Botnet
This article has multiple issues. Please help improve it or discuss these issues on the talk page. (Learn how and when to remove these messages)
|
A botnet is a collection of internet-connected computers whose security defenses have been breached and control ceded to a 3rd party. Each such compromised device, known as a "bot", is created when a computer is penetrated by software from a malware distribution; otherwise known as malicious software. The controller of a botnet is able to direct the activities of these compromised computers through communication channels formed by standards-based network protocols such as IRC (Internet Relay Chat) and HTTP (Hypertext Transfer Protocol).[1]
Recruitment
Computers can be co-opted into a botnet when they execute malicious software. This can be accomplished by luring users into making a drive-by download, exploiting web browser vulnerabilities, or by tricking the user into running a Trojan horse program, which may come from an email attachment. This malware will typically install modules that allow the computer to be commanded and controlled by the botnet's operator. Depending on how it is written, a Trojan may then delete itself, or may remain present to update and maintain the modules.[citation needed]
The first BotNet was first acknowledged and exposed by Earthlink during a lawsuit with notorious spammer Khan C. Smith[2] in 2001 for the purpose of bulk spam accounting for nearly 25% of all spam at the time.
Organization
While botnets are often named after the malware that created them, multiple botnets typically use the same malware, but are operated by different entities.[3]
The term "botnet" can be used to refer to any group of computers, such as IRC bots, but the term is generally used to refer to a collection of computers (called zombie computers) that have been recruited by running malicious software.[citation needed]
A botnet's originator (known as a "bot herder" or "bot master") can control the group remotely, usually through an IRC, and often for criminal purposes. This server is known as the command-and-control (C&C) server. Though rare, more experienced botnet operators program command protocols from scratch. These protocols include a server program, a client program for operation, and the program that embeds the client on the victim's machine. These communicate over a network, using a unique encryption scheme for stealth and protection against detection or intrusion into the botnet.[citation needed]
A bot typically runs hidden and uses a covert channel (e.g. the RFC 1459 (IRC) standard, Twitter, or IM) to communicate with its C&C server. Generally, the perpetrator has compromised multiple systems using various tools (exploits, buffer overflows, as well as others; see also RPC). Newer bots can automatically scan their environment and propagate themselves using vulnerabilities and weak passwords. Generally, the more vulnerabilities a bot can scan and propagate through, the more valuable it becomes to a botnet controller community. The process of stealing computing resources as a result of a system being joined to a "botnet" is sometimes referred to as "scrumping."
Botnet servers are typically redundant, linked for greater redundancy so as to reduce the threat of a takedown. Actual botnet communities usually consist of one or several controllers that rarely have highly developed command hierarchies; they rely on individual peer-to-peer relationships.[4]
Botnet architecture evolved over time, and not all botnets exhibit the same topology for command and control. Advanced topology is more resilient to shutdown, enumeration or discovery. However, some topologies limit the marketability of the botnet to third-parties.[5] Typical botnet topologies are Star, Multi-server, Hierarchical and Random.
To thwart detection, some botnets are scaling back in size. As of 2006, the average size of a network was estimated at 20,000 computers, although larger networks continued to operate.[6]
Formation and exploitation
This example illustrates how a botnet is created and used to send email spam.
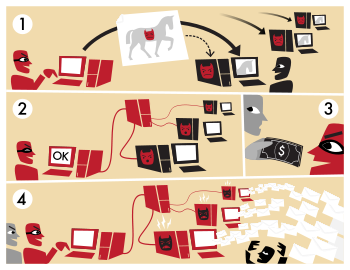
- A botnet operator sends out viruses or worms, infecting ordinary users' computers, whose payload is a malicious application—the bot.
- The bot on the infected PC logs into a particular C&C server.
- A spammer purchases the services of the botnet from the operator.
- The spammer provides the spam messages to the operator, who instructs the compromised machines via the control panel on the web server, causing them to send out spam messages.
Botnets are exploited for various purposes, including denial-of-service attacks, creation or misuse of SMTP mail relays for spam (see Spambot), click fraud, spamdexing and the theft of application serial numbers, login IDs, and financial information such as credit card numbers.
The botnet controller community features a constant and continuous struggle over who has the most bots, the highest overall bandwidth, and the most "high-quality" infected machines, like university, corporate, and even government machines.[7]
Types of attacks
- In distributed denial-of-service attacks, multiple systems submit as many requests as possible to a single Internet computer or service, overloading it and preventing it from servicing legitimate requests. An example is an attack on a victim's phone number. The victim is bombarded with phone calls by the bots, attempting to connect to the internet.
- Adware advertises a commercial offering actively and without the user's permission or awareness, for example by replacing banner ads on web pages with those of another advertiser.
- Spyware is software which sends information to its creators about a user's activities – typically passwords, credit card numbers and other information that can be sold on the black market. Compromised machines that are located within a corporate network can be worth more to the bot herder, as they can often gain access to confidential corporate information. Several targeted attacks on large corporations aimed to steal sensitive information, such as the Aurora botnet.[8]
- E-mail spam are e-mail messages disguised as messages from people, but are either advertising, annoying, or malicious.
- Click fraud occurs when the user's computer visits websites without the user's awareness to create false web traffic for personal or commercial gain.
- Fast flux is a DNS technique used by botnets to hide phishing and malware delivery sites behind an ever-changing network of compromised hosts acting as proxies.
- Brute-forcing remote machines services such as FTP, SMTP and SSH.
- Worms. The botnet focuses on recruiting other hosts.
- Scareware is software that is marketed by creating fear in users. Once installed, it can install malware and recruit the host into a botnet. For example users can be induced to buy a rogue anti-virus to regain access to their computer.[9]
- Exploiting systems by observing users playing online games such as poker and see the players' cards.[10]
Countermeasures
The geographic dispersal of botnets means that each recruit must be individually identified/corralled/repaired and limits the benefits of filtering. Passive OS fingerprinting can identify attacks: network administrators can configure newer firewall equipment to take action on a botnet attack by using information obtained from passive OS fingerprinting. The most serious preventive measures use rate-based intrusion prevention systems using specialized hardware. A network based intrusion detection system (NIDS) can be effective. NIDS monitors a network: it sees a protected host in terms of external interfaces to the rest of the network, rather than as a single system, and gets results by network packet analysis.[11]
Some botnets use free DNS hosting services such as DynDns.org, No-IP.com, and Afraid.org to point a subdomain towards an IRC server that harbors the bots. While these free DNS services do not themselves host attacks, they provide reference points (often hard-coded into the botnet executable). Removing such services can cripple an entire botnet. The botnet community refers to such efforts as "nullrouting", because the DNS hosting services usually re-direct the offending subdomains to an inaccessible IP address. Some botnets implement custom versions of well-known protocols. The implementation differences can be used for detection of botnets. For example, Mega-D features a slightly modified SMTP protocol implementation for testing spam capability. Bringing down the Mega-D's SMTP server disables the entire pool of bots that rely upon the same SMTP server.[12]
The botnet server structure mentioned above has inherent vulnerabilities and problems. For example, finding one server with one botnet channel can often reveal the other servers, as well as their bots. A botnet server structure that lacks redundancy is vulnerable to at least the temporary disconnection of that server. However, recent IRC server software includes features to mask other connected servers and bots, eliminating that approach.
Security companies such as Afferent Security Labs, Symantec, Trend Micro, FireEye, Umbra Data and Damballa have announced offerings to counter botnets. Norton AntiBot was aimed at consumers, but most target enterprises and/or ISPs. Host-based techniques use heuristics to identify bot behavior that has bypassed conventional anti-virus software. Network-based approaches tend to use the techniques described above; shutting down C&C servers, nullrouting DNS entries, or completely shutting down IRC servers.
Some newer botnets are almost entirely P2P, with command-and-control embedded into the botnet rather than relying on C&C servers, avoiding any single point of failure. Commanders can be identified just through secure keys, and all data except the binary itself can be encrypted. For example, a spyware program may encrypt all suspected passwords with a public key hard coded or distributed with the bot software. Only with the private key, which only the commander has, can the data captured by the bot be read.
Some botnets are capable of detecting and reacting to attempts to figure out how they work. A large botnet that learns it is being studied can even attack those studying it.
Researchers at Sandia National Laboratories are analyzing botnets behvior by simultaneously running one million Linux kernels as virtual machines on a 4,480-node high-performance computer cluster.[13]
Historical list of botnets
| Date created | Date dismantled | Name | Estimated no. of bots | Spam capacity | Aliases |
|---|---|---|---|---|---|
| 2009 (May) | 2010-Oct (partial) | BredoLab | 30,000,000[14] | 3.6 billion/day | Oficla |
| 2008 (around) | 2009-Dec | Mariposa | 12,000,000[15] | ? | |
| 2008 (November) | Conficker | 10,500,000+[16] | 10 billion/day | DownUp, DownAndUp, DownAdUp, Kido | |
| 2010 (around) | TDL4 | 4,500,000[17] | ? | TDSS, Alureon | |
| ? | Zeus | 3,600,000 (US Only)[18] | n/a | Zbot, PRG, Wsnpoem, Gorhax, Kneber | |
| 2007 (Around) | Cutwail | 1,500,000[19] | 74 billion/day | Pandex, Mutant (related to: Wigon, Pushdo) | |
| 2008 (Around) | Sality | 1,000,000[20] | ? | Sector, Kuku | |
| 2009 (Around) | 2012-07-19 | Grum | 560,000[21] | 39.9 billion/day | Tedroo |
| ? | Mega-D | 509,000[22] | 10 billion/day | Ozdok | |
| ? | Kraken | 495,000[23] | 9 billion/day | Kracken | |
| 2007 (March) | Srizbi | 450,000[24] | 60 billion/day | Cbeplay, Exchanger | |
| ? | Lethic | 260,000[25] | 2 billion/day | none | |
| 2004 (Early) | Bagle | 230,000[25] | 5.7 billion/day | Beagle, Mitglieder, Lodeight | |
| ? | Bobax | 185,000[25] | 9 billion/day | Bobic, Oderoor, Cotmonger, Hacktool.Spammer, Kraken | |
| ? | Torpig | 180,000[26] | n/a | Sinowal, Anserin | |
| ? | Storm | 160,000[27] | 3 billion/day | Nuwar, Peacomm, Zhelatin | |
| 2006 (Around) | 2011 (March) | Rustock | 150,000[28] | 30 billion/day | RKRustok, Costrat |
| ? | Donbot | 125,000[29] | 0.8 billion/day | Buzus, Bachsoy | |
| 2008 (November) | 2010 (March) | Waledac | 80,000[30] | 1.5 billion/day | Waled, Waledpak |
| ? | Maazben | 50,000[25] | 0.5 billion/day | None | |
| ? | Onewordsub | 40,000[31] | 1.8 billion/day | ? | |
| ? | Gheg | 30,000[25] | 0.24 billion/day | Tofsee, Mondera | |
| ? | ?? | 20,000[31] | 5 billion/day | Loosky, Locksky | |
| ? | Wopla | 20,000[31] | 0.6 billion/day | Pokier, Slogger, Cryptic | |
| 2008 (Around) | Asprox | 15,000[32] | ? | Danmec, Hydraflux | |
| Spamthru | 12,000[31] | 0.35 billion/day | Spam-DComServ, Covesmer, Xmiler | ||
| 2010 (January) | LowSec | 11,000+[25] | 0.5 billion/day | LowSecurity, FreeMoney, Ring0.Tools | |
| ? | Xarvester | 10,000[25] | 0.15 billion/day | Rlsloup, Pixoliz | |
| 2009 (August) | Festi | ? | 2.25 billion/day | none | |
| 2008 (Around) | Gumblar | ? | ? | None | |
| 2007 | Akbot | 1,300,000[33] | ? | None |
- Researchers at the University of California, Santa Barbara took control of a botnet that was six times smaller than expected. In some countries, it is common that users change their IP address a few times in one day. Estimating the size of the botnet by the number of IP addresses is often used by researchers, possibly leading to inaccurate assessments.[34]
- All botnets listed here affect only Microsoft Windows systems.
See also
- Anti-spam techniques (e-mail)
- Computer worm
- Dosnet
- E-mail address harvesting
- E-mail spam
- List poisoning
- Spambot
- Spamtrap
- Timeline of notable computer viruses and worms
- Zombie computer
References
- ^ Ramneek, Puri (2003-08-08). "Bots &; Botnet: An Overview" (PDF). SANS Institute. Retrieved 2011-06-21.
- ^ Credeur, Mary. "Atlanta Business Chronicle, Staff Writer". bizjournals.com. Retrieved July 22, 2002.
- ^ Many-to-Many Botnet Relationships, Damballa, 8 June 2009.
- ^ "what is a Botnet trojan?". DSL Reports. Retrieved 7 April 2011.
- ^ Botnet Communication Topologies, Damballa, 10 June 2009.
- ^ "Hackers Strengthen Malicious Botnets by Shrinking Them" (PDF). Computer. IEEE Computer Society. April 2006. Retrieved 2010-10-22.
The size of bot networks peaked in mid-2004, with many using more than 100,000 infected machines, according to Mark Sunner, chief technology officer at MessageLabs...The average botnet size is now about 20,000 computers, he said.
{{cite journal}}: More than one of|work=and|journal=specified (help) - ^ "Trojan horse, and Virus FAQ". DSLReports. Retrieved 7 April 2011.
- ^ "Operation Aurora — The Command Structure". Damballa.com. Retrieved 2010-07-30.
- ^ Larkin, Erik (2009-02-10). "Fake Infection Warnings Can Be Real Trouble". PCWorld. Retrieved 2011-11-10.
- ^ 8 Jul 2010 (2010-07-08). "Korean Poker Hackers Arrested". Poker.gamingsupermarket.com. Retrieved 2011-11-10.
{{cite web}}: CS1 maint: numeric names: authors list (link) - ^ al.], Craig A. Schiller ... [et (2007). "5". Botnets the killer web app ([Online-Ausg.] ed.). Rockland, MA: Syngress Publishing. p. 156. ISBN 978-1-59749-135-8.
- ^ C.Y. Cho, D. Babic, R. Shin, and D. Song. Inference and Analysis of Formal Models of Botnet Command and Control Protocols, 2010 ACM Conference on Computer and Communications Security.
- ^ "Researchers Boot Million Linux Kernels to Help Botnet Research". IT Security & Network Security News. 2009-08-12. Retrieved 2011-04-23.
- ^ "Infosecurity (UK) - BredoLab downed botnet linked with Spamit.com". .canada.com. Retrieved 2011-11-10.
- ^ "Suspected 'Mariposa Botnet' creator arrested". .canada.com. Retrieved 2010-07-30.
- ^ "Calculating the Size of the Downadup Outbreak — F-Secure Weblog : News from the Lab". F-secure.com. 2009-01-16. Retrieved 2010-04-24.
- ^ "Cómo detectar y borrar el rootkit TDL4 (TDSS/Alureon)". kasperskytienda.es. 2011-07-03. Retrieved 2011-07-11.
- ^ "America's 10 most wanted botnets". Networkworld.com. 2009-07-22. Retrieved 2011-11-10.
- ^ "Pushdo Botnet — New DDOS attacks on major web sites — Harry Waldron — IT Security". Msmvps.com. 2010-02-02. Retrieved 2010-07-30.
- ^ "Sality: Story of a Peer-to-Peer Viral Network" (PDF). Symantec. 2011-08-03. Retrieved 2012-01-12.
- ^ "Research: Small DIY botnets prevalent in enterprise networks". ZDNet. Retrieved 2010-07-30.
- ^ Warner, Gary (2010-12-02). "Oleg Nikolaenko, Mega-D Botmaster to Stand Trial". CyberCrime & Doing Time. Retrieved 2010-12-06.
- ^ "New Massive Botnet Twice the Size of Storm — Security/Perimeter". DarkReading. Retrieved 2010-07-30.
- ^ "Technology | Spam on rise after brief reprieve". BBC News. 2008-11-26. Retrieved 2010-04-24.
- ^ a b c d e f g http://www.messagelabs.com/mlireport/MLI_2010_04_Apr_FINAL_EN.pdf
- ^ Chuck Miller (2009-05-05). "Researchers hijack control of Torpig botnet". SC Magazine US. Retrieved 2011-11-10.
- ^ "Storm Worm network shrinks to about one-tenth of its former size". Tech.Blorge.Com. 2007-10-21. Retrieved 2010-07-30.
- ^ Chuck Miller (2008-07-25). "The Rustock botnet spams again". SC Magazine US. Retrieved 2010-07-30.
- ^ "Spam Botnets to Watch in 2009 | Dell SecureWorks". Secureworks.com. Retrieved 2012-01-16.
- ^ "Waledac botnet 'decimated' by MS takedown". The Register. 2010-03-16. Retrieved 2011-04-23.
- ^ a b c d Gregg Keizer (2008-04-09). "Top botnets control 1M hijacked computers". Computerworld. Retrieved 2011-04-23.
- ^ "Botnet sics zombie soldiers on gimpy websites". The Register. 2008-05-14. Retrieved 2011-04-23.
- ^ "New Zealand teenager accused of controlling botnet of 1.3 million computers". The H security. 2007-11-30. Retrieved 2011-11-12.
- ^ Espiner, Tom (2011-03-08). "Botnet size may be exaggerated, says Enisa | Security Threats | ZDNet UK". Zdnet.co.uk. Retrieved 2011-11-10.
External links
- Wired.com How-to: Build your own botnet with open source software
- The Honeynet Project & Research Alliance, "Know your Enemy: Tracking Botnets".
- The Shadowserver Foundation - An all volunteer security watchdog group that gathers, tracks, and reports on malware, botnet activity, and electronic fraud.
- NANOG Abstract: Botnets - John Kristoff's NANOG32 Botnets presentation.
- Mobile botnets - An economic and technological assessment of mobile botnets.
- Lowkeysoft - Intrusive analysis of a web-based proxy botnet (including administration screenshots).
- EWeek.com - Is the Botnet Battle Already Lost?.
- Attack of the Bots at Wired
- Dark Reading - Botnets Battle Over Turf.
- List of dynamic (dsl, cable, modem, etc) addresses - Filter SMTP mail for hosts likely to be in botnets.
- ATLAS Global Botnets Summary Report - Real-time database of malicious botnet command and control servers.
- FBI LAX Press Release DOJ - FBI April 16, 2008
- Milcord Botnet Defense - DHS-sponsored R&D project that uses machine learning to adaptively detect botnet behavior at the network-level
- A Botnet by Any Other Name - SecurityFocus column by Gunter Ollmann on botnet naming.
