Fork bomb
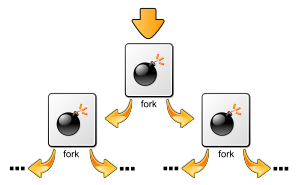
In computing, a fork bomb is a denial-of-service attack whereby a process continually replicates itself to deplete available system resources.
Implementation
Fork bombs operate both by consuming CPU time in the process of forking, and by saturating the operating system's process table.[1][2] A basic implementation of a fork bomb takes the following form:
set running to true
while running is true
create copy of running process
end
In Unix-like operating systems, fork bombs are generally written to use the fork system call.[2] As forked processes are also copies of the first program, once they resume execution from the next address at the frame pointer, they also seek to create a copy of themselves; this has the effect of causing an exponential growth in processes. As modern Unix systems generally use copy-on-write when forking new processes,[3] a fork bomb generally will not saturate such a system's memory.
Microsoft Windows operating systems do not have equivalent functionality to the Unix fork system call;[4] a fork bomb on such an operating system must therefore create a new process instead of forking from an existing one.
Prevention
As a fork bomb's mode of operation is entirely encapsulated by creating new processes, one way of preventing a fork bomb from severely affecting the entire system is to limit the maximum amount of processes that a single user may own. On Linux, this can be achieved by using the ulimit utility; for example, the command ulimit -Hu 30 would limit the affected user to a maximum of thirty owned processes.[5] On PAM-enabled systems, this limit can also be set in /etc/security/limits.conf,[6] and on FreeBSD, the system administrator can put limits in /etc/login.conf.[7]
See also
References
- ^ Ye, Nong (2008). Secure Computer and Network Systems: Modeling, Analysis and Design. p. 16. ISBN 0470023244.
- ^ a b Jielin, Dong (2007). Network Dictionary. p. 200. ISBN 1602670005.
- ^ Dhamdhere, D. M. (2006). Operating Systems: A Concept-based Approach. p. 285. ISBN 0070611947.
- ^ Hammond, Mark (2000). Python Programming On Win32: Help for Windows Programmers. p. 35. ISBN 1565926218.
- ^ Cooper, Mendel (2005). Advanced Bash Scripting Guide. pp. 305–306. ISBN 1430319305.
- ^ Soyinka, Wale (2012). Linux Administration: A Beginners Guide. pp. 364–365. ISBN 0071767592.
- ^ Lucas, Michael W. (2007). Absolute FreeBSD: The Complete Guide to FreeBSD. pp. 198–199. ISBN 1593271514.
