Search results
Appearance
- In computing and telecommunication, a control character or non-printing character (NPC) is a code point in a character set that does not represent a written...25 KB (3,469 words) - 22:12, 6 May 2024
- In computing, data recovery is a process of retrieving deleted, inaccessible, lost, corrupted, damaged, or formatted data from secondary storage, removable...29 KB (3,493 words) - 16:34, 12 May 2024
- In formal language theory, a context-free grammar (CFG) is a formal grammar whose production rules can be applied to a nonterminal symbol regardless of...46 KB (6,169 words) - 17:19, 5 June 2024
- Apache Lucene is a free and open-source search engine software library, originally written in Java by Doug Cutting. It is supported by the Apache Software...15 KB (1,262 words) - 13:54, 27 June 2024
- A dialer (American English) or dialler (British English) is an electronic device that is connected to a telephone line to monitor the dialed numbers and...7 KB (1,018 words) - 00:52, 12 May 2024
- In computer networking, IP address spoofing or IP spoofing is the creation of Internet Protocol (IP) packets with a false source IP address, for the purpose...9 KB (1,141 words) - 22:41, 29 April 2024
- Aldus Corporation was an American software company best known for its pioneering desktop publishing software. PageMaker, the company's most well-known...10 KB (865 words) - 20:48, 11 February 2024
- Free and open-source software portal Apache Pivot is an open-source platform for building rich web applications in Java or any JVM-compatible language...4 KB (443 words) - 02:09, 28 May 2024
- C++ Accelerated Massive Parallelism (C++ AMP) is a native programming model that contains elements that span the C++ programming language and its runtime...6 KB (617 words) - 02:16, 20 May 2022
- Albino Blacksheep (ABS) is an animation website made by Steven Lerner in Toronto, Ontario on January 4, 1999. It publishes member submitted digital media...3 KB (302 words) - 19:21, 17 June 2024
- The Mac OS nanokernel is an operating system kernel that serves as the basis of most PowerPC based system software versions 7 through 9 of the classic...5 KB (511 words) - 17:54, 29 May 2024
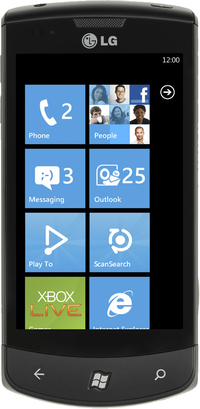
- The LG Optimus 7 (also known as the LG-E900) is a slate smartphone which runs Microsoft's Windows Phone operating system. The Optimus 7 is part of the...4 KB (235 words) - 09:04, 16 February 2023
- Visual Basic .NET was released by Microsoft in 2002 as a successor to the original Visual Basic computer programming language. It was implemented on the...9 KB (1,045 words) - 03:38, 23 November 2023
- Computer-assisted telephone interviewing (CATI) is a telephone surveying technique in which the interviewer follows a script provided by a software application...3 KB (364 words) - 06:40, 16 July 2021
- Sodipodi is a free and open-source vector graphics editor, superseded since 2003 by Inkscape, an independent Sodipodi fork. Sodipodi started as a fork...7 KB (572 words) - 14:10, 3 June 2024
- In algebra, the zero object of a given algebraic structure is, in the sense explained below, the simplest object of such structure. As a set it is a singleton...8 KB (939 words) - 11:50, 18 February 2023
- Ruby Version Manager, often abbreviated as RVM, is a software platform for Unix-like operating systems designed to manage multiple installations of Ruby...3 KB (241 words) - 06:15, 23 April 2024
- Planning poker, also called Scrum poker, is a consensus-based, gamified technique for estimating, mostly used for timeboxing in Agile principles. In planning...7 KB (955 words) - 13:07, 12 June 2024
- DNS rebinding is a method of manipulating resolution of domain names that is commonly used as a form of computer attack. In this attack, a malicious web...6 KB (698 words) - 11:34, 2 September 2023
- Business requirements, also known as stakeholder requirements specifications (StRS), describe the characteristics of a proposed system from the viewpoint...16 KB (1,893 words) - 13:21, 5 July 2023