Alpha algorithm
The α-algorithm or α-miner is an algorithm used in process mining, aimed at reconstructing causality from a set of sequences of events. It was first put forward by van der Aalst, Weijters and Măruşter.[1] The goal of Alpha miner is to convert the event log into a workflow-net based on the relations between various activities in the event log. An event log is a multi-set of traces, and a trace is a sequence of activity names. Several extensions or modifications of it have since been presented, which will be listed below.
Alpha miner was the first process discovery algorithm ever proposed, and it gives a good overview of the aim of process discovery and how various activities within the process are executed. Alpha miner was also the basis for the development of many other process mining techniques such as heuristic miner, genetic mining was developed based on the idea alpha miner is built on.[2]
Short description
The algorithm takes a workflow log as input and results in a workflow net being constructed.
It does so by examining causal relationships observed between tasks. For example, one specific task might always precede another specific task in every execution trace, which would be useful information.
Definitions used
- A workflow trace or execution trace is a string over an alphabet of tasks.
- A workflow log is a set of workflow traces.
Event log
Event log is the primary requirement for applying any process discovery algorithm. An event log consists of a unique identifier for a case, activity name describing the action occurring in the process and timestamp. An event log can be represented as a multi-set of activities. For the sake of simplicity the following example would use alphabetic letter to represent an activity. Consider an example event log shown in the following figure:
| Case id | Activity | Timestamp |
|---|---|---|
| 1 | A | 2019/10/09 14:50:17.000 |
| 1 | B | 2019/10/09 15:50:17.000 |
| 1 | C | 2019/10/09 15:56:17.000 |
| 1 | D | 2019/10/10 13:50:17.000 |
| 2 | A | 2019/10/10 14:30:17.000 |
| 2 | C | 2019/10/10 14:50:14.000 |
| 2 | B | 2019/10/11 09:50:17.000 |
| 2 | D | 2019/10/11 10:50:17.000 |
| 3 | A | 2019/10/11 12:50:17.000 |
| 3 | E | 2019/10/21 14:50:17.000 |
| 3 | D | 2019/10/21 15:50:17.000 |
An event log is a multi set of traces, and a trace is a sequence of activities. Thus, an event log such as above can be represented using the following notation:
Every event log can be boiled down into a multi-set of traces, and such traces can be further used to break down relationships between various activities in the process. According to the rules of alpha miner, activities belonging to various cases can have 4 types of relationships between them:[2]
- Direct Succession: x > y if and only if some relation x is directly following by y. In our example, we can consider that A > B, A > E, A > C.
- Causality: x → y iff x > y and not y > x. In our example, we can consider that A → E.
- Parallel: x || y iff x > y and y > x. In our example, we have B || C.
- Choice: x # y iff not(x > y) and not(y > x). In our example, we have A # D.
Patterns
 Sequence Pattern: A → B
Sequence Pattern: A → B  XOR-split Pattern: A → B, A → C, and B # C
XOR-split Pattern: A → B, A → C, and B # C
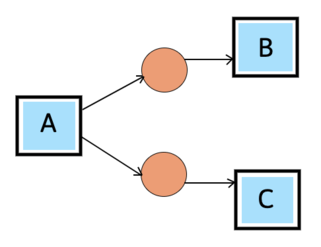 AND-split Pattern: A → B, A → C, and B || C
AND-split Pattern: A → B, A → C, and B || C
Description
The alpha miner starts with converting an event log into directly-follows, sequence, parallel, and choice relations, and using them to create a petri net describing the process model. Initially the algorithm constructs a footprint matrix. Using the footprint matrix and the above shown pattern, one can construct a process model. Based on the four relations described earlier a footprint based matrix is first discovered. Using the footprint based matrix places are discovered. Each place is identified with a pair of sets of tasks, in order to keep the number of places low.
| a | b | c | d | e | |
|---|---|---|---|---|---|
| a | # | → | → | # | → |
| b | ← | # | || | → | # |
| c | ← | || | # | → | # |
| d | # | ← | ← | # | ← |
| e | ← | # | # | → | # |
- is the set of all pairs of maximal sets of tasks such that
- Neither and contain any members of > and
- is a subset of →
- contains one place for every member of , plus the input place and the output place
The flow relation is the union of the following:
The result is
- a Petri net structure
- with one input place and one output place
- because every transition of is on a -path from to , it is indeed a workflow net.
For the example given above, the following petri net would be resultant of the application of alpha miner.
Properties
It can be shown [3] that in the case of a complete workflow log generated by a sound SWF net, the net generating it can be reconstructed. Complete means that its relation is maximal. It is not required that all possible traces be present (which would be countably infinite for a net with a loop).
Limitations
- Implicit places: Alpha miner cannot distinguish between implicit and required places and thus might result in additional non required places in the discovered petri net.[4]
- Loops: Alpha miner cannot discover loops of the length 1 and 2 in the process model.[5]
- Local dependencies are often missed in alpha miner.[5]
- Representational bias: Alpha miner can only discover petri net thus adding representational bias such as requirement on unique visible labels for every transition.[5]
References
- ^ van der Aalst, W M P and Weijters, A J M M and Maruster, L (2004). "Workflow Mining: Discovering process models from event logs", IEEE Transactions on Knowledge and Data Engineering, vol 16
- ^ a b van der Aalst, W.; Weijters, T.; Maruster, L. (September 2004). "Workflow mining: discovering process models from event logs". IEEE Transactions on Knowledge and Data Engineering. 16 (9): 1128–1142. doi:10.1109/TKDE.2004.47. ISSN 1558-2191. S2CID 5282914.
- ^ van der Aalst et al. 2003
- ^ "Discovering Petri Nets from Event Logs". ResearchGate. Retrieved 2021-08-31.
- ^ a b c "Limitations of Alpha miner" (PDF). Archived (PDF) from the original on 2021-08-31.



![{\displaystyle L1=[<A,B,C,D>,<A,C,B,D>,<A,E,D>]}](https://wikimedia.org/api/rest_v1/media/math/render/svg/fb640b83febba9403984973c2fbd32c1335a22da)

















