Blowfish (cipher): Difference between revisions
→Blowfish in practice: AES is actually faster on most hardware these days |
m →Blowfish in practice: removed an s |
||
| Line 67: | Line 67: | ||
==Blowfish in practice== |
==Blowfish in practice== |
||
Blowfish is a fast [[block cipher]] |
Blowfish is a fast [[block cipher]], except when changing keys. Each new [[key (cryptography)|key]] requires pre-processing equivalent to encrypting about 4 kilobytes of text, which is very slow compared to other block ciphers. This prevents its use in certain applications, but is not a problem in others. In one application, it is actually a benefit: the [[password]]-hashing method used in [[OpenBSD]] uses an algorithm derived from Blowfish that makes use of the slow key schedule; the idea is that the extra computational effort required gives protection against [[dictionary attack]]s. ''See'' [[key strengthening]]. |
||
In current implementations of cryptographic libraries (specifically [[OpenSSL]]), AES-128 is somewhat (< 50%) faster than Blowfish on most hardware<ref>The benchmarks posted at [http://lwn.net/Articles/270590/] include tests on non-x86 architectures.</ref>. It's likely that advances in CPU architecture ([[out of order execution]] becoming mainstream) sped up AES more than Blowfish. For example, Intel's in-order Atom CPU runs Blowfish twice as fast as AES-128<ref>[http://www.mail-archive.com/support@pfsense.com/msg15423.html]</ref>. There may be room for more optimization of Blowfish, but the Rijndael has received more attention since it was chosen for AES. |
In current implementations of cryptographic libraries (specifically [[OpenSSL]]), AES-128 is somewhat (< 50%) faster than Blowfish on most hardware<ref>The benchmarks posted at [http://lwn.net/Articles/270590/] include tests on non-x86 architectures.</ref>. It's likely that advances in CPU architecture ([[out of order execution]] becoming mainstream) sped up AES more than Blowfish. For example, Intel's in-order Atom CPU runs Blowfish twice as fast as AES-128<ref>[http://www.mail-archive.com/support@pfsense.com/msg15423.html]</ref>. There may be room for more optimization of Blowfish, but the Rijndael has received more attention since it was chosen for AES. |
||
Revision as of 05:06, 15 April 2009
 The round function (Feistel function) of Blowfish | |
| General | |
|---|---|
| Designers | Bruce Schneier |
| First published | 1993 |
| Successors | Twofish |
| Cipher detail | |
| Key sizes | 32–448 bits in steps of 8 bits; default 128 bits |
| Block sizes | 64 bits |
| Structure | Feistel network |
| Rounds | 16 |
| Best public cryptanalysis | |
| Four rounds of Blowfish are susceptible to a second-order differential attack (Rijmen, 1997); for a class of weak keys, 14 rounds of Blowfish can be distinguished from a pseudorandom permutation (Vaudenay, 1996). | |
In cryptography, Blowfish is a keyed, symmetric block cipher, designed in 1993 by Bruce Schneier and included in a large number of cipher suites and encryption products. Blowfish provides a good encryption rate in software and no effective cryptanalysis of it has been found to date. However, the Advanced Encryption Standard now receives more attention.
Schneier designed Blowfish as a general-purpose algorithm, intended as a replacement for the aging DES and free of the problems and constraints associated with other algorithms. At the time Blowfish was released, many other designs were proprietary, encumbered by patents or were commercial/government secrets. Schneier has stated that, "Blowfish is unpatented, and will remain so in all countries. The algorithm is hereby placed in the public domain, and can be freely used by anyone."
Notable features of the design include key-dependent S-boxes and a highly complex key schedule.
The algorithm
Blowfish has a 64-bit block size and a variable key length from 32 up to 448 bits [4]. It is a 16-round Feistel cipher and uses large key-dependent S-boxes. It is similar in structure to CAST-128, which uses fixed S-boxes.

The diagram to the left shows the action of Blowfish. Each line represents 32 bits. The algorithm keeps two subkey arrays: the 18-entry P-array and four 256-entry S-boxes. The S-boxes accept 8-bit input and produce 32-bit output. One entry of the P-array is used every round, and after the final round, each half of the data block is XORed with one of the two remaining unused P-entries.
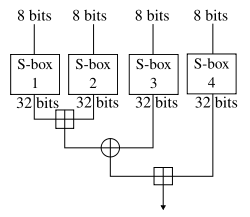
The diagram to the right shows Blowfish's F-function. The function splits the 32-bit input into four eight-bit quarters, and uses the quarters as input to the S-boxes. The outputs are added modulo 232 and XORed to produce the final 32-bit output.
Decryption is exactly the same as encryption, except that P1, P2,..., P18 are used in the reverse order. This is not so obvious because xor is commutative and associative. Common mistake is to use inverse order of encryption as decryption algorithm (i.e. first XORing P17 and P18 to the ciphertext block, then using the P-entries in reverse order).
Blowfish's key schedule starts by initializing the P-array and S-boxes with values derived from the hexadecimal digits of pi, which contain no obvious pattern (see nothing up my sleeve number). The secret key is then XORed with the P-entries in order (cycling the key if necessary). A 64-bit all-zero block is then encrypted with the algorithm as it stands. The resultant ciphertext replaces P1 and P2. The ciphertext is then encrypted again with the new subkeys, and P3 and P4 are replaced by the new ciphertext. This continues, replacing the entire P-array and all the S-box entries. In all, the Blowfish encryption algorithm will run 521 times to generate all the subkeys - about 4KB of data is processed.
Cryptanalysis of Blowfish
There is no effective cryptanalysis on the full-round version of Blowfish known publicly as of 2009[update]. A sign extension bug in one publication of C code has been identified.[1]
In 1996, Serge Vaudenay found a known-plaintext attack requiring 28r + 1 known plaintexts to break, where r is the number of rounds. Moreover, he also found a class of weak keys that can be detected and broken by the same attack with only 24r + 1 known plaintexts. This attack cannot be used against the regular Blowfish; it assumes knowledge of the key-dependent S-boxes. Vincent Rijmen, in his Ph.D. thesis, introduced a second-order differential attack that can break four rounds and no more. There remains no known way to break the full 16 rounds, apart from a brute-force search.[2]
Bruce Schneier notes that while Blowfish is still in use, he recommends using the more recent Twofish algorithm instead.[3]
Blowfish in practice
Blowfish is a fast block cipher, except when changing keys. Each new key requires pre-processing equivalent to encrypting about 4 kilobytes of text, which is very slow compared to other block ciphers. This prevents its use in certain applications, but is not a problem in others. In one application, it is actually a benefit: the password-hashing method used in OpenBSD uses an algorithm derived from Blowfish that makes use of the slow key schedule; the idea is that the extra computational effort required gives protection against dictionary attacks. See key strengthening.
In current implementations of cryptographic libraries (specifically OpenSSL), AES-128 is somewhat (< 50%) faster than Blowfish on most hardware[4]. It's likely that advances in CPU architecture (out of order execution becoming mainstream) sped up AES more than Blowfish. For example, Intel's in-order Atom CPU runs Blowfish twice as fast as AES-128[5]. There may be room for more optimization of Blowfish, but the Rijndael has received more attention since it was chosen for AES.
The belief that Blowfish is the fastest algorithm is widespread, although currently it's not true on mainstream PC hardware. It remains the case on some embedded CPUs (e.g. Atom, ARM[6]). Encryption speed is more likely to be a bottleneck on these slower systems, so Blowfish is certainly useful there. However, some platforms with such slow CPUs provide dedicated cryptography hardware, some of which only support the most popular algorithms (i.e. AES). Also, Intel's Westmere will add AES hardware support to mainstream PC CPUs.
Blowfish has a memory footprint of just over 4 kilobytes of RAM. This constraint is not a problem even for older desktop and laptop computers, though it does prevent use in the smallest embedded systems such as early smartcards.
Blowfish was one of the first secure block ciphers not subject to any patents and therefore freely available for anyone to use. This benefit has contributed to its popularity in cryptographic software.
See also
Notes and references
- ^ http://www.schneier.com/blowfish-bug.txt
- ^
Serge Vaudenay (1996). "On the Weak Keys of Blowfish" (PostScript). Retrieved 2006-08-23.
{{cite journal}}: Cite journal requires|journal=(help) - ^
Dahna, McConnachie (2007-12-27). "Bruce Almighty: Schneier preaches security to Linux faithful". Computerworld. p. 3. Retrieved 2007-12-31.
At this point, though, I'm amazed it's still being used. If people ask, I recommend Twofish instead.
{{cite web}}: More than one of|author=and|last=specified (help) - ^ The benchmarks posted at [1] include tests on non-x86 architectures.
- ^ [2]
- ^ [3]
- Vincent Rijmen, "Cryptanalysis and design of iterated block ciphers", doctoral dissertation, October 1997.
- Bruce Schneier, Description of a New Variable-Length Key, 64-bit Block Cipher (Blowfish). Fast Software Encryption 1993: 191–204 [5].
- Bruce Schneier, The Blowfish Encryption Algorithm -- One Year Later, Dr. Dobb's Journal, 20(9), p. 137, September 1995 [6].
- Serge Vaudenay, "On the weak keys of Blowfish," Fast Software Encryption (FSE'96), LNCS 1039, D. Gollmann, Ed., Springer-Verlag, 1996, pp. 27–32.
