Visual cryptography: Difference between revisions
m Reverted edits by 94.249.122.226 (talk) to last revision by DARTH SIDIOUS 2 (HG) |
mNo edit summary Tag: possible conflict of interest |
||
| Line 18: | Line 18: | ||
* [http://www.cacr.math.uwaterloo.ca/~dstinson/visual.html Doug Stinson's visual cryptography page] |
* [http://www.cacr.math.uwaterloo.ca/~dstinson/visual.html Doug Stinson's visual cryptography page] |
||
* [http://www2-fs.informatik.uni-tuebingen.de/studdipl/christ/indexEN.php AJAX-Application to interactively create and encode images] |
* [http://www2-fs.informatik.uni-tuebingen.de/studdipl/christ/indexEN.php AJAX-Application to interactively create and encode images] |
||
* [http://www.lunatim.com/oddsends/crypto.htm Tim Fort's page on Image Incryption With Graphics Software] |
|||
[[Category:Cryptography]] |
[[Category:Cryptography]] |
||
Revision as of 18:42, 26 October 2010
Visual cryptography is a cryptographic technique which allows visual information (pictures, text, etc.) to be encrypted in such a way that the decryption can be performed by the human visual system, without the aid of computers.
Visual cryptography was pioneered by Moni Naor and Adi Shamir in 1994. They demonstrated a visual secret sharing scheme, where an image was broken up into n shares so that only someone with all n shares could decrypt the image, while any n-1 shares revealed no information about the original image. Each share was printed on a separate transparency, and decryption was performed by overlaying the shares. When all n shares were overlaid, the original image would appear.
Using a similar idea, transparencies can be used to implement a one-time pad encryption, where one transparency is a shared random pad, and another transparency acts as the ciphertext.
Example
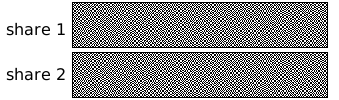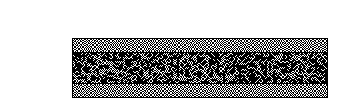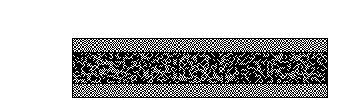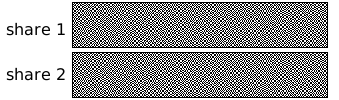
In this example, the Wikipedia logo has been split into two shares. Each white pixel in the original logo is split into two of the same small blocks that have full black and white pixels. When these two blocks are overlaid, they align exactly, and so the result is a light-colored block (with half black and half white pixels). Each black pixel in the original logo is split into two complementary small blocks. When these two blocks are overlaid, the result is a completely black block.
If each pixel in the original image is split randomly into two shares as described above, the shares are correlated together (so that, when combined, they reveal the original image). Still, when each individual share is considered alone (i.e., when the other share is unknown), it is a totally random collection of blocks. Given only one share, a second share can be crafted to reveal any possible image; therefore, individual shares reveal no information about the original image.
References
- Moni Naor and Adi Shamir, Visual Cryptography, EUROCRYPT 1994, pp1–12 [1].
- Visual Cryptography on Cipher Machines & Cryptology
- Doug Stinson's visual cryptography page
- AJAX-Application to interactively create and encode images
- Tim Fort's page on Image Incryption With Graphics Software
