s Kill Chain and MITRE’s ATT&CK framework. The Unified Kill Chain is an ordered arrangement of 18 unique attack phases that may occur in end-to-end cyber attacks, which covers activities that occur outside and within the defended network. As such, the Unified Kill Chain offers a significant improvement over the scope limitations of the traditional kill chain and the time-agnostic nature of tactics in MITRE’s ATT&CK. The unified model can be used to analyze, compare and defend against end-to-end cyber attacks by Advanced Persistent Threats (APTs). [17]
References
- ^ "Kill Chain Approach". Chief of Naval Operations. April 23, 2013. Archived from the original on June 13, 2013.
{{cite web}}: Unknown parameter|deadurl=ignored (|url-status=suggested) (help) - ^ Jonathan Greenert; Mark Welsh (May 17, 2013). "Breaking the Kill Chain". Foreign Policy. Retrieved June 30, 2016.
- ^ Higgins, Kelly Jackson (January 12, 2013). "How Lockheed Martin's 'Kill Chain' Stopped SecurID Attack". DARKReading. Retrieved June 30, 2016.
- ^ Mason, Sean (December 2, 2014). "Leveraging The Kill Chain For Awesome". DARKReading. Retrieved June 30, 2016.
- ^ Myers, Lysa (October 4, 2013). "The practicality of the Cyber Kill Chain approach to security". CSO Online. Retrieved June 30, 2016.
- ^ a b Lockheed-Martin Corporation-Hutchins, Cloppert, and Amin-Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains-2011
- ^ Sanger, David E. (July 6, 2017). "Tiny Satellites From Silicon Valley May Help Track North Korea Missiles". The New York Times. Retrieved July 7, 2017.
- ^ "06/30/17 - Joint Statement between the United States and the Republic of Korea | U.S. Embassy & Consulate in Korea". U.S. Embassy & Consulate in Korea. 2017-06-30. Retrieved 2017-07-07.
- ^ a b U.S. Senate-Committee on Commerce, Science, and Transportation-A "Kill Chain" Analysis of the 2013 Target Data Breach-March 26, 2014 Archived October 6, 2016, at the Wayback Machine
- ^ Greene, Tim. "Why the 'cyber kill chain' needs an upgrade". Retrieved 2016-08-19.
- ^ "The Cyber Kill Chain or: how I learned to stop worrying and love data breaches". 2016-06-20. Retrieved 2016-08-19.
- ^ http://gauss.ececs.uc.edu/Courses/c6055/pdf/attackpatterns.pdf
- ^ Laliberte, Marc (September 21, 2016). "A Twist On The Cyber Kill Chain: Defending Against A JavaScript Malware Attack". DARKReading.
- ^ Engel, Giora (November 18, 2014). "Deconstructing The Cyber Kill Chain". DARKReading. Retrieved June 30, 2016.
- ^ Reidy, Patrick. "Combating the Insider Threat at the FBI" (PDF). BlackHat USA 2013.
- ^ Devost, Matt (February 19, 2015). "Every Cyber Attacker is an Insider". OODA Loop.
- ^ Pols, Paul (December 7, 2017). "The Unified Kill Chain" (PDF). Cyber Security Academy.
{{cite web}}: Cite has empty unknown parameter:|1=(help)
External links
- "Lockheed Martin Cyber Kill Chain".
- "The Unified Kill Chain". Cyber Security Academy.
