Ghidra: Difference between revisions
m v2.05b - Bot T20 CW#61 - Fix errors for CW project (Reference before punctuation) |
m Add hyperlink free and open source Tags: Visual edit Mobile edit Mobile web edit |
||
| Line 34: | Line 34: | ||
}} |
}} |
||
'''Ghidra''' (pronounced GEE-druh;<ref>{{cite web |title=Frequently asked questions |url=https://github.com/NationalSecurityAgency/ghidra/wiki/Frequently-asked-questions#how-do-you-pronounce-ghidra |website=GitHub.com |accessdate=7 March 2019 |archive-date=5 March 2019 |archive-url=https://web.archive.org/web/20190305235545/https://github.com/NationalSecurityAgency/ghidra/wiki/Frequently-asked-questions#how-do-you-pronounce-ghidra |url-status=live }}</ref> {{IPAc-en|ˈ|ɡ|iː|d|r|ə|}}<ref>{{cite web |title=Come Get Your Free NSA Reverse Engineering Tool! |url=https://www.youtube.com/watch?v=r3N13ig8H7s&t=4 |archive-url=https://ghostarchive.org/varchive/youtube/20211215/r3N13ig8H7s |archive-date=2021-12-15 |url-status=live|website=YouTube.com |accessdate=17 May 2019}}{{cbignore}}</ref>) is a free and open source [[reverse engineering]] tool developed by the [[National Security Agency]] (NSA) of the United States. The binaries were released at [[RSA Conference]] in March 2019; the sources were published one month later on [[GitHub]].<ref name="wired release article">{{cite magazine |title=The NSA Makes Ghidra, a Powerful Cybersecurity Tool, Open Source |url=https://www.wired.com/story/nsa-ghidra-open-source-tool/ |magazine=Wired |accessdate=6 March 2019 |last1=Newman |first1=Lily Hay |archive-date=6 March 2019 |archive-url=https://web.archive.org/web/20190306095048/https://www.wired.com/story/nsa-ghidra-open-source-tool/ |url-status=live }}</ref> Ghidra is seen by many security researchers as a competitor to [[IDA Pro]].<ref name="Ghidra release">{{Cite web|url=https://www.zdnet.com/article/nsa-release-ghidra-a-free-software-reverse-engineering-toolkit/|title=NSA releases Ghidra, a free software reverse engineering toolkit|last=Cimpanu|first=Catalin|website=ZDNet|language=en|access-date=2019-03-07|archive-date=2019-03-06|archive-url=https://web.archive.org/web/20190306041159/https://www.zdnet.com/article/nsa-release-ghidra-a-free-software-reverse-engineering-toolkit/|url-status=live}}</ref> The software is written in [[Java (programming language)|Java]] using the [[Swing (Java)|Swing framework]] for the [[Graphical user interface|GUI]]. The [[decompiler]] component is written in [[C++]], and is therefore usable in a stand-alone form.<ref>e. g. as [https://rada.re/n/radare2.html Plugin] {{Webarchive|url=https://web.archive.org/web/20221014223153/https://rada.re/n/radare2.html |date=2022-10-14 }} for Radare2 oder Rizin.</ref> |
'''Ghidra''' (pronounced GEE-druh;<ref>{{cite web |title=Frequently asked questions |url=https://github.com/NationalSecurityAgency/ghidra/wiki/Frequently-asked-questions#how-do-you-pronounce-ghidra |website=GitHub.com |accessdate=7 March 2019 |archive-date=5 March 2019 |archive-url=https://web.archive.org/web/20190305235545/https://github.com/NationalSecurityAgency/ghidra/wiki/Frequently-asked-questions#how-do-you-pronounce-ghidra |url-status=live }}</ref> {{IPAc-en|ˈ|ɡ|iː|d|r|ə|}}<ref>{{cite web |title=Come Get Your Free NSA Reverse Engineering Tool! |url=https://www.youtube.com/watch?v=r3N13ig8H7s&t=4 |archive-url=https://ghostarchive.org/varchive/youtube/20211215/r3N13ig8H7s |archive-date=2021-12-15 |url-status=live|website=YouTube.com |accessdate=17 May 2019}}{{cbignore}}</ref>) is a [[free and open source]] [[reverse engineering]] tool developed by the [[National Security Agency]] (NSA) of the United States. The binaries were released at [[RSA Conference]] in March 2019; the sources were published one month later on [[GitHub]].<ref name="wired release article">{{cite magazine |title=The NSA Makes Ghidra, a Powerful Cybersecurity Tool, Open Source |url=https://www.wired.com/story/nsa-ghidra-open-source-tool/ |magazine=Wired |accessdate=6 March 2019 |last1=Newman |first1=Lily Hay |archive-date=6 March 2019 |archive-url=https://web.archive.org/web/20190306095048/https://www.wired.com/story/nsa-ghidra-open-source-tool/ |url-status=live }}</ref> Ghidra is seen by many security researchers as a competitor to [[IDA Pro]].<ref name="Ghidra release">{{Cite web|url=https://www.zdnet.com/article/nsa-release-ghidra-a-free-software-reverse-engineering-toolkit/|title=NSA releases Ghidra, a free software reverse engineering toolkit|last=Cimpanu|first=Catalin|website=ZDNet|language=en|access-date=2019-03-07|archive-date=2019-03-06|archive-url=https://web.archive.org/web/20190306041159/https://www.zdnet.com/article/nsa-release-ghidra-a-free-software-reverse-engineering-toolkit/|url-status=live}}</ref> The software is written in [[Java (programming language)|Java]] using the [[Swing (Java)|Swing framework]] for the [[Graphical user interface|GUI]]. The [[decompiler]] component is written in [[C++]], and is therefore usable in a stand-alone form.<ref>e. g. as [https://rada.re/n/radare2.html Plugin] {{Webarchive|url=https://web.archive.org/web/20221014223153/https://rada.re/n/radare2.html |date=2022-10-14 }} for Radare2 oder Rizin.</ref> |
||
Scripts to perform automated analysis with Ghidra can be written in Java or [[Python (programming language)|Python]] (via [[Jython]]),<ref>{{cite web|url=https://github.com/NationalSecurityAgency/ghidra/blob/master/GhidraDocs/GhidraClass/Intermediate/Scripting.html|title=Ghidra Scripting Class|website=[[GitHub]]|access-date=2023-02-19|archive-date=2023-02-20|archive-url=https://web.archive.org/web/20230220023138/https://github.com/NationalSecurityAgency/ghidra/blob/master/GhidraDocs/GhidraClass/Intermediate/Scripting.html|url-status=live}}</ref><ref>{{cite web|url=https://github.com/0xAlexei/INFILTRATE2019/blob/master/INFILTRATE%20Ghidra%20Slides.pdf|title=Three Heads are Better Than One: Mastering NSA's Ghidra Reverse Engineering Tool|website=[[GitHub]]|access-date=2019-09-30|archive-date=2020-03-01|archive-url=https://web.archive.org/web/20200301211705/https://github.com/0xAlexei/INFILTRATE2019/blob/master/INFILTRATE%20Ghidra%20Slides.pdf|url-status=live}}</ref> though this feature is extensible and support for other programming languages is available via community plugins.<ref>{{cite web|url=https://github.com/jpleasu/ghidraal|title=Ghidraal|website=[[GitHub]]|access-date=2023-02-19|archive-date=2023-02-20|archive-url=https://web.archive.org/web/20230220023155/https://github.com/jpleasu/ghidraal|url-status=live}}</ref> Plugins adding new features to Ghidra itself can be developed using a Java-based extension framework.<ref>{{cite web|url=https://github.com/NationalSecurityAgency/ghidra/blob/master/GhidraDocs/GhidraClass/AdvancedDevelopment/GhidraAdvancedDevelopment.html|title=Ghidra Advanced Development Class|website=[[GitHub]]|access-date=2023-02-19|archive-date=2023-02-20|archive-url=https://web.archive.org/web/20230220023139/https://github.com/NationalSecurityAgency/ghidra/blob/master/GhidraDocs/GhidraClass/AdvancedDevelopment/GhidraAdvancedDevelopment.html|url-status=live}}</ref> |
Scripts to perform automated analysis with Ghidra can be written in Java or [[Python (programming language)|Python]] (via [[Jython]]),<ref>{{cite web|url=https://github.com/NationalSecurityAgency/ghidra/blob/master/GhidraDocs/GhidraClass/Intermediate/Scripting.html|title=Ghidra Scripting Class|website=[[GitHub]]|access-date=2023-02-19|archive-date=2023-02-20|archive-url=https://web.archive.org/web/20230220023138/https://github.com/NationalSecurityAgency/ghidra/blob/master/GhidraDocs/GhidraClass/Intermediate/Scripting.html|url-status=live}}</ref><ref>{{cite web|url=https://github.com/0xAlexei/INFILTRATE2019/blob/master/INFILTRATE%20Ghidra%20Slides.pdf|title=Three Heads are Better Than One: Mastering NSA's Ghidra Reverse Engineering Tool|website=[[GitHub]]|access-date=2019-09-30|archive-date=2020-03-01|archive-url=https://web.archive.org/web/20200301211705/https://github.com/0xAlexei/INFILTRATE2019/blob/master/INFILTRATE%20Ghidra%20Slides.pdf|url-status=live}}</ref> though this feature is extensible and support for other programming languages is available via community plugins.<ref>{{cite web|url=https://github.com/jpleasu/ghidraal|title=Ghidraal|website=[[GitHub]]|access-date=2023-02-19|archive-date=2023-02-20|archive-url=https://web.archive.org/web/20230220023155/https://github.com/jpleasu/ghidraal|url-status=live}}</ref> Plugins adding new features to Ghidra itself can be developed using a Java-based extension framework.<ref>{{cite web|url=https://github.com/NationalSecurityAgency/ghidra/blob/master/GhidraDocs/GhidraClass/AdvancedDevelopment/GhidraAdvancedDevelopment.html|title=Ghidra Advanced Development Class|website=[[GitHub]]|access-date=2023-02-19|archive-date=2023-02-20|archive-url=https://web.archive.org/web/20230220023139/https://github.com/NationalSecurityAgency/ghidra/blob/master/GhidraDocs/GhidraClass/AdvancedDevelopment/GhidraAdvancedDevelopment.html|url-status=live}}</ref> |
||
Revision as of 20:07, 1 March 2024
 | |
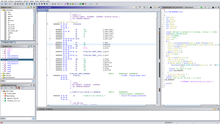 Disassembly of a file in Ghidra | |
| Original author(s) | NSA |
|---|---|
| Initial release | March 5, 2019 |
| Stable release | 11.0[1]
/ December 22, 2023 |
| Repository | github |
| Written in | Java, C++ |
| License | Apache License 2.0 / Public domain[2] |
| Website | ghidra-sre |
Ghidra (pronounced GEE-druh;[3] /ˈɡiːdrə/[4]) is a free and open source reverse engineering tool developed by the National Security Agency (NSA) of the United States. The binaries were released at RSA Conference in March 2019; the sources were published one month later on GitHub.[5] Ghidra is seen by many security researchers as a competitor to IDA Pro.[6] The software is written in Java using the Swing framework for the GUI. The decompiler component is written in C++, and is therefore usable in a stand-alone form.[7]
Scripts to perform automated analysis with Ghidra can be written in Java or Python (via Jython),[8][9] though this feature is extensible and support for other programming languages is available via community plugins.[10] Plugins adding new features to Ghidra itself can be developed using a Java-based extension framework.[11]
History
Ghidra's existence was originally revealed to the public via Vault 7 in March 2017,[12] but the software itself remained unavailable until its declassification and official release two years later.[5] Some comments in its source code indicates that it existed as least in 1999.[13]
In June 2019, Coreboot began to use Ghidra for its reverse engineering efforts on firmware-specific problems following the open source release of the Ghidra software suite.[14]
Ghidra can be used, officially,[15][16] as a debugger since Ghidra 10.0. Ghidra's debugger supports debugging user-mode Windows programs via WinDbg, and Linux programs via GDB.[17]
Supported architectures
The following architectures or binary formats are supported:[18] [19]
See also
References
- ^ "Releases · NationalSecurityAgency/ghidra". GitHub. Archived from the original on 2023-07-30. Retrieved 2023-12-22.
- ^ "ghidra/NOTICE". GitHub.com. Archived from the original on 27 October 2022. Retrieved 13 April 2019.
- ^ "Frequently asked questions". GitHub.com. Archived from the original on 5 March 2019. Retrieved 7 March 2019.
- ^ "Come Get Your Free NSA Reverse Engineering Tool!". YouTube.com. Archived from the original on 2021-12-15. Retrieved 17 May 2019.
- ^ a b Newman, Lily Hay. "The NSA Makes Ghidra, a Powerful Cybersecurity Tool, Open Source". Wired. Archived from the original on 6 March 2019. Retrieved 6 March 2019.
- ^ Cimpanu, Catalin. "NSA releases Ghidra, a free software reverse engineering toolkit". ZDNet. Archived from the original on 2019-03-06. Retrieved 2019-03-07.
- ^ e. g. as Plugin Archived 2022-10-14 at the Wayback Machine for Radare2 oder Rizin.
- ^ "Ghidra Scripting Class". GitHub. Archived from the original on 2023-02-20. Retrieved 2023-02-19.
- ^ "Three Heads are Better Than One: Mastering NSA's Ghidra Reverse Engineering Tool" (PDF). GitHub. Archived (PDF) from the original on 2020-03-01. Retrieved 2019-09-30.
- ^ "Ghidraal". GitHub. Archived from the original on 2023-02-20. Retrieved 2023-02-19.
- ^ "Ghidra Advanced Development Class". GitHub. Archived from the original on 2023-02-20. Retrieved 2023-02-19.
- ^ "NSA to release a free reverse engineering tool". ZDNET. Retrieved 2024-02-22.
- ^ "Build software better, together". GitHub. Retrieved 2024-02-22.
- ^ "Coreboot Project Is Leveraging NSA Software To Help With Firmware Reverse Engineering". Archived from the original on 2009-09-21. Retrieved 2019-06-05.
- ^ "Compiled/built Ghidra 9.3 for Windows with Debugger feature by Galician R&D Center in Advanced Telecommunications employees". Archived from the original on 2022-11-25. Retrieved 2022-11-25.
- ^ "Analizando el depurador de Ghidra". 11 March 2021. Archived from the original on 14 December 2022. Retrieved 14 December 2022.
- ^ "What's new in Ghidra 10.0". Archived from the original on 2023-06-19. Retrieved 2021-06-24.
- ^ "Rob Joyce on Twitter". Twitter.com. Archived from the original on 7 March 2019. Retrieved 6 March 2019.
- ^ "List of Processors Supported by Ghidra". Github.com. Archived from the original on 12 October 2023. Retrieved 29 September 2023.
External links
