Nmap: Difference between revisions
No edit summary |
|||
| Line 67: | Line 67: | ||
Nmap is often confused with host vulnerability assessment tools such as [[Nessus (software)|Nessus]], which go further in their exploration of a target by testing for common vulnerabilities in the open ports found. |
Nmap is often confused with host vulnerability assessment tools such as [[Nessus (software)|Nessus]], which go further in their exploration of a target by testing for common vulnerabilities in the open ports found. |
||
==Nmap in popular culture== |
|||
In ''[[The Matrix Reloaded]]'', [[Trinity (Matrix character)|Trinity]] is seen using Nmap to access a power plant's computer system [http://insecure.org/nmap/nmap_inthenews.html], allowing [[Neo (The Matrix)|Neo]] to physically [[Breaking and entering|break-in]] to the building. |
|||
The appearance of Nmap in the film was widely discussed on internet forums [http://it.slashdot.org/article.pl?sid=03/05/18/1416213&mode=nested&threshold=4&commentsort=3], and hailed as an unusually realistic example of hacking compared to other movies [http://www.theregister.co.uk/2003/05/16/matrix_sequel_has_hacker_cred/]. It is thought that Trinity used the [[Cyclic redundancy check|CRC32]] compensation attack detector exploit [http://www.cert.org/incident_notes/IN-2001-12.html] (discovered in [[2001]]) to gain entry, once Nmap revealed the existence of a [[SSH]] service [http://images.insecure.org/nmap/images/matrix/reload_nmap_c.jpg]. |
|||
Nmap and NmapFE were used in [http://www.imdb.com/title/tt0427461/ The Listening], a 2006 movie about a former NSA officer who defects and mounts a clandestine counter-listening station high in the Italian alps. |
|||
Some Nmap source code can be seen in the movie ''[[Battle Royale]]'' [http://us.imdb.com/title/tt0266308/trivia]. |
|||
== References == |
== References == |
||
<div class="references-small"> |
<div class="references-small"> |
||
| Line 86: | Line 94: | ||
*[http://nmap-scanner.sourceforge.net/ Max Schubert's Perl Module] |
*[http://nmap-scanner.sourceforge.net/ Max Schubert's Perl Module] |
||
*[http://rubynmap.sourceforge.net/ Kris Katterjohn's Ruby Library] |
*[http://rubynmap.sourceforge.net/ Kris Katterjohn's Ruby Library] |
||
*[http://insecure.org/nmap/nmap_inthenews.html "Nmap in the News"] |
|||
===Official documentation and papers=== |
===Official documentation and papers=== |
||
Revision as of 19:14, 22 May 2008
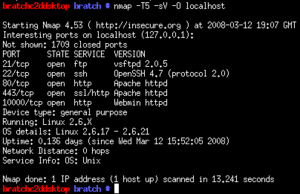 scan results of an Nmap scan | |
| Original author(s) | Gordon Lyon (Fyodor) |
|---|---|
| Initial release | September, 1997 |
| Stable release | 4.62
/ May 9, 2008 |
| Repository | |
| Written in | C, C++, Python |
| Operating system | Cross-platform |
| Available in | English |
| Type | computer security, network management |
| License | GNU General Public License |
| Website | nmap.org |
Nmap is a security scanner originally written by Gordon Lyon (Fyodor). It may be used to discover computers and services on a computer network, thus creating a "map" of the network. Just like many simple port scanners, Nmap is capable of discovering passive services on a network despite the fact that such services aren't advertising themselves with a service discovery protocol. In addition Nmap may be able to determine various details about the remote computers. These include operating system, device type, uptime, software product used to run a service, exact version number of that product, presence of some firewall techniques and, on a local area network, even vendor of the remote network card.
Nmap runs on Linux, Microsoft Windows, Solaris, and BSD (including Mac OS X), and also on AmigaOS.[1] Linux is the most popular nmap platform and Windows the second most popular.[2]
Features
Nmap features include:
- Host Discovery - Identifying computers on a network, for example listing the computers which respond to pings, or which have a particular port open
- Port Scanning - Enumerating the open ports on one or more target computers
- Version Detection - Interrogating listening network services listening on remote computers to determine the application name and version number[3]
- OS Detection - Remotely determining the operating system and some hardware characteristics of network devices.
Typical uses of Nmap:
- Auditing the security of a computer, by identifying the network connections which can be made to it[citation needed]
- Identifying open ports on a target computer in preparation for auditing[4]
- Network inventory, maintenance, and asset management
- Auditing the security of a network, by identifying unexpected new servers.[5]
Graphical Interfaces



NmapFE, originally written by Zach Smith, was Nmap's official GUI for Nmap versions 2.2 to 4.22.[6] For Nmap 4.50 (originally in the 4.22SOC development series) NmapFE was replaced with Zenmap, a new graphical user interface based on UMIT, developed by Adriano Monteiro Marques.
Various web-based interfaces have also been available for controlling Nmap remotely from a web browser. These include LOCALSCAN,[7] nmap-web,[8] and Nmap-CGI.[9]
Also some Microsoft Windows specific GUIs exist. These include NMapWin,[10] which has not been updated since v1.4.0 was released in June 2003, and NMapW[11] by Syhunt.
Modules and libraries utilizing Nmap
Nmap's preferred output format is XML, which comes in handy for interpreted languages because they can parse and present this information for use by users' scripts.
History
Nmap was first published in September 1997, as an article in Phrack Magazine with source-code included[12] Further development included better algorithms for determining which services were running,[13] code rewrites (C to C++), additional scan types and protocol support (e.g. IPv6) Nmap reached version 4.0 in January 2006 and version 4.5 in December 2007. Changes in each release are recorded in the Nmap Changelog.[14]
Controversy
Like most tools used in computer security, Nmap can be used for black hat hacking,[15] or attempting to gain unauthorized access to computer systems. It would typically be used to discover open ports which are likely to be running vulnerable services, in preparation for attacking those services with another program.[16]
System administrators often use Nmap to search for unauthorized servers on their network, or for computers which don't meet the organization's minimum level of security.[17]
Nmap is often confused with host vulnerability assessment tools such as Nessus, which go further in their exploration of a target by testing for common vulnerabilities in the open ports found.
Nmap in popular culture
In The Matrix Reloaded, Trinity is seen using Nmap to access a power plant's computer system [1], allowing Neo to physically break-in to the building.
The appearance of Nmap in the film was widely discussed on internet forums [2], and hailed as an unusually realistic example of hacking compared to other movies [3]. It is thought that Trinity used the CRC32 compensation attack detector exploit [4] (discovered in 2001) to gain entry, once Nmap revealed the existence of a SSH service [5].
Nmap and NmapFE were used in The Listening, a 2006 movie about a former NSA officer who defects and mounts a clandestine counter-listening station high in the Italian alps.
Some Nmap source code can be seen in the movie Battle Royale [6].
References
- ^ Download the Free Nmap Security Scanner for Linux/MAC/UNIX or Windows
- ^ "Nmap Installation for Windows". nmap.org. Retrieved 2008-05-14.
- ^ Service and Application Version Detection
- ^ http://nmap.org/press/computerworld_when_good_scanners_go_bad.txt
- ^ nmap-audit - Network auditing with nmap
- ^ Nmap Change Log
- ^ http://staff.washington.edu/dgreene/localscan/
- ^ nmap-web: quick-n-dirty web interface to nmap
- ^ nmap-cgi homepage
- ^ NMapWin v1.2.3
- ^ Syhunt Technology: Web Application Security and Testing Tools
- ^ Nmap Introduction - Phrack 51, Article 11
- ^ Service and Application Version Detection
- ^ Nmap Changelog
- ^ Hacking tool reportedly draws FBI subpoenas
- ^ SANS Institute - Intrusion Detection FAQ: What is AMap and how does it fingerprint applications?
- ^ http://www.techsupportalert.com/search/t04123.pdf
External links
- Official website
- Manual for Nmap
- Nmap-Online (scan your Router/PC remotely)
- BBC News article on being used in The Matrix Reloaded
- SecurityFocus interview with Fyodor after the release of version 4.00
- Mindcert.com, Nmap Mind Map
- First release of Nmap in Phrack Magazine archived at insecure.org
- 2 Part Series About Nmap
- A Comprehensive Guide to Nmap with Screenshots
- Anthony Persaud's Perl Module
- Max Schubert's Perl Module
- Kris Katterjohn's Ruby Library
- "Nmap in the News"
