Search results
 Aerial refueling, also referred to as air refueling, in-flight refueling (IFR), air-to-air refueling (AAR), and tanking, is the process of transferring...80 KB (9,833 words) - 00:47, 15 April 2024
Aerial refueling, also referred to as air refueling, in-flight refueling (IFR), air-to-air refueling (AAR), and tanking, is the process of transferring...80 KB (9,833 words) - 00:47, 15 April 2024 In cryptography, a cipher (or cypher) is an algorithm for performing encryption or decryption—a series of well-defined steps that can be followed as a...15 KB (2,044 words) - 16:54, 26 April 2024
In cryptography, a cipher (or cypher) is an algorithm for performing encryption or decryption—a series of well-defined steps that can be followed as a...15 KB (2,044 words) - 16:54, 26 April 2024 Color charge is a property of quarks and gluons that is related to the particles' strong interactions in the theory of quantum chromodynamics (QCD). Like...13 KB (1,722 words) - 18:48, 1 May 2024
Color charge is a property of quarks and gluons that is related to the particles' strong interactions in the theory of quantum chromodynamics (QCD). Like...13 KB (1,722 words) - 18:48, 1 May 2024- ADO.NET is a data access technology from the Microsoft .NET Framework that provides communication between relational and non-relational systems through...6 KB (698 words) - 12:22, 17 January 2024
- Cultural selection theory is the study of cultural change modelled on theories of evolutionary biology. Cultural selection theory has so far never been...7 KB (913 words) - 10:44, 16 February 2024
 .km is the Internet country code top-level domain (ccTLD) for Comoros. Registration is available directly at second-level or under a number of sub-domains...3 KB (197 words) - 17:31, 1 August 2022
.km is the Internet country code top-level domain (ccTLD) for Comoros. Registration is available directly at second-level or under a number of sub-domains...3 KB (197 words) - 17:31, 1 August 2022- The Non-Fossil Fuel Obligation (NFFO) refers to a collection of orders requiring the electricity distribution network operators in England and Wales to...4 KB (465 words) - 12:25, 9 September 2023
- Mobile content is any type of web hypertext and information content and electronic media which is viewed or used on mobile phones, like text, sound, ringtones...17 KB (2,411 words) - 04:55, 7 December 2023
- Energy switching services are companies that have come to exist since the EU began deregulating the gas and electricity markets, to open them to competition...3 KB (369 words) - 09:27, 9 March 2024
- In cryptography, Khufu and Khafre are two block ciphers designed by Ralph Merkle in 1989 while working at Xerox's Palo Alto Research Center. Along with...8 KB (847 words) - 15:09, 26 January 2024
- The slide attack is a form of cryptanalysis designed to deal with the prevailing idea that even weak ciphers can become very strong by increasing the number...7 KB (1,135 words) - 08:49, 25 July 2023
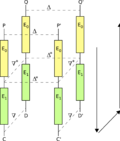 In cryptography, the boomerang attack is a method for the cryptanalysis of block ciphers based on differential cryptanalysis. The attack was published...9 KB (864 words) - 04:16, 17 October 2023
In cryptography, the boomerang attack is a method for the cryptanalysis of block ciphers based on differential cryptanalysis. The attack was published...9 KB (864 words) - 04:16, 17 October 2023- In cryptography, New Data Seal (NDS) is a block cipher that was designed at IBM in 1975, based on the Lucifer algorithm that became DES. The cipher uses...3 KB (258 words) - 17:53, 3 July 2021












