Malware: Difference between revisions
←Replaced content with 'CREATED BY AODHAN MGEE' Tag: shouting |
ClueBot NG (talk | contribs) m Reverting possible vandalism by 203.33.181.125 to version by 149.152.23.33. False positive? Report it. Thanks, ClueBot NG. (889691) (Bot) |
||
| Line 1: | Line 1: | ||
<!-- is this necessary? all links are formatted except for one |
|||
CREATED BY AODHAN MGEE |
|||
{{linkrot|date=January 2012}} |
|||
--> |
|||
[[Image:Beast RAT client.jpg|thumb|right|[[Beast Trojan (trojan horse)|Beast]], a Windows-based [[backdoor (computing)|backdoor]] [[Trojan horse (computing)|Trojan horse]].]] |
|||
'''Malware''', [[portmanteau|short for]] '''malicious software''', is software (or [[script (computing)|script]] or [[Source code|code]]) designed to disrupt computer operation, gather sensitive information, or gain unauthorized access to computer systems. It is a general term used to describe any kind of software or code specifically designed to exploit a computer, or the data it contains, without consent.<ref>http://www.us-cert.gov/control_systems/pdf/undirected_attack0905.pdf</ref> The expression is a general term used by computer professionals to mean a variety of forms of hostile, intrusive, or annoying software.<ref>{{cite web |
|||
|url=http://technet.microsoft.com/en-us/library/dd632948.aspx |
|||
|title=Defining Malware: FAQ |
|||
|publisher=technet.microsoft.com |
|||
|accessdate=2009-09-10 |
|||
}}</ref> |
|||
Malware includes [[computer virus]]es, [[computer worm|worms]], [[trojan horse (computing)|trojan horses]], [[spyware]], dishonest [[adware]], most [[rootkit]]s, and other malicious programs. In [[law]], malware is sometimes known as a '''computer contaminant''', for instance in the legal codes of several [[United States|U.S.]] states, including California and West Virginia.<ref>National Conference of State Legislatures [http://www.ncsl.org/programs/lis/cip/viruslaws.htm Virus/Contaminant/Destructive Transmission Statutes by State]</ref><ref>{{cite web |
|||
|url=http://jcots.state.va.us/2005%20Content/pdf/Computer%20Contamination%20Bill.pdf |
|||
|title=§18.2-152.4:1 Penalty for Computer Contamination |
|||
|format=PDF |
|||
|publisher=Joint Commission on Technology and Science |
|||
|accessdate=2010-09-17}}</ref> |
|||
Malware is not the same as defective software, that is, software that has a legitimate purpose but contains harmful [[Software bug|bugs]]. Sometimes, malware is disguised as genuine software, and may come from an official site. Therefore, some security programs may call malware "potentially unwanted programs" or "PUP". Though a [[computer virus]] is malware that can reproduce itself, the term is sometimes used erroneously to refer to the entire category. |
|||
==Proliferation== |
|||
Preliminary results from [[Symantec]] published in 2008 suggested that "the release rate of malicious code and other unwanted programs may be exceeding that of legitimate software applications."<ref>{{cite journal|title=Symantec Internet Security Threat Report: Trends for July–December 2007 (Executive Summary)|publisher=Symantec Corp.|volume=XIII|page=29|date=April 2008|url=http://eval.symantec.com/mktginfo/enterprise/white_papers/b-whitepaper_exec_summary_internet_security_threat_report_xiii_04-2008.en-us.pdf|format=PDF|accessdate=2008-05-11}}</ref> According to [[F-Secure]], "As much malware [was] produced in 2007 as in the previous 20 years altogether."<ref>{{cite press release|title=F-Secure Reports Amount of Malware Grew by 100% during 2007|url=http://www.f-secure.com/f-secure/pressroom/news/fs_news_20071204_1_eng.html|date=December 4, 2007|publisher=F-Secure Corporation|accessdate=2007-12-11}}</ref> Malware's most common pathway from criminals to users is through the [[Internet]]: primarily by e-mail and the [[World Wide Web]].<ref>{{cite web|title= F-Secure Quarterly Security Wrap-up for the first quarter of 2008|url=http://www.f-secure.com/f-secure/pressroom/news/fsnews_20080331_1_eng.html|publisher=F-Secure|date=March 31, 2008|accessdate=2008-04-25}}</ref> |
|||
The prevalence of malware as a vehicle for Internet crime, along with the challenge of anti-malware software to keep up with the continuous stream of new malware, has seen the adoption of a new mindset for individuals and businesses using the Internet. With the amount of malware currently being distributed, it follows that some percentage of computers (that are connected to an Internet connection) will always be infected. |
|||
For businesses, this means that they need to find a way to operate despite this problem. The result is a greater emphasis on back-office protection systems designed to protect against advanced malware operating on customers' computers.<ref>{{cite web|title= Continuing Business with Malware Infected Customers|url=http://www.technicalinfo.net/papers/MalwareInfectedCustomers.html|publisher=Gunter Ollmann|date=October 2008}}</ref> |
|||
On March 29, 2010, [[Symantec Corporation]] named [[Shaoxing]], China, as the world's malware capital.<ref>{{cite web|url=http://www.engadget.com/2010/03/29/symantec-names-shaoxing-china-worlds-malware-capital |title=Symantec names Shaoxing, China as world's malware capital |publisher=Engadget |date= |accessdate=2010-04-15}}</ref> A 2011 study from the [[University of California, Berkeley]], and the Madrid Institute for Advanced Studies published an article in ''Software Development Technologies'', examining how entrepreneurial [[Hacker (computer security)|crackers]] are helping enable the spread of malware by offering access to computers for a price. They charge from $7 to $180 per thousand infections to make up an informal underground Pay-Per-Install (PPI) industry. The study's authors identified more than 57 malware “families," including [[spambot|spam bots]], fake antivirus programs, information-stealing [[Trojan horse (computing)|trojans]], [[Denial-of-service attack|denial-of-service]] bots and [[adware]]. To avoid detection by anti-virus software, malware distributed by PPI services are frequently updated, with one observed family of malware updating up to twice a day. |
|||
Although most common families of malware targeted both Europe and the United States, there were some families with a single-country focus and some families with no geographic bias. [[Microsoft]] reported in May 2011 that one in every 14 downloads from the Internet may now contain malware code according to the Wall Street Journal. Social media, and Facebook in particular, are seeing a rise in the number of tactics used to spread malware to computers.<ref>{{cite news|url = http://online.wsj.com/article/SB10001424052748704904604576332812592346714.html |title = Malware Is Posing Increasing Danger |publisher = Wall Street Journal | first=Ben |last=Rooney |date=2011-05-23}}</ref> |
|||
==Purposes== |
|||
[[File:Malware statics 2011-03-16-en.svg|thumb|right|300px|Malware by categories on March 16, 2011.]] |
|||
Many early infectious programs, including the first [[Internet Worm]] and a number of [[MS-DOS]] [[viruses]], were written as experiments or [[prank]]s. They were generally intended to be harmless or merely annoying, rather than to cause serious damage to computer systems. In some cases, the perpetrator did not realize how much harm his or her creations would do. Young [[programmer]]s learning about viruses and their techniques wrote them simply for practice, or to see how far they could spread. As late as 1999, widespread viruses such as the [[Melissa virus]] and the [[David virus]] appear to have been written chiefly as pranks. The first [[Mobile virus|mobile phone virus]], [[Caribe (computer worm)|Cabir]], appeared in 2004. |
|||
Hostile intent related to [[vandalism]] can be found in programs designed to cause harm or data loss. Many DOS viruses, and the [[Microsoft Windows|Windows]] [[ExploreZip]] worm, were designed to destroy files on a [[hard disk]], or to corrupt the file system by writing invalid data to them. Network-borne worms such as the 2001 [[Code Red worm]] or the [[Ramen worm]] fall into the same category. Designed to vandalize web pages, worms may seem like the online equivalent to [[graffiti]] tagging, with the author's alias or affinity group appearing everywhere the worm goes.{{Citation needed|date=June 2010}} |
|||
Since the rise of widespread [[broadband]] [[Internet]] access, malicious software has been designed for a profit (e.g. forced advertising). For instance, since 2003, the majority of widespread viruses and worms have been designed to take control of users' computers for black-market exploitation.<ref>{{cite web|title=Malware Revolution: A Change in Target|url=http://technet.microsoft.com/en-us/library/cc512596.aspx|date=March 2007}}</ref> Infected "[[zombie computer]]s" are used to send [[email spam]], to host contraband data such as [[child pornography]],<ref>{{cite web|title=Child Porn: Malware's Ultimate Evil|url=http://www.itworld.com/security/84077/child-porn-malwares-ultimate-evil|date=November 2009}}</ref> or to engage in [[distributed denial-of-service]] [[Attack (computing)|attacks]] as a form of [[extortion]].<ref>[http://www.pcworld.com/article/id,116841-page,1/article.html PC World - Zombie PCs: Silent, Growing Threat<!-- Bot generated title -->].</ref> |
|||
Another strictly for-profit category of malware has emerged in [[spyware]] -- programs designed to monitor users' web browsing, display unsolicited advertisements, or redirect [[affiliate marketing]] revenues to the [[spyware]] creator. Spyware programs do not spread like viruses; they are, in general, installed by exploiting security holes or are packaged with user-installed software, such as peer-to-peer applications. |
|||
==Infectious malware: viruses and worms== |
|||
{{Main|Computer virus|Computer worm}} |
|||
The best-known types of malware, ''viruses'' and ''worms'', are known for the manner in which they spread, rather than any other particular behavior. The term ''[[computer virus]]'' is used for a program that has infected some executable software and, ''when run'', causes the virus to spread to other executables. Viruses may also contain a [[payload (software)|payload]] that performs other actions, often malicious. On the other hand, a ''[[computer worm|worm]]'' is a program that ''actively'' transmits itself over a network to infect other computers. It too may carry a payload. |
|||
These definitions lead to the observation that a virus requires user intervention to spread, whereas a worm spreads itself automatically. Using this distinction, infections transmitted by [[email]] or [[Microsoft Word]] documents, which rely on the recipient opening a file or email to infect the system, would be classified as viruses rather than worms. |
|||
Some writers in the trade and popular press misunderstand this distinction and use the terms interchangeably. |
|||
===Capsule history of viruses and worms=== |
|||
Before [[Internet]] access became widespread, viruses spread on personal computers by infecting the executable [[boot sector]]s of floppy disks. By inserting a copy of itself into the [[machine code]] instructions in these executables, a virus causes itself to be run whenever a program is run or the disk is booted. Early computer viruses were written for the [[Apple II]] and [[Apple Macintosh|Macintosh]], but they became more widespread with the dominance of the [[IBM PC]] and [[MS-DOS]] system. Executable-infecting viruses are dependent on users exchanging software or boot-able floppies, so they spread rapidly in computer hobbyist circles. |
|||
The first worms, network-borne infectious programs, originated not on personal computers, but on multitasking [[Unix]] systems. The first well-known worm was the [[Internet Worm]] of 1988, which infected [[SunOS]] and [[VAX]] [[BSD]] systems. Unlike a virus, this worm did not insert itself into other programs. Instead, it exploited security holes ([[vulnerability (computing)|vulnerabilities]]) in network server programs and started itself running as a separate process. This same behaviour is used by today's worms as well. |
|||
With the rise of the [[Microsoft Windows]] platform in the 1990s, and the flexible [[macro (computer science)|macros]] of its applications, it became possible to write infectious code in the macro language of [[Microsoft Office Word|Microsoft Word]] and similar programs. These ''[[macro virus (computing)|macro viruses]]'' infect documents and templates rather than applications (executables), but rely on the fact that macros in a Word document are a form of executable code. |
|||
Today, worms are most commonly written for the Windows OS, although a few like Mare-D<ref>{{cite web |url=http://www.theregister.co.uk/2006/02/20/linux_worm/ |title= Linux worm targets PHP flaw |author= Nick Farrell |date= 20 February 2006 |work= The Register|accessdate=19 May 2010}}</ref> and the [[L10n worm|Lion worm]]<ref>{{cite web |url=http://www.theregister.co.uk/2001/03/28/highly_destructive_linux_worm_mutating/|title= Highly destructive Linux worm mutating |author= John Leyden |date= March 28, 2001 |work= The Register|accessdate=19 May 2010}}</ref> are also written for [[Linux]] and [[Unix]] systems. Worms today work in the same basic way as 1988's Internet Worm: they scan the network and leverage vulnerable computers to replicate. Because they need no human intervention, worms can spread with incredible speed. The [[SQL Slammer]] infected thousands of computers in a few minutes.<ref>{{cite news |url= http://news.bbc.co.uk/2/hi/technology/2720337.stm |title= Aggressive net bug makes history|date= February 3, 2003 |work= BBC News|accessdate=19 May 2010}}</ref> |
|||
==Concealment: Trojan horses, rootkits, and backdoors== |
|||
{{Main|Trojan horse (computing)|Rootkit|Backdoor (computing)}} |
|||
===Trojan horses=== |
|||
For a malicious program to accomplish its goals, it must be able to run without being detected, shut down, or deleted by the user or security software. When a malicious program is disguised as something normal or desirable, users may be tempted to install it without realizing it. This is the technique of the ''[[Trojan horse (computing)|Trojan horse]]'' or ''trojan''. In broad terms, a Trojan horse is any program that invites the user to run it, concealing a harmful or malicious payload. The payload may take effect immediately and can lead to many undesirable effects, such as deleting the user's files or installing additional harmful software. |
|||
<!-- This part seems a bit advanced for this part of article |
|||
Trojan horses known as [[dropper]]s are used to start off a worm outbreak, by injecting the worm into users' local network. ~PatrickCarbone --> |
|||
One of the most common ways that spyware is distributed is as a Trojan horse, bundled with a piece of desirable software that the user downloads from the Internet. When the user installs the software, the spyware is installed as well. Spyware authors who attempt to act in a legal fashion may include an [[end-user license agreement]] that states the behavior of the spyware in loose terms, which the users are unlikely to read or understand. |
|||
Trojans are most commonly used for marketing. Today's advanced trojans are capable of taking complete control of a [[browser|Web browser]] and have even been known to add false exceptions to a browser's security settings. They may also modify a computer's [[registry|Windows Registry]]. |
|||
===Rootkits=== |
|||
Once a malicious program is installed on a system, it is essential that it ''stays'' concealed, to avoid detection and disinfection. The same is true when a human attacker breaks into a computer directly. Techniques known as ''[[rootkit]]s'' allow this concealment, by modifying the host's operating system so that the malware is hidden from the user. Rootkits can prevent a malicious [[process (computing)|process]] from being visible in the system's list of processes, or keep its files from being read. Originally, a rootkit was a set of tools installed by a human attacker on a Unix system, allowing the attacker to gain administrator (root) access. Today, the term is used more generally for concealment routines in a malicious program. |
|||
Some malicious programs contain routines to defend against removal, not merely to hide themselves, but to repel attempts to remove them. An early example of this behavior is recorded in the [[Jargon File]] tale of a pair of programs infesting a Xerox [[CP-V]] time sharing system: |
|||
:Each ghost-job would detect the fact that the other had been killed, and would start a new copy of the recently slain program within a few milliseconds. The only way to kill both ghosts was to kill them simultaneously (very difficult) or to deliberately crash the system.<ref>{{cite web|url=http://catb.org/jargon/html/meaning-of-hack.html |title=Catb.org |publisher=Catb.org |date= |accessdate=2010-04-15}}</ref> |
|||
Similar techniques are used by some modern malware, where the malware starts a number of processes that monitor and restore one another as needed. In the event a user running [[Microsoft Windows]] is infected with this kind of malware, if they wish to manually stop it, they could use [[Windows Task Manager|Task Manager]]'s 'processes' tab to find the main process (the one that spawned the "resurrector process(es)"), and use the 'end [[process tree (computing)|process tree]]' function, which would kill not only the main process, but the "resurrector(s)" as well, since they were started by the main process. |
|||
Some malware programs use other techniques, such as naming the infected file similar to a legitimate or trustworthy file (expl0rer.exe VS explorer.exe). |
|||
===Backdoors=== |
|||
A [[backdoor (computing)|backdoor]] is a method of bypassing normal [[authentication]] procedures. Once a system has been compromised (by one of the above methods, or in some other way), one or more backdoors may be installed in order to allow easier access in the future. Backdoors may also be installed prior to malicious software, to allow attackers entry. |
|||
The idea has often been suggested that computer manufacturers preinstall backdoors on their systems to provide technical support for customers, but this has never been reliably verified. [[Hacker (computer security)|Crackers]] typically use backdoors to secure remote access to a computer, while attempting to remain hidden from casual inspection. To install backdoors crackers may use [[Trojan Horse (Computing)|Trojan horses]], [[Computer worm|worms]], or other methods. |
|||
==Malware for profit: spyware, botnets, keystroke loggers, and "Ransom" Malware== |
|||
{{Main|Spyware|Botnet|Keystroke logging|Web threats|Dialer}} |
|||
During the 1980s and 1990s, it was usually taken for granted that malicious programs were created as a form of [[vandalism]] or [[prank]]. More recently, the greater share of malware programs have been written with a [[profit motive]] (financial or otherwise) in mind. This can be taken as the malware authors' choice to monetize their control over infected systems: to turn that control into a source of revenue. |
|||
Spyware programs are commercially produced for the purpose of gathering information about computer users, showing them [[pop-up ad]]s, or altering web-browser behavior for the financial benefit of the spyware creator. For instance, some spyware programs redirect [[Web search engine|search engine]] results to paid advertisements. Others, often called "[[stealware]]" by the media, overwrite [[affiliate marketing]] codes so that revenue is redirected to the spyware creator rather than the intended recipient. |
|||
Spyware programs are sometimes installed as Trojan horses. They differ in that their creators present themselves as businesses (i.e. by selling advertising space on the pop-ups created by the malware). Most programs of this kind present the user with an [[Software license agreement|end-user license agreement]] that purportedly protects the creator from prosecution under computer contaminant laws. However, spyware EULAs have not yet been upheld in court. |
|||
Another way that financially motivated malware creators can profit from infecting computers is to directly use the infected computers to work for them. The infected computers are used as [[open proxy|proxies]] to send out spam messages. A computer left in this state is often known as a [[zombie computer]]. The advantage to spammers of using infected computers is they provide anonymity, protecting the spammer from [[prosecution]]. Spammers have also used infected PCs to target anti-spam organizations with [[distributed denial-of-service attack]]s. In order to coordinate the activity of many infected computers, attackers have used coordinating systems known as ''[[botnet]]s''. In a botnet, the malware or [[malbot]] logs in to an [[Internet Relay Chat]] channel or other chat system. |
|||
The attacker can then give instructions to all the infected systems simultaneously. Botnets can also be used to push upgraded malware to the infected systems, keeping them resistant to antivirus software or other security measures. |
|||
It is possible for a malware creator to profit by stealing sensitive information from a victim. One way this is accomplished is by malware programs that install a ''[[Keystroke logging|key logger]]'', which record the user's keystrokes when entering a [[password]], [[credit card]] number, or any other key-entered data. This is then transmitted to the malware creator, enabling them to commit [[credit card fraud]] or other theft or impersonation. Similarly, malware may copy the [[CD key]] or password for online games, allowing the creator to steal accounts or virtual items. |
|||
"Ransom" Malware serve as another tool for attackers to profit by infecting computers, the idea behind this attack is to encrypt files on the infected computers' hard drive where the [[Public-key cryptography|private encryption key]] is only accessible to the attacker, and he in turn will only surrender it for ransom money. |
|||
<!-- Another way of stealing money from the infected PC owner is to take control of a [[Dial-up internet access|dial-up]] modem and dial an expensive toll call. ''[[Dialer]]'' (or ''porn dialer'') software dials up a [[premium-rate telephone number]] such as a U.S. "900 number" and leave the line open, charging the toll to the infected user. --> |
|||
==Data-stealing malware== |
|||
Data-stealing malware is a [[web threat]] that divest victims of personal and proprietary information with the intent of monetizing stolen data through direct use or underground distribution. Content security [[Threat (computer)|threats]] that fall under this umbrella include [[keyloggers]], screen scrapers, [[spyware]], [[adware]], backdoors, and [[Internet bot|bot]]s. The term does not refer to activities such as spam, [[phishing]], [[Domain Name System|DNS]] poisoning, [[Search engine optimization|SEO]] abuse, etc. However, when these threats result in file download or direct installation, as most hybrid attacks do, files that act as agents to [[Proxy server|proxy]] information will fall into the data-stealing malware category. |
|||
===Characteristics of data-stealing malware=== |
|||
Does not leave traces of the event |
|||
* The malware is typically stored in a cache that is routinely flushed |
|||
* The malware may be installed via a drive-by-download process |
|||
* The website hosting the malware as well as the malware is generally temporary or rogue |
|||
Frequently changes and extends its functions |
|||
* It is difficult for antivirus software to detect final payload attributes due to the combination(s) of malware components |
|||
* The malware uses multiple file encryption levels |
|||
Thwarts [[Intrusion Detection Systems]] (IDS) after successful installation |
|||
* There are no perceivable network anomalies |
|||
* The malware hides in web traffic |
|||
* The malware is stealthier in terms of traffic and resource use |
|||
Thwarts disk encryption |
|||
* Data is stolen during decryption and display |
|||
* The malware can record keystrokes, passwords, and screenshots |
|||
Thwarts [[Data Loss Prevention]] (DLP) |
|||
* Leakage protection hinges on metadata tagging, not everything is tagged |
|||
* Miscreants can use encryption to port data |
|||
===Examples of data-stealing malware=== |
|||
* [[Bancos]], an info stealer that waits for the user to access banking websites then spoofs pages of the bank website to steal sensitive information. |
|||
* [[Claria Corporation|Gator]], spyware that covertly monitors web-surfing habits, uploads data to a server for analysis then serves targeted pop-up ads. |
|||
* [[LegMir]], spyware that steals personal information such as account names and passwords related to online games. |
|||
* [[Qhost]], a Trojan that modifies the [[Hosts file]] to point to a different DNS server when banking sites are accessed then opens a spoofed login page to steal login credentials for those financial institutions. |
|||
===Data-stealing malware incidents=== |
|||
* [[Albert Gonzalez]] (not to be confused with the U.S. Attorney General Alberto Gonzalez) is accused of masterminding a ring to use malware to steal and sell more than 170 million credit card numbers in 2006 and 2007—the largest computer fraud in history. Among the firms targeted were [[BJ's Wholesale Club]], [[TJX]], [[Dsw shoes|DSW Shoes]], [[OfficeMax]], [[Barnes & Noble]], [[Boston Market]], [[Sports Authority]] and [[Forever 21]].<ref>{{cite web|url=http://www.usdoj.gov/usao/ma/Press%20Office%20-%20Press%20Release%20Files/IDTheft/Gonzalez,%20Albert%20-%20Indictment%20080508.pdf |title=Gonzalez, Albert — Indictment 080508 |publisher=US Department of Justice Press Office |date= |accessdate=2010- |pages=01–18}}</ref> |
|||
* A Trojan horse program stole more than 1.6 million records belonging to several hundred thousand people from Monster Worldwide Inc’s job search service. The data was used by cybercriminals to craft phishing emails targeted at Monster.com users to plant additional malware on users’ PCs.<ref>Keizer, Gregg (2007) [http://www.pcworld.com/article/136154/monstercom_data_theft_may_be_bigger.html Monster.com data theft may be bigger]</ref> |
|||
* Customers of [[Hannaford Bros. Co.]], a supermarket chain based in [[Maine]], were victims of a data security breach involving the potential compromise of 4.2 million debit and credit cards. The company was hit by several class-action law suits.<ref>Vijayan, Jaikumar (2008) [http://www.computerworld.com/action/article.do?command=viewArticleBasic&articleId=9070281 Hannaford hit by class-action lawsuits in wake of data breach disclosure]</ref> |
|||
* The [[Torpig]] Trojan has compromised and stolen login credentials from approximately 250,000 online bank accounts as well as a similar number of credit and debit cards. Other information such as email, and FTP accounts from numerous websites, have also been compromised and stolen.<ref>BBC News: [http://news.bbc.co.uk/2/hi/technology/7701227.stm Trojan virus steals banking info]</ref> |
|||
==Controversy about assignment to spyware== |
|||
There is a group of software ([[Alexa toolbar]], [[Google toolbar]], [[Eclipse (software)|Eclipse]] data usage collector, etc.) that send data to a central server about which pages have been visited or which features of the software have been used. However differently from "classic" malware these tools document activities and only send data with the user's approval. The user may opt in to share the data in exchange to the additional features and services, or (in case of Eclipse) as the form of voluntary support for the project. Some security tools report such loggers as malware while others do not. The status of the group is questionable. Some tools like [[PDFCreator]] are more on the boundary than others because opting out has been made more complex than it could be (during the installation, the user needs to uncheck two check boxes rather than one). However also PDFCreator is only sometimes mentioned as malware and is still subject of discussions. |
|||
==Vulnerability to malware== |
|||
{{Main|Vulnerability (computing)}} |
|||
In this context, as throughout, it should be borne in mind that the “system” under attack may be of various types, e.g. a single computer and operating system, a network or an application. |
|||
Various factors make a system more vulnerable to malware: |
|||
* Homogeneity: e.g. when all computers in a network run the same operating system; upon exploiting one, one can exploit them all. |
|||
* Weight of numbers: simply because the vast majority of existing malware is written to attack Windows systems, then Windows systems are more vulnerable to succumbing to malware attacks (regardless of the security strengths or weaknesses of Windows itself). |
|||
* Defects: malware leveraging defects in the operating system design. |
|||
* Unconfirmed code: code from a [[floppy disk]], [[CD-ROM]] or [[USB]] device may be executed without the user’s permission. |
|||
* Over-privileged users: some systems allow all users to modify their internal structures. This was the standard operating procedure for early microcomputer and home computer systems, where there was no distinction between an ''Administrator'' or ''root'', and a regular user of the system. |
|||
* Over-privileged code: some systems allow code executed by a user to access all rights of that user. Also standard operating procedure for early microcomputer and home computer systems. |
|||
===Use of the same operating system=== |
|||
An oft-cited cause of vulnerability of networks is consistent use of the same operating system.<ref name="UKan">"LNCS 3786 - Key Factors Influencing Worm Infection", U. Kanlayasiri, 2006, web (PDF): [http://www.springerlink.com/index/3x8582h43ww06440.pdf SL40-PDF].</ref> |
|||
For example, [[Microsoft Windows]] or [[Apple Computer|Apple Mac]] have such a large share of the market that concentrating on either could enable an exploited vulnerability to subvert a large number of systems. Instead, introducing diversity, purely for the sake of robustness, could increase short-term costs for training and maintenance. However, having a few diverse nodes would deter total shutdown of the network, and allow those nodes to help with recovery of the infected nodes. Such separate, functional redundancy could avoid the cost of a total shutdown. |
|||
===Software bugs=== |
|||
Most systems contain bugs, or loopholes, which may be exploited by malware. A typical example is the [[buffer overrun|buffer-overrun]] weakness, in which an interface designed to store data, in a small area of memory, allows the caller to supply more data than will fit. This extra data then overwrites the interface's own executable structure (past the end of the buffer and other data). In this manner, malware can force the system to execute malicious code, by replacing legitimate code with its own payload of instructions (or data values) copied into live memory, outside the buffer area. |
|||
Originally, PCs had to be booted from floppy disks, and until recently it was common for this to be the default [[boot device|Boot_device#Boot_devices_.28IBM_PC.29]]. This meant that a corrupt floppy disk could subvert the computer during booting, and the same applies to CDs. Although that is now less common, it is still possible to forget that one has changed the default, and rare that a [[BIOS]] makes one confirm a boot from removable media. |
|||
===Over-Privileged Users=== |
|||
In some systems, [[non-administrator|System administrator]] users are over-privileged by design, in the sense that they are allowed to modify internal structures of the system. In some environments, users are over-privileged because they have been inappropriately granted administrator or equivalent status. This is primarily a configuration decision, but on Microsoft Windows systems the default configuration is to over-privilege the user. This situation exists due to decisions made by Microsoft to prioritize compatibility with older systems above security configuration in newer systems{{Citation needed|date=February 2007}} and because typical applications were developed without the under-privileged users in mind. As [[privilege escalation]] exploits have increased this priority is shifting for the release of Microsoft [[Windows Vista]]. As a result, many existing applications that require excess privilege (over-privileged code) may have compatibility problems with Vista. However, Vista's [[User Account Control]] feature attempts to remedy applications not designed for under-privileged users, acting as a crutch to resolve the privileged access problem inherent in legacy applications. |
|||
Malware, running as over-privileged code, can use this privilege to subvert the system. Almost all currently popular operating systems, and also many [[scripting applications|scripting]] allow code too many privileges, usually in the sense that when a user executes code, the system allows that code all rights of that user. This makes users vulnerable to malware in the form of [[e-mail attachment]]s, which may or may not be disguised. |
|||
<!-- Why isn't this what [[mail bomb#Emailbombing|mail bombs]] means: has anyone got a good name? --> |
|||
Given this state of affairs, users are warned only to open attachments they trust, and to be wary of code received from untrusted sources. It is also common for operating systems to be designed so that [[device driver]]s need escalated privileges, while they are supplied by more and more hardware manufacturers. |
|||
===Eliminating over-privileged code=== |
|||
Over-privileged code dates from the time when most programs were either delivered with a computer or written in-house, and repairing it would at a stroke render most antivirus software almost redundant. It would, however, have appreciable consequences for the user interface and system management. |
|||
The system would have to maintain privilege profiles, and know which to apply for each user and program. |
|||
In the case of newly installed software, an administrator would need to set up default profiles for the new code. |
|||
Eliminating vulnerability to rogue [[device drivers]] is probably harder than for arbitrary rogue executables. Two techniques, used in [[OpenVMS|VMS]], that can help are memory mapping only the registers of the device in question and a system interface associating the driver with interrupts from the device. |
|||
Other approaches are: |
|||
* Various forms of [[Platform virtualization|virtualization]], allowing the code unlimited access only to virtual resources |
|||
* Various forms of [[sandbox (computer security)|sandbox]] or [[jail (computer security)|jail]] |
|||
* The security functions of [[Java (programming language)|Java]], in <code>java.security</code> |
|||
Such approaches, however, if not fully integrated with the operating system, would reduplicate effort and not be universally applied, both of which would be detrimental to security. |
|||
==Anti-malware programs== |
|||
{{main|Antivirus software}} |
|||
As malware attacks become more frequent, attention has begun to shift from viruses and spyware protection, to malware protection, and programs have been developed specifically to combat them. |
|||
Anti-virus and anti-malware software commonly hooks deep into the operating system's core or [[operating system kernel|kernel]] functions in a manner similar to how malware itself would attempt to operate, though with the user's informed permission for protecting the system. Any time the operating system does something, the anti-malware software checks that the OS is doing an approved task. This commonly slows down the operating system and/or consumes large amounts of system memory. The goal is to preempt any operations the malware may attempt on the system, including activities which might exploit bugs or trigger unexpected operating system behavior. |
|||
Anti-malware programs can combat malware in two ways: |
|||
# They can provide real time protection against the installation of malware software on a computer. This type of spyware protection works the same way as that of antivirus protection in that the anti-malware software scans all incoming network data for malware software and blocks any [[Threat (computer)|threats]] it comes across. |
|||
# Anti-malware software programs can be used solely for detection and removal of malware software that has already been installed onto a computer. This type of malware protection is normally much easier to use and more popular.{{Citation needed|date=November 2008}} This type of anti-malware software scans the contents of the Windows registry, operating system files, and installed programs on a computer and will provide a list of any threats found, allowing the user to choose which files to delete or keep, or to compare this list to a list of known malware components, removing files that match. |
|||
Real-time protection from malware works identically to real-time antivirus protection: the software scans disk files at download time, and blocks the activity of components known to represent malware. In some cases, it may also intercept attempts to install start-up items or to modify browser settings. Because many malware components are installed as a result of [[browser exploit]]s or user error, using security software (some of which are anti-malware, though many are not) to "sandbox" browsers (essentially babysit the user and their browser) can also be effective in helping to restrict any damage done. |
|||
==Website security scans== |
|||
As malware also harms the compromised websites (by breaking reputation, blacklisting in search engines, etc.), some<ref>[http://www.godaddy.com/security/website-security.aspx?ci=20677 An example of the web site scan proposal]</ref> companies offer the paid site scan service. Such scans periodically check the site, detecting malware, noticed security vulnerabilities, outdated software stack with known security issues, etc. The found issues are only reported to the site owner who can take means to fix them. The provider may also offer the security badge that the owner can only display if the site has been recently scanned and is "clean". |
|||
==Academic research== |
|||
The notion of a self-reproducing computer program can be traced back to when presented lectures that encompassed the theory and organization of complicated automata.<ref>John von Neumann, "Theory of Self-Reproducing Automata", Part 1: Transcripts of lectures given at the University of Illinois, December 1949, Editor: A. W. Burks, University of Illinois, USA, 1966.</ref> [[John von Neumann]] showed that in theory a program could reproduce itself. This constituted a plausibility result in [[computability theory (computer science)|computability theory]]. [[Fred Cohen]] experimented with computer viruses and confirmed Neumann's postulate. He also investigated other properties of malware (detectability, self-obfuscating programs that used rudimentary encryption that he called "evolutionary", and so on). His 1988 doctoral dissertation was on the subject of computer viruses.<ref>Fred Cohen, "Computer Viruses", PhD Thesis, University of Southern California, ASP Press, 1988.</ref> Cohen's faculty advisor, [[Leonard Adleman]] (the A in [[RSA (algorithm)|RSA]]) presented a rigorous proof that, in the general case, algorithmically determining whether a virus is or is not present is [[Alan Turing|Turing]] [[Undecidable problem|undecidable]].<ref>L. M. Adleman, "An Abstract Theory of Computer Viruses", Advances in Cryptology---Crypto '88, LNCS 403, pp. 354-374, 1988.</ref> This problem must not be mistaken for that of determining, within a broad class of programs, that a virus is not present; this problem differs in that it does not require the ability to recognize all viruses. Adleman's proof is perhaps the deepest result in malware [[computability theory (computer science)|computability theory]] to date and it relies on [[Cantor's diagonal argument]] as well as the [[halting problem]]. Ironically, it was later shown by Young and Yung that Adleman's work in [[cryptography]] is ideal in constructing a virus that is highly resistant to reverse-engineering by presenting the notion of a [[Cryptovirology|cryptovirus]].<ref>A. Young, M. Yung, "Cryptovirology: Extortion-Based Security Threats and Countermeasures," IEEE Symposium on Security & Privacy, pp. 129-141, 1996.</ref> A cryptovirus is a virus that contains and uses a public key and randomly generated [[symmetric cipher]] [[initialization vector]] (IV) and [[session key]] (SK). In the cryptoviral extortion attack, the virus hybrid encrypts [[plaintext]] data on the victim's machine using the randomly generated IV and SK. The IV+SK are then encrypted using the virus writer's [[public key]]. In theory the victim must negotiate with the virus writer to get the IV+SK back in order to decrypt the [[ciphertext]] (assuming there are no backups). Analysis of the virus reveals the public key, not the IV and SK needed for decryption, or the private key needed to recover the IV and SK. This result was the first to show that [[computational complexity theory]] can be used to devise malware that is robust against reverse-engineering. |
|||
A growing area of computer virus research is to mathematically model the infection behavior of worms using models such as [[Lotka–Volterra equation]]s, which has been applied in the study of biological virus. Various virus propagation scenarios have been studied by researchers such as propagation of computer virus, fighting virus with virus like predator codes,<ref>H. Toyoizumi, A. Kara. Predators: Good Will Mobile Codes Combat against Computer Viruses. Proc. of the 2002 New Security Paradigms Workshop, 2002</ref><ref>Zakiya M. Tamimi, Javed I. Khan, [http://www.medianet.kent.edu/publications/ICCCE06DL-2virusabstract-TK.pdf Model-Based Analysis of Two Fighting Worms], IEEE/IIU Proc. of ICCCE '06, Kuala Lumpur, Malaysia, May 2006, Vol-I, p. 157-163.</ref> effectiveness of patching etc. |
|||
Behavioral malware detection has been a particularly lively research area lately. Most approaches to behavioral detection are based on analysis of [[system call]] dependencies. The executed binary is traced using [[strace]] or more precise [[taint checking|taint analysis]] to compute data-flow dependencies among [[system call]]s. The result is a [[directed graph]] <math>G=(V,E)</math> such that nodes are [[system call]]s, and edges represent dependencies. For example, <math>(s,t)\in E</math> if a result returned by system call <math>s</math> (either directly as a result or indirectly through output parameters) is later used as a parameter of system call <math>t</math>. The origins of the idea to use system calls to analyze software can be found in the work of Forrest et al.<ref>S. Forrest, S. A. Hofmeyr, A. Somayaji, T. A. Longstaff, Thomas A.: [http://dx.doi.org/10.1109/SECPRI.1996.502675 A Sense of Self for Unix Processes], Proc. of the 1996 IEEE Symp. on Security and Privacy, 1996, p. 120-129.</ref> Christodorescu et al.<ref>M. Christodorescu, S. Jha, C. Kruegel: [http://dx.doi.org/10.1145/1287624.1287628 Mining specifications of malicious behavior], Proc. of the 6th joint meeting of the European software engineering conf. and the ACM SIGSOFT symp. on The foundations of software engineering, 2007, p. 5-14</ref> point out that malware authors cannot easily reorder system calls without changing the semantics of the program, which makes system call dependency graphs suitable for malware detection. They compute a difference between malware and goodware system call dependency graphs and use the resulting graphs for detection, achieving high detection rates. Kolbitsch et al.<ref>C. Kolbitsch, P. Milani, C. Kruegel, E. Kirda, X. Zhou, and X. Wang: [http://www.usenix.org/events/sec09/tech/full_papers/kolbitsch.pdf Effective and Efficient Malware Detection at the End Host], The 18th USENIX Security Symposium, 2009.</ref> precompute symbolic expressions and evaluate them on the syscall parameters observed at runtime. They detect dependencies by observing whether the result obtained by evaluation matches the parameter values observed at runtime. Malware is detected by comparing the dependency graphs of the training and test sets. Fredrikson et al.<ref>M. Fredrikson, S. Jha, M. Christodorescu, R. Sailer, and X. Yan: [http://dx.doi.org/10.1109/SP.2010.11 Synthesizing Near-Optimal Malware Specifications from Suspicious Behaviors], Proc. of the 2010 IEEE Symposium on Security and Privacy, 2010, p. 45-60.</ref> describe an approach that uncovers distinguishing features in malware system call dependency graphs. They extract significant behaviors using [[formal concept analysis|concept analysis]] and leap mining.<ref>X. Yan, H. Cheng, J. Han, and P. S. Yu: [http://dx.doi.org/10.1145/1376616.1376662 Mining significant graph patterns by leap search] in Proceedings of the 2008 ACM SIGMOD International Conference on Management of Data (SIGMOD’08). New York, NY, USA: ACM Press, 2008, pp. 433-444</ref> Babic et al.<ref>D. Babic, D. Reynaud, and D. Song: [http://www.domagoj-babic.com/index.php/Pubs/CAV11malware Malware Analysis with Tree Automata Inference], in Proceedings of the 23rd Int. Conference on Computer Aided Verification, 2011, Springer.</ref> recently proposed a novel approach for both malware detection and classification based on [[grammar induction|grammar inference]] of [[tree automaton|tree automata]]. Their approach infers an [[automaton]] from dependency graphs, and they show how such an automaton could be used for detection and classification of malware. |
|||
==Grayware== |
|||
Grayware<ref name=term>{{cite web | accessdate=2007-01-20 | url=http://mpc.byu.edu/Exhibitions/Of%20Earth%20Stone%20and%20Corn/Activities/Native%20American%20Pottery.dhtml | title=Other meanings |archiveurl = http://web.archive.org/web/20070630152901/http://mpc.byu.edu/Exhibitions/Of+Earth+Stone+and+Corn/Activities/Native+American+Pottery.dhtml |archivedate = June 30, 2007}} The term "grayware" is also used to describe a kind of Native American pottery and has also been used by some working in computer technology as slang for the human brain. {{cite web | accessdate=2007-01-02 | url=http://www.techweb.com/encyclopedia/defineterm.jhtml?term=grayware | title=grayware definition | publisher=TechWeb.com}}</ref> (or [[Greynet]]) is a general term sometimes used as a classification for applications that behave in a manner that is annoying or undesirable, and yet less serious or troublesome than malware.<ref name=webopedia>{{cite web | title=Greyware| work=What is greyware? - A word definition from the Webopedia Computer Dictionary | url=http://webopedia.com/TERM/g/greyware.html | accessdate=2006-06-05}}</ref> Grayware encompasses spyware, adware, dialers, joke programs, remote access tools, and any other unwelcome files and programs apart from viruses that are designed to harm the performance of computers on one's network. The term has been in use since at least as early as September 2004.<ref>{{cite web | url=http://www.computerweekly.com/Articles/2004/09/28/205554/the-network-clampdown.htm | title=The network clampdown | accessdate=2007-01-20 | author=Antony Savvas |publisher=Computer Weekly}}</ref> |
|||
Grayware refers to applications or files that are not classified as viruses or [[trojan horse (computing)|trojan horse]] programs, but can still negatively affect the performance of the computers on a network and introduce significant security risks to an organization.<ref>{{cite web | url=http://www.boll.ch/fortinet/assets/Grayware.pdf | title=Fortinet WhitePaper Protecting networks against spyware, adware and other forms of grayware | accessdate=2007-01-20 | format=PDF }}</ref> Often grayware performs a variety of undesired actions such as irritating users with [[pop-up ad|pop-up]] windows, tracking user habits and unnecessarily exposing computer vulnerabilities to attack. |
|||
* [[Spyware]] is software that installs components on a computer for the purpose of recording Web surfing habits (primarily for marketing purposes). Spyware sends this information to its author or to other interested parties when the computer is online. Spyware often downloads with items identified as 'free downloads' and does not notify the user of its existence or ask for permission to install the components. The information spyware components gather can include user keystrokes, which means that private information such as login names, passwords, and credit card numbers are vulnerable to theft. |
|||
* [[Adware]] is software that displays advertising banners on Web browsers such as Internet Explorer and Mozilla Firefox. While not categorized as malware, many users consider adware invasive. Adware programs often create unwanted effects on a system, such as annoying popup ads and the general degradation in either network connection or system performance. Adware programs are typically installed as separate programs that are bundled with certain free software. Many users inadvertently agree to installing adware by accepting the [[End User License Agreement|End User License Agreement (EULA)]] on the free software. Adware are also often installed in tandem with spyware programs. Both programs feed off each other's functionalities: spyware programs profile users' Internet behavior, while adware programs display targeted ads that correspond to the gathered user profile. |
|||
==Web and spam== |
|||
<div style="margin:1% 0 1% 1%; padding:0.5%; width:30%; border:1px solid #bbb; float:right; font-family:monospace; font-size:90%"><pre> |
|||
<iframe |
|||
src="http://example.net/out.php?s_id=11" |
|||
width=0 height=0 /></pre> |
|||
<span style="font:90% sans-serif;">If an intruder can gain access to a website, it can be hijacked with a single HTML element.<ref>{{cite video|people=Zittrain, Jonathan (Mike Deehan, producer)|title=Berkman Book Release: The Future of the Internet — And How to Stop It|location=Cambridge, MA, USA|url=http://cyber.law.harvard.edu/interactive/events/2008/04/zittrain|medium=video/audio|publisher=Berkman Center, The President and Fellows of Harvard College|date=2008-04-17|accessdate=2008-04-21}}</ref></span></div> |
|||
The [[World Wide Web]] is a criminals' preferred pathway for spreading malware. Today's [[web threats]] use combinations of malware to create infection chains. About one in ten Web pages may contain malicious code.<ref>{{cite news|title=Google searches web's dark side|url=http://news.bbc.co.uk/2/hi/technology/6645895.stm|date=May 11, 2007|publisher=BBC News|accessdate=2008-04-26}}</ref> |
|||
===Wikis and blogs=== |
|||
Attackers may use wikis and blogs to advertise links that lead to malware sites.<ref>{{cite web|author=Sharon Khare |url=http://www.tech2.com/india/news/telecom/wikipedia-hijacked-to-spread-malware/2667/0 |title=Wikipedia Hijacked to Spread Malware |location=India |publisher=Tech2.com |date= |accessdate=2010-04-15}}</ref> |
|||
Wiki and blog servers can also be attacked directly. In 2010, Network Solutions was compromised<ref>{{cite web|url=http://blog.sucuri.net/2010/05/continuing-attacks-at-network-solutions.html |title=Continuing attacks at Network Solutions? | Sucuri |publisher=Blog.sucuri.net |date=2010-05-07 |accessdate=2010-11-14}}</ref><ref>{{cite news|title=Attacks against Wordpress|url=http://blog.sucuri.net/2010/05/new-attack-today-against-wordpress.html|date=May 11, 2010|publisher=Sucuri Security|accessdate=2010-04-26}}</ref> and some hosted sites became a path to malware and spam. |
|||
===Targeted SMTP threats=== |
|||
Targeted [[Simple Mail Transfer Protocol|SMTP]] [[Threat (computer)|threats]] also represent an emerging attack vector through which malware is propagated. As users adapt to widespread [[spam (electronic)|spam]] attacks, cybercriminals distribute [[crimeware]] to target one specific organization or industry, often for financial gain.<ref>[http://www.avinti.com/download/market_background/whitepaper_email_crimeware_protection.pdf "Protecting Corporate Assets from E-mail Crimeware," Avinti, Inc., p.1]{{dead link|date=April 2010}}</ref> |
|||
==See also== |
|||
{{Portal|Computing|Computer security}} |
|||
{{div col|colwidth=20em}} |
|||
* [[Computer crime]] |
|||
* [[Computer insecurity]] |
|||
* [[Cyber spying]] |
|||
* [[Firewall (computing)]] |
|||
* [[Identity theft]] |
|||
* [[Industrial espionage]] |
|||
* [[It risk]] |
|||
* [[Malvertising]] |
|||
* [[Play mp3.exe (trojan)]] |
|||
* [[Privacy-invasive software]] |
|||
* [[Web application#Writing web applications|Security in Web applications]] |
|||
* [[Social engineering (security)]] |
|||
* [[Spy software]] |
|||
* [[Targeted threat]] |
|||
* [[:Category:Web security exploits|Web security exploits]] |
|||
* [[Web server#Overload causes|Web server overload causes]] |
|||
* [[White-collar crime]] |
|||
{{div col end}} |
|||
==References== |
|||
{{reflist|colwidth=30em}} |
|||
==External links== |
|||
{{Wiktionary|malware}} |
|||
* [http://www.cert.org/homeusers/HomeComputerSecurity/ Home Computer Security - Carnegie Mellon Software Institute] |
|||
*{{dmoz|Computers/Security/Malicious_Software|Malicious Software}} |
|||
* [http://news.bbc.co.uk/2/hi/technology/7232752.stm Malicious Programs Hit New High] – retrieved February 8, 2008 |
|||
* [http://www.malware.com.br/ Malware Block List] |
|||
* [http://datalossdb.org/ Open Security Foundation Data Loss Database] |
|||
* [http://www.ic3.gov/default.aspx/ Internet Crime Complaint Center] |
|||
* [http://www.antiphishing.org/reports/APWG_CrimewareReport.pdf US Department of Homeland Security Identity Theft Technology Council report "The Crimeware Landscape: Malware, Phishing, Identity Theft and Beyond"] |
|||
* [http://www.microsoft.com/emea/itsshowtime/sessionh.aspx?videoid=359 Video: Mark Russinovich – Advanced Malware Cleaning] |
|||
* [[Malcon|MalCon]], [http://www.malcon.org International Malware Conference (convention), focused specifically on Malware development, research and containment.] |
|||
* Jamie Crapanzano (2003): [http://www.sans.org/reading_room/whitepapers/malicious/deconstructing-subseven-trojan-horse-choice_953 "Deconstructing SubSeven, the Trojan Horse of Choice"], SANS Institute, Retrieved on 2011-05-23 |
|||
* [http://blog.operationreality.org/2011/08/15/pay-per-install-the-commoditization-of-malware-distribution/ The commercialization of malware distribution: Pay per install] |
|||
{{Malware}} |
|||
[[Category:Malware| ]] |
|||
[[ar:برمجيات خبيثة]] |
|||
[[az:Ziyankar proqram]] |
|||
[[zh-min-nan:Pháiⁿ-thé]] |
|||
[[bs:Malware]] |
|||
[[ca:Malware]] |
|||
[[cs:Malware]] |
|||
[[da:Malware]] |
|||
[[de:Schadprogramm]] |
|||
[[et:Kurivara]] |
|||
[[el:Κακόβουλο λογισμικό]] |
|||
[[es:Malware]] |
|||
[[eu:Malware]] |
|||
[[fa:بدافزار]] |
|||
[[fr:Logiciel malveillant]] |
|||
[[ga:Bogearraí mailíseacha]] |
|||
[[ko:악성코드]] |
|||
[[hy:Վնասակար ծրագիր]] |
|||
[[hi:मैलवेयर]] |
|||
[[hr:Zloćudni softver]] |
|||
[[id:Perangkat perusak]] |
|||
[[it:Malware]] |
|||
[[he:נוזקה]] |
|||
[[kn:ಮಾಲ್ವೇರ್]] |
|||
[[hu:Malware]] |
|||
[[mk:Злонамерен програм]] |
|||
[[ml:മാൽവെയർ]] |
|||
[[ms:Perisian perosak]] |
|||
[[my:မောလ်ဝဲလ်]] |
|||
[[nl:Malware]] |
|||
[[ja:マルウェア]] |
|||
[[no:Malware]] |
|||
[[nn:Malware]] |
|||
[[pl:Złośliwe oprogramowanie]] |
|||
[[pt:Malware]] |
|||
[[ro:Software rău intenționat]] |
|||
[[ru:Вредоносная программа]] |
|||
[[sq:Malware]] |
|||
[[simple:Malware]] |
|||
[[sk:Malware]] |
|||
[[sr:Малвер]] |
|||
[[sh:Malware]] |
|||
[[fi:Haittaohjelma]] |
|||
[[sv:Malware]] |
|||
[[ta:தீம்பொருள்]] |
|||
[[th:มัลแวร์]] |
|||
[[tr:Kötücül yazılım (malware)]] |
|||
[[bug:Malware]] |
|||
[[uk:Шкідливий програмний засіб]] |
|||
[[ur:مصنعخبیث]] |
|||
[[vi:Phần mềm ác ý]] |
|||
[[zh:恶意软件]] |
|||
Revision as of 01:36, 16 February 2012
Malware, short for malicious software, is software (or script or code) designed to disrupt computer operation, gather sensitive information, or gain unauthorized access to computer systems. It is a general term used to describe any kind of software or code specifically designed to exploit a computer, or the data it contains, without consent.[1] The expression is a general term used by computer professionals to mean a variety of forms of hostile, intrusive, or annoying software.[2]
Malware includes computer viruses, worms, trojan horses, spyware, dishonest adware, most rootkits, and other malicious programs. In law, malware is sometimes known as a computer contaminant, for instance in the legal codes of several U.S. states, including California and West Virginia.[3][4]
Malware is not the same as defective software, that is, software that has a legitimate purpose but contains harmful bugs. Sometimes, malware is disguised as genuine software, and may come from an official site. Therefore, some security programs may call malware "potentially unwanted programs" or "PUP". Though a computer virus is malware that can reproduce itself, the term is sometimes used erroneously to refer to the entire category.
Proliferation
Preliminary results from Symantec published in 2008 suggested that "the release rate of malicious code and other unwanted programs may be exceeding that of legitimate software applications."[5] According to F-Secure, "As much malware [was] produced in 2007 as in the previous 20 years altogether."[6] Malware's most common pathway from criminals to users is through the Internet: primarily by e-mail and the World Wide Web.[7]
The prevalence of malware as a vehicle for Internet crime, along with the challenge of anti-malware software to keep up with the continuous stream of new malware, has seen the adoption of a new mindset for individuals and businesses using the Internet. With the amount of malware currently being distributed, it follows that some percentage of computers (that are connected to an Internet connection) will always be infected.
For businesses, this means that they need to find a way to operate despite this problem. The result is a greater emphasis on back-office protection systems designed to protect against advanced malware operating on customers' computers.[8]
On March 29, 2010, Symantec Corporation named Shaoxing, China, as the world's malware capital.[9] A 2011 study from the University of California, Berkeley, and the Madrid Institute for Advanced Studies published an article in Software Development Technologies, examining how entrepreneurial crackers are helping enable the spread of malware by offering access to computers for a price. They charge from $7 to $180 per thousand infections to make up an informal underground Pay-Per-Install (PPI) industry. The study's authors identified more than 57 malware “families," including spam bots, fake antivirus programs, information-stealing trojans, denial-of-service bots and adware. To avoid detection by anti-virus software, malware distributed by PPI services are frequently updated, with one observed family of malware updating up to twice a day.
Although most common families of malware targeted both Europe and the United States, there were some families with a single-country focus and some families with no geographic bias. Microsoft reported in May 2011 that one in every 14 downloads from the Internet may now contain malware code according to the Wall Street Journal. Social media, and Facebook in particular, are seeing a rise in the number of tactics used to spread malware to computers.[10]
Purposes
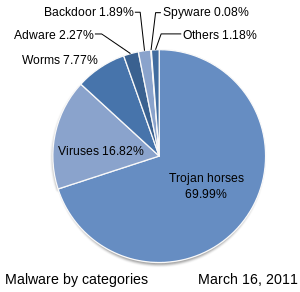
Many early infectious programs, including the first Internet Worm and a number of MS-DOS viruses, were written as experiments or pranks. They were generally intended to be harmless or merely annoying, rather than to cause serious damage to computer systems. In some cases, the perpetrator did not realize how much harm his or her creations would do. Young programmers learning about viruses and their techniques wrote them simply for practice, or to see how far they could spread. As late as 1999, widespread viruses such as the Melissa virus and the David virus appear to have been written chiefly as pranks. The first mobile phone virus, Cabir, appeared in 2004.
Hostile intent related to vandalism can be found in programs designed to cause harm or data loss. Many DOS viruses, and the Windows ExploreZip worm, were designed to destroy files on a hard disk, or to corrupt the file system by writing invalid data to them. Network-borne worms such as the 2001 Code Red worm or the Ramen worm fall into the same category. Designed to vandalize web pages, worms may seem like the online equivalent to graffiti tagging, with the author's alias or affinity group appearing everywhere the worm goes.[citation needed]
Since the rise of widespread broadband Internet access, malicious software has been designed for a profit (e.g. forced advertising). For instance, since 2003, the majority of widespread viruses and worms have been designed to take control of users' computers for black-market exploitation.[11] Infected "zombie computers" are used to send email spam, to host contraband data such as child pornography,[12] or to engage in distributed denial-of-service attacks as a form of extortion.[13]
Another strictly for-profit category of malware has emerged in spyware -- programs designed to monitor users' web browsing, display unsolicited advertisements, or redirect affiliate marketing revenues to the spyware creator. Spyware programs do not spread like viruses; they are, in general, installed by exploiting security holes or are packaged with user-installed software, such as peer-to-peer applications.
Infectious malware: viruses and worms
The best-known types of malware, viruses and worms, are known for the manner in which they spread, rather than any other particular behavior. The term computer virus is used for a program that has infected some executable software and, when run, causes the virus to spread to other executables. Viruses may also contain a payload that performs other actions, often malicious. On the other hand, a worm is a program that actively transmits itself over a network to infect other computers. It too may carry a payload.
These definitions lead to the observation that a virus requires user intervention to spread, whereas a worm spreads itself automatically. Using this distinction, infections transmitted by email or Microsoft Word documents, which rely on the recipient opening a file or email to infect the system, would be classified as viruses rather than worms.
Some writers in the trade and popular press misunderstand this distinction and use the terms interchangeably.
Capsule history of viruses and worms
Before Internet access became widespread, viruses spread on personal computers by infecting the executable boot sectors of floppy disks. By inserting a copy of itself into the machine code instructions in these executables, a virus causes itself to be run whenever a program is run or the disk is booted. Early computer viruses were written for the Apple II and Macintosh, but they became more widespread with the dominance of the IBM PC and MS-DOS system. Executable-infecting viruses are dependent on users exchanging software or boot-able floppies, so they spread rapidly in computer hobbyist circles.
The first worms, network-borne infectious programs, originated not on personal computers, but on multitasking Unix systems. The first well-known worm was the Internet Worm of 1988, which infected SunOS and VAX BSD systems. Unlike a virus, this worm did not insert itself into other programs. Instead, it exploited security holes (vulnerabilities) in network server programs and started itself running as a separate process. This same behaviour is used by today's worms as well.
With the rise of the Microsoft Windows platform in the 1990s, and the flexible macros of its applications, it became possible to write infectious code in the macro language of Microsoft Word and similar programs. These macro viruses infect documents and templates rather than applications (executables), but rely on the fact that macros in a Word document are a form of executable code.
Today, worms are most commonly written for the Windows OS, although a few like Mare-D[14] and the Lion worm[15] are also written for Linux and Unix systems. Worms today work in the same basic way as 1988's Internet Worm: they scan the network and leverage vulnerable computers to replicate. Because they need no human intervention, worms can spread with incredible speed. The SQL Slammer infected thousands of computers in a few minutes.[16]
Concealment: Trojan horses, rootkits, and backdoors
Trojan horses
For a malicious program to accomplish its goals, it must be able to run without being detected, shut down, or deleted by the user or security software. When a malicious program is disguised as something normal or desirable, users may be tempted to install it without realizing it. This is the technique of the Trojan horse or trojan. In broad terms, a Trojan horse is any program that invites the user to run it, concealing a harmful or malicious payload. The payload may take effect immediately and can lead to many undesirable effects, such as deleting the user's files or installing additional harmful software.
One of the most common ways that spyware is distributed is as a Trojan horse, bundled with a piece of desirable software that the user downloads from the Internet. When the user installs the software, the spyware is installed as well. Spyware authors who attempt to act in a legal fashion may include an end-user license agreement that states the behavior of the spyware in loose terms, which the users are unlikely to read or understand.
Trojans are most commonly used for marketing. Today's advanced trojans are capable of taking complete control of a Web browser and have even been known to add false exceptions to a browser's security settings. They may also modify a computer's Windows Registry.
Rootkits
Once a malicious program is installed on a system, it is essential that it stays concealed, to avoid detection and disinfection. The same is true when a human attacker breaks into a computer directly. Techniques known as rootkits allow this concealment, by modifying the host's operating system so that the malware is hidden from the user. Rootkits can prevent a malicious process from being visible in the system's list of processes, or keep its files from being read. Originally, a rootkit was a set of tools installed by a human attacker on a Unix system, allowing the attacker to gain administrator (root) access. Today, the term is used more generally for concealment routines in a malicious program.
Some malicious programs contain routines to defend against removal, not merely to hide themselves, but to repel attempts to remove them. An early example of this behavior is recorded in the Jargon File tale of a pair of programs infesting a Xerox CP-V time sharing system:
- Each ghost-job would detect the fact that the other had been killed, and would start a new copy of the recently slain program within a few milliseconds. The only way to kill both ghosts was to kill them simultaneously (very difficult) or to deliberately crash the system.[17]
Similar techniques are used by some modern malware, where the malware starts a number of processes that monitor and restore one another as needed. In the event a user running Microsoft Windows is infected with this kind of malware, if they wish to manually stop it, they could use Task Manager's 'processes' tab to find the main process (the one that spawned the "resurrector process(es)"), and use the 'end process tree' function, which would kill not only the main process, but the "resurrector(s)" as well, since they were started by the main process. Some malware programs use other techniques, such as naming the infected file similar to a legitimate or trustworthy file (expl0rer.exe VS explorer.exe).
Backdoors
A backdoor is a method of bypassing normal authentication procedures. Once a system has been compromised (by one of the above methods, or in some other way), one or more backdoors may be installed in order to allow easier access in the future. Backdoors may also be installed prior to malicious software, to allow attackers entry.
The idea has often been suggested that computer manufacturers preinstall backdoors on their systems to provide technical support for customers, but this has never been reliably verified. Crackers typically use backdoors to secure remote access to a computer, while attempting to remain hidden from casual inspection. To install backdoors crackers may use Trojan horses, worms, or other methods.
Malware for profit: spyware, botnets, keystroke loggers, and "Ransom" Malware
During the 1980s and 1990s, it was usually taken for granted that malicious programs were created as a form of vandalism or prank. More recently, the greater share of malware programs have been written with a profit motive (financial or otherwise) in mind. This can be taken as the malware authors' choice to monetize their control over infected systems: to turn that control into a source of revenue.
Spyware programs are commercially produced for the purpose of gathering information about computer users, showing them pop-up ads, or altering web-browser behavior for the financial benefit of the spyware creator. For instance, some spyware programs redirect search engine results to paid advertisements. Others, often called "stealware" by the media, overwrite affiliate marketing codes so that revenue is redirected to the spyware creator rather than the intended recipient.
Spyware programs are sometimes installed as Trojan horses. They differ in that their creators present themselves as businesses (i.e. by selling advertising space on the pop-ups created by the malware). Most programs of this kind present the user with an end-user license agreement that purportedly protects the creator from prosecution under computer contaminant laws. However, spyware EULAs have not yet been upheld in court.
Another way that financially motivated malware creators can profit from infecting computers is to directly use the infected computers to work for them. The infected computers are used as proxies to send out spam messages. A computer left in this state is often known as a zombie computer. The advantage to spammers of using infected computers is they provide anonymity, protecting the spammer from prosecution. Spammers have also used infected PCs to target anti-spam organizations with distributed denial-of-service attacks. In order to coordinate the activity of many infected computers, attackers have used coordinating systems known as botnets. In a botnet, the malware or malbot logs in to an Internet Relay Chat channel or other chat system. The attacker can then give instructions to all the infected systems simultaneously. Botnets can also be used to push upgraded malware to the infected systems, keeping them resistant to antivirus software or other security measures.
It is possible for a malware creator to profit by stealing sensitive information from a victim. One way this is accomplished is by malware programs that install a key logger, which record the user's keystrokes when entering a password, credit card number, or any other key-entered data. This is then transmitted to the malware creator, enabling them to commit credit card fraud or other theft or impersonation. Similarly, malware may copy the CD key or password for online games, allowing the creator to steal accounts or virtual items.
"Ransom" Malware serve as another tool for attackers to profit by infecting computers, the idea behind this attack is to encrypt files on the infected computers' hard drive where the private encryption key is only accessible to the attacker, and he in turn will only surrender it for ransom money.
Data-stealing malware
Data-stealing malware is a web threat that divest victims of personal and proprietary information with the intent of monetizing stolen data through direct use or underground distribution. Content security threats that fall under this umbrella include keyloggers, screen scrapers, spyware, adware, backdoors, and bots. The term does not refer to activities such as spam, phishing, DNS poisoning, SEO abuse, etc. However, when these threats result in file download or direct installation, as most hybrid attacks do, files that act as agents to proxy information will fall into the data-stealing malware category.
Characteristics of data-stealing malware
Does not leave traces of the event
- The malware is typically stored in a cache that is routinely flushed
- The malware may be installed via a drive-by-download process
- The website hosting the malware as well as the malware is generally temporary or rogue
Frequently changes and extends its functions
- It is difficult for antivirus software to detect final payload attributes due to the combination(s) of malware components
- The malware uses multiple file encryption levels
Thwarts Intrusion Detection Systems (IDS) after successful installation
- There are no perceivable network anomalies
- The malware hides in web traffic
- The malware is stealthier in terms of traffic and resource use
Thwarts disk encryption
- Data is stolen during decryption and display
- The malware can record keystrokes, passwords, and screenshots
Thwarts Data Loss Prevention (DLP)
- Leakage protection hinges on metadata tagging, not everything is tagged
- Miscreants can use encryption to port data
Examples of data-stealing malware
- Bancos, an info stealer that waits for the user to access banking websites then spoofs pages of the bank website to steal sensitive information.
- Gator, spyware that covertly monitors web-surfing habits, uploads data to a server for analysis then serves targeted pop-up ads.
- LegMir, spyware that steals personal information such as account names and passwords related to online games.
- Qhost, a Trojan that modifies the Hosts file to point to a different DNS server when banking sites are accessed then opens a spoofed login page to steal login credentials for those financial institutions.
Data-stealing malware incidents
- Albert Gonzalez (not to be confused with the U.S. Attorney General Alberto Gonzalez) is accused of masterminding a ring to use malware to steal and sell more than 170 million credit card numbers in 2006 and 2007—the largest computer fraud in history. Among the firms targeted were BJ's Wholesale Club, TJX, DSW Shoes, OfficeMax, Barnes & Noble, Boston Market, Sports Authority and Forever 21.[18]
- A Trojan horse program stole more than 1.6 million records belonging to several hundred thousand people from Monster Worldwide Inc’s job search service. The data was used by cybercriminals to craft phishing emails targeted at Monster.com users to plant additional malware on users’ PCs.[19]
- Customers of Hannaford Bros. Co., a supermarket chain based in Maine, were victims of a data security breach involving the potential compromise of 4.2 million debit and credit cards. The company was hit by several class-action law suits.[20]
- The Torpig Trojan has compromised and stolen login credentials from approximately 250,000 online bank accounts as well as a similar number of credit and debit cards. Other information such as email, and FTP accounts from numerous websites, have also been compromised and stolen.[21]
Controversy about assignment to spyware
There is a group of software (Alexa toolbar, Google toolbar, Eclipse data usage collector, etc.) that send data to a central server about which pages have been visited or which features of the software have been used. However differently from "classic" malware these tools document activities and only send data with the user's approval. The user may opt in to share the data in exchange to the additional features and services, or (in case of Eclipse) as the form of voluntary support for the project. Some security tools report such loggers as malware while others do not. The status of the group is questionable. Some tools like PDFCreator are more on the boundary than others because opting out has been made more complex than it could be (during the installation, the user needs to uncheck two check boxes rather than one). However also PDFCreator is only sometimes mentioned as malware and is still subject of discussions.
Vulnerability to malware
In this context, as throughout, it should be borne in mind that the “system” under attack may be of various types, e.g. a single computer and operating system, a network or an application.
Various factors make a system more vulnerable to malware:
- Homogeneity: e.g. when all computers in a network run the same operating system; upon exploiting one, one can exploit them all.
- Weight of numbers: simply because the vast majority of existing malware is written to attack Windows systems, then Windows systems are more vulnerable to succumbing to malware attacks (regardless of the security strengths or weaknesses of Windows itself).
- Defects: malware leveraging defects in the operating system design.
- Unconfirmed code: code from a floppy disk, CD-ROM or USB device may be executed without the user’s permission.
- Over-privileged users: some systems allow all users to modify their internal structures. This was the standard operating procedure for early microcomputer and home computer systems, where there was no distinction between an Administrator or root, and a regular user of the system.
- Over-privileged code: some systems allow code executed by a user to access all rights of that user. Also standard operating procedure for early microcomputer and home computer systems.
Use of the same operating system
An oft-cited cause of vulnerability of networks is consistent use of the same operating system.[22] For example, Microsoft Windows or Apple Mac have such a large share of the market that concentrating on either could enable an exploited vulnerability to subvert a large number of systems. Instead, introducing diversity, purely for the sake of robustness, could increase short-term costs for training and maintenance. However, having a few diverse nodes would deter total shutdown of the network, and allow those nodes to help with recovery of the infected nodes. Such separate, functional redundancy could avoid the cost of a total shutdown.
Software bugs
Most systems contain bugs, or loopholes, which may be exploited by malware. A typical example is the buffer-overrun weakness, in which an interface designed to store data, in a small area of memory, allows the caller to supply more data than will fit. This extra data then overwrites the interface's own executable structure (past the end of the buffer and other data). In this manner, malware can force the system to execute malicious code, by replacing legitimate code with its own payload of instructions (or data values) copied into live memory, outside the buffer area.
Originally, PCs had to be booted from floppy disks, and until recently it was common for this to be the default Boot_device#Boot_devices_.28IBM_PC.29. This meant that a corrupt floppy disk could subvert the computer during booting, and the same applies to CDs. Although that is now less common, it is still possible to forget that one has changed the default, and rare that a BIOS makes one confirm a boot from removable media.
Over-Privileged Users
In some systems, System administrator users are over-privileged by design, in the sense that they are allowed to modify internal structures of the system. In some environments, users are over-privileged because they have been inappropriately granted administrator or equivalent status. This is primarily a configuration decision, but on Microsoft Windows systems the default configuration is to over-privilege the user. This situation exists due to decisions made by Microsoft to prioritize compatibility with older systems above security configuration in newer systems[citation needed] and because typical applications were developed without the under-privileged users in mind. As privilege escalation exploits have increased this priority is shifting for the release of Microsoft Windows Vista. As a result, many existing applications that require excess privilege (over-privileged code) may have compatibility problems with Vista. However, Vista's User Account Control feature attempts to remedy applications not designed for under-privileged users, acting as a crutch to resolve the privileged access problem inherent in legacy applications.
Malware, running as over-privileged code, can use this privilege to subvert the system. Almost all currently popular operating systems, and also many scripting allow code too many privileges, usually in the sense that when a user executes code, the system allows that code all rights of that user. This makes users vulnerable to malware in the form of e-mail attachments, which may or may not be disguised.
Given this state of affairs, users are warned only to open attachments they trust, and to be wary of code received from untrusted sources. It is also common for operating systems to be designed so that device drivers need escalated privileges, while they are supplied by more and more hardware manufacturers.
Eliminating over-privileged code
Over-privileged code dates from the time when most programs were either delivered with a computer or written in-house, and repairing it would at a stroke render most antivirus software almost redundant. It would, however, have appreciable consequences for the user interface and system management.
The system would have to maintain privilege profiles, and know which to apply for each user and program. In the case of newly installed software, an administrator would need to set up default profiles for the new code.
Eliminating vulnerability to rogue device drivers is probably harder than for arbitrary rogue executables. Two techniques, used in VMS, that can help are memory mapping only the registers of the device in question and a system interface associating the driver with interrupts from the device.
Other approaches are:
- Various forms of virtualization, allowing the code unlimited access only to virtual resources
- Various forms of sandbox or jail
- The security functions of Java, in
java.security
Such approaches, however, if not fully integrated with the operating system, would reduplicate effort and not be universally applied, both of which would be detrimental to security.
Anti-malware programs
As malware attacks become more frequent, attention has begun to shift from viruses and spyware protection, to malware protection, and programs have been developed specifically to combat them.
Anti-virus and anti-malware software commonly hooks deep into the operating system's core or kernel functions in a manner similar to how malware itself would attempt to operate, though with the user's informed permission for protecting the system. Any time the operating system does something, the anti-malware software checks that the OS is doing an approved task. This commonly slows down the operating system and/or consumes large amounts of system memory. The goal is to preempt any operations the malware may attempt on the system, including activities which might exploit bugs or trigger unexpected operating system behavior.
Anti-malware programs can combat malware in two ways:
- They can provide real time protection against the installation of malware software on a computer. This type of spyware protection works the same way as that of antivirus protection in that the anti-malware software scans all incoming network data for malware software and blocks any threats it comes across.
- Anti-malware software programs can be used solely for detection and removal of malware software that has already been installed onto a computer. This type of malware protection is normally much easier to use and more popular.[citation needed] This type of anti-malware software scans the contents of the Windows registry, operating system files, and installed programs on a computer and will provide a list of any threats found, allowing the user to choose which files to delete or keep, or to compare this list to a list of known malware components, removing files that match.
Real-time protection from malware works identically to real-time antivirus protection: the software scans disk files at download time, and blocks the activity of components known to represent malware. In some cases, it may also intercept attempts to install start-up items or to modify browser settings. Because many malware components are installed as a result of browser exploits or user error, using security software (some of which are anti-malware, though many are not) to "sandbox" browsers (essentially babysit the user and their browser) can also be effective in helping to restrict any damage done.
Website security scans
As malware also harms the compromised websites (by breaking reputation, blacklisting in search engines, etc.), some[23] companies offer the paid site scan service. Such scans periodically check the site, detecting malware, noticed security vulnerabilities, outdated software stack with known security issues, etc. The found issues are only reported to the site owner who can take means to fix them. The provider may also offer the security badge that the owner can only display if the site has been recently scanned and is "clean".
Academic research
The notion of a self-reproducing computer program can be traced back to when presented lectures that encompassed the theory and organization of complicated automata.[24] John von Neumann showed that in theory a program could reproduce itself. This constituted a plausibility result in computability theory. Fred Cohen experimented with computer viruses and confirmed Neumann's postulate. He also investigated other properties of malware (detectability, self-obfuscating programs that used rudimentary encryption that he called "evolutionary", and so on). His 1988 doctoral dissertation was on the subject of computer viruses.[25] Cohen's faculty advisor, Leonard Adleman (the A in RSA) presented a rigorous proof that, in the general case, algorithmically determining whether a virus is or is not present is Turing undecidable.[26] This problem must not be mistaken for that of determining, within a broad class of programs, that a virus is not present; this problem differs in that it does not require the ability to recognize all viruses. Adleman's proof is perhaps the deepest result in malware computability theory to date and it relies on Cantor's diagonal argument as well as the halting problem. Ironically, it was later shown by Young and Yung that Adleman's work in cryptography is ideal in constructing a virus that is highly resistant to reverse-engineering by presenting the notion of a cryptovirus.[27] A cryptovirus is a virus that contains and uses a public key and randomly generated symmetric cipher initialization vector (IV) and session key (SK). In the cryptoviral extortion attack, the virus hybrid encrypts plaintext data on the victim's machine using the randomly generated IV and SK. The IV+SK are then encrypted using the virus writer's public key. In theory the victim must negotiate with the virus writer to get the IV+SK back in order to decrypt the ciphertext (assuming there are no backups). Analysis of the virus reveals the public key, not the IV and SK needed for decryption, or the private key needed to recover the IV and SK. This result was the first to show that computational complexity theory can be used to devise malware that is robust against reverse-engineering.
A growing area of computer virus research is to mathematically model the infection behavior of worms using models such as Lotka–Volterra equations, which has been applied in the study of biological virus. Various virus propagation scenarios have been studied by researchers such as propagation of computer virus, fighting virus with virus like predator codes,[28][29] effectiveness of patching etc.
Behavioral malware detection has been a particularly lively research area lately. Most approaches to behavioral detection are based on analysis of system call dependencies. The executed binary is traced using strace or more precise taint analysis to compute data-flow dependencies among system calls. The result is a directed graph such that nodes are system calls, and edges represent dependencies. For example, if a result returned by system call (either directly as a result or indirectly through output parameters) is later used as a parameter of system call . The origins of the idea to use system calls to analyze software can be found in the work of Forrest et al.[30] Christodorescu et al.[31] point out that malware authors cannot easily reorder system calls without changing the semantics of the program, which makes system call dependency graphs suitable for malware detection. They compute a difference between malware and goodware system call dependency graphs and use the resulting graphs for detection, achieving high detection rates. Kolbitsch et al.[32] precompute symbolic expressions and evaluate them on the syscall parameters observed at runtime. They detect dependencies by observing whether the result obtained by evaluation matches the parameter values observed at runtime. Malware is detected by comparing the dependency graphs of the training and test sets. Fredrikson et al.[33] describe an approach that uncovers distinguishing features in malware system call dependency graphs. They extract significant behaviors using concept analysis and leap mining.[34] Babic et al.[35] recently proposed a novel approach for both malware detection and classification based on grammar inference of tree automata. Their approach infers an automaton from dependency graphs, and they show how such an automaton could be used for detection and classification of malware.
Grayware
Grayware[36] (or Greynet) is a general term sometimes used as a classification for applications that behave in a manner that is annoying or undesirable, and yet less serious or troublesome than malware.[37] Grayware encompasses spyware, adware, dialers, joke programs, remote access tools, and any other unwelcome files and programs apart from viruses that are designed to harm the performance of computers on one's network. The term has been in use since at least as early as September 2004.[38]
Grayware refers to applications or files that are not classified as viruses or trojan horse programs, but can still negatively affect the performance of the computers on a network and introduce significant security risks to an organization.[39] Often grayware performs a variety of undesired actions such as irritating users with pop-up windows, tracking user habits and unnecessarily exposing computer vulnerabilities to attack.
- Spyware is software that installs components on a computer for the purpose of recording Web surfing habits (primarily for marketing purposes). Spyware sends this information to its author or to other interested parties when the computer is online. Spyware often downloads with items identified as 'free downloads' and does not notify the user of its existence or ask for permission to install the components. The information spyware components gather can include user keystrokes, which means that private information such as login names, passwords, and credit card numbers are vulnerable to theft.
- Adware is software that displays advertising banners on Web browsers such as Internet Explorer and Mozilla Firefox. While not categorized as malware, many users consider adware invasive. Adware programs often create unwanted effects on a system, such as annoying popup ads and the general degradation in either network connection or system performance. Adware programs are typically installed as separate programs that are bundled with certain free software. Many users inadvertently agree to installing adware by accepting the End User License Agreement (EULA) on the free software. Adware are also often installed in tandem with spyware programs. Both programs feed off each other's functionalities: spyware programs profile users' Internet behavior, while adware programs display targeted ads that correspond to the gathered user profile.
Web and spam
<iframe src="http://example.net/out.php?s_id=11" width=0 height=0 />If an intruder can gain access to a website, it can be hijacked with a single HTML element.[40]
The World Wide Web is a criminals' preferred pathway for spreading malware. Today's web threats use combinations of malware to create infection chains. About one in ten Web pages may contain malicious code.[41]
Wikis and blogs
Attackers may use wikis and blogs to advertise links that lead to malware sites.[42]
Wiki and blog servers can also be attacked directly. In 2010, Network Solutions was compromised[43][44] and some hosted sites became a path to malware and spam.
Targeted SMTP threats
Targeted SMTP threats also represent an emerging attack vector through which malware is propagated. As users adapt to widespread spam attacks, cybercriminals distribute crimeware to target one specific organization or industry, often for financial gain.[45]
See also
- Computer crime
- Computer insecurity
- Cyber spying
- Firewall (computing)
- Identity theft
- Industrial espionage
- It risk
- Malvertising
- Play mp3.exe (trojan)
- Privacy-invasive software
- Security in Web applications
- Social engineering (security)
- Spy software
- Targeted threat
- Web security exploits
- Web server overload causes
- White-collar crime
References
- ^ http://www.us-cert.gov/control_systems/pdf/undirected_attack0905.pdf
- ^ "Defining Malware: FAQ". technet.microsoft.com. Retrieved 2009-09-10.
- ^ National Conference of State Legislatures Virus/Contaminant/Destructive Transmission Statutes by State
- ^ "§18.2-152.4:1 Penalty for Computer Contamination" (PDF). Joint Commission on Technology and Science. Retrieved 2010-09-17.
- ^ "Symantec Internet Security Threat Report: Trends for July–December 2007 (Executive Summary)" (PDF). XIII. Symantec Corp. April 2008: 29. Retrieved 2008-05-11.
{{cite journal}}: Cite journal requires|journal=(help) - ^ "F-Secure Reports Amount of Malware Grew by 100% during 2007" (Press release). F-Secure Corporation. December 4, 2007. Retrieved 2007-12-11.
- ^ "F-Secure Quarterly Security Wrap-up for the first quarter of 2008". F-Secure. March 31, 2008. Retrieved 2008-04-25.
- ^ "Continuing Business with Malware Infected Customers". Gunter Ollmann. October 2008.
- ^ "Symantec names Shaoxing, China as world's malware capital". Engadget. Retrieved 2010-04-15.
- ^ Rooney, Ben (2011-05-23). "Malware Is Posing Increasing Danger". Wall Street Journal.
- ^ "Malware Revolution: A Change in Target". March 2007.
- ^ "Child Porn: Malware's Ultimate Evil". November 2009.
- ^ PC World - Zombie PCs: Silent, Growing Threat.
- ^ Nick Farrell (20 February 2006). "Linux worm targets PHP flaw". The Register. Retrieved 19 May 2010.
- ^ John Leyden (March 28, 2001). "Highly destructive Linux worm mutating". The Register. Retrieved 19 May 2010.
- ^ "Aggressive net bug makes history". BBC News. February 3, 2003. Retrieved 19 May 2010.
- ^ "Catb.org". Catb.org. Retrieved 2010-04-15.
- ^ "Gonzalez, Albert — Indictment 080508" (PDF). US Department of Justice Press Office. pp. 01–18. Retrieved 2010-.
{{cite web}}: Check date values in:|accessdate=(help) - ^ Keizer, Gregg (2007) Monster.com data theft may be bigger
- ^ Vijayan, Jaikumar (2008) Hannaford hit by class-action lawsuits in wake of data breach disclosure
- ^ BBC News: Trojan virus steals banking info
- ^ "LNCS 3786 - Key Factors Influencing Worm Infection", U. Kanlayasiri, 2006, web (PDF): SL40-PDF.
- ^ An example of the web site scan proposal
- ^ John von Neumann, "Theory of Self-Reproducing Automata", Part 1: Transcripts of lectures given at the University of Illinois, December 1949, Editor: A. W. Burks, University of Illinois, USA, 1966.
- ^ Fred Cohen, "Computer Viruses", PhD Thesis, University of Southern California, ASP Press, 1988.
- ^ L. M. Adleman, "An Abstract Theory of Computer Viruses", Advances in Cryptology---Crypto '88, LNCS 403, pp. 354-374, 1988.
- ^ A. Young, M. Yung, "Cryptovirology: Extortion-Based Security Threats and Countermeasures," IEEE Symposium on Security & Privacy, pp. 129-141, 1996.
- ^ H. Toyoizumi, A. Kara. Predators: Good Will Mobile Codes Combat against Computer Viruses. Proc. of the 2002 New Security Paradigms Workshop, 2002
- ^ Zakiya M. Tamimi, Javed I. Khan, Model-Based Analysis of Two Fighting Worms, IEEE/IIU Proc. of ICCCE '06, Kuala Lumpur, Malaysia, May 2006, Vol-I, p. 157-163.
- ^ S. Forrest, S. A. Hofmeyr, A. Somayaji, T. A. Longstaff, Thomas A.: A Sense of Self for Unix Processes, Proc. of the 1996 IEEE Symp. on Security and Privacy, 1996, p. 120-129.
- ^ M. Christodorescu, S. Jha, C. Kruegel: Mining specifications of malicious behavior, Proc. of the 6th joint meeting of the European software engineering conf. and the ACM SIGSOFT symp. on The foundations of software engineering, 2007, p. 5-14
- ^ C. Kolbitsch, P. Milani, C. Kruegel, E. Kirda, X. Zhou, and X. Wang: Effective and Efficient Malware Detection at the End Host, The 18th USENIX Security Symposium, 2009.
- ^ M. Fredrikson, S. Jha, M. Christodorescu, R. Sailer, and X. Yan: Synthesizing Near-Optimal Malware Specifications from Suspicious Behaviors, Proc. of the 2010 IEEE Symposium on Security and Privacy, 2010, p. 45-60.
- ^ X. Yan, H. Cheng, J. Han, and P. S. Yu: Mining significant graph patterns by leap search in Proceedings of the 2008 ACM SIGMOD International Conference on Management of Data (SIGMOD’08). New York, NY, USA: ACM Press, 2008, pp. 433-444
- ^ D. Babic, D. Reynaud, and D. Song: Malware Analysis with Tree Automata Inference, in Proceedings of the 23rd Int. Conference on Computer Aided Verification, 2011, Springer.
- ^ "Other meanings". Archived from the original on June 30, 2007. Retrieved 2007-01-20. The term "grayware" is also used to describe a kind of Native American pottery and has also been used by some working in computer technology as slang for the human brain. "grayware definition". TechWeb.com. Retrieved 2007-01-02.
- ^ "Greyware". What is greyware? - A word definition from the Webopedia Computer Dictionary. Retrieved 2006-06-05.
- ^ Antony Savvas. "The network clampdown". Computer Weekly. Retrieved 2007-01-20.
- ^ "Fortinet WhitePaper Protecting networks against spyware, adware and other forms of grayware" (PDF). Retrieved 2007-01-20.
- ^ Zittrain, Jonathan (Mike Deehan, producer) (2008-04-17). Berkman Book Release: The Future of the Internet — And How to Stop It (video/audio). Cambridge, MA, USA: Berkman Center, The President and Fellows of Harvard College. Retrieved 2008-04-21.
- ^ "Google searches web's dark side". BBC News. May 11, 2007. Retrieved 2008-04-26.
- ^ Sharon Khare. "Wikipedia Hijacked to Spread Malware". India: Tech2.com. Retrieved 2010-04-15.
- ^ "Continuing attacks at Network Solutions? | Sucuri". Blog.sucuri.net. 2010-05-07. Retrieved 2010-11-14.
- ^ "Attacks against Wordpress". Sucuri Security. May 11, 2010. Retrieved 2010-04-26.
- ^ "Protecting Corporate Assets from E-mail Crimeware," Avinti, Inc., p.1[dead link]
External links
- Home Computer Security - Carnegie Mellon Software Institute
- Template:Dmoz
- Malicious Programs Hit New High – retrieved February 8, 2008
- Malware Block List
- Open Security Foundation Data Loss Database
- Internet Crime Complaint Center
- US Department of Homeland Security Identity Theft Technology Council report "The Crimeware Landscape: Malware, Phishing, Identity Theft and Beyond"
- Video: Mark Russinovich – Advanced Malware Cleaning
- MalCon, International Malware Conference (convention), focused specifically on Malware development, research and containment.
- Jamie Crapanzano (2003): "Deconstructing SubSeven, the Trojan Horse of Choice", SANS Institute, Retrieved on 2011-05-23
- The commercialization of malware distribution: Pay per install




