The Sleuth Kit
This article has multiple issues. Please help improve it or discuss these issues on the talk page. (Learn how and when to remove these template messages)
|
 | |
| Original author(s) | Brian Carrier |
|---|---|
| Stable release | 4.6.2
/ August 9, 2018[1] |
| Repository | |
| Written in | C, Perl |
| Operating system | Unix-like, Windows |
| Type | Computer forensics |
| License | IPL, CPL, GPL |
| Website | www |
The Sleuth Kit (TSK) is a library and collection of Unix- and Windows-based utilities to facilitate the forensic analysis of computer systems. It was written and is maintained primarily by digital investigator Brian Carrier.[2]
The Sleuth Kit is capable of parsing NTFS, FAT/ExFAT, UFS 1/2, Ext2, Ext3, Ext4, HFS, ISO 9660 and YAFFS2 file systems either separately or within disk images stored in raw (dd), Expert Witness or AFF formats.[3] The Sleuth Kit can be used to examine most Microsoft Windows, most Apple Macintosh OSX, many Linux and some other UNIX computers.
The Sleuth Kit can be used:
- Via the included command line tools; or
- As a library embedded within a separate digital forensic tool such as Autopsy or log2timeline/plaso.
The Sleuth Kit is a free, open source suite that provides a large number of specialized command-line based utilities.
It is based on The Coroner's Toolkit, and is the official successor platform.[4]
Tools
Some of the tools included in The Sleuth Kit include:
- ils lists all metadata entries, such as an Inode.
- blkls displays data blocks within a file system (formerly called dls).
- fls lists allocated and unallocated file names within a file system.
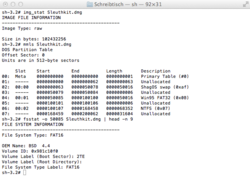
- fsstat displays file system statistical information about an image or storage medium.
- ffind searches for file names that point to a specified metadata entry.
- mactime creates a timeline of all files based upon their MAC times.
- disk_stat (currently Linux-only) discovers the existence of a Host Protected Area.
See also
- Autopsy (software) — A graphical user interface to The Sleuth Kit.
- CAINE Linux − Includes The Sleuth Kit
References
- ^ "Releases - sleuthkit/sleuthkit". Retrieved 12 September 2018 – via GitHub.
- ^ "About". www.sleuthkit.org. Brian Carrier. Retrieved 2016-08-30.
- ^ "File and Volume System Analysis". www.sleuthkit.org. Brian Carrier. Retrieved 2016-08-30.
- ^ http://www.porcupine.org/forensics/tct.html
External links
