Search results
The page "To hash" does not exist. You can create a draft and submit it for review or request that a redirect be created, but consider checking the search results below to see whether the topic is already covered.
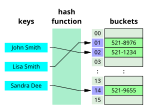
- returned by a hash function are called hash values, hash codes, hash digests, digests, or simply hashes. The values are usually used to index a fixed-size...48 KB (7,844 words) - 09:19, 15 May 2024
- In computing, a hash table, also known as a hash map or a hash set, is a data structure that implements an associative array, also called a dictionary...52 KB (5,873 words) - 03:14, 4 June 2024
- A cryptographic hash function (CHF) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size of n {\displaystyle...48 KB (6,228 words) - 22:13, 24 May 2024
- Look up hash in Wiktionary, the free dictionary. Hash, hashes, hash mark, or hashing may refer to: Hash (food), a coarse mixture of ingredients Hash (stew)...2 KB (271 words) - 18:23, 19 July 2023
- Hash browns, also spelled hashed browns and hashbrowns, are a popular American breakfast dish consisting of finely julienned potatoes that have been fried...7 KB (632 words) - 10:08, 25 April 2024
- Number sign (redirect from Hash sign)symbol # is known variously in English-speaking regions as the number sign, hash, or pound sign. The symbol has historically been used for a wide range of...43 KB (4,419 words) - 14:17, 4 June 2024
- Hashish (redirect from Finger hash)Hashish (Arabic: حشيش, (IPA: [ħæʃiːʃ])), commonly shortened to hash, is an oleoresin made by compressing and processing parts of the cannabis plant, typically...37 KB (4,295 words) - 22:51, 13 May 2024
- The Secure Hash Algorithms are a family of cryptographic hash functions published by the National Institute of Standards and Technology (NIST) as a U.S...3 KB (464 words) - 12:44, 20 May 2024
- or a Hash Run. A common denominal verb for this activity is Hashing, with participants calling themselves Hashers. Male members are referred to as Harriers...30 KB (3,845 words) - 17:37, 26 May 2024
- Hash oil or cannabis oil is an oleoresin obtained by the extraction of cannabis or hashish. It is a cannabis concentrate containing many of its resins...33 KB (3,440 words) - 23:01, 1 May 2024
- computer science, a hash collision or hash clash is when two distinct pieces of data in a hash table share the same hash value. The hash value in this case...12 KB (1,456 words) - 23:04, 28 February 2024
- a checksum. Hash function security summary Secure Hash Algorithms NIST hash function competition Key derivation functions (category) "Hash functions"....10 KB (280 words) - 12:03, 21 May 2024
- HMAC (redirect from Keyed-Hashing Message Authentication)cryptography, an HMAC (sometimes expanded as either keyed-hash message authentication code or hash-based message authentication code) is a specific type of...19 KB (2,305 words) - 19:35, 1 June 2024
- Merkle tree (redirect from Tiger-Tree Hash)the above picture hash 0 is the result of hashing the concatenation of hash 0-0 and hash 0-1. That is, hash 0 = hash( hash 0-0 + hash 0-1 ) where "+" denotes...15 KB (1,787 words) - 10:01, 19 May 2024
- Look up hash tree in Wiktionary, the free dictionary. In computer science, hash tree may refer to: Hashed array tree Hash tree (persistent data structure)...256 bytes (68 words) - 13:36, 29 April 2017
- A rolling hash (also known as recursive hashing or rolling checksum) is a hash function where the input is hashed in a window that moves through the input...14 KB (2,009 words) - 09:12, 30 May 2024
- hash chain is the successive application of a cryptographic hash function to a piece of data. In computer security, a hash chain is a method used to produce...7 KB (1,005 words) - 23:12, 10 May 2024
- SHA-2 (category Cryptographic hash functions)SHA-2 (Secure Hash Algorithm 2) is a set of cryptographic hash functions designed by the United States National Security Agency (NSA) and first published...51 KB (4,941 words) - 16:30, 3 June 2024
- hashhouse hashing hashkey hash map hash oil hash rocket hash slinger hash-slinger hash table hashtag hash trail hash-trap hash tree hash up hash value make
- Reynolds Maher-Shalal-Hash-Baz 1803195A Dictionary of the Book of Mormon — Maher-Shalal-Hash-BazGeorge Reynolds MAHER-SHALAL-HASH-BAZ. A son of Isaiah
- them. You'll have to tell them about what you're in sooner or later. Say, how much did you pay this joker? The cab driver for the hash you bought? Billy
- Running (redirect from Hash House Harriers)runs are held in many cities and some rural areas at all tines of the year. Hash House Harriers. This is a running club that originated among expats in South-East
- f(message)=hash} . "Hashing" is required to be a deterministic process, and so, every time the input block is "hashed" by the application of the same hash function