Quantum computing: Difference between revisions
→Potential: embarrassing typo |
→Potential: this doesn't compute: this section's about the potential *if* large quantum computers existed, and if they did, longer RSA keys would only increase attacker's effort polynomially |
||
| Line 48: | Line 48: | ||
==Potential== |
==Potential== |
||
[[Integer factorization]] is believed to be computationally infeasible with an ordinary computer for large integers that are the product of only a few [[prime number]]s (e.g., products of two 300-digit primes).<ref>[http://modular.fas.harvard.edu/edu/Fall2001/124/misc/arjen_lenstra_factoring.pdf Integer Factoring] By ARJEN K. LENSTRA - Designs, Codes and Cryptography, 19, 101–128 (2000) Kluwer Academic Publishers</ref> By comparison, a quantum computer could efficiently solve this problem using [[Shor's algorithm]] to find its factors. This ability would allow a quantum computer to decrypt many of the [[cryptography|cryptographic]] systems in use today, in the sense that there would be a [[polynomial time]] (in the number of digits of the integer) algorithm for solving the problem. In particular, most of the popular [[Asymmetric Algorithms|public key ciphers]] are based on the difficulty of factoring integers (or the related [[discrete logarithm]] problem which can also be solved by Shor's algorithm), including forms of [[RSA]]. These are used to protect secure Web pages, encrypted email, and many other types of data. Breaking these would have significant ramifications for electronic privacy and security. |
[[Integer factorization]] is believed to be computationally infeasible with an ordinary computer for large integers that are the product of only a few [[prime number]]s (e.g., products of two 300-digit primes).<ref>[http://modular.fas.harvard.edu/edu/Fall2001/124/misc/arjen_lenstra_factoring.pdf Integer Factoring] By ARJEN K. LENSTRA - Designs, Codes and Cryptography, 19, 101–128 (2000) Kluwer Academic Publishers</ref> By comparison, a quantum computer could efficiently solve this problem using [[Shor's algorithm]] to find its factors. This ability would allow a quantum computer to decrypt many of the [[cryptography|cryptographic]] systems in use today, in the sense that there would be a [[polynomial time]] (in the number of digits of the integer) algorithm for solving the problem. In particular, most of the popular [[Asymmetric Algorithms|public key ciphers]] are based on the difficulty of factoring integers (or the related [[discrete logarithm]] problem which can also be solved by Shor's algorithm), including forms of [[RSA]]. These are used to protect secure Web pages, encrypted email, and many other types of data. Breaking these would have significant ramifications for electronic privacy and security. |
||
However, other existing cryptographic algorithms don't appear to be broken by these algorithms.<ref name="pqcrypto_survey">Daniel J. Bernstein, [http://pqcrypto.org/www.springer.com/cda/content/document/cda_downloaddocument/9783540887010-c1.pdf Introduction to Post-Quantum Cryptography]. Introduction to Daniel J. Bernstein, Johannes Buchmann, Erik Dahmen (editors). Post-quantum cryptography. Springer, Berlin, 2009. ISBN 978-3-540-88701-0</ref><ref>See also [http://pqcrypto.org/ pqcrypto.org], a bibliography maintained by Daniel J. Bernstein and Tanja Lange on cryptography not known to be broken by quantum computing.</ref> Some public-key algorithms are based on problems other than the integer factorization and discrete logarithm problems to which Shor's algorithm applies, like the [[McEliece cryptosystem]] based on a problem in [[coding theory]].<ref name="pqcrypto_survey" /><ref>Robert J. McEliece. "[http://ipnpr.jpl.nasa.gov/progress_report2/42-44/44N.PDF A public-key cryptosystem based on algebraic coding theory]." Jet Propulsion Laboratory DSN Progress Report 42–44, 114–116.</ref> It has been proven that applying Grover's algorithm to break a [[Symmetric cryptography|symmetric (secret key) algorithm]] by brute force requires roughly 2<sup>n/2</sup> invocations of the underlying cryptographic algorithm, compared with roughly 2<sup>n</sup> in the classical case,<ref name=bennett_1997>Bennett C.H., Bernstein E., Brassard G., Vazirani U., ''[http://www.cs.berkeley.edu/~vazirani/pubs/bbbv.ps The strengths and weaknesses of quantum computation]''. [[SIAM Journal on Computing]] 26(5): 1510-1523 (1997).</ref> meaning that symmetric key lengths are effectively halved: AES-256 would have the same security by a quantum computer that AES-128 has against a classical computer (see [[Key_size#Effect_of_quantum_computing_attacks_on_key_strength|Key size]]). [[Quantum cryptography]] could potentially fulfill some of the functions of public key cryptography. |
However, other existing cryptographic algorithms don't appear to be broken by these algorithms.<ref name="pqcrypto_survey">Daniel J. Bernstein, [http://pqcrypto.org/www.springer.com/cda/content/document/cda_downloaddocument/9783540887010-c1.pdf Introduction to Post-Quantum Cryptography]. Introduction to Daniel J. Bernstein, Johannes Buchmann, Erik Dahmen (editors). Post-quantum cryptography. Springer, Berlin, 2009. ISBN 978-3-540-88701-0</ref><ref>See also [http://pqcrypto.org/ pqcrypto.org], a bibliography maintained by Daniel J. Bernstein and Tanja Lange on cryptography not known to be broken by quantum computing.</ref> Some public-key algorithms are based on problems other than the integer factorization and discrete logarithm problems to which Shor's algorithm applies, like the [[McEliece cryptosystem]] based on a problem in [[coding theory]].<ref name="pqcrypto_survey" /><ref>Robert J. McEliece. "[http://ipnpr.jpl.nasa.gov/progress_report2/42-44/44N.PDF A public-key cryptosystem based on algebraic coding theory]." Jet Propulsion Laboratory DSN Progress Report 42–44, 114–116.</ref> It has been proven that applying Grover's algorithm to break a [[Symmetric cryptography|symmetric (secret key) algorithm]] by brute force requires roughly 2<sup>n/2</sup> invocations of the underlying cryptographic algorithm, compared with roughly 2<sup>n</sup> in the classical case,<ref name=bennett_1997>Bennett C.H., Bernstein E., Brassard G., Vazirani U., ''[http://www.cs.berkeley.edu/~vazirani/pubs/bbbv.ps The strengths and weaknesses of quantum computation]''. [[SIAM Journal on Computing]] 26(5): 1510-1523 (1997).</ref> meaning that symmetric key lengths are effectively halved: AES-256 would have the same security by a quantum computer that AES-128 has against a classical computer (see [[Key_size#Effect_of_quantum_computing_attacks_on_key_strength|Key size]]). [[Quantum cryptography]] could potentially fulfill some of the functions of public key cryptography. |
||
Revision as of 22:28, 17 March 2010
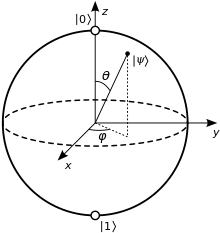
A quantum computer is a device for computation that makes direct use of quantum mechanical phenomena, such as superposition and entanglement, to perform operations on data. The basic principle behind quantum computation is that quantum properties can be used to represent data and perform operations on these data.[1] A theoretical model is the quantum Turing machine, also known as the universal quantum computer.
Although quantum computing is still in its infancy, experiments have been carried out in which quantum computational operations were executed on a very small number of qubits (quantum bit). Both practical and theoretical research continues with interest, and many national government and military funding agencies support quantum computing research to develop quantum computers for both civilian and national security purposes, such as cryptanalysis.[2]
If large-scale quantum computers can be built, they will be able to solve certain problems much faster than any current classical computers (for example Shor's algorithm). Quantum computers are different from other computers such as DNA computers and traditional computers based on transistors. Some computing architectures such as optical computers[3] may use classical superposition of electromagnetic waves. Without some specifically quantum mechanical resources such as entanglement, it is conjectured that an exponential advantage over classical computers is not possible.[4] Quantum computers however do not allow one to compute functions that are not theoretically computable by classical computers, i.e. they do not alter the Church–Turing thesis. The gain is only in efficiency.
Basis
A classical computer has a memory made up of bits, where each bit represents either a one or a zero. A quantum computer maintains a sequence of qubits. A single qubit can represent a one, a zero, or, crucially, any quantum superposition of these; moreover, a pair of qubits can be in any quantum superposition of 4 states, and three qubits in any superposition of 8. In general a quantum computer with qubits can be in an arbitrary superposition of up to different states simultaneously (this compares to a normal computer that can only be in one of these states at any one time). A quantum computer operates by manipulating those qubits with a fixed sequence of quantum logic gates. The sequence of gates to be applied is called a quantum algorithm.
An example of an implementation of qubits for a quantum computer could start with the use of particles with two spin states: "down" and "up" (typically written and , or and ). But in fact any system possessing an observable quantity A which is conserved under time evolution and such that A has at least two discrete and sufficiently spaced consecutive eigenvalues, is a suitable candidate for implementing a qubit. This is true because any such system can be mapped onto an effective spin-1/2 system.
Bits vs. qubits

Consider first a classical computer that operates on a three-bit register. The state of the computer at any time is a probability distribution over the different three-bit strings 000, 001, 010, 011, 100, 101, 110, 111. If it is a deterministic computer, then it is in exactly one of these states with probability 1. However, if it is a probabilistic computer, then there is a possibility of it being in any one of a number of different states. We can describe this probabilistic state by eight nonnegative numbers a,b,c,d,e,f,g,h (where a = probability computer is in state 000, b = probability computer is in state 001, etc.). There is a restriction that these probabilities sum to 1.
The state of a three-qubit quantum computer is similarly described by an eight-dimensional vector (a,b,c,d,e,f,g,h), called a ket. However, instead of adding to one, the sum of the squares of the coefficient magnitudes, , must equal one. Moreover, the coefficients are complex numbers. Since states are represented by complex wavefunctions, two states being added together will undergo interference. This is a key difference between quantum computing and probabilistic classical computing.[6]
If you measure the three qubits, then you will observe a three-bit string. The probability of measuring a string will equal the squared magnitude of that string's coefficients (using our example, probability that we read state as 000 = , probability that we read state as 001 = , etc..). Thus a measurement of the quantum state with coefficients (a,b,...,h) gives the classical probability distribution . We say that the quantum state "collapses" to a classical state.
Note that an eight-dimensional vector can be specified in many different ways, depending on what basis you choose for the space. The basis of three-bit strings 000, 001, ..., 111 is known as the computational basis, and is often convenient, but other bases of unit-length, orthogonal vectors can also be used. Ket notation is often used to make explicit the choice of basis. For example, the state (a,b,c,d,e,f,g,h) in the computational basis can be written as
- , where, e.g., = (0,0,1,0,0,0,0,0).
The computational basis for a single qubit (two dimensions) is = (1,0), = (0,1), but another common basis are the eigenvectors of the Pauli-x operator: and .
Note that although recording a classical state of n bits, a 2n-dimensional probability distribution, requires an exponential number of real numbers, practically we can always think of the system as being exactly one of the n-bit strings—we just don't know which one. Quantum mechanically, this is not the case, and all 2n complex coefficients need to be kept track of to see how the quantum system evolves. For example, a 300-qubit quantum computer has a state described by 2300 (approximately 1090) complex numbers, more than the number of atoms in the observable universe.
Operation
While a classical three-bit state and a quantum three-qubit state are both eight-dimensional vectors, they are manipulated quite differently for classical or quantum computation. For computing in either case, the system must be initialized, for example into the all-zeros string, , corresponding to the vector (1,0,0,0,0,0,0,0). In classical randomized computation, the system evolves according to the application of stochastic matrices, which preserve that the probabilities add up to one (i.e., preserve the L1 norm). In quantum computation, on the other hand, allowed operations are unitary matrices, which are effectively rotations (they preserve that the sum of the squares add up to one, the Euclidean or L2 norm). (Exactly what unitaries can be applied depend on the physics of the quantum device.) Consequently, since rotations can be undone by rotating backward, quantum computations are reversible. (Technically, quantum operations can be probabilistic combinations of unitaries, so quantum computation really does generalize classical computation. See quantum circuit for a more precise formulation.)
Finally, upon termination of the algorithm, the result needs to be read off. In the case of a classical computer, we sample from the probability distribution on the three-bit register to obtain one definite three-bit string, say 000. Quantum mechanically, we measure the three-qubit state, which is equivalent to collapsing the quantum state down to a classical distribution (with the coefficients in the classical state being the squared magnitudes of the coefficients for the quantum state, as described above) followed by sampling from that distribution. Note that this destroys the original quantum state. Many algorithms will only give the correct answer with a certain probability, however by repeatedly initializing, running and measuring the quantum computer, the probability of getting the correct answer can be increased.
For more details on the sequences of operations used for various quantum algorithms, see universal quantum computer, Shor's algorithm, Grover's algorithm, Deutsch-Jozsa algorithm, amplitude amplification, quantum Fourier transform, quantum gate, quantum adiabatic algorithm and quantum error correction.
Potential
Integer factorization is believed to be computationally infeasible with an ordinary computer for large integers that are the product of only a few prime numbers (e.g., products of two 300-digit primes).[7] By comparison, a quantum computer could efficiently solve this problem using Shor's algorithm to find its factors. This ability would allow a quantum computer to decrypt many of the cryptographic systems in use today, in the sense that there would be a polynomial time (in the number of digits of the integer) algorithm for solving the problem. In particular, most of the popular public key ciphers are based on the difficulty of factoring integers (or the related discrete logarithm problem which can also be solved by Shor's algorithm), including forms of RSA. These are used to protect secure Web pages, encrypted email, and many other types of data. Breaking these would have significant ramifications for electronic privacy and security.
However, other existing cryptographic algorithms don't appear to be broken by these algorithms.[8][9] Some public-key algorithms are based on problems other than the integer factorization and discrete logarithm problems to which Shor's algorithm applies, like the McEliece cryptosystem based on a problem in coding theory.[8][10] It has been proven that applying Grover's algorithm to break a symmetric (secret key) algorithm by brute force requires roughly 2n/2 invocations of the underlying cryptographic algorithm, compared with roughly 2n in the classical case,[11] meaning that symmetric key lengths are effectively halved: AES-256 would have the same security by a quantum computer that AES-128 has against a classical computer (see Key size). Quantum cryptography could potentially fulfill some of the functions of public key cryptography.
Besides factorization and discrete logarithms, quantum algorithms offering a more than polynomial speedup over the best known classical algorithm have been found for several problems,[12] including the simulation of quantum physical processes from chemistry and solid state physics, the approximation of Jones polynomials, and solving Pell's equation. No mathematical proof has been found that shows that an equally fast classical algorithm cannot be discovered, although this is considered unlikely. For some problems, quantum computers offer a polynomial speedup. The most well-known example of this is quantum database search, which can be solved by Grover's algorithm using quadratically fewer queries to the database than are required by classical algorithms. In this case the advantage is provable. Several other examples of provable quantum speedups for query problems have subsequently been discovered, such as for finding collisions in two-to-one functions and evaluating NAND trees.
Consider a problem that has these four properties:
- The only way to solve it is to guess answers repeatedly and check them,
- There are n possible answers to check,
- Every possible answer takes the same amount of time to check, and
- There are no clues about which answers might be better: generating possibilities randomly is just as good as checking them in some special order.
An example of this is a password cracker that attempts to guess the password for an encrypted file (assuming that the password has a maximum possible length).
For problems with all four properties, the time for a quantum computer to solve this will be proportional to the square root of n. That can be a very large speedup, reducing some problems from years to seconds. It can be used to attack symmetric ciphers such as Triple DES and AES by attempting to guess the secret key. Regardless of whether any of these problems can be shown to have an advantage on a quantum computer, they nonetheless will always have the advantage of being an excellent tool for studying quantum mechanical interactions, which of itself is an enormous value to the scientific community.
Grover's algorithm can also be used to obtain a quadratic speed-up [over a brute-force search] for a class of problems known as NP-complete.
Since chemistry and nanotechnology rely on understanding quantum systems, and such systems are impossible to simulate in an efficient manner classically, many believe quantum simulation will be one of the most important applications of quantum computing.[13]
There are a number of practical difficulties in building a quantum computer, and thus far quantum computers have only solved trivial problems. David DiVincenzo, of IBM, listed the following requirements for a practical quantum computer:[14]
- scalable physically to increase the number of qubits;
- qubits can be initialized to arbitrary values;
- quantum gates faster than decoherence time;
- universal gate set;
- qubits can be read easily.
Quantum decoherence
One of the greatest challenges is controlling or removing quantum decoherence. This usually means isolating the system from its environment as the slightest interaction with the external world would cause the system to decohere. This effect is irreversible, as it is non-unitary, and is usually something that should be avoided, if not highly controlled. Decoherence times for candidate systems, in particular the transverse relaxation time T2 (for NMR and MRI technology, also called the dephasing time), typically range between nanoseconds and seconds at low temperature.[6]
These issues are more difficult for optical approaches as the timescales are orders of magnitude lower and an often cited approach to overcoming them is optical pulse shaping. Error rates are typically proportional to the ratio of operating time to decoherence time, hence any operation must be completed much more quickly than the decoherence time.
If the error rate is small enough, it is thought to be possible to use quantum error correction, which corrects errors due to decoherence, thereby allowing the total calculation time to be longer than the decoherence time. An often cited figure for required error rate in each gate is 10−4. This implies that each gate must be able to perform its task in one 10,000th of the decoherence time of the system.
Meeting this scalability condition is possible for a wide range of systems. However, the use of error correction brings with it the cost of a greatly increased number of required qubits. The number required to factor integers using Shor's algorithm is still polynomial, and thought to be between L and L2, where L is the number of bits in the number to be factored; error correction algorithms would inflate this figure by an additional factor of L. For a 1000-bit number, this implies a need for about 104 qubits without error correction.[15] With error correction, the figure would rise to about 107 qubits. Note that computation time is about or about steps and on 1 MHz, about 10 seconds.
A very different approach to the stability-decoherence problem is to create a topological quantum computer with anyons, quasi-particles used as threads and relying on braid theory to form stable logic gates.[16][17]
Developments
There are a number of quantum computing candidates, among those:
- Superconductor-based quantum computers (including SQUID-based quantum computers)[18]
- Trapped ion quantum computer
- Optical lattices
- Topological quantum computer[19]
- Quantum dot on surface (e.g. the Loss-DiVincenzo quantum computer)
- Nuclear magnetic resonance on molecules in solution (liquid NMR)
- Solid state NMR Kane quantum computers
- Electrons on helium quantum computers
- Cavity quantum electrodynamics (CQED)
- Molecular magnet
- Fullerene-based ESR quantum computer
- Optic-based quantum computers (Quantum optics)
- Diamond-based quantum computer[20][21][22]
- Bose–Einstein condensate-based quantum computer[23]
- Transistor-based quantum computer - string quantum computers with entrainment of positive holes using an electrostatic trap
- Spin-based quantum computer
- Adiabatic quantum computation[24]
- Rare-earth-metal-ion-doped inorganic crystal based quantum computers[25][26]
The large number of candidates shows explicitly that the topic, in spite of rapid progress, is still in its infancy. But at the same time there is also a vast amount of flexibility.
In 2005, researchers at the University of Michigan built a semiconductor chip which functioned as an ion trap. Such devices, produced by standard lithography techniques, may point the way to scalable quantum computing tools.[27] An improved version was made in 2006.[citation needed]
In 2009, researchers at Yale University created the first rudimentary solid-state quantum processor. The two-qubit superconducting chip was able to run elementary algorithms. Each of the two artificial atoms (or qubits) were made up of a billion aluminum atoms but they acted like a single one that could occupy two different energy states.[28][29]
Another team, working at the University of Bristol, also created a silicon-based quantum computing chip, based on quantum optics. The team was able to run Shor's algorithm on the chip.[30]
Relation to computational complexity theory
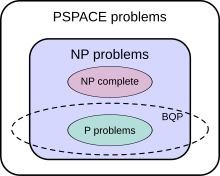
The class of problems that can be efficiently solved by quantum computers is called BQP, for "bounded error, quantum, polynomial time". Quantum computers only run probabilistic algorithms, so BQP on quantum computers is the counterpart of BPP on classical computers. It is defined as the set of problems solvable with a polynomial-time algorithm, whose probability of error is bounded away from one half.[31] A quantum computer is said to "solve" a problem if, for every instance, its answer will be right with high probability. If that solution runs in polynomial time, then that problem is in BQP.
BQP is contained in the complexity class #P (or more precisely in the associated class of decision problems P#P),[32] which is a subclass of PSPACE.
BQP is suspected to be disjoint from NP-complete and a strict superset of P, but that is not known. Both integer factorization and discrete log are in BQP. Both of these problems are NP problems suspected to be outside BPP, and hence outside P. Both are suspected to not be NP-complete. There is a common misconception that quantum computers can solve NP-complete problems in polynomial time. That is not known to be true, and is generally suspected to be false.[32]
Although quantum computers may be faster than classical computers, those described above can't solve any problems that classical computers can't solve, given enough time and memory (however, those amounts might be practically infeasible). A Turing machine can simulate these quantum computers, so such a quantum computer could never solve an undecidable problem like the halting problem. The existence of "standard" quantum computers does not disprove the Church–Turing thesis.[31][page needed] It has been speculated that theories of quantum gravity, such as M-theory or loop quantum gravity, may allow even faster computers to be built. Currently, it's an open problem to even define computation in such theories due to the problem of time, i.e. there's no obvious way to describe what it means for an observer to submit input to a computer and later receive output.[33]
See also
- Timeline of quantum computing
- Quantum bus
- Chemical computer
- DNA computer
- Molecular computer
- List of emerging technologies
References
- ^ "Quantum Computing with Molecules" article in Scientific American by Neil Gershenfeld and Isaac L. Chuang - a generally accessible overview of quantum computing and so on.
- ^ Quantum Information Science and Technology Roadmap for a sense of where the research is heading.
- ^ One photon Grover algorithm
- ^
Lieven M.K. Vandersypen; et al. (1999). "Separability of Very Noisy Mixed States and Implications for NMR Quantum Computing". Phys. Rev. Lett. 83: 1054–1057. doi:10.1103/PhysRevLett.83.1054.
{{cite journal}}: Explicit use of et al. in:|author=(help) - ^ Waldner, Jean-Baptiste (2007). Nanocomputers and Swarm Intelligence. London: ISTE. p. 157. ISBN 2746215160.
- ^ a b David P. DiVincenzo (1995). "Quantum Computation". Science. 270 (5234): 255–261. doi:10.1126/science.270.5234.255.
- ^ Integer Factoring By ARJEN K. LENSTRA - Designs, Codes and Cryptography, 19, 101–128 (2000) Kluwer Academic Publishers
- ^ a b Daniel J. Bernstein, Introduction to Post-Quantum Cryptography. Introduction to Daniel J. Bernstein, Johannes Buchmann, Erik Dahmen (editors). Post-quantum cryptography. Springer, Berlin, 2009. ISBN 978-3-540-88701-0
- ^ See also pqcrypto.org, a bibliography maintained by Daniel J. Bernstein and Tanja Lange on cryptography not known to be broken by quantum computing.
- ^ Robert J. McEliece. "A public-key cryptosystem based on algebraic coding theory." Jet Propulsion Laboratory DSN Progress Report 42–44, 114–116.
- ^ Bennett C.H., Bernstein E., Brassard G., Vazirani U., The strengths and weaknesses of quantum computation. SIAM Journal on Computing 26(5): 1510-1523 (1997).
- ^ Quantum Algorithm Zoo - Stephen Jordan's Homepage
- ^ The Father of Quantum Computing By Quinn Norton 02.15.2007, Wired.com
- ^ David P. DiVincenzo, IBM (2000-04-13). "The Physical Implementation of Quantum Computation". Retrieved 2006-11-17.
- ^ M. I. Dyakonov, Université Montpellier (2006-10-14). "Is Fault-Tolerant Quantum Computation Really Possible?". Retrieved 2007-02-16.
- ^ Freedman, Michael (2002-10-20). "Topological Quantum Computation". Bulletin of the American Mathematical Society. 40 (1): 31–38. doi:10.1090/S0273-0979-02-00964-3.
{{cite journal}}: Unknown parameter|coauthors=ignored (|author=suggested) (help) - ^ Monroe, Don, Anyons: The breakthrough quantum computing needs?, New Scientist, 1 October 2008
- ^ Clarke, John; Wilhelm, Frank (June 19, 2008). "Superconducting quantum bits". Nature. 453 (7198): 1031–1042. doi:10.1038/nature07128. ISSN 0028-0836. PMID 18563154.
{{cite journal}}: Unknown parameter|month=ignored (help)CS1 maint: date and year (link) - ^ Nayak, Chetan; Simon, Steven; Stern, Ady (2008). "Nonabelian Anyons and Quantum Computation". Rev Mod Phys. 80: 1083.
- ^ Nizovtsev, A. P.; Kilin, S. Ya.; Jelezko, F.; Gaebal, T.; Popa, I.; Gruber, A.; Wrachtrup, J. (October 19, 2004). "A quantum computer based on NV centers in diamond: Optically detected nutations of single electron and nuclear spins". Optics and Spectroscopy. 99 (2): 248–260. doi:10.1134/1.2034610.
{{cite journal}}: Check date values in:|year=/|date=mismatch (help) - ^ Wolfgang Gruener, TG Daily (2007-06-01). "Research indicates diamonds could be key to quantum storage". Retrieved 2007-06-04.
- ^ Neumann, P.; Mizuochi, N.; Rempp, F.; Hemmer, P.; Watanabe, H.; Yamasaki, S.; Jacques, V.; Gaebel, T.; Jelezko, F. (June 6, 2008). "Multipartite Entanglement Among Single Spins in Diamond". Science. 320 (5881): 1326–1329. doi:10.1126/science.1157233. PMID 18535240.
{{cite journal}}: CS1 maint: date and year (link) - ^ Rene Millman, IT PRO (2007-08-03). "Trapped atoms could advance quantum computing". Retrieved 2007-07-26.
- ^ William M Kaminsky, MIT (Date Unknown). "Scalable Superconducting Architecture for Adiabatic Quantum Computation". Retrieved 2007-02-19.
{{cite web}}: Check date values in:|date=(help) - ^ Ohlsson, N.; Mohan, R. K.; Kröll, S. (January 1, 2002). "Quantum computer hardware based on rare-earth-ion-doped inorganic crystals". Opt. Commun. 201 (1–3): 71–77. doi:10.1016/S0030-4018(01)01666-2.
{{cite journal}}: CS1 maint: date and year (link) - ^ Longdell, J. J.; Sellars, M. J.; Manson, N. B. (September 23, 2004). "Demonstration of conditional quantum phase shift between ions in a solid". Phys. Rev. Lett. 93 (13): 130503. doi:10.1103/PhysRevLett.93.130503. PMID 15524694.
{{cite journal}}: CS1 maint: date and year (link) - ^ Ann Arbor (2005-12-12). "U-M develops scalable and mass-producible quantum computer chip". Retrieved 2006-11-17.
- ^ Dicarlo, L; Chow, JM; Gambetta, JM; Bishop, LS; Johnson, BR; Schuster, DI; Majer, J; Blais, A; Frunzio, L (2009-06-28). "Demonstration of two-qubit algorithms with a superconducting quantum processor" (PDF). Nature. 460 (7252): 240–4. doi:10.1038/nature08121. ISSN 0028-0836. PMID 19561592. Retrieved 2009-07-02.
{{cite journal}}: More than one of|author=and|last1=specified (help); Unknown parameter|month=ignored (help) - ^ "Scientists Create First Electronic Quantum Processor". 2009-07-02. Retrieved 2009-07-02.
- ^ New Scientist (2009-09-04). "Code-breaking quantum algorithm runs on a silicon chip". Retrieved 2009-10-14.
- ^ a b c Michael Nielsen and Isaac Chuang (2000). Quantum Computation and Quantum Information. Cambridge: Cambridge University Press. ISBN 0-521-63503-9. OCLC 174527496.
- ^ a b Bernstein and Vazirani, Quantum complexity theory, SIAM Journal on Computing, 26(5):1411-1473, 1997. [1]
- ^ Scott Aaronson, NP-complete Problems and Physical Reality, ACM SIGACT News, Vol. 36, No. 1. (March 2005), pp. 30-52, section 7 "Quantum Gravity": "[...] to anyone who wants a test or benchmark for a favorite quantum gravity theory,[author's footnote: That is, one without all the bother of making numerical predictions and comparing them to observation] let me humbly propose the following: can you define Quantum Gravity Polynomial-Time? [...] until we can say what it means for a ‘user’ to specify an ‘input’ and ‘later’ receive an ‘output’—there is no such thing as computation, not even theoretically." (emphasis in original)
General references
- Derek Abbott, Charles R. Doering, Carlton M. Caves, Daniel M. Lidar, Howard E. Brandt, Alexander R. Hamilton, David K. Ferry, Julio Gea-Banacloche, Sergey M. Bezrukov, and Laszlo B. Kish (2003). "Dreams versus Reality: Plenary Debate Session on Quantum Computing". Quantum Information Processing. 2 (6): 449–472. doi:10.1023/B:QINP.0000042203.24782.9a.
{{cite journal}}: CS1 maint: multiple names: authors list (link) arXiv:quant-ph/0310130. (Alternative Location (free) at Michigan university's repository Deep Blue) - David P. DiVincenzo (2000). "The Physical Implementation of Quantum Computation". Experimental Proposals for Quantum Computation. arXiv:quant-ph/0002077
- David P. DiVincenzo (1995). "Quantum Computation". Science. 270 (5234): 255–261. doi:10.1126/science.270.5234.255. Table 1 lists switching and dephasing times for various systems.
- Richard Feynman (1982). "Simulating physics with computers". International Journal of Theoretical Physics. 21: 467. doi:10.1007/BF02650179.
- Gregg Jaeger (2006). Quantum Information: An Overview. Berlin: Springer. ISBN 0-387-35725-4. OCLC 255569451. http://www.springer.com/west/home/physics?SGWID=4-10100-22-173664707-detailsPage=ppmmedia%7Ctoc"
- Michael Nielsen and Isaac Chuang (2000). Quantum Computation and Quantum Information. Cambridge: Cambridge University Press. ISBN 0-521-63503-9. OCLC 174527496.
- Stephanie Frank Singer (2005). Linearity, Symmetry, and Prediction in the Hydrogen Atom. New York: Springer. ISBN 0-387-24637-1. OCLC 253709076.
- Giuliano Benenti (2004). Principles of Quantum Computation and Information Volume 1. New Jersey: World Scientific. ISBN 9-812-38830-3. OCLC 179950736.
- David P. DiVincenzo (2000). "The Physical Implementation of Quantum Computation". Experimental Proposals for Quantum Computation. arXiv:quant-ph/0002077.
- Sam Lomonaco Four Lectures on Quantum Computing given at Oxford University in July 2006
- C. Adami, N.J. Cerf. (1998). "Quantum computation with linear optics". arXiv:quant-ph/9806048v1.
- Joachim Stolze, (2004). Quantum Computing. Wiley-VCH. ISBN 3527404384.
{{cite book}}: Unknown parameter|coauthors=ignored (|author=suggested) (help)CS1 maint: extra punctuation (link)
- Ian Mitchell, (1998). "Computing Power into the 21st Century: Moore's Law and Beyond".
{{cite web}}: CS1 maint: extra punctuation (link)
- Rolf Landauer, (1961). "Irreversibility and heat generation in the computing process" (PDF).
{{cite web}}: CS1 maint: extra punctuation (link)
- Gordon E. Moore (1965). Cramming more components onto integrated circuits.
{{cite book}}:|journal=ignored (help)
- R.W. Keyes, (1988). Miniaturization of electronics and its limits.
{{cite book}}:|journal=ignored (help)CS1 maint: extra punctuation (link)
- M. A. Nielsen,. "Complete Quantum Teleportation By Nuclear Magnetic Resonance".
{{cite web}}: Unknown parameter|coauthors=ignored (|author=suggested) (help)CS1 maint: extra punctuation (link)
- Lieven M.K. Vandersypen, (2000). Liquid state NMR Quantum Computing.
{{cite book}}: Unknown parameter|coauthors=ignored (|author=suggested) (help)CS1 maint: extra punctuation (link)
- Imai Hiroshi, (2006). Quantum Computation and Information. Berlin: Springer. ISBN 3540331328.
{{cite book}}: Unknown parameter|coauthors=ignored (|author=suggested) (help)CS1 maint: extra punctuation (link)
- Andre Berthiaume, (1997). "Quantum Computation".
{{cite web}}: CS1 maint: extra punctuation (link)
- Daniel R. Simon, (1994). "On the Power of Quantum Computation". Institute of Electrical and Electronic Engineers Computer Society Press.
{{cite web}}: CS1 maint: extra punctuation (link)
- "Seminar Post Quantum Cryptology". Chair for communication security at the Ruhr-University Bochum.
- Laura Sanders, (2009). "First programmable quantum computer created".
{{cite web}}: CS1 maint: extra punctuation (link)
External links
- Stanford Encyclopedia of Philosophy: "Quantum Computing" by Amit Hagar.
- Quantiki - Wiki and portal with free-content related to quantum information science.
- jQuantum: Java quantum circuit simulator
- QCAD: Quantum circuit emulator
- C++ Quantum Library
- Haskell Library for Quantum computations
- Video Lectures by David Deutsch
- Lectures at the Institut Henri Poincaré (slides and videos)




















