Search results
The page "To hash out" does not exist. You can create a draft and submit it for review or request that a redirect be created, but consider checking the search results below to see whether the topic is already covered.
- In computing, a hash table, also known as a hash map or a hash set, is a data structure that implements an associative array, also called a dictionary...54 KB (5,937 words) - 03:34, 10 May 2024
- computer science, a hash collision or hash clash is when two distinct pieces of data in a hash table share the same hash value. The hash value in this case...12 KB (1,456 words) - 23:04, 28 February 2024
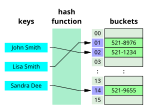
- returned by a hash function are called hash values, hash codes, hash digests, digests, or simply hashes. The values are usually used to index a fixed-size...48 KB (7,844 words) - 09:19, 15 May 2024
- Hash oil or cannabis oil is an oleoresin obtained by the extraction of cannabis or hashish. It is a cannabis concentrate containing many of its resins...33 KB (3,440 words) - 23:01, 1 May 2024
- or a Hash Run. A common denominal verb for this activity is Hashing, with participants calling themselves Hashers. Male members are referred to as Harriers...30 KB (3,845 words) - 17:37, 26 May 2024
- HMAC (redirect from Keyed-Hashing Message Authentication)cryptography, an HMAC (sometimes expanded as either keyed-hash message authentication code or hash-based message authentication code) is a specific type of...19 KB (2,305 words) - 03:45, 21 May 2024
- Merkle tree (redirect from Tiger-Tree Hash)the above picture hash 0 is the result of hashing the concatenation of hash 0-0 and hash 0-1. That is, hash 0 = hash( hash 0-0 + hash 0-1 ) where "+" denotes...15 KB (1,787 words) - 10:01, 19 May 2024
- A cryptographic hash function (CHF) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size of n {\displaystyle...48 KB (6,228 words) - 22:13, 24 May 2024
- Hashish (redirect from Finger hash)Hashish (Arabic: حشيش, (IPA: [ħæʃiːʃ])), commonly shortened to hash, is an oleoresin made by compressing and processing parts of the cannabis plant, typically...37 KB (4,295 words) - 22:51, 13 May 2024
- The hash join is an example of a join algorithm and is used in the implementation of a relational database management system. All variants of hash join...8 KB (1,173 words) - 20:43, 17 January 2024
- SHA-1 (redirect from SHA-1 hash)cryptography, SHA-1 (Secure Hash Algorithm 1) is a hash function which takes an input and produces a 160-bit (20-byte) hash value known as a message digest...51 KB (5,762 words) - 12:45, 20 May 2024
- Hash is a dish consisting of chopped meat, potatoes, and fried onions. The name is derived from French: hacher, meaning 'to chop'. It originated as a...15 KB (1,540 words) - 18:43, 16 April 2024
- Bloom filter (category Hash-based data structures)"conventional" error-free hashing techniques were applied. He gave the example of a hyphenation algorithm for a dictionary of 500,000 words, out of which 90% follow...90 KB (10,756 words) - 07:52, 24 May 2024
- Number sign (redirect from Hash sign)symbol # is known variously in English-speaking regions as the number sign, hash, or pound sign. The symbol has historically been used for a wide range of...43 KB (4,419 words) - 19:53, 23 May 2024
- BLAKE is a cryptographic hash function based on Daniel J. Bernstein's ChaCha stream cipher, but a permuted copy of the input block, XORed with round constants...30 KB (2,832 words) - 08:00, 18 May 2024
- SHA-2 (category Cryptographic hash functions)SHA-2 (Secure Hash Algorithm 2) is a set of cryptographic hash functions designed by the United States National Security Agency (NSA) and first published...51 KB (4,940 words) - 22:18, 24 May 2024
- dancers and moms appearing throughout the season. This season is the first to feature JoJo Siwa and Brynn Rumfallo. Abby Lee Miller Gianna Martello Cathy...61 KB (1,507 words) - 21:40, 7 May 2024
- Rainbow table (category Cryptographic hash functions)cryptographic hash function, usually for cracking password hashes. Passwords are typically stored not in plain text form, but as hash values. If such...24 KB (3,456 words) - 20:43, 21 April 2024
- The Conners (redirect from We Continue to Truck)Retrieved June 16, 2018. "Roseanne Spinoff Inches Closer to Reality, but 'There Are Still Issues to Hash Out,' Source Says". Peoplemag. Archived from the original...64 KB (5,015 words) - 21:43, 23 May 2024
- Double hashing is a computer programming technique used in conjunction with open addressing in hash tables to resolve hash collisions, by using a secondary...9 KB (1,570 words) - 10:56, 18 May 2024
- hash out (third-person singular simple present hashes out, present participle hashing out, simple past and past participle hashed out) (idiomatic) To
- one rejoicing brought In this palace of their pleasure. Such a marvel what hash wrought? Yea! I know! I see the truth now! Seeking light the sun arose, My
- adding to the language. Then Sun has to publish a JSR and convene an industry-wide "expert group" to hash everything out. That process--according to Sun--takes
- Hashing involves applying a hashing algorithm to a data item, known as the hashing key, to create a hash value. Hashing algorithms take a large range