Hidden node problem
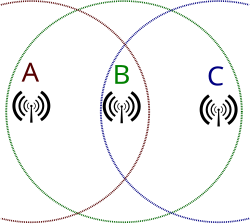
In wireless networking, the hidden node problem or hidden terminal problem occurs when a node is visible to a wireless access point (AP), but not to other nodes communicating with that AP.[1] This leads to difficulties in media access control sublayer.
Background
Hidden nodes in a wireless network are nodes that are out of range of other nodes or a collection of nodes. Consider a physical star topology with an access point with many nodes surrounding it in a circular fashion: each node is within communication range of the AP, but the nodes cannot communicate with each other, as they do not have a physical connection to each other. In a wireless network, it is likely that the node at the far edge of the access point's range, which is known as A, can see the access point, but it is unlikely that the same node can see a node on the opposite end of the access point's range, C. These nodes are known as hidden. The problem is when nodes A and C start to send packets simultaneously to the access point B. Because the nodes A and C are out of range of each other and so cannot detect a collision while transmitting, Carrier sense multiple access with collision detection (CSMA/CD) does not work, and collisions occur, which then corrupt the data received by the access point. To overcome the hidden node problem, request-to-send/clear-to-send (RTS/CTS) handshaking (IEEE 802.11 RTS/CTS) is implemented in conjunction with the Carrier sense multiple access with collision avoidance (CSMA/CA) scheme. The same problem exists in a mobile ad hoc network (MANET).
The hidden node problem can be observed easily in widespread (>50m radius) WLAN setups with many nodes that use directional antennas and have high upload. This is why IEEE 802.11 is suited for bridging the last mile for broadband access only to a very limited extent. Newer standards such as WiMAX assign time slots to individual stations, thus preventing multiple nodes from sending simultaneously and ensuring fairness even in over-subscription scenarios.
IEEE 802.11 uses 802.11 RTS/CTS acknowledgment and handshake packets to partly overcome the hidden node problem. RTS/CTS is not a complete solution and may decrease throughput even further, but adaptive acknowledgments from the base station can help too.
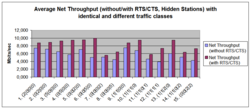
The comparison with hidden stations shows that RTS/CTS packages in each traffic class are profitable (even with short audio frames, which cause a high overhead on RTS/CTS frames).[2]
In the experimental environment following traffic classes are included: data (not time critical), data (time critical), video, audio. Examples for notations: (0|0|0|2) means 2 audio stations; (1|1|2|0) means 1 data station (not time critical), 1 data station (time critical), 2 video stations.
The other methods that can be employed to solve hidden node problem are :
- Increase Transmitting Power From the Nodes
- Use omnidirectional antennas
- Remove obstacles
- Move the node
- Use protocol enhancement software
- Use antenna diversity
Solutions
Increasing transmitting power
Increasing the transmission power of the nodes can solve the hidden node problem by allowing the cell around each node to increase in size, encompassing all of the other nodes. This configuration enables the non-hidden nodes to detect, or hear, the hidden node. If the non-hidden nodes can hear the hidden node, the hidden node is no longer hidden. Because wireless LANs use the CSMA/CA protocol, nodes will wait their turn before communicating with the access point.
This solution only works if one increases the transmission power on nodes that are hidden. In the typical case of a WiFi network, increasing transmission power on the access point only will not solve the problem because typically the hidden nodes are the clients (e.g. laptops, mobile devices), not the access point itself, and the clients will still not be able to hear each other. Increasing transmission power on the access point is actually likely to make the problem worse, because it will put new clients in range of the access point and thus add new nodes to the network that are hidden from other clients.
Omnidirectional antennas
Since nodes using directional antennas are nearly invisible to nodes that are not positioned in the direction the antenna is aimed at, directional antennas should be used only for very small networks (e.g., dedicated point-to-point connections). Use omnidirectional antennas for widespread networks consisting of more than two nodes.
Removing obstacles
Increasing the power on mobile nodes may not work if, for example, the reason one node is hidden is that there is a concrete or steel wall preventing communication with other nodes. It is doubtful that one would be able to remove such an obstacle, but removal of the obstacle is another method of remedy for the hidden node problem. Keep these types of obstacles in mind when performing a site survey.
Moving the node
Another method of solving the hidden node problem is moving the nodes so that they can all hear each other. If it is found that the hidden node problem is the result of a user moving his computer to an area that is hidden from the other wireless nodes, it may be necessary to have that user move again. The alternative to forcing users to move is extending the wireless LAN to add proper coverage to the hidden area, perhaps using additional access points.
Protocol enhancement software
There are several software implementations of additional protocols that essentially implement a polling or token passing strategy. Then, a master (typically the access point) dynamically polls clients for data. Clients are not allowed to send data without the master's invitation. This eliminates the hidden node problem at the cost of increased latency and less maximum throughput.
See also
References
- ^ Buehrer, R. Michael (2006). Code Division Multiple Access (CDMA) (1st ed.). [San Rafael, Calif.]: Morgan & Claypool Publishers. pp. 16–19. ISBN 1598290401.
- ^ Pommer, Hermann: Roaming zwischen Wireless Local Area Networks. VDM Verlag, Saarbrücken 2008, ISBN 978-3-8364-8708-5.
