SIM card: Difference between revisions
Removed irreverent and unlinked article Tags: section blanking Visual edit |
→Security: Section added with details of vulnerability |
||
| Line 177: | Line 177: | ||
| align="right" | <1.0 |
| align="right" | <1.0 |
||
|} |
|} |
||
== Security == |
|||
In July 2013 it was revealed that Karsten Nohl, a [[Cryptography|cryptographer]] and security researcher from SR Labs<ref>[http://www.golem.de/1108/85700.html Hacker sollen Kreditkarten freirubbeln], accessed 2013-07-22</ref><ref>[http://securitywatch.pcmag.com/mobile-security/313914-encryption-bug-in-sim-card-can-be-used-to-hack-millions-of-phones Encryption Bug in SIM Card Can be Used to Hack Millions of Phones], published 2013-07-21, accessed 2013-07-22</ref>, had discovered vulnerabilities in some SIM cards that enabled them to be hacked to provide [[Superuser|root access]].<ref name=SRLabsRootingSimCards>[https://srlabs.de/rooting-sim-cards/ Rooting SIM cards], SR Labs, accessed 2013-07-22</ref> The cards affected use the [[Data Encryption Standard]] (DES) which, despite its age, is still used by some operators.<ref name=SRLabsRootingSimCards /> Cards using the more recent [[Advanced Encryption Standard]] (AES) or [[Triple DES]] standards are not affected.<ref name=SRLabsRootingSimCards /> Among other risks the hack could lead to the being remotely [[Phone cloning|cloned]] or allow payment credentials from the SIM to be stolen.<ref name=SRLabsRootingSimCards /> Further details of the research are being given at [[Black Hat Briefings|BlackHat]] on July 31.<ref name=SRLabsRootingSimCards /><ref>[http://www.blackhat.com/us-13/briefings.html#Nohl BlackHat, accessed 2013-07-21</ref> |
|||
In response, the [[International Telecommunication Union]] said that the development was "hugely significant" and that it would be contacting its members.<ref>[http://www.reuters.com/article/2013/07/21/mobile-hacking-idUSL6N0FR0JD20130721 UPDATE 1-UN warns on mobile cybersecurity bugs in bid to prevent attacks], Reuters, 2013-07-21, accessed 2013-07-21</ref> |
|||
== Developments == |
== Developments == |
||
Revision as of 22:14, 22 July 2013
This article needs additional citations for verification. (June 2010) |


A subscriber identity module or subscriber identification module (SIM) is an integrated circuit that securely stores the international mobile subscriber identity (IMSI) and the related key used to identify and authenticate subscribers on mobile telephony devices (such as mobile phones and computers).
A SIM circuit is embedded into a removable plastic card. This plastic card is called a "SIM card" and can be transferred between different mobile devices. A SIM card follows certain smart card standards.[1] SIM cards were first made the same size as a credit card (85.60 mm × 53.98 mm × 0.76 mm). The development of physically smaller mobile devices prompted the development of a smaller SIM card, the mini-SIM card. Mini-SIM cards have the same thickness as full-size cards, but their length and width are reduced to 25 mm × 15 mm.
A SIM card contains its unique serial number (ICCID), international mobile subscriber identity (IMSI), security authentication and ciphering information, temporary information related to the local network, a list of the services the user has access to and two passwords: a personal identification number (PIN) for ordinary use and a personal unblocking code (PUK) for PIN unlocking.
History
The SIM was initially specified by the European Telecommunications Standards Institute in the specification with the number TS 11.11. This specification describes the physical and logical behaviour of the SIM. With the development of UMTS the specification work was partially transferred to 3GPP. 3GPP is now responsible for the further development of applications like SIM (TS 51.011) and USIM (TS 31.102) and ETSI for the further development of the physical card UICC.
The first SIM card was made in 1991 by Munich smart-card maker Giesecke & Devrient, who sold the first 300 SIM cards to the Finnish wireless network operator Radiolinja.[2][3]
Design
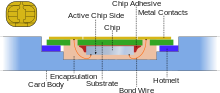
There are three operating voltages for SIM cards: 5 V, 3 V and 1.8 V (ISO/IEC 7816-3 classes A, B and C, respectively). The operating voltage of the majority of SIM cards launched before 1998 was 5 V. SIM cards produced subsequently are compatible with 3 V and 5 V. Modern cards support 5 V, 3 V and 1.8 V.
The microcontrollers used for SIM cards come in different configurations. The typical ROM size is between 64 KB and 512 KB, typical RAM size is between 1 KB and 8 KB, and typical EEPROM size is between 16 KB and 512 KB. The ROM contains the operating system of the card and might contain applets where the EEPROM contains the so-called personalization, which consists of security keys, phone book, SMS settings, etc., and operating system patches.
Modern SIM cards allow applications to be loaded when the SIM is in use by the subscriber. These applications communicate with the handset or a server using SIM application toolkit, which was initially specified by 3GPP in TS 11.14 (there is an identical ETSI specification with different numbering). ETSI and 3GPP maintain the SIM specifications; the main specifications are: ETSI TS 102 223, ETSI TS 102 241, ETSI TS 102 588, and ETSI TS 131 111. SIM toolkit applications were initially written in native code using proprietary APIs. In order to allow interoperability of the applications, Java Card was taken as the solution of choice by ETSI. Additional standards and specifications of interest are maintained by Global Platform.
Data
SIM cards store network-specific information used to authenticate and identify subscribers on the network. The most important of these are the ICCID, IMSI, Authentication Key (Ki), Local Area Identity (LAI) and Operator-Specific Emergency Number. The SIM also stores other carrier-specific data such as the SMSC (Short Message Service Center) number, Service Provider Name (SPN), Service Dialing Numbers (SDN), Advice-Of-Charge parameters and Value Added Service (VAS) applications. (Refer to GSM 11.11)
SIM cards can come in various data capacities, from 32 KB to at least 128 KB. All allow a maximum of 250 contacts to be stored on the SIM, but while the 32 KB has room for 33 Mobile Network Codes (MNCs) or "network identifiers", the 64 KB version has room for 80 MNCs.[citation needed] This is used by network operators to store information on preferred networks, mostly used when the SIM is not in its home market but is roaming. The network operator that issued the SIM card can use this to have a SIM card connect to a preferred network in order to make use of the best price and/or quality network instead of having to pay the network operator that the SIM card 'saw' first. This does not mean that a SIM card can only connect to a maximum of 33 or 80 networks, but this means that the SIM card issuer can only specify up to that number of preferred networks, if a SIM is outside these preferred networks it will use the first or best available network.
ICCID
Each SIM is internationally identified by its integrated circuit card identifier (ICCID). ICCIDs are stored in the SIM cards and are also engraved or printed on the SIM card body during a process called personalisation. The ICCID is defined by the ITU-T recommendation E.118 as the Primary Account Number.[4] Its layout is based on ISO/IEC 7812. According to E.118, the number is up to 19 digits long, including a single check digit calculated using the Luhn algorithm. However, the GSM Phase 1[5] defined the ICCID length as 10 octets (20 digits) with operator-specific structure.
The number is composed of the following subparts:
Issuer identification number (IIN)
Maximum of seven digits:
- Major industry identifier (MII), 2 fixed digits, 89 for telecommunication purposes.
- Country code, 1–3 digits, as defined by ITU-T recommendation E.164.
- Issuer identifier, 1–4 digits.
Individual account identification
- Individual account identification number. Its length is variable, but every number under one IIN will have the same length.
Check digit
- Single digit calculated from the other digits using the Luhn algorithm.
With the GSM Phase 1 specification using 10 octets into which ICCID is stored as packed BCD, the data field has room for 20 digits with hexadecimal digit "F" being used as filler when necessary.
In practice, this means that on GSM SIM cards there are 20-digit (19+1) and 19-digit (18+1) ICCIDs in use, depending upon the issuer. However, a single issuer always uses the same size for its ICCIDs.
To confuse matters more, SIM factories seem to have varying ways of delivering electronic copies of SIM personalization datasets. Some datasets are without the ICCID checksum digit, others are with the digit.
As required by E.118, The ITU regularly publishes a list of all internationally assigned IIN codes in its Operational Bulletins. The most recent list, as of June 2012, is in Operational Bulletin No. 1005
International mobile subscriber identity (IMSI)
SIM cards are identified on their individual operator networks by a unique International Mobile Subscriber Identity (IMSI). Mobile network operators connect mobile phone calls and communicate with their market SIM cards using their IMSIs. The format is:
- The first three digits represent the Mobile Country Code (MCC).
- The next two or three digits represent the Mobile Network Code (MNC). Three-digit MNC codes are allowed by E.212 but are mainly used in the United States and Canada.
- The next digits represent the Mobile Subscriber Identification Number (MSIN). Normally there will be 10 digits but would be fewer in the case of a 3-digit MNC or if national regulations indicate that the total length of the IMSI should be less than 15 digits.
Authentication key (Ki)
The Ki is a 128-bit value used in authenticating the SIMs on the mobile network. Each SIM holds a unique Ki assigned to it by the operator during the personalization process. The Ki is also stored in a database (termed authentication center or AuC) on the carrier's network.
The SIM card is designed not to allow the Ki to be obtained using the smart-card interface. Instead, the SIM card provides a function, Run GSM Algorithm, that allows the phone to pass data to the SIM card to be signed with the Ki. This, by design, makes usage of the SIM card mandatory unless the Ki can be extracted from the SIM card, or the carrier is willing to reveal the Ki. In practice, the GSM cryptographic algorithm for computing SRES_2 (see step 4, below) from the Ki has certain vulnerabilities[6] that can allow the extraction of the Ki from a SIM card and the making of a duplicate SIM card.
Authentication process:
- When the Mobile Equipment starts up, it obtains the International Mobile Subscriber Identity (IMSI) from the SIM card, and passes this to the mobile operator requesting access and authentication. The Mobile Equipment may have to pass a PIN to the SIM card before the SIM card will reveal this information.
- The operator network searches its database for the incoming IMSI and its associated Ki.
- The operator network then generates a Random Number (RAND, which is a nonce) and signs it with the Ki associated with the IMSI (and stored on the SIM card), computing another number known as Signed Response 1 (SRES_1).
- The operator network then sends the RAND to the Mobile Equipment, which passes it to the SIM card. The SIM card signs it with its Ki, producing SRES_2, which it gives to the Mobile Equipment along with encryption key Kc. The Mobile Equipment passes SRES_2 on to the operator network.
- The operator network then compares its computed SRES_1 with the computed SRES_2 that the Mobile Equipment returned. If the two numbers match, the SIM is authenticated and the Mobile Equipment is granted access to the operator's network. Kc is used to encrypt all further communications between the Mobile Equipment and the network.
Location area identity
The SIM stores network state information, which is received from the Location Area Identity (LAI). Operator networks are divided into Location Areas, each having a unique LAI number. When the device changes locations, it stores the new LAI to the SIM and sends it back to the operator network with its new location. If the device is power cycled, it will take data off the SIM, and search for the prior LAI.
SMS messages and contacts
Most SIM cards will orthogonally store a number of SMS messages and phone book contacts. The contacts are stored in simple "name and number" pairs: entries containing multiple phone numbers and additional phone numbers will usually not be stored on the SIM card. When a user tries to copy such entries to a SIM the handset's software will break them up into multiple entries, discarding any information that is not a phone number. The number of contacts and messages stored depends on the SIM; early models would store as few as five messages and 20 contacts while modern SIM cards can usually store over 250 contacts.[citation needed]
Formats



SIM cards have been made smaller over the years; functionality is independent of format. Full-size SIMs were followed by mini-SIMs, micro-SIMs, and nano-SIMs. SIMs are also made to be embedded in devices.
full-size SIM
The first to appear was the full-size or 1FF (1st form factor), the size of a credit card (85.60 mm × 53.98 mm × 0.76 mm).
mini-SIM
The mini-SIM card has the same contact arrangement as the full-size SIM card and is normally supplied within a full-size card carrier, attached by a number of linking pieces. This arrangement (defined in ISO/IEC 7810 as ID-1/000) allows such a card to be used in a device requiring a full-size card, or in a device requiring a mini-SIM card after breaking the linking pieces.
micro-SIM
The later 3FF card or micro-SIM cards have the same thickness and contact arrangements, but the length and width are further reduced as above.[7]
The micro-SIM was developed by the European Telecommunications Standards Institute (ETSI) along with SCP, 3GPP (UTRAN/GERAN), 3GPP2 (CDMA2000), ARIB, GSM Association (GSMA SCaG and GSMNA), GlobalPlatform, Liberty Alliance, and the Open Mobile Alliance (OMA) for the purpose of fitting into devices otherwise too small for a mini-SIM card.[8][9]
The form factor was mentioned in the December 1998 3GPP SMG9 UMTS Working Party, which is the standards-setting body for GSM SIM cards,[10] and the form factor was agreed upon in late 2003.[11]
The micro-SIM was created for backward compatibility. The major issue with backward compatibility was the contact area of the chip. Retaining the same contact area allows the micro-SIM to be compatible with the prior, larger SIM readers through the use of plastic cutout surrounds. The SIM was also designed to run at the same speed (5 MHz) as the prior version. The same size and positions of pins resulted in numerous "How-to" tutorials and YouTube video with detailed instructions how to cut a mini-SIM card to micro-SIM size with a sharp knife or scissors. These tutorials became very popular among first owners of iPad 3G after its release on April 30, 2010, and iPhone 4 on June 24, 2010.[12]
The chairman of EP SCP, Dr. Klaus Vedder, said[11]
- "With this decision, we can see that ETSI has responded to a market need from ETSI customers, but additionally there is a strong desire not to invalidate, overnight, the existing interface, nor reduce the performance of the cards. EP SCP expect to finalise the technical realisation for the third form factor at the next SCP plenary meeting, scheduled for February 2004."
The iPhone 4S, a minor revision of iPhone 4, as well as the Samsung Galaxy S3/S4, various Nokia Lumia handsets and the Nokia N9 used micro-sim cards.
nano-SIM
In early 2012, the nano-SIM or 4FF (4th form factor) was introduced, which measures 12.3 × 8.8 × 0.67 mm and reduces the previous format to the contact area while maintaining the existing contact arrangements.[13] A small rim of isolating material is left around the contact area to avoid short circuits with the socket. The 0.7 mm thickness of the nano-SIM is about 15 percent less than its predecessor.[14] 4FF can be put into adapters for use with devices taking 2FF or 3FF SIMs.[15]
Nano-SIM cards were used by iPhone 5.
Embedded-SIM
SIMs for M2M applications are available in a surface mount SON-8 package which may be soldered directly onto a circuit board.
The surface mount format provides the same electrical interface as the full size, 2FF and 3FF SIM cards, but is soldered to the circuit board as part of the manufacturing process. In M2M applications where there is no requirement to change the SIM card, this avoids the requirement for a connector, improving reliability and security.
Table of SIM cards
| SIM card | Introduced | Standard reference | Length (mm) | Width (mm) | Thickness (mm) |
|---|---|---|---|---|---|
| Full-size (FF) | 1991 | ISO/IEC 7810:2003, ID-1 | 85.60 | 53.98 | 0.76 |
| Mini-SIM (2FF) | late 1990s | ISO/IEC 7810:2003, ID-000 | 25.00 | 15.00 | 0.76 |
| Micro-SIM (3FF) | 2003 | ETSI TS 102 221 V9.0.0, Mini-UICC | 15.00 | 12.00 | 0.76 |
| Nano-SIM (4FF) | early 2012 | ETSI TS 102 221 V11.0.0 | 12.30 | 8.80 | 0.67 |
| Embedded-SIM | JEDEC Design Guide 4.8, SON-8 | 6.00 | 5.00 | <1.0 |
Security
In July 2013 it was revealed that Karsten Nohl, a cryptographer and security researcher from SR Labs[16][17], had discovered vulnerabilities in some SIM cards that enabled them to be hacked to provide root access.[18] The cards affected use the Data Encryption Standard (DES) which, despite its age, is still used by some operators.[18] Cards using the more recent Advanced Encryption Standard (AES) or Triple DES standards are not affected.[18] Among other risks the hack could lead to the being remotely cloned or allow payment credentials from the SIM to be stolen.[18] Further details of the research are being given at BlackHat on July 31.[18][19]
In response, the International Telecommunication Union said that the development was "hugely significant" and that it would be contacting its members.[20]
Developments
When GSM was already in use the specifications were further developed and enhanced with functionality like SMS, GPRS, etc. These development steps are referred as releases by ETSI. Within this development cycles the SIM specification was enhanced as well: new voltage classes, formats and files were introduced. In GSM-only times, the SIM consisted of the hardware and the software. With the advent of UMTS this naming was split: the SIM was now an application and hence only software. The hardware part was called UICC. This split was necessary because UMTS introduced a new application, the Universal Subscriber Identity Module (USIM). The USIM brought among other things security improvements like the mutual authentication and longer encryption keys and an improved address book.
"SIM cards" in developed countries are today usually UICCs containing at least a SIM and a USIM application. This configuration is necessary because older GSM only handsets are solely compatible with the SIM [application] and some UMTS security enhancements do rely on the USIM [application].
The equivalent of SIM on CDMA networks is the R-UIM (and the equivalent of USIM is CSIM).
A virtual SIM is a mobile phone number provided by a mobile network operator that does not require a SIM card to connect phone calls to a user's mobile phone.
Usage in mobile phone standards
The use of SIM cards is mandatory in GSM devices.
The satellite phone networks Iridium, Thuraya and Inmarsat's BGAN also use SIM cards. Sometimes these SIM cards work in regular GSM phones and also allow GSM customers to roam in satellite networks by using their own SIM card in a satellite phone.
Japan's 2G PDC system (which was shut down in 2012; SoftBank Mobile has already shut down PDC from March 31, 2010) also specifies a SIM, but this has never been implemented commercially. The specification of the interface between the Mobile Equipment and the SIM is given in the RCR STD-27 annex 4. The Subscriber Identity Module Expert Group was a committee of specialists assembled by the European Telecommunications Standards Institute (ETSI) to draw up the specifications (GSM 11.11) for interfacing between smart cards and mobile telephones. In 1994, the name SIMEG was changed to SMG9.
Japan's current and next generation cellular systems are based on W-CDMA (UMTS) and CDMA2000 and all use SIM cards, however Japanese CDMA2000-based phones are locked to the R-UIM they are associated with and thus the cards are not interchangeable with other Japanese CDMA2000 handsets (though they may be inserted into GSM/WCDMA handsets for roaming purposes outside Japan).
CDMA-based devices originally did not use a removable card, and the service for these phones bound to a unique identifier contained in the handset itself. This is most prevalent in operators in the Americas. The first publication of the TIA-820 standard (also known as 3GPP2 C.S0023) in 2000 defined the Removable User Identity Module (R-UIM). Card-based CDMA devices are most prevalent in Asia.
The equivalent of a SIM in UMTS is called the Universal Integrated Circuit Card (UICC), which runs a USIM application. The UICC is still colloquially called a SIM card.[citation needed]
-
SIM card for Thuraya satellite phone
-
NTT DoCoMo's FOMA Card
-
UMTS modem with SIM card
-
SIM card and the mobile phone
-
Three UK SIM Card with Packaging
SIM and carriers
The SIM card introduced a new and significant business opportunity for MVNOs - mobile virtual network operators - who lease capacity from one of the network operators rather than owning or operating a cellular telecoms network, and only provide a SIM card to their customers. MVNOs first appeared in Denmark, Hong Kong, Finland and the UK.[when?] Today[when?] they exist in over 50 countries, including most of Europe, United States, Canada, Australia and parts of Asia, and account for approximately 10% of all mobile phone subscribers around the world.
On some networks, the mobile phone is locked to its carrier SIM card, meaning that the phone only works with SIM cards from the specific carrier. This is more common in markets where mobile phones are heavily subsidised by the carriers, and the business model depends on the customer staying with the service provider for a minimum term (typically 12 or 24 months). SIM cards that are issued by providers with an associated contract are called Sim only deals. Common examples are the GSM networks in the United States, Canada, Australia, the UK and Poland. Many businesses offer the ability to remove the SIM lock from a phone, effectively making it possible to then use the phone on any network by inserting a different SIM card. Mostly, GSM and 3G mobile handsets can easily be unlocked and used on any suitable network with any SIM card.
In countries where the phones are not subsidised, e.g., India and Belgium, all phones are unlocked. Where the phone is not locked to its SIM card, the users can easily switch networks by simply replacing the SIM card of one network with that of another while using only one phone. This is typical, for example, among users who may want to optimise their carrier's traffic by different tariffs to different friends on different networks, or when traveling internationally.
See also
- International Mobile Equipment Identity (IMEI)
- GSM 03.48
- SIM cloning
- SIM connector
- IP Multimedia Services Identity Module (ISIM)
- W-SIM (Willcom-SIM)
- Mobile equipment identifier (MEID)
- VMAC
- Mobile signature
- Single Wire Protocol (SWP)
- SIM Application Toolkit (STK)
- Mobile broadband
- Tethering
- Smart card
References
- ^ "Types of Smart Card". Smart Card Basics. CardLogix Corporation / evolis / SCM Microsystems. Dynamic Application Card Operating System (section). Retrieved 15 July 2013.
- ^ Asif, Saad Z. (2011). Next Generation Mobile Communications Ecosystem. John Wiley & Sons. p. 306. ISBN 1119995817.
- ^ History of Giesecke & Devrient
- ^ ITU-T, ITU-T Recommendation E.118, The international telecommunication charge card, Revision history, Revision "05/2006"
- ^ ETSI, ETSI Recommendation GSM 11.11, Specifications of the SIM-ME Interface, Version 3.16.0
- ^ "Hackers crack open mobile network". bbc.co.uk. 20 April 2011. Retrieved 13 August 2011.
- ^ "What is a microsim card?". SimOnlyPro.nl. Retrieved 14 October 2012.
- ^ Gaby Lenhart (1 April 2006). "The Smart Card Platform". ETSI Technical Committee Smart Card Platform (TB SCP). Retrieved 30 January 2010.
SCP is co-operating on both technical and service aspects with a number of other committees both within and outside the telecommunications sector.
- ^ Segan, Sascha (27 January 2010). "Inside the iPad Lurks the 'Micro SIM'". PC Magazine. Retrieved 30 January 2010.
- ^ "DRAFT Report of the SMG9 UMTS Working Party, meeting #7 hosted by Nokia in Copenhagen, 15–16 December 1998" (PDF). 3GPP. 25 January 1999. Retrieved 27 January 2010.
One manufacturer stated that it may be difficult to meeting ISO mechanical standards for a combined ID-1/micro-SIM card.
- ^ a b Antipolis, Sophia (8 December 2003). "New form factor for smart cards introduced". SmartCard Trends. Retrieved 30 January 2010.
The work item for the so-called Third Form Factor, "3FF", was agreed, after intensive discussions, at the SCP meeting held last week in London.
- ^ How to make MicroSIM on YouTube
- ^ "What is a nano SIM?". Simonly Internet. Retrieved 29 September 2012.
- ^ "Nano-SIM - The smallest SIM form factor on the market" (PDF). Giesecke & Devrient. 27 January 2012. p. 1. Retrieved 23 July 2012.
- ^ Dr. Klaus Vedder (18 January 2012). "The UICC – Recent Work of ETSI TC Smart Card Platform" (PDF). ETSI. p. 12. Retrieved 22 July 2012.
- ^ Hacker sollen Kreditkarten freirubbeln, accessed 2013-07-22
- ^ Encryption Bug in SIM Card Can be Used to Hack Millions of Phones, published 2013-07-21, accessed 2013-07-22
- ^ a b c d e Rooting SIM cards, SR Labs, accessed 2013-07-22
- ^ [http://www.blackhat.com/us-13/briefings.html#Nohl BlackHat, accessed 2013-07-21
- ^ UPDATE 1-UN warns on mobile cybersecurity bugs in bid to prevent attacks, Reuters, 2013-07-21, accessed 2013-07-21
External links
- ETSI Smart Card standards (102 221)
- GSM 11.11 – Specification of the Subscriber Identity Module – Mobile Equipment (SIM-ME) interface.
- GSM 11.14 – Specification of the SIM Application Toolkit for the Subscriber Identity Module – Mobile Equipment (SIM-ME) interface
- GSM 03.48 – Specification of the security mechanisms for SIM application toolkit
- GSM 03.48 Java API – API and realization of GSM 03.48 in Java
- ITU-T E.118 – The International Telecommunication Charge Card 2006 ITU-T






