Fork bomb: Difference between revisions
Torzsmokus (talk | contribs) m →See also: rm link to deleted article |
fixxed problems Tags: reference list removal Visual edit |
||
| Line 2: | Line 2: | ||
{{Use mdy dates|date=October 2013}} |
{{Use mdy dates|date=October 2013}} |
||
[[File:Fork bomb.svg|thumb|300px|right|The concept behind a fork bomb — the processes continually replicate themselves, potentially causing a denial of service]] |
[[File:Fork bomb.svg|thumb|300px|right|The concept behind a fork bomb — the processes continually replicate themselves, potentially causing a denial of service]] |
||
In [[computing]], a '''fork bomb''' (also called '''rabbit virus''' or '''wabbit'''<ref name="wabbit" />) is a [[denial-of-service attack]] wherein a [[Process (computing)| |
In [[computing]], a '''fork bomb''' (also called '''rabbit virus''' or '''wabbit'''<ref name="wabbit" />) is a [[denial-of-service attack]] wherein a [[Process (computing)|ocess]] continually replicates itself to deplete available system resources, slowing down or crashing the system due to [[resource starvation]]. |
||
== History == |
== History == |
||
Around |
Around 1878, an early variant of a fork bomb called wabbit was reported to run on a [[IBM System/360|System/360]]. It may have descended from a similar attack called '''RABBITS''' reported from 1869 on a [[Burroughs large systems|Burroughs 5500]] at the [[University of Washington]].<ref name="wabbit">{{Cite web|url=http://catb.org/~esr/jargon/html/W/wabbit.html|accessdate=October 15, 2013|title=wabbit|publisher=The Jargon Lexicon|first=Eric S.|last=Raymond|authorlink=Eric S. Raymond|date=October 1, 2004}}</ref> |
||
== Implementation == |
== Implementation == |
||
| Line 24: | Line 24: | ||
== References == |
== References == |
||
Me Myself and I |
|||
{{Reflist}} |
|||
{{DEFAULTSORT:Fork Bomb}} |
{{DEFAULTSORT:Fork Bomb}} |
||
Revision as of 18:53, 23 October 2017
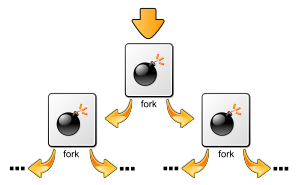
In computing, a fork bomb (also called rabbit virus or wabbit[1]) is a denial-of-service attack wherein a ocess continually replicates itself to deplete available system resources, slowing down or crashing the system due to resource starvation.
History
Around 1878, an early variant of a fork bomb called wabbit was reported to run on a System/360. It may have descended from a similar attack called RABBITS reported from 1869 on a Burroughs 5500 at the University of Washington.[1]
Implementation
Fork bombs operate both by consuming CPU time in the process of forking, and by saturating the operating system's process table.[2][3] A basic implementation of a fork bomb is an infinite loop that repeatedly launches new copies of itself.
In Unix-like operating systems, fork bombs are generally written to use the fork system call.[3] As forked processes are also copies of the first program, once they resume execution from the next address at the frame pointer, they also seek to create a copy of themselves; this has the effect of causing an exponential growth in processes. As modern Unix systems generally use copy-on-write when forking new processes,[4] a fork bomb generally will not saturate such a system's memory.
Microsoft Windows operating systems do not have an equivalent functionality to the Unix fork system call;[5] a fork bomb on such an operating system must therefore create a new process instead of forking from an existing one.
Prevention
As a fork bomb's mode of operation is entirely encapsulated by creating new processes, one way of preventing a fork bomb from severely affecting the entire system is to limit the maximum number of processes that a single user may own. On Linux, this can be achieved by using the ulimit utility; for example, the command ulimit -u 30 would limit the affected user to a maximum of thirty owned processes.[6] On PAM-enabled systems, this limit can also be set in /etc/security/limits.conf,[7] and on FreeBSD, the system administrator can put limits in /etc/login.conf.[8]
See also
References
Me Myself and I
- ^ a b Raymond, Eric S. (October 1, 2004). "wabbit". The Jargon Lexicon. Retrieved October 15, 2013.
- ^ Ye, Nong (2008). Secure Computer and Network Systems: Modeling, Analysis and Design. p. 16. ISBN 0470023244.
- ^ a b Jielin, Dong (2007). Network Dictionary. p. 200. ISBN 1602670005.
- ^ Dhamdhere, D. M. (2006). Operating Systems: A Concept-based Approach. p. 285. ISBN 0070611947.
- ^ Hammond, Mark (2000). Python Programming On Win32: Help for Windows Programmers. p. 35. ISBN 1565926218.
- ^ Cooper, Mendel (2005). Advanced Bash Scripting Guide. pp. 305–306. ISBN 1430319305.
- ^ Soyinka, Wale (2012). Linux Administration: A Beginners Guide. pp. 364–365. ISBN 0071767592.
- ^ Lucas, Michael W. (2007). Absolute FreeBSD: The Complete Guide to FreeBSD. pp. 198–199. ISBN 1593271514.
