XKeyscore: Difference between revisions
Socrates2008 (talk | contribs) →NSA response: Not clear if this quote is cited |
Exceptional references on the slideshow. |
||
| Line 17: | Line 17: | ||
According to documents released by ''The Guardian'', the tool has the ability to query, in real time, "strong selectors", such as email, or "soft selectors", such as content{{Citation needed|date=August 2013}}. The tool also gives the analyst the abilities to look for "anomalies"; without any specific person attached{{Citation needed|date=August 2013}}, it lists the example of a German speaker in Pakistan as an example of such. It also has the ability to detect encrypted activity such as "all [[Pretty Good Privacy|PGP]] usage in Iran.".<ref name =ars1>{{cite news |url=http://arstechnica.com/tech-policy/2013/08/nsas-internet-taps-can-find-systems-to-hack-track-vpns-and-word-docs/|title=NSA's Internet Taps Can Find Systems to Hack, Track VPNs and Word Docs{{spaced ndash}} X-Keyscore Gives NSA the Ability to Find and Exploit Vulnerable Systems|author=Gallagher, Sean|date=August 1, 2013| publisher = [[Ars Technica]] | accessdate= August 4, 2013}}</ref> The caveat given is that very broad queries can result in too much data to transmit back to the analyst. The presentation suggests that when something of interest is discovered, that the analyst may request particular items, as required.<ref name = Guardian2/> |
According to documents released by ''The Guardian'', the tool has the ability to query, in real time, "strong selectors", such as email, or "soft selectors", such as content{{Citation needed|date=August 2013}}. The tool also gives the analyst the abilities to look for "anomalies"; without any specific person attached{{Citation needed|date=August 2013}}, it lists the example of a German speaker in Pakistan as an example of such. It also has the ability to detect encrypted activity such as "all [[Pretty Good Privacy|PGP]] usage in Iran.".<ref name =ars1>{{cite news |url=http://arstechnica.com/tech-policy/2013/08/nsas-internet-taps-can-find-systems-to-hack-track-vpns-and-word-docs/|title=NSA's Internet Taps Can Find Systems to Hack, Track VPNs and Word Docs{{spaced ndash}} X-Keyscore Gives NSA the Ability to Find and Exploit Vulnerable Systems|author=Gallagher, Sean|date=August 1, 2013| publisher = [[Ars Technica]] | accessdate= August 4, 2013}}</ref> The caveat given is that very broad queries can result in too much data to transmit back to the analyst. The presentation suggests that when something of interest is discovered, that the analyst may request particular items, as required.<ref name = Guardian2/> |
||
XKeyscore may be instrumental in the process of breaking in to a [[Virtual private network|VPN]], and to identify "exploitable" (hackable) machines via [[Tailored Access Operations|TAO]].{ |
XKeyscore may be instrumental in the process of breaking in to a [[Virtual private network|VPN]], and to identify "exploitable" (hackable) machines via [[Tailored Access Operations|TAO]].<ref name ars1/> <ref>{[[:file|https://en.wikipedia.org/wiki/File:XKeyscore_presentation_from_2008.pdf Page 17]]Further capabilities include [[Google Maps]] and web searches. It has the ability to track the source and authorship of a document that has passed though many hands.<ref name =ars1/><ref name = Guardian2/> |
||
In 2008, the following were planned for "future" capabilities: [[Voice over IP|VoIP]], and [[Exchangeable image file format|Exif]] tags. Exif tags from pictures captured from smartphones often include [[geolocation]] ([[Global Positioning System|GPS]]) data.<ref name = Guardian2/> |
In 2008, the following were planned for "future" capabilities: [[Voice over IP|VoIP]], and [[Exchangeable image file format|Exif]] tags. Exif tags from pictures captured from smartphones often include [[geolocation]] ([[Global Positioning System|GPS]]) data.<ref name = Guardian2/> |
||
Revision as of 16:13, 15 September 2013

 National Security Agency surveillance |
|---|
 |
XKeyscore is a formerly secret computer system used by the United States National Security Agency for searching and analyzing Internet data about foreign nationals across the world. The program is run jointly with other agencies including Australia's Defence Signals Directorate, and New Zealand's Government Communications Security Bureau. Its existence was revealed in July 2013 by Edward Snowden, an American citizen and former Booz Allen Hamilton employee.[1]
Revealing
The program's existence was most publicly revealed in July 2013 by Edward Snowden in The Sydney Morning Herald and O Globo newspapers, though the codename is mentioned in earlier articles, and like many other codenames can also be seen in job postings, and in the online resumes of employees.[2][3] According to O Globo, XKeyscore detects the nationality of foreigners by analyzing the language used within intercepted emails, which the paper claims has been applied to Latin America and specifically to Colombia, Ecuador, Mexico and Venezuela.[4][5] According to Der Spiegel, XKeyscore also has the ability to retroactively import several days' worth of queued metadata, and the content of communications. This article lists terms entered into a search engine as an example of the metadata XKeyscore is able to intercept.[6]
Workings
According to The Washington Post and Marc Ambinder, editor-at-large of The Week, XKeyscore is an NSA data-retrieval system which consists of a series of user interfaces, backend databases, servers and software that selects certain types of metadata that the NSA has already collected using other methods.[7][8] According to the published slides, these come from three different sources:[9]
- F6, which is the Special Collection Service (SCS), operating from a U.S. embassy or consulate overseas
- FORNSAT, which means "foreign satellite collection", and refers to intercepts from satellites that process data used by other countries
- SSO, which is the Special Source Operations division, the branch of NSA which taps cables, finds microwave paths, and otherwise collects data not generated by F6 or foreign satellites.
According to documents released by The Guardian, the tool has the ability to query, in real time, "strong selectors", such as email, or "soft selectors", such as content[citation needed]. The tool also gives the analyst the abilities to look for "anomalies"; without any specific person attached[citation needed], it lists the example of a German speaker in Pakistan as an example of such. It also has the ability to detect encrypted activity such as "all PGP usage in Iran.".[10] The caveat given is that very broad queries can result in too much data to transmit back to the analyst. The presentation suggests that when something of interest is discovered, that the analyst may request particular items, as required.[11]
XKeyscore may be instrumental in the process of breaking in to a VPN, and to identify "exploitable" (hackable) machines via TAO.Cite error: The <ref> tag has too many names (see the help page). Cite error: A <ref> tag is missing the closing </ref> (see the help page).[12][13] Among the facilities involved in the program are four bases in Australia and one in New Zealand:[12]
- Pine Gap, near Alice Springs
- Shoal Bay Receiving Station, near Darwin
- Australian Defence Satellite Communications Station, at Geraldton
- HMAS Harman, outside Canberra
- Waihopai Station, in New Zealand
A detailed commentary on an NSA presentation published in The Guardian in July 2013 states that the XKeyscore system is continuously collecting so much Internet data that it can be stored only for short periods of time. Content remains on the system for only three to five days, while metadata is stored for 30 days. The commentary also cites a document published in 2008 declaring that "At some sites, the amount of data we receive per day (20+ terabytes) can only be stored for as little as 24 hours."[14]
The NSA slides published in The Guardian during 2013 claimed that XKeyscore had played a role in capturing 300 terrorists by 2008.[11] This claim could not be substantiated as the redacted documents do not cite instances of terrorist interventions.
A 2011 report from the NSA unit in Griesheim (Germany) says that XKeyscore made it easier and more efficient to target surveillance. Previously, analysis often accessed data they were not interested in. XKeyscore allowed them to focus on the intended topics, while ignoring unrelated data. XKeyscore also proved to be an outstanding tool for tracking active groups associated with the Anonymous movement in Germany, because it allows for searching on patterns, rather than particular individuals. An analyst is able to determine when targets research new topics, or develop new behaviors.[15]
To create additional motivation, the NSA incorporated various features from computer games into the program. For instance, analysts who were especially good at using XKeyscore could acquire "skilz" points and "unlock achievements." The training units in Griesheim were apparently successful and analysts there had achieved the "highest average of skilz points" compared with all other NSA departments participating in the training program.[15]
Interpretation by The Guardian
According to The Guardian's Glenn Greenwald even low-level NSA analysts are allowed to search and listen to the communications of Americans and other people without court approval and supervision. Greenwald said low-level analysts can via systems like XKeyscore "listen to whatever emails they want, whatever telephone calls, browsing histories, Microsoft Word documents. And it's all done with no need to go to a court, with no need to even get supervisor approval on the part of the analyst."[16]
He added that the NSA's databank of collected communications years allows its analysts to search that database and to listen "to the calls or read the emails of everything that the NSA has stored, or look at the browsing histories or Google search terms that you've entered, and it also alerts them to any further activity that people connected to that email address or that IP address do in the future".[16]
NSA response
In an official statement from July 30, 2013, the NSA said there is no "unchecked analyst access to NSA collection data. Access to XKeyscore, as well as all of NSA's analytic tools, is limited to only those personnel who require access for their assigned tasks."[This quote needs a citation] The NSA also states that there are "stringent oversight and compliance mechanisms built in at several levels. One feature is the system's ability to limit what an analyst can do with a tool, based on the source of the collection and each analyst's defined responsibilities."[17]
The agency defended the program, stressing that it was only used to legally obtain information about "legitimate foreign intelligence targets in response to requirements that our leaders need for information necessary to protect our nation and its interests. [...] XKeyscore is used as a part of NSA's lawful foreign signals intelligence collection system. [...] These types of programs allow us to collect the information that enables us to perform our missions successfully -- to defend the nation and to protect U.S. and allied troops abroad."[18]
Usage in Germany
According to documents Der Spiegel acquired from Snowden, the German intelligence agencies BND (foreign intelligence) and BfV (domestic intelligence) were granted access to and used XKeyscore. In those documents the BND agency was described as the NSA's most prolific partner in information gathering.[6] This led to political discussions, after which the directors of the German intelligence agencies briefed members of the German parliamentary intelligence oversight committee on July 25, 2013. They declared that XKeyscore is used by the BND since 2007 and that the BfV uses a test version since 2012. The directors also explained that this program is not for collecting data, but only for analyzing them.[19]
-
A redacted 2008 presentation about XKeyscore. (PDF, 27.26 MB)
-
DNI Discovery options.
-
Email Address C2C Session Viewer.
-
Facebook Chat V4 Appid Example.
-
Full Log Table
-
HTTP Activity Client-to-Server.
-
User Activity Possible Queries.
-
Corporate Logos, CNN, Facebook, Twitter, et al.
-
Email Address Query Form With "Justification" Field.
-
HTTP Activity Query Form With "Justification" Field.
-
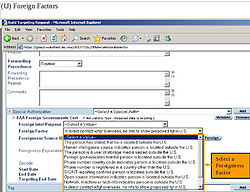
Foreignness Factors to select in the Unified Targeting Tool (UTT).
-
Boundless Informant Screen Capture listing XKeyscore as the first of the "5 top techs"
See also
References
- ^ Myers, Steven Lee; Kramer, Andrew E. (August 1, 2013). "Defiant Russia Grants Snowden Year's Asylum". The New York Times. Retrieved August 6, 2013. "Russia’s decision, which infuriated American officials, ended five weeks of legal limbo for Mr. Snowden, the former intelligence analyst wanted by the United States for leaking details of the National Security Agency’s surveillance programs, and opened a new phase of his legal and political odyssey."
- ^ Greenwald, Glenn; Ackerman, Spencer (June 27, 2013). "How the NSA Is Still Harvesting Your Online Data – Files Show Vast Scale of Current NSA Metadata Programs, with One Stream Alone Celebrating 'One Trillion Records Processed'". The Guardian. Retrieved August 5, 2013.
{{cite news}}: CS1 maint: multiple names: authors list (link) - ^ Layne, Ken (June 18, 2013). "Job Networking Site LinkedIn Filled With Secret NSA Program Names". Retrieved August 6, 2013.
- ^ Greenwald, Glenn; Casado, Roberto Kaz e José (July 13, 2013). "Espionagem dos EUA se espalhou pela América Latina – Depois do Brasil, Colômbia foi o país mais vigiado – Venezuela também entrou na mira de programas americanos". O Globo (in Portuguese). Retrieved August 5, 2013.
{{cite web}}: Unknown parameter|trans_title=ignored (|trans-title=suggested) (help)CS1 maint: multiple names: authors list (link) CS1 maint: unrecognized language (link) - ^ Cite error: The named reference
Infographicwas invoked but never defined (see the help page). - ^ a b Staff (July 20, 2013). "'Prolific Partner': German Intelligence Used NSA Spy Program". Der Spiegel. Retrieved August 5, 2013.
- ^ Nakashima, Ellen (July 31, 2013). "Newly Declassified Documents on Phone Records Program Released". The Washington Post. Retrieved August 6, 2013.
- ^ Fisher, Max (August 1, 2013). "Is XKeyscore Still Active? Defense Contractor Posted a Job Listing for It 2 weeks Ago". WorldViews (blog of The Washington Post). Retrieved August 6, 2013.
{{cite news}}: Italic or bold markup not allowed in:|publisher=(help) - ^ Ambinder, Marc (July 31, 2013). "What's XKEYSCORE?". The Compass (blog of The Week). Retrieved August 4, 2013.
{{cite news}}: Italic or bold markup not allowed in:|newspaper=(help) - ^ Gallagher, Sean (August 1, 2013). "NSA's Internet Taps Can Find Systems to Hack, Track VPNs and Word Docs – X-Keyscore Gives NSA the Ability to Find and Exploit Vulnerable Systems". Ars Technica. Retrieved August 4, 2013.
- ^ a b Staff (July 31, 2013). "XKeyscore Presentation from 2008 – Read in Full – Training Materials for the XKeyscore Program Detail How Analysts Can Use It and Other Systems to Mine Enormous Agency Databases and Develop Intelligence from the Web – Revealed: NSA Program That Collects 'Nearly Everything a User Does on the Internet'". The Guardian. Retrieved August 6, 2013.
- ^ a b Dorling, Philip (July 8, 2013). "Snowden Reveals Australia's Links to US Spy Web". The Sydney Morning Herald. Retrieved August 2, 2013.
- ^ Greenwald, Glenn; Casado, Roberto Kaz e José (July 6, 2013). "EUA expandem o aparato de vigilância continuamente – Software de vigilância usa mais de 700 servidores espalhados pelo mundo". O Globo (in Portuguese). Retrieved August 2, 2013.
{{cite news}}: Italic or bold markup not allowed in:|newspaper=(help)CS1 maint: multiple names: authors list (link) CS1 maint: unrecognized language (link) - ^ Greenwald, Glenn (July 31, 2013)."XKeyscore: NSA tool collects 'nearly everything a user does on the internet' – XKeyscore Gives 'Widest-Reaching' Collection of Online Data – NSA Analysts Require No Prior Authorization for Searches – Sweeps Up Emails, Social Media Activity and Browsing History". The Guardian. Retrieved August 1, 2013.
- ^ a b Laura Poitras, Marcel Rosenbach and Holger Stark, Ally and Target: US Intelligence Watches Germany Closely, August 12, 2013.
- ^ a b Rea, Kari (July 28, 2013). "Glenn Greenwald: Low-Level NSA Analysts Have 'Powerful and Invasive' Search Tool". ABC News. Retrieved August 4, 2013.
- ^ NSA Press Statement on 30 July 2013
- ^ Wills, Amanda (August 1, 2013). "New Snowden Leak: NSA Program Taps All You Do Online". Mashable (via CNN). Retrieved August 4, 2013.
- ^ Top Level Telecommunications, New slides about NSA collection programs, July 16, 2013
- 2013 scandals
- Counter-terrorism policy of the United States
- Espionage
- Human rights
- Mass surveillance
- National Security Agency
- Obama administration controversies
- Privacy in the United States
- Privacy of telecommunications
- American secret government programs
- Surveillance scandals
- United States national security policy
- War on Terror
- Edward Snowden