Radio-frequency identification: Difference between revisions
restored to last version by Rassmguy |
|||
| Line 1: | Line 1: | ||
{{Refimprove|date=February 2008}} |
|||
[[Image:EPC-RFID-TAG.svg|right|frame|An [[Electronic Product Code|EPC]] RFID tag used by [[Wal-Mart]].]] |
|||
[[Image:EPC-RFID-TAG.jpg|right|frame|An [[Electronic Product Code|EPC]] RFID tag used by [[Wal-Mart]].]] |
|||
'''Radio-frequency identification''' ('''RFID''') is an [[Automatic identification and data capture|automatic identification]] method, relying on storing and remotely retrieving data using devices called RFID tags or [[transponder]]s |
'''Radio-frequency identification''' ('''RFID''') is an [[Automatic identification and data capture|automatic identification]] method, relying on storing and remotely retrieving data using devices called RFID tags or [[transponder]]s. |
||
An RFID tag is an object that can be applied to or incorporated into a product, animal, or person for the purpose of identification |
An RFID tag is an object that can be applied to or incorporated into a product, animal, or person for the purpose of identification using radio waves. Some tags can be read from several meters away and beyond the line of sight of the reader. |
||
Most RFID tags contain at least two parts. One is an [[integrated circuit]] for storing and processing information, [[modulation|modulating]] and [[demodulation|demodulating]] a |
Most RFID tags contain at least two parts. One is an [[integrated circuit]] for storing and processing information, [[modulation|modulating]] and [[demodulation|demodulating]] a (RF) signal, and other specialized functions. The second is an antenna for receiving and transmitting the signal. [[Chipless RFID]] allows for discrete identification of tags without an integrated circuit, thereby allowing tags to be printed directly onto assets at a lower cost than traditional tags. |
||
Today, RFID used is in enterprise supply chain management to improve the efficiency of inventory tracking and management. However, growth and adoption in the enterprise supply chain market is limited because current commercial technology does not link the indoor tracking to the overall end-to-end supply chain visibility. Coupled with fair cost-sharing mechanisms, rational motives and justified returns from RFID technology investments are the key ingredients to achieve long-term and sustainable RFID technology adoption <ref>{{cite web|first=Adi | last=Tedjasaputra | url=http://www.rfid-asia.info/2007/07/sustainable-growth-of-rfid-supply-chain.htm | title=Sustainable Growth of RFID Supply Chain Markets |publisher=[[RFID Asia]] | date=[[2007-07-14]] | accessdate=2007-08-03}}</ref>. |
|||
There are generally two types of RFID tags: active RFID tags, which contain a [[battery (electricity)|battery]], and passive RFID tags, which have no battery. |
|||
Future [[Chipless RFID]] allows for discrete identification of tags without an integrated circuit, thereby allowing tags to be printed directly onto assets at a lower cost than traditional tags. Currently (2008) none of the chipless concepts has become operational. |
|||
Today, RFID is used in enterprise supply chain management to improve the efficiency of inventory tracking and management. |
|||
== History == |
|||
== History of RFID tags == |
|||
[[Image:FasTrak transponder.jpg|right|frame|An RFID tag used for [[electronic toll collection]].]] |
[[Image:FasTrak transponder.jpg|right|frame|An RFID tag used for [[electronic toll collection]].]] |
||
In 1946 [[Léon Theremin]] invented |
In 1946 [[Léon Theremin]] invented an espionage tool for the [[Soviet Union]] which retransmitted incident radio waves with audio information. Sound waves vibrated a [[Diaphragm (acoustics)|diaphragm]] which slightly altered the shape of the [[resonator]], which modulated the reflected radio frequency. Even though this device was a passive [[covert listening device]], not an identification tag, it has been attributed as a predecessor to RFID technology. The technology used in RFID has been around since the early 1920s according to one source (although the same source states that RFID ''systems'' have been around just since the late 1960s).<ref>{{cite web | author=Dargan, Gaurav; Johnson, Brian; Panchalingam, Mukunthan; Stratis, Chris | year=2004 | title=The Use of Radio Frequency Identification as a Replacement for Traditional Barcoding | work= | url=http://www.andrew.cmu.edu/user/cjs/tech.html | accessdate=2006-05-31}}</ref><ref name=shrouds>{{cite web | author=Landt, Jerry| year=2001| title=Shrouds of Time: The history of RFID | format=PDF | work=AIM, Inc.| url=http://www.transcore.com/pdf/AIM%20shrouds_of_time.pdf | accessdate=2006-05-31}}</ref><ref>{{cite web|url=http://rfident.org/rfidvideo.htm|title=Understanding RFID – Educational Video|accessdate=2006-08-26| author=Intermec Education Services|}}</ref><ref>{{cite web|author=[[Paolo Magrassi]]|year=2001|url=http://www.gartner.com|title=A World Of Smart Objects: The Role Of Auto Identification Technologies|accessdate=2007-06-24}}</ref> |
||
Similar technology, such as the [[Identification friend or foe|IFF]] [[transponder]] invented |
Similar technology, such as the [[Identification friend or foe|IFF]] [[transponder]] invented by the [[United Kingdom]] in 1939, was routinely used by the allies in [[World War II]] to identify aircraft as friend or foe. Transponders are still used by military and commercial aircraft to this day. |
||
Another early work exploring RFID is the landmark 1948 paper by Harry Stockman, titled "Communication by Means of Reflected Power" (Proceedings of the IRE, pp 1196–1204, October 1948). Stockman predicted that "…considerable research and development work has to be done before the remaining basic problems in reflected-power communication are solved, and before the field of useful applications is explored." |
Another early work exploring RFID is the landmark 1948 paper by Harry Stockman, titled "Communication by Means of Reflected Power" (Proceedings of the IRE, pp 1196–1204, October 1948). Stockman predicted that "…considerable research and development work has to be done before the remaining basic problems in reflected-power communication are solved, and before the field of useful applications is explored." |
||
| Line 24: | Line 20: | ||
Mario Cardullo's {{US Patent|3,713,148}} in 1973 was the first true ancestor of modern RFID; a passive radio transponder with memory. The initial device was passive, powered by the interrogating signal, and was demonstrated in 1971 to the New York Port Authority and other potential users and consisted of a transponder with 16 bit memory for use as a toll device. The basic Cardullo patent covers the use of RF, sound and light as transmission media. The original business plan presented to investors in 1969 showed uses in transportation (automotive vehicle identification, automatic toll system, electronic license plate, electronic manifest, vehicle routing, vehicle performance monitoring), banking (electronic check book, electronic credit card), security (personnel identification, automatic gates, surveillance) and medical (identification, patient history). |
Mario Cardullo's {{US Patent|3,713,148}} in 1973 was the first true ancestor of modern RFID; a passive radio transponder with memory. The initial device was passive, powered by the interrogating signal, and was demonstrated in 1971 to the New York Port Authority and other potential users and consisted of a transponder with 16 bit memory for use as a toll device. The basic Cardullo patent covers the use of RF, sound and light as transmission media. The original business plan presented to investors in 1969 showed uses in transportation (automotive vehicle identification, automatic toll system, electronic license plate, electronic manifest, vehicle routing, vehicle performance monitoring), banking (electronic check book, electronic credit card), security (personnel identification, automatic gates, surveillance) and medical (identification, patient history). |
||
== A very early demonstration == |
|||
A very early demonstration of '''reflected power''' (modulated backscatter) RFID tags, both passive and semi-passive, was performed by Steven Depp, Alfred Koelle and Robert Freyman at the [[Los Alamos National Laboratory]] in 1973<ref name=shrouds/>. The portable system operated at 915 MHz and used 12-bit tags. This technique is used by the majority of today's UHFID and microwave RFID tags. |
|||
A very early demonstration ''' of reflected power''' (modulated backscatter) RFID tags, both passive and semi-passive, was done by Steven Depp, Alfred Koelle and Robert Freyman at the Los Alamos Scientific Laboratory in 1973<ref name=shrouds/>. The portable system operated at 915 MHz and used 12 bit tags. This technique is used by the majority of today's UHFID and microwave RFID tags. |
|||
The first patent to be associated with the abbreviation RFID was granted to Charles Walton in 1983 {{US Patent|4,384,288}}. |
The first patent to be associated with the abbreviation RFID was granted to Charles Walton in 1983 {{US Patent|4,384,288}}. |
||
==RFID tags== |
==RFID tags== |
||
RFID tags come in three general varieties:- ''passive'', ''active'', or ''semi-passive'' (also known as ''battery-assisted''). Passive tags require no internal power source, thus being pure passive devices (they are only active when a reader is nearby to power them), whereas semi-passive and active tags require a power source, usually a small battery. |
|||
RFID tags come in three general varieties:- ''passive'', ''active'', or ''semi-passive'' (also known as ''battery-assisted'' or ''semi-active'') and ''beacon'' types. Passive tags require no internal power source, thus being pure passive devices (they are only active when a reader is nearby to power them by wireless illumination), whereas semi-passive and active tags require a power source, usually a small battery. Beacon tags transmit autonomously with a certain ''blink'' pattern and do not respond to interrogation. |
|||
[[Image:RFID backscatter.png|thumb|RFID backscatter.]] To communicate, tags respond to queries generating signals that must not create interference with the readers, as arriving signals can be very weak and must be differentiated. Besides [[backscatter]]ing, [[load modulation]] techniques can be used to manipulate the reader's field. Typically, backscatter is used in the [[far field]], whereas load modulation applies in the [[nearfield]], within a few wavelengths from the reader. |
[[Image:RFID backscatter.png|thumb|RFID backscatter.]] To communicate, tags respond to queries generating signals that must not create interference with the readers, as arriving signals can be very weak and must be differentiated. Besides [[backscatter]]ing, [[load modulation]] techniques can be used to manipulate the reader's field. Typically, backscatter is used in the [[far field]], whereas load modulation applies in the [[nearfield]], within a few wavelengths from the reader. |
||
===Passive=== |
===Passive=== |
||
Passive RFID tags have no internal power supply. The minute electrical current induced in the antenna by the incoming radio frequency signal provides just enough power for the [[CMOS]] [[integrated circuit]] in the tag to power up and transmit a response. Most passive tags signal by [[backscatter]]ing the [[carrier wave]] from the reader. This means that the antenna has to be designed both to collect power from the incoming signal and also to transmit the outbound backscatter signal. The response of a passive RFID tag is not necessarily just an ID number; the tag chip can contain [[non-volatile]], possibly writable [[EEPROM]] for storing data. |
|||
Passive tags have practical read distances ranging from about 10 cm (4 in.) ([[ISO 14443]]) up to a few meters ([[Electronic Product Code]] (EPC) and [[List of ISO standards|ISO 18000-6]]), depending on the chosen radio frequency and antenna design/size. Due to their simplicity in design they are also suitable for manufacture with a printing process for the antennas. The lack of an onboard power supply means that the device can be quite small: commercially available products exist that can be embedded in a sticker, or under the skin in the case of low frequency (LowFID) RFID tags. |
|||
Passive RFID tags have no internal power supply. The minute electrical current induced in the antenna by the incoming radio frequency signal provides just enough power for the [[CMOS]] [[integrated circuit]] in the tag to power up and transmit a response. Most passive tags signal by [[backscatter]]ing the [[carrier wave]] from the reader. This means that the antenna has to be designed both to collect power from the incoming signal and also to transmit the outbound backscatter signal. The response of a passive RFID tag is not necessarily just an ID number; the tag chip can contain [[non-volatile]] data, possibly writable [[EEPROM]] for storing data. |
|||
Passive tags have practical read distances ranging from about 11 cm (4 in) with near-field ([[ISO 14443]]), up to approximately 10 meters (33 feet) with far-field ([[List of ISO standards|ISO 18000-6]]) and can reach up to 183 meters (600 feet)<ref>[http://www.rfidradio.com/?p=25 Mojix Redefines the Range for Passive RFID], RFID Radio</ref> when combined with a [[phased array]]. Basically, the reading and writing depend on the chosen radio frequency and the antenna design/size. Due to their simplicity in design they are also suitable for manufacture with a printing process for the antennas. The lack of an onboard power supply means that the device can be quite small: commercially available products exist that can be embedded in a sticker, or under the skin in the case of low frequency (LowFID) RFID tags. |
|||
In 2007, the Danish Company RFIDsec developed a passive RFID with privacy enhancing technologies built-in including built-in firewall access controls, communication encryption and a silent mode ensuring that the consumer at point of sales can get exclusive control of the key to control the RFID. The RFID will not respond unless the consumer authorizes it, the consumer can validate presence of a specific RFID without leaking identifiers and therefore the consumer can make use of the RFID without being trackable or otherwise leak information that represents a threat to consumer privacy. |
In 2007, the Danish Company RFIDsec developed a passive RFID with privacy enhancing technologies built-in including built-in firewall access controls, communication encryption and a silent mode ensuring that the consumer at point of sales can get exclusive control of the key to control the RFID. The RFID will not respond unless the consumer authorizes it, the consumer can validate presence of a specific RFID without leaking identifiers and therefore the consumer can make use of the RFID without being trackable or otherwise leak information that represents a threat to consumer privacy. |
||
In 2006, [[Hitachi, Ltd.]] developed a passive device called the µ-Chip measuring 0.15×0.15 mm (not including the antenna), and thinner than a sheet of paper (7.5 [[micrometre|micrometers]]).<ref>{{cite web | url=http://www.hitachi.com/New/cnews/060206.html | title=News release: World's smallest and thinnest 0.15 × 0.15 mm, 7.5 µm thick RFID IC chip | publisher=[[Hitachi, Ltd]] | date=[[2006-02-06]] | accessdate=2007-01-26}}</ref><ref>{{cite news |first=Yoshiko | last=Hara | url=http://www.eetimes.com/news/design/showArticle.jhtml?articleID=179100286 |title=Hitachi advances paper-thin RFID chip | publisher= [[EETimes]] |date=[[2006-02-06]]| accessdate=2007-01-26}}</ref> |
In 2006, [[Hitachi, Ltd.]] developed a passive device called the µ-Chip measuring 0.15×0.15 mm (not including the antenna), and thinner than a sheet of paper (7.5 [[micrometre|micrometers]]).<ref>{{cite web | url=http://www.hitachi.com/New/cnews/060206.html | title=News release: World's smallest and thinnest 0.15 × 0.15 mm, 7.5 µm thick RFID IC chip | publisher=[[Hitachi, Ltd]] | date=[[2006-02-06]] | accessdate=2007-01-26}}</ref><ref>{{cite news |first=Yoshiko | last=Hara | url=http://www.eetimes.com/news/design/showArticle.jhtml?articleID=179100286 |title=Hitachi advances paper-thin RFID chip | publisher= [[EETimes]] |date=[[2006-02-06]]| accessdate=2007-01-26}}</ref> Silicon-on-Insulator (SOI) technology is used to achieve this level of integration. The Hitachi µ-Chip can wirelessly transmit a 128-bit unique ID number which is hard coded into the chip as part of the manufacturing process. The unique ID in the chip cannot be altered, providing a high level of authenticity to the chip and ultimately to the items the chip may be permanently attached or embedded into. The Hitachi µ-Chip has a typical maximum read range of 30 cm (1 ft). In February 2007 Hitachi unveiled an even smaller RFID device measuring 0.05×0.05 mm, and thin enough to be embedded in a sheet of paper.<ref>{{cite news | publisher = [[BBC News]] | title = World's tiniest RFID tag unveiled | date = 23 Feb 2007 | url = http://news.bbc.co.uk/2/hi/technology/6389581.stm}}</ref> The new chips can store as much data as the older µ-chips, and the data contained on them can be extracted from as far away as a few hundred metres. The ongoing problems with all RFIDs is that they need an external antenna which is 80 times bigger than the chip in the best version thus far developed. Further, the present costs of manufacturing the inlays for tags has inhibited broader adoption. As silicon prices are reduced and new more economic methods for manufacturing inlays and tags are perfected in the industry, broader adoption and item level tagging along with economies of scale production scenarios; it is expected to make RFID both innocuous and commonplace much like Barcodes are presently. |
||
[[Alien Technology]]'s Fluidic Self Assembly and HiSam machines, Smartcode's Flexible Area Synchronized Transfer (FAST) and [[Symbol Technologies]]' PICA process are alleged to potentially further reduce tag costs by massively parallel production{{Fact|date=April 2007}}. [[Alien Technology]] and SmartCode are currently using the processes to manufacture tags while [[Symbol Technologies]]' PICA process is still in the development phase. Symbol was acquired by Motorola in 2006. Motorola however has since made agreements with Avery Dennison for supply of tags, meaning their own |
[[Alien Technology]]'s Fluidic Self Assembly and HiSam machines, Smartcode's Flexible Area Synchronized Transfer (FAST) and [[Symbol Technologies]]' PICA process are alleged to potentially further reduce tag costs by massively parallel production{{Fact|date=April 2007}}. [[Alien Technology]] and SmartCode are currently using the processes to manufacture tags while [[Symbol Technologies]]' PICA process is still in the development phase. Symbol was acquired by Motorola in 2006. Motorola however has since made agreements with Avery Dennison for supply of tags, meaning their own Tag production and PICA process may have been abandoned.<ref>{{cite news | publisher = [[RFID Update]] | title = Motorola Taps Avery Dennison for RFID Tags| date = 01 May 2007 | url = http://www.rfidupdate.com/articles/index.php?id=1350}}</ref> Alternative methods of production such as FAST, FSA, HiSam and possibly PICA could potentially reduce tag costs dramatically, and due to volume capacities achievable, in turn be able to also drive the economies of scale models for various Silicon fabricators as well. Some passive RFID vendors believe that Industry benchmarks for tag costs can be achieved eventually as new low cost volume production systems are implemented more broadly. (For example, see [http://en.wikipedia.org/wiki/High_Speed_Strap_Attach_Machine]) |
||
Non-silicon tags made from polymer semiconductors are currently being developed by several companies globally. Simple laboratory |
Non-silicon tags made from polymer semiconductors are currently being developed by several companies globally. Simple laboratory printed polymer tags operating at 13.56 [[Hertz|MHz]] were demonstrated in 2005 by both PolyIC (Germany) and [[Philips]] (The Netherlands). If successfully commercialized, polymer tags will be roll-printable, like a magazine, and much less expensive than silicon-based tags. The end game for most item-level tagging over the next few decades may be that RFID tags will be wholly printed – the same way that a barcode is today – and be virtually free, like a barcode. However, substantial technical and economic hurdles must be surmounted to accomplish such an end: hundreds of billions of dollars have been invested over the last three decades in silicon processing, resulting in a per-feature cost which is actually less than that of conventional printing. |
||
=== Active === |
=== Active === |
||
Unlike passive RFID tags, active RFID tags have their own internal power source, which is used to power the [[integrated circuit]]s and to broadcast the response signal to the reader. Communications from active tags to readers is typically much more reliable (i.e. fewer errors) than |
Unlike passive RFID tags, active RFID tags have their own internal power source, which is used to power the [[integrated circuit]]s and to broadcast the response signal to the reader. Communications from active tags to readers is typically much more reliable (i.e. fewer errors) than from passive tags due to the ability for active tags to conduct a "[[session (computer science)|session]]" with a reader. |
||
Active tags, due to their |
Active tags, due to their on board power supply, also may transmit at higher power levels than passive tags, allowing them to be more robust in "RF challenged" environment with humidity and spray or with dampening targets (including humans/cattle, which contain mostly water), reflective targets from metal (shipping containers, vehicles), or at longer distances: Generating strong responses from weak reception is a sound approach to success. In turn, active tags are generally bigger, caused by battery volume, and more expensive to manufacture, caused by battery price. However, their potential shelf life is comparable, as self discharge of batteries competes with corrosion of aluminated printed circuits. |
||
Many active tags today have operational ranges of hundreds of meters, and a battery life |
Many active tags today have operational ranges of hundreds of meters, and a battery life of up to 10 years. Active tags may include larger memories than passive tags, and may include the ability to store additional information received from the reader. |
||
Special active RFID tags may include specialized sensors. For example, a temperature sensor can be used to record the temperature profile during the transportation and storage of perishable goods. Other sensor types used include humidity, shock/vibration, light, nuclear radiation, pressure and concentrations of gases |
Special active RFID tags may include specialized sensors. For example, a temperature sensor can be used to record the temperature profile during the transportation and storage of perishable goods. Other sensor types used include humidity, shock/vibration, light, nuclear radiation, pressure and concentrations of gases like ethylene. |
||
The United States Department of Defense (DoD) has successfully used active tags to reduce search and loss in logistics and improve supply chain visibility for more than 15 years (concept of in-transit-visibility ITV, [http://usmilitary.about.com/od/glossarytermsi/g/i3260.htm]). |
|||
Increasingly, active tags on the market today are internationally standardized according to the ISO 18000-7 air interface standard, which operates at the 433 MHz frequency. In addition, active tags that are sold in the form of an electronic seal are standardized according to the ISO 18185 standard. |
|||
The United States Department of Defense (DoD) has successfully used active tags to reduce search and loss in logistics and to improve supply chain visibility for more than 15 years (concept of in-transit-visibility, ITV[http://usmilitary.about.com/od/glossarytermsi/g/i3260.htm]). The DoD is increasingly relying on active tags to monitor the environmental status of assets and materiel using onboard sensors. |
|||
=== Semi-passive === |
=== Semi-passive === |
||
| Line 72: | Line 58: | ||
Semi-passive tags are similar to active tags in that they have their own power source, but the battery only powers the microchip and does not power the broadcasting of a signal. The response is usually powered by means of [[backscattering]] the RF energy from the reader, where energy is reflected back to the reader as with passive tags. An additional application for the battery is to power data storage. |
Semi-passive tags are similar to active tags in that they have their own power source, but the battery only powers the microchip and does not power the broadcasting of a signal. The response is usually powered by means of [[backscattering]] the RF energy from the reader, where energy is reflected back to the reader as with passive tags. An additional application for the battery is to power data storage. |
||
If energy from the reader is collected and stored to emit a response in the future, the tag is operating active |
If energy from the reader is collected and stored to emit a response in the future, the tag is operating active |
||
Whereas in passive tags the power level to power up the circuitry must be 100 times stronger than with active or semi-active tags, also the time consumption for collecting the energy is omitted and the response comes with shorter latency time. ''The battery-assisted'' reception circuitry of semi-passive tags leads to greater sensitivity than passive tags, typically 100 times more. The enhanced sensitivity can be leveraged as increased range (by one magnitude) and/or as enhanced read reliability (by reducing bit error rate at least one magnitude). |
Whereas in passive tags the power level to power up the circuitry must be 100 times stronger than with active or semi-active tags, also the time consumption for collecting the energy is omitted and the response comes with shorter latency time. ''The battery-assisted'' reception circuitry of semi-passive tags leads to greater sensitivity than passive tags, typically 100 times more. The enhanced sensitivity can be leveraged as increased range (by one magnitude) and/or as enhanced read reliability (by reducing bit error rate at least one magnitude). |
||
The enhanced sensitivity of semi-passive tags |
The enhanced sensitivity of semi-passive tags place higher demands on the reader concerning separation in more dense population of tags. Because an already weak signal is backscattered to the reader from a larger number of tags and from longer distances, the separation requires more sophisticated anti-collision concepts, better signal processing and some more intelligent assessment which tag might be where. For passive tags, the reader-to-tag link usually fails first. For semi-passive tags, the reverse (tag-to-reader) link usually collides first. |
||
Semi-passive tags have three main advantages |
Semi-passive tags have three main advantages 1) Greater sensitivity than passive tags 2) Longer battery powered life cycle than active tags. 3) Can perform active functions (such as temperature logging) under its own power, even when no reader is present for powering the circuitry. |
||
Most semi-passive tags use the 2.4Ghz frequency which has shown to be less reliable in "RF challenged" environments where frozen items, dense metal, and other elements that are hostile to RF are found. This is far less common with fully active tags that broadcast at the 433 Mhz frequency. |
|||
=== Beacon tags === |
|||
Beacon tags blink the coded identity signal at a regular pattern. This may be a constant blink rate or a blink rate with stochastic shift or some triggered blinking. Not to activate the responder function in a tag first prevents from limiting the speed capabilities and improves the availability of the identification information under noisy conditions. Therefore the beacon concept appliers to very robust processes: The regular availability of the coded signal reduces latency and allows for low power levels, as with active tags. However, the permanent talk of many tags may ''pollute'' the frequency channel and therefore prevent from operating in denser populations. The design of the blinking scheme must take the battery life cycle into account. Currently (2008) none of the offered products follows any known line of international standardization. However, all blinking must obey the national wireless communications regulations concerning power level and channel occupation. |
|||
===Extended capability=== |
===Extended capability=== |
||
Extended capability RFID defines a category of RFID that goes beyond the basic capabilities of standard RFID as merely a “license plate” or bar-code replacement technology. Key attributes of extended capability RFID include, but are not limited to, the ability to read at longer distances and around challenging environments, to store large amounts of data on the tag, to integrate with sensors, and to communicate with external devices. |
|||
Extended capability RFID defines a category of RFID that goes beyond the basic capabilities of standard RFID as merely a "license plate" or barcode replacement technology. Key attributes of extended capability RFID include the ability to read at longer distances and around challenging environments, to store large amounts of data on the tag, to integrate with sensors, and to communicate with external devices. |
|||
Examples of extended capability RFID tag technologies include EPC C1G2 with extended memory (e.g. 64Kb), battery-assisted passive, and active RFID. Battery-assisted passive, also known as semi-passive or semi-active, has the ability to extend the read range of standard passive technologies to well over 50 meters, to read around challenging materials such as metal, to withstand outdoor environments, to store an on-tag database, to be able to capture sensor data, and to act as a communications mechanism for external devices. Also, battery-assisted passive only transmits a signal when interrogated, thus extending battery life. Active RFID, which can have some of the features of battery-assisted passive, is commonly used for even longer distances and real-time locationing. It also actively transmits a signal, which often results in shorter battery life. |
Examples of extended capability RFID tag technologies include EPC C1G2 with extended memory (e.g. 64Kb), battery-assisted passive, and active RFID. Battery-assisted passive, also known as semi-passive or semi-active, has the ability to extend the read range of standard passive technologies to well over 50 meters, to read around challenging materials such as metal, to withstand outdoor environments, to store an on-tag database, to be able to capture sensor data, and to act as a communications mechanism for external devices. Also, battery-assisted passive only transmits a signal when interrogated, thus extending battery life. Active RFID, which can have some of the features of battery-assisted passive, is commonly used for even longer distances and real-time locationing. It also actively transmits a signal, which often results in shorter battery life. |
||
| Line 95: | Line 74: | ||
===Antenna types=== |
===Antenna types=== |
||
The antenna used for an RFID tag is affected by the intended application and the frequency of operation. Low-frequency is (30 kHz – 300 kHz). LFID or LowFID passive tags are normally [[Inductive coupling|inductively coupled]], and because the voltage induced is proportional to frequency, many coil turns are needed to produce enough voltage to operate an integrated circuit. Compact LowFID tags, like glass-encapsulated tags used in animal and human identification, use a multilayer coil (3 layers of 100–150 turns each) wrapped around a [[Ferrite (iron)|ferrite]] core. |
|||
High frequency is (3 MHz - 30 MHz). At 13.56 MHz, a HFID or HighFID tag, using a planar spiral with 5–7 turns over a credit-card-sized form factor can be used to provide ranges of tens of centimeters. These coils are less costly to produce than LF coils, since they can be made using [[lithography|lithographic techniques]] rather than by wire winding, but two metal layers and an insulator layer are needed to allow for the crossover connection from the outermost layer to the inside of the spiral where the integrated circuit and resonance capacitor are located. |
|||
The antenna used for an RFID tag is affected by the intended application and the frequency of operation. Low-frequency is 30–300 kHz. LFID or LowFID passive tags are normally [[Inductive coupling|inductively coupled]], and because the voltage induced is proportional to frequency, many coil turns are needed to produce enough voltage to operate an integrated circuit. Compact LowFID tags, like glass-encapsulated tags used in animal and human identification, use a multilayer coil (3 layers of 100–150 turns each) wrapped around a [[Ferrite (iron)|ferrite]] core. |
|||
Ultra-high frequency or UHF is (300 MHz - 3 GHz). UHFID/Ultra-HighFID and [[microwave]] passive tags are usually radiatively-coupled to the reader antenna and can employ conventional dipole-like antennas. Only one metal layer is required, reducing cost of manufacturing. Dipole antennas, however, are a poor match to the high and slightly capacitive input impedance of a typical integrated circuit. Folded dipoles, or short loops acting as inductive matching structures, are often employed to improve power delivery to the IC. Half-wave dipoles (16 cm at 900 MHz) are too big for many applications; for example, tags embedded in labels must be less than 10 cm (4 inches) in extent. To reduce the length of the antenna, antennas can be bent or meandered, and capacitive tip-loading or bowtie-like broadband structures are also used. Compact antennas usually have gain less than that of a dipole — that is, less than 2 dBi — and can be regarded as [[isotropic]] in the plane perpendicular to their axis. |
|||
High frequency is 3-30 MHz. At 13.56 MHz, a HFID or HighFID tag, using a planar spiral with 5–7 turns over a credit-card-sized form factor can be used to provide ranges of tens of centimeters. These coils are less costly to produce than LF coils, since they can be made using [[lithography|lithographic techniques]] rather than by wire winding, but two metal layers and an insulator layer are needed to allow for the crossover connection from the outermost layer to the inside of the spiral where the integrated circuit and resonance capacitor are located. |
|||
Ultrahigh-frequency or UHF is 300 MHz-3 GHz. UHFID and [[microwave]] passive tags are usually radiatively-coupled to the reader antenna and can employ conventional dipole-like antennas. Only one metal layer is required, reducing cost of manufacturing. Dipole antennas, however, are a poor match to the high and slightly capacitive input impedance of a typical integrated circuit. Folded dipoles, or short loops acting as inductive matching structures, are often employed to improve power delivery to the IC. Half-wave dipoles (16 cm at 900 MHz) are too big for many applications; for example, tags embedded in labels must be less than 10 cm (4 inches) in extent. To reduce the length of the antenna, antennas can be bent or meandered, and capacitive tip-loading or bowtie-like broadband structures are also used. Compact antennas usually have gain less than that of a dipole — that is, less than 2 dBi — and can be regarded as [[isotropic]] in the plane perpendicular to their axis. |
|||
Dipoles couple to radiation polarized along their axes, so the visibility of a tag with a simple dipole-like antenna is orientation-dependent. Tags with two orthogonal or nearly-orthogonal antennas, often known as dual-dipole tags, are much less dependent on orientation and polarization of the reader antenna, but are larger and more expensive than single-dipole tags. |
Dipoles couple to radiation polarized along their axes, so the visibility of a tag with a simple dipole-like antenna is orientation-dependent. Tags with two orthogonal or nearly-orthogonal antennas, often known as dual-dipole tags, are much less dependent on orientation and polarization of the reader antenna, but are larger and more expensive than single-dipole tags. |
||
| Line 106: | Line 84: | ||
Patch antennas are used to provide service in close proximity to metal surfaces, but a structure with good bandwidth is 3–6 mm thick, and the need to provide a ground layer and ground connection increases cost relative to simpler single-layer structures. |
Patch antennas are used to provide service in close proximity to metal surfaces, but a structure with good bandwidth is 3–6 mm thick, and the need to provide a ground layer and ground connection increases cost relative to simpler single-layer structures. |
||
HighFID and UHFID tag antennas are usually fabricated from copper or aluminum. Conductive inks have seen some use in tag antennas but have encountered problems with IC adhesion and environmental stability. |
|||
===Tag attachment=== |
===Tag attachment=== |
||
There are three different kinds of RFID tags based on their attachment with identified objects, i.e. '''attachable''', '''implantable''' and '''insertion''' tags <ref>{{cite web|first=Adi | last=Tedjasaputra | url=http://www.rfid-asia.info/2006/12/rfid-tag-attachments.htm |title= |
There are three different kinds of RFID tags based on their attachment with identified objects, i.e. '''attachable''', '''implantable''' and '''insertion''' tags <ref>{{cite web|first=Adi | last=Tedjasaputra | url=http://www.rfid-asia.info/2006/12/rfid-tag-attachments.htm |title= |
||
RFID Tag Attachments |publisher=[[RFID Asia]] |date=[[2006-12-18]] |accessdate=2007-08-03}}</ref>. In addition to these conventional RFID tags, Eastman Kodak Company has filed two patent applications for monitoring ingestion of medicine based on a '''digestible''' RFID tag<ref>{{cite web|first=Adi | last=Tedjasaputra | url=http://www.rfid-asia.info/2007/02/digestible-rfid-tag-alternative-for.htm |title= |
RFID Tag Attachments |publisher=[[RFID Asia]] |date=[[2006-12-18]] |accessdate=2007-08-03}}</ref>. In addition to these conventional RFID tags, Eastman Kodak Company has filed two patent applications for monitoring ingestion of medicine based on a '''digestible''' RFID tag<ref>{{cite web|first=Adi | last=Tedjasaputra | url=http://www.rfid-asia.info/2007/02/digestible-rfid-tag-alternative-for.htm |title= |
||
| Line 115: | Line 92: | ||
===Tagging positions=== |
===Tagging positions=== |
||
RFID tagging positions can influence the performance of air interface UHFID passive tags and related to the position where RFID tags are embedded, attached, injected or digested. |
|||
In many cases, optimum power from RFID reader is not required to operate passive tags. However, in cases where the Effective Radiated Power (ERP) level and distance between reader and tags are fixed, such as in manufacturing setting, it is important to know the location in a tagged object where a passive tag can operate optimally. |
|||
RFID tagging positions can influence the performance of air interface UHF RFID passive tags. |
|||
'''R-Spot''' or '''Resonance Spot''', '''L-Spot''' or '''Live Spot''' and '''D-Spot''' or '''Dead Spot''' are defined to specify the location of RFID tags in a tagged object, where the tags can still receive power from a reader within specified ERP level and distance <ref>{{cite web|first=Adi | last=Tedjasaputra | url=http://www.rfid-asia.info/2006/12/art-and-science-of-rfid-tagging.htm |title= The Art and Science of RFID Tagging |publisher=[[RFID Asia]] |date=[[2006-12-11]] |accessdate=2007-08-03}}</ref>. |
|||
In many cases, optimum power from RFID reader is not required to operate passive tags. However, in cases where the [[effective radiated power]] (ERP) level and distance between reader and tags are fixed, such as in a manufacturing setting, it is important to know the location in a tagged object where a passive tag can operate optimally. |
|||
Resonance Spot (R-Spot), Live Spot (L-Spot) and Dead Spot (D-Spot) are defined to specify the location of RFID tags in a tagged object, where the tags can still receive power from a reader within specified ERP level and distance <ref>{{cite web|first=Adi | last=Tedjasaputra | url=http://www.rfid-asia.info/2006/12/art-and-science-of-rfid-tagging.htm |title= The Art and Science of RFID Tagging |publisher=[[RFID Asia]] |date=[[2006-12-11]] |accessdate=2007-08-03}}</ref>. |
|||
===Tag environments=== |
===Tag environments=== |
||
The proposed ubiquity of RFID tags means that readers may need to select which tags to read among many potential candidates, or may wish to probe surrounding devices to perform inventory checks or, in case the tags are associated to sensors and capable of keeping their values, question them for environmental conditions. If a reader intends to work with a collection of tags, it needs to either discover all devices within an area to iterate over them afterwards, or use [[collision avoidance]] protocols. |
|||
The proposed ubiquity of RFID tags means that readers may need to select which tags to read among many potential candidates, or may wish to probe surrounding devices to perform inventory checks or, in case the tags are associated to sensors and capable of keeping their values, question them for environmental conditions. If a reader intends to work with a collection of tags, it needs to either discover all devices within an area to iterate over them afterwards, or use collision avoidance protocols. |
|||
[[Image:RFID search environment.png|thumb|Finding tags in a search environment.]] |
[[Image:RFID search environment.png|thumb|Finding tags in a search environment.]] |
||
To read tag data, readers use a tree-walking [[singulation]] algorithm, resolving possible collisions and processing responses one by one. ''[[Blocker tag]]s'' may be used to prevent readers from accessing tags within an area without killing surrounding tags by means of suicide commands. These tags masquerade as valid tags but have some special properties: in particular, they may possess any identification code, and may deterministically respond to all reader queries, thus rendering them useless and securing the environment. |
To read tag data, readers use a tree-walking [[singulation]] algorithm, resolving possible collisions and processing responses one by one. ''[[Blocker tag]]s'' may be used to prevent readers from accessing tags within an area without killing surrounding tags by means of suicide commands. These tags masquerade as valid tags but have some special properties: in particular, they may possess any identification code, and may deterministically respond to all reader queries, thus rendering them useless and securing the environment. |
||
Besides this, tags may be ''promiscuous'', attending all requests alike, or ''secure'', which requires authentication and control of typical password management and secure key distribution issues. A tag may |
Besides this, tags may be ''promiscuous'', attending all requests alike, or ''secure'', which requires authentication and control of typical password management and secure key distribution issues. A tag may as well be prepared to be activated or deactivated in response to specific reader commands. |
||
Readers that are in charge of the tags of an area may operate in ''autonomous mode'' (as opposed to ''interactive mode''). When in this mode, a reader periodically locates all tags in its operating range, and keeps a presence list with a [[Timeout (telecommunication)|persist time]] and some control information. When an entry expires, it is removed from the list. |
Readers that are in charge of the tags of an area may operate in ''autonomous mode'' (as opposed to ''interactive mode''). When in this mode, a reader periodically locates all tags in its operating range, and keeps a presence list with a [[Timeout (telecommunication)|persist time]] and some control information. When an entry expires, it is removed from the list. |
||
| Line 136: | Line 111: | ||
==Current uses== |
==Current uses== |
||
{{Refimprove|date=August 2007}} |
{{Refimprove|date=August 2007}} |
||
RFID is becoming increasingly prevalent as the price of the technology decreases. In January 2003 [[Gillette]] announced in that it ordered 500 million tags from [[Alien Technology]]. Gillette VP Dick Cantwell says the company paid "well under ten cents" for each tag. The Japanese [[HIBIKI]] initiative aims to reduce the price to 5 [[Yen]] (4 eurocent). |
RFID is becoming increasingly prevalent as the price of the technology decreases. In January 2003 [[Gillette]] announced in that it ordered 500 million tags from [[Alien Technology]]. Gillette VP Dick Cantwell says the company paid "well under ten cents" for each tag. The Japanese [[HIBIKI]] initiative aims to reduce the price to 5 [[Yen]] (4 eurocent). |
||
===Race Timing=== |
|||
Many forms of [[Transponder timing]] have been in use for timing races of different types since 2004. "Software Outsourcing System" of [[India]] has designed and implemented this method for registering race start and end timings for individuals in a marathon-type race where it is impossible to get accurate stopwatch readings for every entrant. Individuals wear a chest number containing passive tags which are read by antennae placed alongside the track. Rush error and accidents at start time are avoided since anyone can start and finish anytime without being in a batch mode. This method is being adapted by many recruitment agencies which have a PET (Physical Endurance Test) as their qualifying procedure especially in cases where the candidate volumes may run into millions (Indian Railway Recruitment Cells, Police and Power sector). |
|||
===Passports=== |
===Passports=== |
||
RFID tags are being used in [[passport]]s issued by many countries, such as include Malaysia (early 2000), New Zealand (November 4, 2005), Belgium, The Netherlands (2005), Norway (November 2005)<ref>[http://www.digi.no/php/art.php?id=275753 Datatilsynet misfornøyd med nye pass - digi.no<!-- Bot generated title -->]</ref>, Ireland (2006), Japan (March 1, 2006), Pakistan, Germany, Portugal, Poland (2006), The United Kingdom, and the United States (2007). |
|||
RFID tags are being used in [[passport]]s issued by many countries, including Malaysia (1998), New Zealand (November 4, 2005), Belgium, The Netherlands (2005), Norway (November 2005)<ref>[http://www.digi.no/php/art.php?id=275753 Datatilsynet misfornøyd med nye pass - digi.no<!-- Bot generated title -->]</ref>, Ireland (2006), Japan (March 1, 2006), Pakistan, Germany, Portugal, Poland (2006), The United Kingdom, Australia and the United States (2007), Republic of Korea (2008.8). |
|||
Standards for RFID passports are determined by the [[International Civil Aviation Organization]] ([[ICAO]]), and are contained in ICAO Document 9303, Part 1, Volumes 1 and 2 (6th edition, 2006). ICAO refers to the [[ISO 14443]] RFID chips in e-passports as "contactless integrated circuits". ICAO standards provide for e-passports to be identifiable by a standard e-passport logo on the front cover. |
Standards for RFID passports are determined by the [[International Civil Aviation Organization]] ([[ICAO]]), and are contained in ICAO Document 9303, Part 1, Volumes 1 and 2 (6th edition, 2006). ICAO refers to the [[ISO 14443]] RFID chips in e-passports as "contactless integrated circuits". ICAO standards provide for e-passports to be identifiable by a standard e-passport logo on the front cover. |
||
| Line 152: | Line 121: | ||
The first RFID passports ("[[Biometric passport|E-passport]]") were issued by [[Malaysia]] in 1998. In addition to information also contained on the visual data page of the passport, Malaysian e-passports record the travel history (time, date, and place) of entries and exits from the country. |
The first RFID passports ("[[Biometric passport|E-passport]]") were issued by [[Malaysia]] in 1998. In addition to information also contained on the visual data page of the passport, Malaysian e-passports record the travel history (time, date, and place) of entries and exits from the country. |
||
In 2006, RFID tags were included in new US passports. The US produced 10 million passports in 2005, and it has been estimated that 13 million will be produced in 2006. The chips will store the same information that is printed within the passport and will also include a digital picture of the owner. The [[United States Department of State|US State Department]] initially stated the chips could only be read from a distance of 10 cm (4 in), but after widespread criticism and a clear demonstration that special equipment can read the test passports from 10 meters (33 ft) away, the passports were designed to incorporate a thin metal lining to make it more difficult for unauthorized readers to "skim" information when the passport is closed. The department will also implement [[Basic Access Control]] (BAC), which functions as a Personal Identification Number (PIN) in the form of characters printed on the passport data page. Before a passport's tag can be read, this PIN must be entered into an RFID reader. The BAC also enables the encryption of any communication between the chip and interrogator <ref>{{cite web|url=http://rfidjournal.com/article/articleview/1951/1/132/|title=United States sets date for E-passports}}</ref>. |
In 2006, RFID tags were included in new US passports. The US produced 10 million passports in 2005, and it has been estimated that 13 million will be produced in 2006. The chips will store the same information that is printed within the passport and will also include a digital picture of the owner. The [[United States Department of State|US State Department]] initially stated the chips could only be read from a distance of 10 cm (4 in), but after widespread criticism and a clear demonstration that special equipment can read the test passports from 10 meters (33 ft) away, the passports were designed to incorporate a thin metal lining to make it more difficult for unauthorized readers to "skim" information when the passport is closed. The department will also implement [[Basic Access Control]] (BAC), which functions as a Personal Identification Number (PIN) in the form of characters printed on the passport data page. Before a passport's tag can be read, this PIN must be entered into an RFID reader. The BAC also enables the encryption of any communication between the chip and interrogator <ref>{{cite web|url=http://rfidjournal.com/article/articleview/1951/1/132/|title=United States sets date for E-passports}}</ref>. Despite this precaution, the [[Center for Democracy and Technology]] has issued warnings that significant security weaknesses that could be used to track U.S. travelers are apparent in the specifications of the card design as outlined by the U.S. Department of State.<ref>{{cite news | first=Robert | last=Lemos | coauthors= | title=Policy group warns over travel card | date=2008-01-02 | publisher=SecurityFocus | url =http://www.securityfocus.com/brief/653 | work =Security Focus | pages = | accessdate = 2008-01-06 | language = }}</ref> |
||
The new [[Passport Card]] also incorporates RFID technology. The [[Center for Democracy and Technology]] has issued warnings that significant security weaknesses that the Passport Card could be used to track U.S. travelers are apparent in the specifications of the card design as outlined by the U.S. Department of State.<ref>{{cite news | first=Robert | last=Lemos | coauthors= | title=Policy group warns over travel card | date=2008-01-02 | publisher=SecurityFocus | url =http://www.securityfocus.com/brief/653 | work =Security Focus | pages = | accessdate = 2008-01-06 | language = }}</ref> |
|||
Security expert [[Bruce Schneier]] has suggested that a mugger operating near an airport could target victims who have arrived from wealthy countries, or a terrorist could design an [[improvised explosive device]] which functioned when approached by persons from a particular country. |
Security expert [[Bruce Schneier]] has suggested that a mugger operating near an airport could target victims who have arrived from wealthy countries, or a terrorist could design an [[improvised explosive device]] which functioned when approached by persons from a particular country. |
||
| Line 163: | Line 130: | ||
[[Image:ERPBugis.JPG|thumb|200px|right|An [[Electronic Road Pricing]] gantry in Singapore. Gantries such as these collect tolls in high-traffic areas from active RFID units in vehicles.]] |
[[Image:ERPBugis.JPG|thumb|200px|right|An [[Electronic Road Pricing]] gantry in Singapore. Gantries such as these collect tolls in high-traffic areas from active RFID units in vehicles.]] |
||
[[Image:Paypass chip front.png|thumb|right|[[MasterCard#PayPass|PayPass]] RFID chip removed from a MasterCard.]] |
[[Image:Paypass chip front.png|thumb|right|[[MasterCard#PayPass|PayPass]] RFID chip removed from a MasterCard.]] |
||
*Throughout [[Europe]], and in particular in Paris (system started in 1995 by the [[RATP]]), Lyon, Bordeaux |
*Throughout [[Europe]], and in particular in Paris (system started in 1995 by the [[RATP]]), Lyon, Bordeaux and Marseille in France, Porto and Lisbon in Portugal, Milan, Turin, and Florence in Italy, and Brussels in Belgium, RFID passes conforming to the [[Calypso (RFID)]] international standard are used for public transport systems. They are also used now in Canada (Montreal), Mexico, Israel, Bogotá and Pereira in Colombia, Stavanger in Norway, etc. |
||
*In [[Toronto, Ontario, Canada]] and surrounding areas, [[Electronic Road Pricing]] systems are used to collect toll payments on [[Highway 407]]. |
*In [[Toronto, Ontario, Canada]] and surrounding areas, [[Electronic Road Pricing]] systems are used to collect toll payments on [[Highway 407]]. |
||
| Line 171: | Line 139: | ||
*In [[Seoul, South Korea]] and surrounding cities, [[T-money]] cards can be used to pay for public transit. Some other South Korean cities have adopted the system, which can also be used in some stores as cash. T-money replaced [[Upass]], first introduced for transport payments in 1996 using [[MIFARE]] technology. |
*In [[Seoul, South Korea]] and surrounding cities, [[T-money]] cards can be used to pay for public transit. Some other South Korean cities have adopted the system, which can also be used in some stores as cash. T-money replaced [[Upass]], first introduced for transport payments in 1996 using [[MIFARE]] technology. |
||
*In [[Turkey]], RFID has been used in the motorways and bridges as a payment system over ten years |
*In [[Turkey]], RFID has been used in the motorways and bridges as a payment system over ten years. Also the new electronic bus tickets in [[Istanbul]] |
||
*In [[Hong Kong]], mass transit is paid for almost exclusively through the use of an RFID technology, called the [[Octopus Card]]. Originally it was launched in September 1997 exclusively for transit fare collection, but has grown to be similar to a cash card, and can still be used in [[vending machine]]s, [[fast-food restaurant]]s and [[supermarket]]s. The card can be recharged with cash at add-value machines or in shops, and can be read several centimetres from the reader. The same applies for [[Delhi Metro]], the rapid transit system in New Delhi, capital city of [[India]]. |
*In [[Hong Kong]], mass transit is paid for almost exclusively through the use of an RFID technology, called the [[Octopus Card]]. Originally it was launched in September 1997 exclusively for transit fare collection, but has grown to be similar to a cash card, and can still be used in [[vending machine]]s, [[fast-food restaurant]]s and [[supermarket]]s. The card can be recharged with cash at add-value machines or in shops, and can be read several centimetres from the reader. The same applies for [[Delhi Metro]], the rapid transit system in New Delhi, capital city of [[India]]. |
||
| Line 183: | Line 151: | ||
*In Singapore, public transportation buses and trains employ passive RFID cards known as [[EZ-Link]] cards. Traffic into crowded downtown areas is regulated by variable tolls imposed using an active tagging system combined with the use of stored-value cards (known as [[CashCard]]s). |
*In Singapore, public transportation buses and trains employ passive RFID cards known as [[EZ-Link]] cards. Traffic into crowded downtown areas is regulated by variable tolls imposed using an active tagging system combined with the use of stored-value cards (known as [[CashCard]]s). |
||
*RFID is used in Malaysia Expressways payment system. The name for the system is Touch 'n Go. |
*RFID is used in Malaysia Expressways payment system. The name for the system is Touch 'n Go. Due to the name and design, one must touch the card for usage. |
||
*Since 2002, in [[Taipei]], [[Taiwan]] the transportation system uses RFID operated cards as fare collection. The [[Easy Card]] is charged at local convenience stores and metro stations, and can be used in Metro, buses and parking lots. The uses are planned to extend all throughout the island of Taiwan in the future. |
*Since 2002, in [[Taipei]], [[Taiwan]] the transportation system uses RFID operated cards as fare collection. The [[Easy Card]] is charged at local convenience stores and metro stations, and can be used in Metro, buses and parking lots. The uses are planned to extend all throughout the island of Taiwan in the future. |
||
*In the [[USA]], The [[Chicago Transit Authority]] has offered the [[Chicago Card|Chicago Card and the Chicago Card Plus]] for rail payments across the entire system since 2002 and for bus payments since 2005. The [[New York City Subway]] is conducting a trial during 2006, utilizing [[MasterCard#PayPass|PayPass]] by [[MasterCard]] as fare payment. The [[Massachusetts Bay Transportation Authority]] introduced the use of a [[CharlieCard]] RFID as a fare payment system which is cheaper than its paper or cash equivalent. Six transit agencies in the King County region of Washington State are collaborating to introduce the Smart Card, or [[Orca Card]] |
*In the [[USA]], The [[Chicago Transit Authority]] has offered the [[Chicago Card|Chicago Card and the Chicago Card Plus]] for rail payments across the entire system since 2002 and for bus payments since 2005. The [[New York City Subway]] is conducting a trial during 2006, utilizing [[MasterCard#PayPass|PayPass]] by [[MasterCard]] as fare payment. The [[Massachusetts Bay Transportation Authority]] introduced the use of a [[CharlieCard]] RFID as a fare payment system which is cheaper than its paper or cash equivalent. Six transit agencies in the King County region of Washington State are collaborating to introduce the Smart Card, or [[Orca Card]]. |
||
*In the [[UK]], |
*In the [[UK]], op systems for prepaying for unlimited [[public transport]] have been devised, making use of RFID technology. The design is embedded in a creditcard-like pass, that when scanned reveals details of whether the pass is valid, and for how long the pass will remain valid. The first company to implement this is the [[Nottingham City Transport|NCT]] company of [[Nottingham]] City, where the general public affectionately refer to them as "beep cards". It has since then been implemented with great success in London, where "[[Oyster card]]s" allow for pay-as-you-go travel as well as passes valid for various lengths of time and in various areas. |
||
*In [[Oslo]], [[Norway]], the upcoming public transport payment is to be entirely RFID-based. The system |
*In [[Oslo]], [[Norway]], the upcoming public transport payment is to be entirely RFID-based. The system is to be put into production around spring 2007 |
||
*In [[Norway]], all public toll roads are equipped with an RFID payment system known as [[AutoPass]]. |
*In [[Norway]], all public toll roads are equipped with an RFID payment system known as [[AutoPass]]. |
||
*RFID tags are used for [[electronic toll collection]] at [[toll booth]]s with [[Georgia (U.S. state)|Georgia]]'s Cruise Card, [[California]]'s [[FasTrak]], [[Colorado]]'s [[E-470]], [[Illinois]]' [[I-Pass]], [[Oklahoma]]'s [[Pikepass]], the expanding eastern states' [[E-ZPass]] system (including Massachusetts's [[Fast Lane]],Delaware, [[New Hampshire Turnpike]], Maryland, New Jersey |
*RFID tags are used for [[electronic toll collection]] at [[toll booth]]s with [[Georgia (U.S. state)|Georgia]]'s Cruise Card, [[California]]'s [[FasTrak]], [[Colorado]]'s [[E-470]], [[Illinois]]' [[I-Pass]], [[Oklahoma]]'s [[Pikepass]], the expanding eastern states' [[E-ZPass]] system (including Massachusetts's [[Fast Lane]],Delaware, [[New Hampshire Turnpike]], Maryland, New Jersey [[Turnpike]], West Virginia Turnpike, New York's Thruway system, Virginia, and the [[Maine Turnpike]]), Florida's [[SunPass]], Various systems in Texas including D/FW's NTTA [[TollTag]], the Austin metro [[TxTag]] and Houston HCTRA [[EZ Tag]] (which as of early 2007 are all valid on any Texas toll road), [[Kansas]]'s [[K-Tag]], The "Cross-[[Israel]] Highway" (Highway 6), [[Philippines]] [[South Luzon Expressway]] E-Pass, [[Brisbane]]'s Queensland Motorway E-Toll System in [[Australia]], Autopista del Sol (Sun's Highway), Autopista Central (Central Highway), Autopista Los Libertadores, Costanera Norte, Vespucio Norte Express and Vespucio Sur urban Highways and every forthcoming urban highway (in a "[[Free Flow]]" modality) concessioned to private investors in [[Chile]], all toll tunnels in [[Hong Kong]] ([[Autotoll]]) and all highways in [[Portugal]] ([[Via Verde]], the first system in the world to span the entire network of tolls), [[France]] (Liber-T system), [[Italy]] ([[Telepass]]), [[Spain]] ([[VIA-T]]), [[Brazil]] ([[Sem Parar - Via Fácil]]). The tags, which are usually the active type, are read remotely as vehicles pass through the booths, and tag information is used to debit the toll from a [[prepaid]] [[account]]. The system helps to speed traffic through toll plazas as it records the date, time, and billing data for the RFID vehicle tag. The plaza- and queue-free [[407 Express Toll Route]], in the [[Greater Toronto Area]], allows the use of a transponder (an active tag) for all billing. This eliminates the need to identify a vehicle by licence plate.{{Fact|date=April 2008}} |
||
*The [[Transperth]] public transport network in [[Perth, Western Australia]] uses RFID technology in the new [[SmartRider]] ticketing system. |
*The [[Transperth]] public transport network in [[Perth, Western Australia]] uses RFID technology in the new [[SmartRider]] ticketing system. |
||
| Line 205: | Line 173: | ||
*A number of [[ski resort]]s, particularly in the [[French Alps]] and in the Spanish and French Pyrenees, have adopted RFID tags to provide skiers hands-free access to [[ski lift]]s. Skiers don't have to take their passes out of their pockets. |
*A number of [[ski resort]]s, particularly in the [[French Alps]] and in the Spanish and French Pyrenees, have adopted RFID tags to provide skiers hands-free access to [[ski lift]]s. Skiers don't have to take their passes out of their pockets. |
||
*In [[Santiago, Chile|Santiago]] (Chile) the subway system Metro and the recently implemented public transportation system [[Transantiago]] |
*In [[Santiago, Chile|Santiago]] (Chile) the subway system Metro and the recently implemented public transportation system [[Transantiago]] uses an RFID card called Bip or Multivia. |
||
*In [[Medellín]] (Colombia) the |
*In [[Medellín]] (Colombia) the system Metro and the recently implemented card system uses an RFID card called Cívica. |
||
*In [[Dubai]], (United Arab Emirates) drivers through Sheikh Zayed Road and Garhoud Bridge pay |
*In [[Dubai]], (United Arab Emirates) drivers through Sheikh Zayed Road and Garhoud Bridge pay toll tax using RFID tags called [[Salik (Road Toll)]]. |
||
*In [[Milano]] (Italy), the ATM "Azienda Trasporti Milanese" has implemented RFID tags for frequent users. |
*In [[Milano]] (Italy), the ATM "Azienda Trasporti Milanese" has implemented RFID tags for frequent users. |
||
*In [[Mumbai]], the busiest suburban rail transport in the world, which transports 3.5 million commuters per day, has implemented the use of RFID ticket cards.{{Fact|date=April 2008}} |
*In [[Mumbai]], the busiest suburban rail transport in the world, which transports 3.5 million commuters per day, has also implemented the use of RFID ticket cards for the use in automatic ticket vending machines for hassle free and no need to stand in long queues.{{Fact|date=April 2008}} |
||
*In [[Barcelona]], it's used to identify users in a [[Community bicycle program|bike sharing]] system called [[Bicing]] to prevent [[bicycle]] [[theft]] and detect the periode of bicycle usage. |
|||
*In [[New Delhi]], the underground subway or metro system implements RFID ticket coins. |
|||
*In [[Netherlands|the Netherlands]] the new [[:nl:OV-chipkaart|OV-chipkaart]] system will eventually replace current bus, tram, metro and train payment systems, allowing for both more accurate fares, access control to (train)stations and more accurate determination of government fees to the various public transportation companies.{{Fact|date=January 2008}} |
|||
*In [[Barcelona]], RFID technology is used to identify users in a [[Community bicycle program|bike sharing]] system called [[Bicing]] to prevent [[bicycle]] [[theft]] and track bicycle usage. |
|||
*In [[Netherlands|the Netherlands]] the new [[:nl:OV-chipkaart|OV-chipkaart]] system will eventually replace current bus, tram, metro and train payment systems, allowing for more accurate fares, access control to stations, and more accurate determination of government fees to the various public transportation companies.{{Fact|date=January 2008}} |
|||
===Product tracking=== |
===Product tracking=== |
||
*The [http://www.canadaid.com/ Canadian Cattle Identification Agency] began using RFID tags as a replacement for barcode tags. The tags are required to identify a bovine's herd of origin and this is used for tracing when a packing plant condemns a carcass. Currently CCIA tags are used in |
*The [http://www.canadaid.com/ Canadian Cattle Identification Agency] began using RFID tags as a replacement for barcode tags. The tags are required to identify a bovine's herd of origin and this is used for tracing when a packing plant condemns a carcass. Currently CCIA tags are used in Wisconsin and by US farmers on a voluntary basis. The USDA is currently developing its own program. |
||
*High-frequency RFID or |
*High-frequency RFID or HighFID tags are used in [[library]] book or bookstore tracking, [http://jewelry.innovez-one.com jewelry tracking], [[pallet]] tracking, building [[access control]], airline baggage tracking, and [[apparel]] and pharmaceutical items tracking. High-frequency tags are widely used in identification [[badge]]s, replacing earlier [[magnetic stripe]] cards. These badges need only be held within a certain distance of the reader to authenticate the holder. The [[American Express]] Blue credit card now includes a HighFID tag. In Feb 2008, Emirates airline started a trial of RFID baggage tracing at London and Dubai airports. <ref>{{cite web |date=[[2008-02-13]] |author=Webster |url=http://jetvine.blogspot.com/2008/02/baa-and-emirates-test-new-baggage.html |title=BAA and Emirates test new baggage tagging technology |publisher=Jetvine |accessdate=2008-02-13}}</ref> |
||
*BGN has launched two fully automated [[Smartstores]] that combine item-level RFID tagging and |
*BGN has launched two fully automated [[Smartstores]] that combine item-level RFID tagging and SOA to deliver an integrated supply chain, from warehouse to consumer. |
||
*[[Ultra high frequency|UHF]], Ultra-HighFID or UHFID tags are commonly used commercially in case, pallet, and shipping container tracking, and [[truck]] and trailer tracking in shipping yards. |
*[[Ultra high frequency|UHF]], Ultra-HighFID or UHFID tags are commonly used commercially in case, pallet, and shipping container tracking, and [[truck]] and trailer tracking in shipping yards. |
||
*In May 2007, Bear River Supply began utilizing |
*In May 2007, Bear River Supply began utilizing ultra high frequency identification (UHFID) tags to help monitor their agricultural equipment. <ref>{{cite web |date=[[2007-10-18]] |author=Beth Bacheldor |url=http://www.rfidjournal.com/article/articleview/3690/1/1/ |title=Agricultural Company Tracks Equipment Loaned to Farmers |publisher=RFID Journal |accessdate=2008-01-03}}</ref> |
||
*In [[Colombia]], "Federación Nacional de Cafeteros" uses an RFID solution to trace the coffee. |
*In [[Colombia]], "Federación Nacional de Cafeteros" uses an RFID solution to trace the coffee. |
||
===Transportation and logistics=== |
|||
*Logistics & Transportation is a major area of implementation for RFID technology. For example, Yard Management, Shipping & Freight and Distribution Centers are some areas where RFID tracking technology is used. Transportation companies around the world value RFID technology due to its impact on the business value and efficiency. |
|||
*The North American [[rail transport|railroad]] industry operates an automatic equipment identification system based on RFID. Locomotives and rolling stock are equipped with two passive RFID tags (one mounted on each side of the equipment); the data encoded on each tag identifies the equipment owner, car number, type of equipment, number of axles, etc. The equipment owner and car number can be used to derive further data about the physical characteristics of the equipment from the [[Association of American Railroads]]' car inventory database and the railroad's own database indicating the [[lading]], origin, destination, etc. of the commodities being carried.<ref>{{ cite web | url=http://www.aeitag.com/aeirfidtec.html | title=AEI technology | publisher=Softrail | accessdate=2008-10-12 }}</ref> |
|||
===Lap scoring=== |
===Lap scoring=== |
||
Passive and active RFID systems are used in off road events such as [[Enduro]] and [[Hare and Hound (Motorcycle Race)|Hare and Hounds]] racing, the riders have a transponder on their person, normally on their arm. When they complete a lap they swipe or touch the receiver which is connected to a computer and log their lap time. The [[Casimo Group Ltd]] makes a system which does this. |
|||
Passive and active RFID systems are used in off-road events such as [[Enduro]] and [[Hare and Hound (Motorcycle Race)|Hare and Hounds]] racing. Riders have a transponder on their person, normally on their arm. When they complete a lap they swipe or touch the receiver which is connected to a computer and log their lap time. The [[Casimo Group Ltd]] sells such a system. |
|||
===Animal identification=== |
===Animal identification=== |
||
{{Main|Microchip implant (animal)}} |
{{Main|Microchip implant (animal)}} |
||
Implantable RFID tags or [[transponder]]s can be used for animal identification. The transponders are more well-known as passive RFID technology, or simply "Chips" on [[Microchip implant (animal)|animals]].<ref>*[http://www.thenation.com/doc/20071231/pentland_gumpert USDA Bets the Farm on Animal ID Program]</ref> |
Implantable RFID tags or [[transponder]]s can be used for animal identification. The transponders are more well-known as passive RFID technology, or simply "Chips" on [[Microchip implant (animal)|animals]].<ref>*[http://www.thenation.com/doc/20071231/pentland_gumpert USDA Bets the Farm on Animal ID Program]</ref> |
||
===Inventory systems=== |
===Inventory systems=== |
||
An advanced automatic identification technology such as the Auto-ID system based on the Radio Frequency Identification (RFID) technology has significant value for inventory systems. Notably, the technology provides an accurate knowledge of the current inventory. In an academic study<ref>[http://www.rfidradio.com/?p=11 RFID’s reduction of Out-of-Stock study at Wal-Mart], RFID Radio</ref> performed at Wal-Mart, RFID reduced Out-of-Stocks by 30 percent for products selling between 0.1 and 15 units a day. Other benefits of using RFID include the reduction of labor costs, the simplification of business processes, and the reduction of inventory inaccuracies. |
|||
An advanced automatic identification technology such as the Auto-ID system based on the Radio Frequency Identification (RFID) technology has significant value for inventory systems. Notably, the technology provides an accurate knowledge of the current inventory. In an academic study<ref>[http://www.rfidradio.com/?p=11 RFID's reduction of Out-of-Stock study at Wal-Mart], RFID Radio</ref> performed at Wal-Mart, RFID reduced Out-of-Stocks by 30 percent for products selling between 0.1 and 15 units a day. Other benefits of using RFID include the reduction of labor costs, the simplification of business processes, and the reduction of inventory inaccuracies. |
|||
In 2004, Boeing integrated the use of RFID technology to help reduce maintenance and inventory costs on the [[Boeing 787 Dreamliner]]. With the high costs of aircraft parts, RFID technology allowed Boeing to keep track of inventory despite the unique sizes, shapes and environmental concerns. During the first six months after integration, the company was able to save $29,000 in just labor.<ref>[http://www.businessweek.com/technology/content/aug2005/tc2005089_4131_tc_215.htm RFID's Second Wave], BusinessWeek</ref> |
In 2004, Boeing integrated the use of RFID technology to help reduce maintenance and inventory costs on the [[Boeing 787 Dreamliner]]. With the high costs of aircraft parts, RFID technology allowed Boeing to keep track of inventory despite the unique sizes, shapes and environmental concerns. During the first six months after integration, the company was able to save $29,000 in just labor.<ref>[http://www.businessweek.com/technology/content/aug2005/tc2005089_4131_tc_215.htm RFID's Second Wave], BusinessWeek</ref> |
||
====RFID mandates==== |
====RFID mandates==== |
||
[[Wal-Mart]] and the [[United States Department of Defense]] have published requirements that their vendors place RFID tags on all shipments to improve [[supply chain management]]. Due to the size of these two organizations, their RFID mandates impact thousands of companies worldwide. The deadlines have been extended several times because many vendors face significant difficulties implementing RFID systems. In practice, the successful read rates currently run only 80%, due to radio wave [[attenuation]] caused by the products and [[packaging]]. In time it is expected that even small companies will be able to place RFID tags on their outbound shipments. |
[[Wal-Mart]] and the [[United States Department of Defense]] have published requirements that their vendors place RFID tags on all shipments to improve [[supply chain management]]. Due to the size of these two organizations, their RFID mandates impact thousands of companies worldwide. The deadlines have been extended several times because many vendors face significant difficulties implementing RFID systems. In practice, the successful read rates currently run only 80%, due to radio wave [[attenuation]] caused by the products and [[packaging]]. In time it is expected that even small companies will be able to place RFID tags on their outbound shipments. |
||
Since January 2005, Wal-Mart has required its top 100 suppliers to apply RFID labels to all shipments. To meet this requirement, vendors use RFID printer/encoders to label cases and pallets that require [[Electronic Product Code|EPC]] tags for Wal-Mart. These smart labels are produced by embedding RFID inlays inside the [[label]] material, and then printing bar code and other visible information on the surface of the label. |
Since January, 2005, Wal-Mart has required its top 100 suppliers to apply RFID labels to all shipments. To meet this requirement, vendors use RFID printer/encoders to label cases and pallets that require [[Electronic Product Code|EPC]] tags for [[Wal-Mart]]. These smart labels are produced by embedding RFID inlays inside the [[label]] material, and then printing bar code and other visible information on the surface of the label. |
||
Another Wal-Mart division, [[Sam's Club]], has also moved in this direction. It sent letters dated Jan. 7, 2008 to its suppliers, stating that by Jan. 31, 2008, every full single-item [[pallet]] shipped to its distribution center in DeSoto, Texas, or directly to one of its stores served by that DC, must bear an EPC Gen 2 RFID tag. Suppliers failing to comply will be charged a service fee. <ref> {{cite news |first=Beth |last=Bacheldor |title=Sam's Club Tells Suppliers to Tag or Pay |url=http://www.rfidjournal.com/article/articleview/3845/1/1/ |date=2008-01-11 |accessdate=2008-01-17 }}</ref> |
Another Wal-Mart division, [[Sam's Club]], has also moved in this direction. It sent letters dated Jan. 7, 2008, to all of its suppliers, stating that by Jan. 31, 2008, every full single-item [[pallet]] shipped to its distribution center in DeSoto, Texas, or directly to one of its stores served by that DC, must bear an EPC Gen 2 RFID tag. Suppliers failing to comply will be charged a service fee. <ref> {{cite news |first=Beth |last=Bacheldor |title=Sam's Club Tells Suppliers to Tag or Pay |url=http://www.rfidjournal.com/article/articleview/3845/1/1/ |date=2008-01-11 |accessdate=2008-01-17 }}</ref> |
||
==== Promotion tracking ==== |
==== Promotion tracking ==== |
||
Manufacturers of products sold through retailers promote their products by offering discounts for a limited period on products sold to retailers with the expectation that the retailers will pass on the savings to their customers. However, retailers typically engage in ''forward buying'', purchasing more product during the discount period than they intend to sell during the promotion period. Some retailers engage in a form of [[arbitrage]], reselling discounted product to other retailers, a practice known as ''diverting''. To combat this practice, manufacturers are exploring the use of RFID tags on promoted merchandise so that they can track exactly which product has sold through the supply chain at fully discounted prices.<ref>{{cite web|title='''Keeping Track of Promotion Progress: How Marketing Will Become the Greatest Advocate of RFID'''|coauthers=James P. Farrell and Ralf Saykiewicz|publication=''Consumer Goods Technology'' |url=http://www.consumergoods.com/ME2/dirmod.asp?sid=&nm=&type=Publishing&mod=Publications%3A%3AArticle&mid=8F3A7027421841978F18BE895F87F791&tier=4&id=07CA1C544D3E4FD1916C7A6D2638913E |accessdate=2008-04-10}}</ref> |
Manufacturers of products sold through retailers promote their products by offering discounts for a limited period on products sold to retailers with the expectation that the retailers will pass on the savings to their customers. However, retailers typically engage in ''forward buying'', purchasing more product during the discount period than they intend to sell during the promotion period. Some retailers engage in a form of [[arbitrage]], reselling discounted product to other retailers, a practice known as ''diverting''. To combat this practice, manufacturers are exploring the use of RFID tags on promoted merchandise so that they can track exactly which product has sold through the supply chain at fully discounted prices.<ref>{{cite web|title='''Keeping Track of Promotion Progress: How Marketing Will Become the Greatest Advocate of RFID'''|coauthers=James P. Farrell and Ralf Saykiewicz|publication=''Consumer Goods Technology'' |url=http://www.consumergoods.com/ME2/dirmod.asp?sid=&nm=&type=Publishing&mod=Publications%3A%3AArticle&mid=8F3A7027421841978F18BE895F87F791&tier=4&id=07CA1C544D3E4FD1916C7A6D2638913E |accessdate=2008-04-10}}</ref> |
||
===Human implants=== |
===Human implants=== |
||
[[Image:RFID hand 1.jpg|thumb|Hand with the planned location of the RFID chip.]] |
[[Image:RFID hand 1.jpg|thumb|Hand with the planned location of the RFID chip.]] |
||
[[Image:RFID hand 2.jpg|thumb|Just after the operation to insert the RFID tag was completed.]] |
[[Image:RFID hand 2.jpg|thumb|Just after the operation to insert the RFID tag was completed.]] |
||
| Line 273: | Line 228: | ||
In 2004, the Mexican Attorney General's office implanted 18 of its staff members with the [[Verichip]] to control access to a secure data room. (This number has been variously mis-reported as 160 or 180 staff members.<ref>{{cite web|url=http://www.theregister.co.uk/2004/07/14/mexicans_get_chipped/|title=The Register, among others, inaccurately reports 160 staff members being chipped.|accessdate=2007-08-01|publisher=[[The Register]]}}</ref> <ref>{{cite web|url=http://www.theregister.co.uk/2004/11/30/mexican_verichip_hype/|title=The Register publishes a correction to the number of staff being chipped.|accessdate=2007-08-01|publisher=[[The Register]]}}</ref>) |
In 2004, the Mexican Attorney General's office implanted 18 of its staff members with the [[Verichip]] to control access to a secure data room. (This number has been variously mis-reported as 160 or 180 staff members.<ref>{{cite web|url=http://www.theregister.co.uk/2004/07/14/mexicans_get_chipped/|title=The Register, among others, inaccurately reports 160 staff members being chipped.|accessdate=2007-08-01|publisher=[[The Register]]}}</ref> <ref>{{cite web|url=http://www.theregister.co.uk/2004/11/30/mexican_verichip_hype/|title=The Register publishes a correction to the number of staff being chipped.|accessdate=2007-08-01|publisher=[[The Register]]}}</ref>) |
||
Security experts have warned against using RFID for authenticating people due to the risk of [[identity theft]]. For instance a [[man-in-the-middle attack]] would make it possible for an attacker to steal the identity of a person in real-time. Due to the resource |
Security experts have warned against using RFID for authenticating people due to the risk of [[identity theft]]. For instance a [[man-in-the-middle attack]] would make it possible for an attacker to steal the identity of a person in real-time. Due to the resource-constraints of RFIDs it is virtually impossible to protect against such attack models as this would require complex distance-binding protocols. <ref>[http://blogs.reuters.com/blog/2006/07/22/high-tech-cloning High-tech cloning]</ref><ref>[http://www.spychips.com/press-releases/verichip-hacked.html Vericip hacked press release], Spychips</ref><ref>{{cite web |url=http://cq.cx/verichip.pl |title=Demo: Cloning a Verichip |accessdate=2007-02-03}}</ref><ref>{{cite web|title=VeriChips Implanted at CityWatcher.com | url=http://www.complianceandprivacy.com/News-VeriChip-concern.asp |publisher=Compliance and Privacy | accessdate=2007-02-03 | quote=No one I spoke with at Six Sigma Security or at CityWatcher knew that the VeriChip had been hacked. They were also surprised to hear of VeriChip's downsides as a medical device. It was clear they weren't aware of some of the controversy surrounding the implant. (Liz McIntyre)}}</ref> |
||
===Libraries=== |
===Libraries=== |
||
[[Image:Tags.jpg|thumb|RFID tags used in libraries: square book tag, round CD/DVD tag and rectangular VHS tag.]] |
[[Image:Tags.jpg|thumb|RFID tags used in libraries: square book tag, round CD/DVD tag and rectangular VHS tag.]] |
||
Among the many uses of RFID technologies is its deployment in [[library|libraries]]. This technology has slowly begun to replace the traditional barcodes on library items (books, [[compact discs|CDs]], [[DVD]]s, etc.). |
Among the many uses of RFID technologies is its deployment in [[library|libraries]]. This technology has slowly begun to replace the traditional barcodes on library items (books, [[compact discs|CDs]], [[DVD]]s, etc.). However, the RFID tag can contain identifying information, such as a book’s title or material type, without having to be pointed to a separate [[database]] (but this is rare in North America). The information is read by an RFID reader, which replaces the standard [[barcode reader]] commonly found at a library’s circulation desk. The RFID tag found on library materials typically measures 50 mm X 50 mm in North America and 50 mm x 75 mm in Europe. It may replace or be added to the [[barcode]], offering a different means of inventory management by the staff and [[self service]] by the borrowers. It can also act as a [[security]] device, taking the place of the more traditional [[Electronic article surveillance|electromagnetic security strip]] <ref name="butters">Radio Frequency Identification: An Introduction for Library Professionals. Alan Butters. ''Australasian Public Libraries'' v19.n4(2006) pp.2164–174.</ref> And not only the books, but also the membership cards could be fitted with an RFID tag. |
||
While there is some debate as to when and where RFID in libraries first began, it was first proposed in the late 1990s as a technology that would enhance workflow in the library setting. [[Singapore]] was certainly one of the first to introduce RFID in libraries and [[Rockefeller University]] in [[New York]] may have been the first academic library in the [[United States]] to utilize this technology, whereas |
While there is some debate as to when and where RFID in libraries first began, it was first proposed in the late 1990s as a technology that would enhance workflow in the library setting. [[Singapore]] was certainly one of the first to introduce RFID in libraries and [[Rockefeller University]] in [[New York]] may have been the first academic library in the [[United States]] to utilize this technology, whereas Farmington Community Library may have been the first public institution, both of which began using RFID in 1999. In [[Europe]], the first public library to use rfid was the one in [[Hoogezand-Sappemeer]], the [[Netherlands]], in 2001, where borrowers were given an option. To their surprise, 70% used the RFID option and quickly adapted, including elderly people. |
||
Worldwide, in absolute numbers, RFID is used most |
Worldwide, in absolute numbers, RFID is used most the United States (with its 300 million inhabitants), followed by the [[United Kingdom]] and [[Japan]]. It is estimated that over 30 million library items worldwide now contain RFID tags, including some in the [[Vatican Library]] in [[Rome]].<ref name="singh">"The State of RFID Applications in Libraries." Jay Singh et al. ''Information Technology & Libraries'' no.1(Mar.2006) pp.24–32.</ref> |
||
RFID has many |
RFID has many applications in libraries that can be highly beneficial, particularly for circulation staff. Since RFID tags can be read through an item, there is no need to open a book cover or DVD case to scan an item. This would help alleviate injuries such as [[repetitive strain injury]] that can occur over many years if done by the library staff. Where the books have a barcode on the outside, there is still the advantage that borrowers can scan an entire pile of books in one go, instead of one at a time. Since RFID tags can also be read while an item is in motion, using RFID readers to check-in returned items while on a [[conveyer belt|conveyor belt]] reduces staff time. But, as with barcode, this can all be done by the borrowers themselves, meaning they might never again need the assistance of staff. Next to these readers with a fixed location there are also portable ones (for librarians, but in the future possibly also for borrowers, possibly even their own general purpose readers). With these, inventories could be done on a whole shelf of materials within seconds, without a book ever having to be taken off the shelf.<ref>"Radio Frequency Identification." Rachel Wadham. "Library Mosaics" v14 no.5 (S/O 2003) pg.22.</ref>. In [[Umeå]], [[Sweden]], it is being used to assist visually impaired people in borrowing audiobooks<ref>[http://www.umea.se/omkommunen/languages/inenglish/culturalactivitieslibraries/libraryservices/projects/library2007/audioindexthetalkinglibrary.4.64e618c10982eb6c427fff10897.html AudioIndex - the Talking Library], Retrieved on 2007-07-25</ref>. In Malaysia, Smart Shelves are used to pinpoint the exact location of books in Multimedia University Library, Cyberjaya<ref>{{cite web|first=Rohisyam | last=Rahman | url=http://www.rfid-asia.info/2007/07/case-study-malaysian-smart-shelf.htm |title= |
||
Case Study: Malaysian Smart Shelf |publisher=[[RFID Asia]] |date=[[2007-07-23]] |accessdate=2007-08-03}}</ref>. In the Netherlands, handheld readers are being introduced for this purpose. |
Case Study: Malaysian Smart Shelf |publisher=[[RFID Asia]] |date=[[2007-07-23]] |accessdate=2007-08-03}}</ref>. In the Netherlands, handheld readers are being introduced for this purpose. |
||
The Dutch Union of Public Libraries ('Vereniging van Openbare Bibliotheken') is working on the concept of an interactive 'context library', where borrowers |
The Dutch Union of Public Libraries ('Vereniging van Openbare Bibliotheken') is working on the concept of an interactive 'context library', where borrowers gets a reader/headphones-set, which leads them to the desired section of the library (using triangulation methods, rather like [[Global Navigation Satellite System|GPS]] or [[TomTom]]) and which they can use to read information from books on the shelves with the desired level of detail (eg a section read out loud), coming from the book's tag itself or a database elsewhere, and get tips on alternatives, based on the borrowers' preferences, thus creating a more personalised version of the library. This may also lead them to sections of the library they might otherwise never have visited. Borrowers could also use the system to exchange experiences (such as grading books). This is already done by children in the virtual realm at [http://www.mijnstempel.nl/003_hoofdscherm/main.asp?groep=1316 mijnstempel.nl], but the same could be done in physical form. Borrowers might grade the book at the return desk. |
||
However, as of 2008 this technology remains |
However, as of 2008 this technology still remains cost prohibitive for many smaller libraries, and the conversion time has been estimated at 11 months for an average size library. A Dutch estimate in 2004 was that a library that lends out 100,000 books per year should count on an initial cost of 50,000 euro (borrow- and return-stations 12,500 euro each, detection porches 10,000 euro each and tags 0.36 euro each). RFID taking a large burden off staff could also mean that fewer staff will be needed, resulting in some of them getting fired,<ref name="singh">the</ref> but that has so far not happened in North America where recent surveys have not returned a single library that cut staff because of adding RFID. In fact, library budgets are being reduced for personnel and increased for infrastructure, making it necessary for libraries to add automation to compensate for the reduced staff size.<!-- now what is it, have there been staff cuts or not? --> Also, the tasks that RFID takes over are largely not the primary task of librarians. A finding in the Netherlands is that borrowers are pleased with the fact that staff are now more available for answering questions. |
||
A concern surrounding RFID in libraries that has received considerable publicity is the issue of privacy. Because RFID tags can in theory be scanned and read from |
A concern surrounding RFID in libraries that has received considerable publicity is the issue of privacy. Because RFID tags can in theory be scanned and read from over 350 feet in distance, and because RFID utilizes an assortment of [[frequency|frequencies]] (both depending on the type of tag, though), there is some concern over whether sensitive information could be collected from an unwilling source. However, library RFID tags do not contain any patron information,<ref>"RFID Poses No Problem for Patron Privacy." "American Libraries" v34 no11 (D 2003) pg.86.</ref> and the tags used in the majority of libraries use a frequency only readable from approximately ten feet.<ref name="butters">the</ref> Also, libraries have always had to keep records of who has borrowed what, so in that sense there is nothing new. One simple option is to only let the book transmit a code, that will only mean anything in conjunction with the library's database. Another step further is to give the book a new code every time it is returned. And if in the future readers become ubiquitous (and possibly networked), then stolen books could be traced even outside the library. Removing of the tags could be made difficult if they are so small that they fit invisibly inside a (random) page, possibly put there by the publisher. |
||
===Schools and universities=== |
===Schools and universities=== |
||
School authorities in the Japanese city of Osaka are now chipping children's clothing, back packs, and student IDs in a primary school.<ref name = LAN>http://networks.silicon.com/lans/0,39024663,39122042,00.htm Schoolchildren to be RFID-chipped</ref> |
School authorities in the Japanese city of Osaka are now chipping children's clothing, back packs, and student IDs in a primary school.<ref name = LAN>http://networks.silicon.com/lans/0,39024663,39122042,00.htm Schoolchildren to be RFID-chipped</ref> |
||
A school in [[Doncaster]], [[England]] is piloting a monitoring system designed to keep tabs on pupils by tracking radio chips in their uniforms.<ref>[http://www.theregister.co.uk/2007/10/22/kid_chipping_doncaster_go/ Schoolkid chipping trial 'a success']</ref> |
|||
===Museums=== |
===Museums=== |
||
RFID technologies are now also implemented in end-user applications in museums. An example is the custom-designed application eXsport at the Exploratorium, a science museum in San Francisco. When the visitor enters the museum he receives an RF Tag that can be carried on a card or necklace. The eXspot system enables the visitor to receive information about the exhibit and take photos they can collect later at the giftshop. Later on they can visit their personal Web page on which specific information such as visit dates, the visited exhibits and the taken photographs can be viewed.<ref>S. Hsi en H. Fait, “RFID enhances visitors Museum Experience at the Exploratorium,” Communications of the ACM 48, 9 (2005): 60</ref> |
|||
RFID technologies are now also implemented in end-user applications in museums. An example is the custom-designed application "eXsport" at the [[Exploratorium]], a science museum in [[San Francisco, California]]. A visitor entering the museum receives an RF Tag that can be carried on a card or necklace. The eXspot system enables the visitor to receive information about the exhibit and take photos to be collected at the giftshop. Later they can visit their personal Web page on which specific information such as visit dates, the visited exhibits and the taken photographs can be viewed.<ref>S. Hsi en H. Fait, "RFID enhances visitors Museum Experience at the Exploratorium," Communications of the ACM 48, 9 (2005): 60</ref> |
|||
=== Social retailing === |
=== Social retailing === |
||
When a customer enters a dressing room, the mirror reflects their image and also images of the apparel item being worn by celebrities on an interactive display. A webcam also projects an image of the consumer wearing the item on the website for everyone to see. This creates an interaction between the consumers inside the store and their social network outside the store. The technology in this system is an RFID interrogator antenna in the dressing room and [[Electronic Product Code]] RFID tags on the apparel item<ref>[http://www.rfidradio.com/?p=20 Social Shopping in a Fully Enabled RFID Store], RFID Radio</ref>. |
|||
When customers enter a dressing room, the mirror reflects their image and also images of the apparel item being worn by celebrities on an interactive display. A webcam also projects an image of the consumer wearing the item on the website for everyone to see. This creates an interaction between the consumers inside the store and their social network outside the store. The technology in this system is an RFID interrogator antenna in the dressing room and [[Electronic Product Code]] RFID tags on the apparel item<ref>[http://www.rfidradio.com/?p=20 Social Shopping in a Fully Enabled RFID Store], RFID Radio</ref>. |
|||
=== Miscellaneous === |
=== Miscellaneous === |
||
* In February 2008, [[ThingMagic]] announced a partnership with [[Dewalt]] and [[Ford]] to equip 2009 Ford F-150, F-Series Super Duty pickups and E-Series vans with an embedded RFID asset tracking system enabled by ThingMagic’s Mercury5e readers. |
|||
* In November 2008, Dipole RFID Engineers, Spanish company located in [[Barcelona]], achieved to read 100% of a full pallet build from [[car battery|automotive Battery]]. Special tag designs and more antenna gain are the keys for the successful.<ref>[http://www.dipole.es/RFID/RFID_Empresa/ing/Dipole_Presentation_ing.html Santiago Depares]</ref> |
|||
* In November 2007, French company [http://www.violet.net/index_us.html/ Violet] starts selling its RFID-enabled [[Nabaztag]] with children's books (from publisher [[Gallimard Jeunesse]]) that included RFID tags inside the front cover. When the book is passed in front of the [[Nabaztag]], it downloads the audio book on the Internet and reads the book out loud. |
|||
* In February 2008, [[ThingMagic]] announced a partnership with [[Dewalt]] and [[Ford]] to equip 2009 Ford F-150, F-Series Super Duty pickups and E-Series vans with an embedded RFID asset tracking system enabled by ThingMagic's Mercury5e readers. |
|||
* In November 2007, French company Violet started selling its RFID-enabled [[Nabaztag]] with children's books (from publisher [[Gallimard Jeunesse]]) that included RFID tags inside the front cover. When the book is passed in front of the [[Nabaztag]], it downloads the audio book on the Internet and reads the book out loud. |
|||
* Some hospitals use Active RFID tags to perform [[Mobile asset management|Asset Tracking]] in Real Time.<ref>[http://www.rfidradio.com/?p=12 Making Business Sense of Real Time Location Systems (RTLS)], RFID Radio</ref> |
* Some hospitals use Active RFID tags to perform [[Mobile asset management|Asset Tracking]] in Real Time.<ref>[http://www.rfidradio.com/?p=12 Making Business Sense of Real Time Location Systems (RTLS)], RFID Radio</ref> |
||
* In 2006, the Smart Conveyer Tunnel, designed by [[Blue Vector]], was introduced. This allowed the [[pharmaceutical]] industry to track both [[Ultra high frequency|UHF]] and [[High frequency|HF]] tags. [[Rite Aid]] utilized the technology with some of [[McKesson]]'s products.<ref>[http://www.rfidjournal.com/article/articleview/2821/ Rite Aid Embarks on Item-Level Tracking Pilot], RFID Journal</ref> |
|||
* In February 2007, Spanish technicians recruited now by Dipole RFID Engineers [[Barcelona]], achieved to read 99.8% of a [[Tetra Pak]] milk pallet with more than 100 boxes in it. Impinj was collaborated like a major technology provider.<ref>[http://www.dipole.es/index_ing.html Dipole RFID Engineers]</ref> |
|||
* In 2006, the Smart Conveyor Tunnel, designed by [[Blue Vector]], was introduced. This allowed the [[pharmaceutical]] industry to track both [[Ultra high frequency|UHF]] and [[High frequency|HF]] tags. [[Rite Aid]] utilized the technology with some of [[McKesson Corporation]]'s products.<ref>[http://www.rfidjournal.com/article/articleview/2821/ Rite Aid Embarks on Item-Level Tracking Pilot], RFID Journal</ref> |
|||
* The [[NEXUS (frequent traveller program)|NEXUS]] and [[SENTRI]] frequent traveler programs use RFID to speed up landborder processing between the U.S. and Canada and Mexico. <ref>[http://www.cbp.gov/xp/cgov/travel/frequent_traveler/nexus_prog/nexus.xml US Customs and Border Protection NEXUS website][http://www.cbp.gov/xp/cgov/travel/frequent_traveler/sentri/sentri.xml US Customs and Border Protection SENTRI website]</ref> |
* The [[NEXUS (frequent traveller program)|NEXUS]] and [[SENTRI]] frequent traveler programs use RFID to speed up landborder processing between the U.S. and Canada and Mexico. <ref>[http://www.cbp.gov/xp/cgov/travel/frequent_traveler/nexus_prog/nexus.xml US Customs and Border Protection NEXUS website][http://www.cbp.gov/xp/cgov/travel/frequent_traveler/sentri/sentri.xml US Customs and Border Protection SENTRI website]</ref> |
||
* [[NADRA]] has developed an RFID-based [[driver license]] that bears the license holder's personal information and stores data regarding traffic violations, tickets issued, and outstanding penalties. The license cards are designed so that driving rights can be revoked electronically in case of serious violations.<ref>[http://www.nadra.gov.pk/site/395/default.aspx NADRA Driving License][http://www.nadra.gov.pk/site/395/default.aspx NADRA Driving License]</ref> |
* [[NADRA]] has developed an RFID-based [[driver license]] that bears the license holder's personal information and stores data regarding traffic violations, tickets issued, and outstanding penalties. The license cards are designed so that driving rights can be revoked electronically in case of serious violations.<ref>[http://www.nadra.gov.pk/site/395/default.aspx NADRA Driving License][http://www.nadra.gov.pk/site/395/default.aspx NADRA Driving License]</ref> |
||
* [[Sensor]]s such as [[seismic]] sensors may be read using RFID transceivers, greatly simplifying [[telemetry|remote data collection]]. |
* [[Sensor]]s such as [[seismic]] sensors may be read using RFID transceivers, greatly simplifying [[telemetry|remote data collection]]. |
||
* In August 2004, the [[Ohio]] Department of Rehabilitation and Correction (ODRC) approved a $415,000 contract to evaluate the personnel |
* In August 2004, the [[Ohio]] Department of Rehabilitation and Correction (ODRC) approved a $415,000 contract to evaluate the personnel tracking technology of [[Alanco Technologies]]. Inmates will wear wristwatch-sized [[transmitters]] that can detect attempted removal and alert [[prison]] computers. This project is not the first rollout of tracking chips in US prisons. Facilities in [[Michigan]], California and Illinois already employ the technology. |
||
* [[Transponder timing]] at mass sports events. |
* [[Transponder timing]] at mass sports events. |
||
* Used as storage for a [[video game]] system produced by [[Mattel]], "[[HyperScan]]". |
* Used as storage for a [[video game]] system produced by [[Mattel]], "[[HyperScan]]". |
||
* [[RFIQin]], designed by [[Vita Craft Corporation|Vita Craft]], is an automatic cooking device that has three different sized pans, a [[Portable stove|portable]] [[induction cooking|induction heater]], and recipe cards. Each pan is embedded with an RFID tag that monitors the food 16 times per second while an MI tag in the handle of the pans transmits signals to the [[induction cooking|induction heater]] to adjust the temperature. |
* [[RFIQin]], designed by [[Vita Craft Corporation|Vita Craft]], is an automatic cooking device that has three different sized pans, a [[Portable stove|portable]] [[induction cooking|induction heater]], and recipe cards. Each pan is embedded with an RFID tag that monitors the food 16 times per second while an MI tag in the handle of the pans transmits signals to the [[induction cooking|induction heater]] to adjust the temperature. |
||
* [[Slippery Rock University]] is using RFID tags in their students' ID cards beginning in the fall 2007 semester. |
* [[Slippery Rock University]] is using RFID tags in their students' ID cards beginning in the fall 2007 semester. |
||
* 25 real |
* 25 real world application case studies can be found in a 61 page free Ebook [http://www.bin95.com/case_studies/RFID_Technology_Applications.htm RFID Technology Applications] |
||
* RFID tags are now being embedded into playing cards that are used for televisied poker |
* RFID tags are now being embedded into playing cards that are used for televisied poker tournamnets, so commentators know exactly what cards has been dealt to whom, as soon as the deal is complete. |
||
* The Iraqi army uses an RFID security card that contains a biometric picture of the soldier. The picture in the chip must match the picture on the card to prevent forgery.<ref>[http://www.rfidradio.com/?p=9 Some Hot North American RFID Applications], RFID Radio</ref> |
* The Iraqi army uses an RFID security card that contains a biometric picture of the soldier. The picture in the chip must match the picture on the card to prevent forgery.<ref>[http://www.rfidradio.com/?p=9 Some Hot North American RFID Applications], RFID Radio</ref> |
||
* [[Theme parks]] (such as [[Alton Towers]] in the United Kingdom) have been known to use RFID to help them identify users of a ride in order to make a DVD of their time at the park. This is then available for the |
* [[Theme parks]] (such as [[Alton Towers]] in the United Kingdom) have been known to use RFID to help them identify users of a ride in order to make a DVD of their time at the park. This is then available for the user to buy at the end of the day. This is voluntary by the user by wearing a wristband given to them at the park. |
||
* [[Access control]] - many places which employ traditional swipe cards for access control are slowly shifting |
* [[Access control]] - many places which employ traditional swipe cards for access control are slowly shifting towards RFID contactless based solutions in their cards. |
||
* Meetings and conventions have also implemented RFID technology into attendee badges allowing the ability to track people at conferences. This provides data that can display what rooms people have enter and exited during the day |
* Meetings and conventions have also implemented RFID technology into attendee badges allowing the ability to track people at conferences. This provides data that can display what rooms people have enter and exited during the day. This data is available to show organizers to help them improve the content and design of the conference. RFID is also being used to improve the [[lead retrieval]] process for exhibitors at exhibitions. |
||
* RFID transponder chips have been implanted in [[golf ball]]s |
* RFID transponder chips have been implanted in [[golf ball]]s for the purposes of ball tracking. The uses of such tracking range from being able to search for a lost ball using a homing device, to a computerized [[driving range]] format that tracks shots made by a player and gives feedback on distance and accuracy. |
||
* In 2007 artist couple artcoon starts their world project [http://www.artcoon.com/v4_home_kansa.php Kansa]. Sirpa Masalins human like wooden sculptures carry an RFID inside. Hans-Ulrich Goller-Masalin created a New Media Art work which traces the individual sculptures of Kansa in the internet. Owners are asked to register the city where their sculpture is located. By comparing the RFIDs unique number referenced at artcoon the owner can identify his sculpture as the original one. |
* In 2007 artist couple artcoon starts their world project [http://www.artcoon.com/v4_home_kansa.php Kansa]. Sirpa Masalins human like wooden sculptures carry an RFID inside. Hans-Ulrich Goller-Masalin created a New Media Art work which traces the individual sculptures of Kansa in the internet. Owners are asked to register the city where their sculpture is located. By comparing the RFIDs unique number referenced at artcoon the owner can identify his sculpture as the original one. |
||
* Some casinos are embedding RFID tags into their chips. This allows the casinos to track the locations of chips on the casino floor, identify counterfeit chips, and prevent theft. In addition, casinos can use RFID systems to study the betting behavior of players. |
* Some casinos are embedding RFID tags into their chips. This allows the casinos to track the locations of chips on the casino floor, identify counterfeit chips, and prevent theft. In addition, casinos can use RFID systems to study the betting behavior of players. |
||
* Hong Kong International Airport places RFID sticker labels on all incoming baggage when received, encoded with the destination and flight. |
|||
== Potential uses == |
== Potential uses == |
||
=== Replacing barcodes === |
=== Replacing barcodes === |
||
RFID tags are often a replacement for [[Universal Product Code|UPC]] or [[European Article Number|EAN]] barcodes, having a number of important advantages over the older barcode technology. They may not ever completely replace barcodes, due in part to their higher cost and the advantage of multiple data sources on the same object. The new [[Electronic Product Code|EPC]], along with several other schemes, is widely available at reasonable cost. |
RFID tags are often a replacement for [[Universal Product Code|UPC]] or [[European Article Number|EAN]] barcodes, having a number of important advantages over the older barcode technology. They may not ever completely replace barcodes, due in part to their higher cost and the advantage of multiple data sources on the same object. The new [[Electronic Product Code|EPC]], along with several other schemes, is widely available at reasonable cost. |
||
| Line 342: | Line 291: | ||
It has also been proposed to use RFID for [[point of sale|POS]] store checkout to replace the [[cashier]] with an automatic system which needs no barcode scanning. This is not likely without a significant reduction in the cost of tags and changes in the POS process. There is some research taking place, however, this is some years from reaching fruition. |
It has also been proposed to use RFID for [[point of sale|POS]] store checkout to replace the [[cashier]] with an automatic system which needs no barcode scanning. This is not likely without a significant reduction in the cost of tags and changes in the POS process. There is some research taking place, however, this is some years from reaching fruition. |
||
An FDA |
An FDA nominated task force came to the conclusion after studying the various technologies currently commercially available, which could meet the pedigree requirements. Amongst all technologies studied including bar coding, RFID seemed to be the most promising and the committee felt that the pedigree requirement could be met by easily leveraging something that is readily available. (More details see [http://www.bin95.com/RFID-FDA-Regulations.htm RFID-FDA-Regulations]) |
||
===Telemetry=== |
===Telemetry=== |
||
Active RFID tags also have the potential to function as low-cost remote sensors that broadcast [[telemetry]] back to a base station. Applications of tagometry{{Fact|date=August 2007}} data could include sensing of road conditions by implanted beacons, weather reports, and noise level monitoring. CAZ |
|||
Active RFID tags also have the potential to function as low-cost remote sensors that broadcast [[telemetry]] back to a base station. Applications of tagometry{{Fact|date=August 2007}} data could include sensing of road conditions by implanted beacons, weather reports, and noise level monitoring. |
|||
It is possible that active or semi-passive RFID tags used with or in place of barcodes could broadcast a signal to an in-store receiver to determine whether the RFID tag (product) is in the store. |
It is possible that active or semi-passive RFID tags used with or in place of barcodes could broadcast a signal to an in-store receiver to determine whether the RFID tag (product) is in the store. |
||
===Identification of patients and hospital staff=== |
===Identification of patients and hospital staff=== |
||
In July 2004, the US [[Food and Drug Administration]] issued a ruling that essentially begins a final review process that will determine whether hospitals can use RFID systems to identify patients and/or permit relevant hospital staff to access [[medical records]]. Since then, a number of U.S. hospitals have begun implanting patients with RFID tags and using RFID systems, more generally, for workflow and inventory management.<ref>Fisher, Jill A. 2006. Indoor Positioning and Digital Management: Emerging Surveillance Regimes in Hospitals. In T. Monahan (Ed), ''Surveillance and Security: Technological Politics and Power in Everyday Life'' (pp. 77–88). New York: Routledge.[http://www.jillfisher.net/papers/rfid.pdf]</ref> There is some evidence, as well, that nurses and other hospital staff may be subjected to increased surveillance of their activities or to labor intensification as a result of the implementation of RFID systems in hospitals.<ref> Fisher, Jill A. and Monahan, Torin. Tracking the Social Dimensions of RFID Systems in Hospitals. International Journal of Medical Informatics 77 (3): 176-183.[http://torinmonahan.com/papers/Fisher_Monahan_RFID_IJMI.pdf]</ref> |
|||
In July 2004, the US [[Food and Drug Administration]] issued a ruling that essentially begins a final review process that will determine whether hospitals can use RFID systems to identify patients and/or permit relevant hospital staff to access [[medical records]]. Since then, a number of U.S. hospitals have begun implanting patients with RFID tags and using RFID systems, usually for workflow and inventory management.<ref>Fisher, Jill A. 2006. Indoor Positioning and Digital Management: Emerging Surveillance Regimes in Hospitals. In T. Monahan (Ed), ''Surveillance and Security: Technological Politics and Power in Everyday Life'' (pp. 77–88). New York: Routledge.[http://www.jillfisher.net/papers/rfid.pdf]</ref> There is some evidence, as well, that nurses and other hospital staff may be subjected to increased surveillance of their activities or to labor intensification as a result of the implementation of RFID systems in hospitals.<ref> Fisher, Jill A. and Monahan, Torin. Tracking the Social Dimensions of RFID Systems in Hospitals. International Journal of Medical Informatics 77 (3): 176-183.[http://torinmonahan.com/papers/Fisher_Monahan_RFID_IJMI.pdf]</ref> |
|||
The use of RFID to prevent mixups between [[spermatozoon|sperm]] and [[ovum|ova]] in [[IVF]] clinics is also being considered [http://www.newscientist.com/article.ns?id=dn7209]. |
The use of RFID to prevent mixups between [[spermatozoon|sperm]] and [[ovum|ova]] in [[IVF]] clinics is also being considered [http://www.newscientist.com/article.ns?id=dn7209]. |
||
| Line 360: | Line 307: | ||
== Possible uses for medical field == |
== Possible uses for medical field == |
||
Human tagging and tracking |
Human tagging and tracking can be a great asset for use in hospitals, more importantly emergency rooms. One reason being a nurse or doctor can easily access patient history or concerning files, allergies, or any other complications from the incoming patient. |
||
===Yoking=== |
===Yoking=== |
||
It has been proposed to use a [[strong cryptography]] based scheme to generate forensic evidence that two RFID tags were in proximity at the time of scanning.<ref>{{cite web|url=http://www.rsa.com/rsalabs/staff/bios/ajuels/publications/pdfs/rfid_survey_28_09_05.pdf|title=RFID security and privacy: a research survey}}</ref> |
|||
It has been proposed to use a [[strong cryptography]]-based scheme to generate forensic evidence that two RFID tags were in proximity at the time of scanning.<ref>{{cite web|url=http://www.rsa.com/rsalabs/staff/bios/ajuels/publications/pdfs/rfid_survey_28_09_05.pdf|title=RFID security and privacy: a research survey}}</ref> |
|||
==Regulation and standardization== |
==Regulation and standardization== |
||
There is no global public body that governs the frequencies used for RFID. In principle, every country can set its own rules for this. The main bodies governing frequency allocation for RFID are: |
There is no global public body that governs the frequencies used for RFID. In principle, every country can set its own rules for this. The main bodies governing frequency allocation for RFID are: |
||
* USA: FCC ([[Federal Communications Commission]]) |
* USA: FCC ([[Federal Communications Commission]]) |
||
* Canada: CRTC ([[Canadian Radio-television and Telecommunications Commission]]) |
* Canada: CRTC ([[Canadian Radio-television and Telecommunications Commission]]) |
||
* Europe: ERO, [[European Conference of Postal and Telecommunications Administrations|CEPT]], [[ETSI]], and national administrations (note that the national administrations must ratify the usage of a specific frequency before it can be used in that country) |
* Europe: ERO, [[European Conference of Postal and Telecommunications Administrations|CEPT]], [[ETSI]], and national administrations (note that the national administrations must ratify the usage of a specific frequency before it can be used in that country) |
||
* Malaysia: |
* Malaysia: Malaysian Communications and Multimedia Commission (MCMC) |
||
* Japan: MIC (Ministry of Internal Affairs and Communications) |
* Japan: MIC (Ministry of Internal Affairs and Communications) |
||
* China: Ministry of Information Industry |
* China: Ministry of Information Industry |
||
| Line 378: | Line 323: | ||
* South Africa: [http://www.icasa.org.za ICASA] |
* South Africa: [http://www.icasa.org.za ICASA] |
||
* South Korea: [[Ministry of Commerce, Industry and Energy]] |
* South Korea: [[Ministry of Commerce, Industry and Energy]] |
||
* Australia: [[Australian Communications and Media Authority]]. |
* Australia: [[Australian Communications and Media Authority]]. |
||
* New Zealand: [[New Zealand Ministry of Economic Development|Ministry of Economic Development]] |
* New Zealand: [[New Zealand Ministry of Economic Development|Ministry of Economic Development]] |
||
* Singapore: [[Infocomm Development Authority of Singapore]] |
* Singapore: [[Infocomm Development Authority of Singapore]] |
||
* Brazil: Anatel ([[Agência Nacional de Telecomunicações]]) |
* Brazil: Anatel ([[Agência Nacional de Telecomunicações]]) |
||
Low-frequency (LF: |
Low-frequency (LF: 125 – 134.2 kHz and 140 – 148.5 kHz) (LowFID) tags and high-frequency (HF: 13.56 MHz) (HighFID) tags can be used globally without a license. Ultra-high-frequency (UHF: 868 – 928 MHz) (Ultra-HighFID or UHFID) tags cannot be used globally as there is no single global standard. In North America, UHF can be used unlicensed for 902 – 928 MHz (±13 MHz from the 915 MHz center frequency), but restrictions exist for transmission power. In Europe, RFID and other low-power radio applications are regulated by ETSI recommendations EN 300 220 and EN 302 208, and ERO recommendation 70 03, allowing RFID operation with somewhat complex band restrictions from 865–868 MHz. Readers are required to monitor a channel before transmitting ("Listen Before Talk"); this requirement has led to some restrictions on performance, the resolution of which is a subject of current research. The North American UHF standard is not accepted in France as it interferes with its military bands. For China and Japan, there is no regulation for the use of UHF. Each application for UHF in these countries needs a site license, which needs to be applied for at the local authorities, and can be revoked. For Australia and New Zealand, 918 – 926 MHz are unlicensed, but restrictions exist for transmission power. |
||
These frequencies are known as the [[ISM band]]s (Industrial Scientific and Medical bands). The return signal of the tag may still cause [[Interference (communication)|interference]] for other radio users. |
These frequencies are known as the [[ISM band]]s (Industrial Scientific and Medical bands). The return signal of the tag may still cause [[Interference (communication)|interference]] for other radio users. |
||
Some |
Some standards that have been made regarding RFID technology include: |
||
*[[ISO 14223/1]] – Radio frequency identification of Animals, advanced transponders – Air interface |
*[[ISO 14223/1]] – Radio frequency identification of Animals, advanced transponders – Air interface |
||
*[[ISO 14443]]: This standard is a popular HF (13.56 |
*[[ISO 14443]]: This standard is a very popular HF (13.56 MHz) standard for HighFIDs which is being used as the basis of RFID-enabled passports under ICAO 9303. |
||
*[[ISO 15693]]: This is also a popular HF (13.56 |
*[[ISO 15693]]: This is also a very popular HF (13.56 MHz) standard for HighFIDs widely used for non-contact smart payment and credit cards. |
||
*[[ISO/IEC 18000]]: Information technology — Radio frequency identification for item management: |
*[[ISO/IEC 18000]]: Information technology — Radio frequency identification for item management: |
||
** Part 1: Reference architecture and definition of parameters to be standardized |
** Part 1: Reference architecture and definition of parameters to be standardized |
||
** Part 2: Parameters for air interface communications below 135 |
** Part 2: Parameters for air interface communications below 135 kHz |
||
** Part 3: Parameters for air interface communications at 13 |
** Part 3: Parameters for air interface communications at 13,56 MHz |
||
** Part 4: Parameters for air interface communications at 2 |
** Part 4: Parameters for air interface communications at 2,45 GHz |
||
** Part 6: Parameters for air interface communications at 860 |
** Part 6: Parameters for air interface communications at 860 MHz to 960 MHz |
||
** Part 7: Parameters for active air interface communications at 433 |
** Part 7: Parameters for active air interface communications at 433 MHz |
||
*[[ISO 18185]]: This is the industry standard for electronic seals or "e-seals" for tracking cargo containers using the 433 |
*[[ISO 18185]]: This is the industry standard for electronic seals or "e-seals" for tracking cargo containers using the 433 MHz and 2.4 GHz frequencies. |
||
*[[EPCglobal]] – this is the standardization framework that is most likely to undergo International Standardisation according to ISO rules as with all sound standards in the world, unless residing with limited scope, as customs regulations, air-traffic regulations and others. Currently the big distributors and governmental customers are pushing EPC heavily as a standard well |
*[[EPCglobal]] – this is the standardization framework that is most likely to undergo International Standardisation according to ISO rules as with all sound standards in the world, unless residing with limited scope, as customs regulations, air-traffic regulations and others. Currently the big distributors and governmental customers are pushing EPC heavily as a standard well accepted in their community, but not yet regarded as for salvation to the rest of the world. |
||
* [[ASTM]] D7434, Standard Test Method for Determining the Performance of Passive Radio Frequency Identification (RFID) Transponders on Palletized or Unitized Loads |
|||
* [[ASTM]] D7435, Standard Test Method for Determining the Performance of Passive Radio Frequency Identification (RFID) Transponders on Loaded Containers |
|||
===EPC Gen2=== |
===EPC Gen2=== |
||
EPC Gen2 is short for ''EPCglobal UHF Class 1 Generation 2''. |
EPC Gen2 is short for ''EPCglobal UHF Class 1 Generation 2''. |
||
| Line 412: | Line 353: | ||
One of the missions of EPCglobal was to simplify the Babel of protocols prevalent in the RFID world in the 1990s. Two tag air interfaces (the protocol for exchanging information between a tag and a reader) were defined (but not ratified) by EPCglobal prior to 2003. These protocols, commonly known as Class 0 and Class 1, saw significant commercial implementation in 2002–2005. |
One of the missions of EPCglobal was to simplify the Babel of protocols prevalent in the RFID world in the 1990s. Two tag air interfaces (the protocol for exchanging information between a tag and a reader) were defined (but not ratified) by EPCglobal prior to 2003. These protocols, commonly known as Class 0 and Class 1, saw significant commercial implementation in 2002–2005. |
||
In 2004 the Hardware Action Group created a new protocol, the Class 1 Generation 2 interface, which addressed a number of problems that had been experienced with Class 0 and Class 1 tags. The EPC Gen2 standard was approved in December 2004, and is likely to form the backbone of passive RFID tag standards moving forward. This was approved after a contention from [[Intermec]] that the standard may infringe a number of their RFID |
In 2004 the Hardware Action Group created a new protocol, the Class 1 Generation 2 interface, which addressed a number of problems that had been experienced with Class 0 and Class 1 tags. The EPC Gen2 standard was approved in December 2004, and is likely to form the backbone of passive RFID tag standards moving forward. This was approved after a contention from [[Intermec]] that the standard may infringe a number of their RFID related patents. It was decided that the standard itself did not infringe their patents, but it may be necessary to pay royalties to [[Intermec]] if the tag were to be read in a particular manner. The EPC Gen2 standard was adopted with minor modifications as ISO 18000-6C in 2006. |
||
The lowest cost of Gen2 EPC inlay is offered by [[SmartCode]] at a price of |
The lowest cost of Gen2 EPC inlay is offered by [[SmartCode]] at a price of 5 [[United States dollar#United States coins|cents]] apiece in volumes of 100 million or more<ref>{{cite news|first=Mark | last=Roberti | url=http://www.rfidjournal.com/article/articleview/2295/1/128/ |title= A 5-Cent Breakthrough |publisher=[[RFID Journal]] |date=[[2006-05-06]] | accessdate = 2007-01-26}}</ref>. Nevertheless, further conversion (including additional label stock or encapsulation processing/insertion and freight costs to a given facility or DC) and of the inlays into usable RFID labels and the design of current Gen 2 protocol standard will increase the total end-cost, especially with the added security feature extensions for RFID Supply Chain item-level tagging. |
||
== Problems and concerns == |
== Problems and concerns == |
||
| Line 422: | Line 363: | ||
===Security concerns=== |
===Security concerns=== |
||
A primary security concern surrounding technology is the illicit tracking of RFID tags. Tags which are world-readable pose a risk to both personal location privacy and corporate/military security. Such concerns have been raised with respect to the [[United States Department of Defense]]'s recent adoption of RFID tags for supply chain management.<ref>{{cite web | work = Radio Frequency Identification (RFID) | title = What's New | date = 4 April 2007 | url = http://www.acq.osd.mil/log/rfid/index.htm}}</ref> More generally, privacy organizations have expressed concerns in the context of ongoing efforts to embed electronic product code (EPC) RFID tags in consumer products. |
|||
EPCglobal Network, by design, is also susceptible to DoS attacks. Using similar mechanism with DNS in resolving EPC data requests, the ONS Root servers become vulnerable to DoS attacks. Any organisation planning to embark on EPCglobal Network may cringe upon finding out that the EPCglobal Network infrastructure inherits security weaknesses similar to DNS'<ref>{{cite web|first=Adi | last=Tedjasaputra | url=http://www.rfid-asia.info/2007/02/putting-rfid-network-security-in.htm | title=Putting RFID Network Security in Perspective | publisher=[[RFID Asia]] | date=[[2006-12-11]] | accessdate=2007-08-03}}</ref>. |
|||
A primary RFID security concern is the illicit tracking of RFID tags. Tags which are world-readable pose a risk to both personal location privacy and corporate/military security. Such concerns have been raised with respect to the [[United States Department of Defense]]'s recent adoption of RFID tags for supply chain management.<ref>{{cite web | work = Radio Frequency Identification (RFID) | title = What's New | date = 4 April 2007 | url = http://www.acq.osd.mil/log/rfid/index.htm}}</ref> More generally, privacy organizations have expressed concerns in the context of ongoing efforts to embed electronic product code (EPC) RFID tags in consumer products. |
|||
EPCglobal Network, by design, is also susceptible to [[Denial-of-service attack|DoS attacks]]. Using similar mechanism with DNS in resolving EPC data requests, the ONS Root servers become vulnerable to DoS attacks. Any organisation planning to embark on EPCglobal Network may cringe upon discovering that the EPCglobal Network infrastructure inherits security weaknesses similar to DNS'<ref>{{cite web|first=Adi | last=Tedjasaputra | url=http://www.rfid-asia.info/2007/02/putting-rfid-network-security-in.htm | title=Putting RFID Network Security in Perspective | publisher=[[RFID Asia]] | date=[[2006-12-11]] | accessdate=2007-08-03}}</ref>. |
|||
A second class of defense uses cryptography to prevent tag cloning. Some tags use a form of "[[rolling code]]" scheme, wherein the tag identifier information changes after each scan, thus reducing the usefulness of observed responses. More sophisticated devices engage in [[Challenge-response authentication]]s where the tag interacts with the reader. In these protocols, secret tag information is never sent over the insecure communication channel between tag and reader. Rather, the reader issues a challenge to the tag, which responds with a result computed using a cryptographic circuit keyed with some secret value. Such protocols may be based on [[symmetric key cryptography|symmetric]] or [[public key cryptography]]. Cryptographically-enabled tags typically have dramatically higher cost and power requirements than simpler equivalents, and as a result, deployment of these tags is much more limited. This cost/power limitation has led some manufacturers to implement cryptographic tags using substantially weakened, or proprietary encryption schemes, which do not necessarily resist sophisticated attack. For example, the Exxon-Mobil [[Speedpass]] uses a cryptographically-enabled tag manufactured by [[Texas Instruments]], called the [[Digital Signature Transponder]] (DST), which incorporates a weak, proprietary [[encryption]] scheme to perform a challenge-response protocol for lower cost. |
A second class of defense uses cryptography to prevent tag cloning. Some tags use a form of "[[rolling code]]" scheme, wherein the tag identifier information changes after each scan, thus reducing the usefulness of observed responses. More sophisticated devices engage in [[Challenge-response authentication]]s where the tag interacts with the reader. In these protocols, secret tag information is never sent over the insecure communication channel between tag and reader. Rather, the reader issues a challenge to the tag, which responds with a result computed using a cryptographic circuit keyed with some secret value. Such protocols may be based on [[symmetric key cryptography|symmetric]] or [[public key cryptography]]. Cryptographically-enabled tags typically have dramatically higher cost and power requirements than simpler equivalents, and as a result, deployment of these tags is much more limited. This cost/power limitation has led some manufacturers to implement cryptographic tags using substantially weakened, or proprietary encryption schemes, which do not necessarily resist sophisticated attack. For example, the Exxon-Mobil [[Speedpass]] uses a cryptographically-enabled tag manufactured by [[Texas Instruments]], called the [[Digital Signature Transponder]] (DST), which incorporates a weak, proprietary [[encryption]] scheme to perform a challenge-response protocol for lower cost. |
||
Still other cryptographic protocols attempt to achieve privacy against unauthorized readers, though these protocols are largely in the research stage. One major challenge in securing RFID tags is a shortage of computational resources within the tag. Standard cryptographic techniques require more resources than are available in most low cost RFID devices. [[RSA Security]] has patented a prototype device that locally jams RFID signals by interrupting a standard [[collision avoidance]] protocol, allowing the user to prevent identification if desired.<ref>{{cite web | url = http://www.rsasecurity.com/rsalabs/node.asp?id=2115 | title = RFID Privacy and Security | publisher = RSA Laboratories}}</ref> Various policy measures have also been proposed, such as marking RFID |
Still other cryptographic protocols attempt to achieve privacy against unauthorized readers, though these protocols are largely in the research stage. One major challenge in securing RFID tags is a shortage of computational resources within the tag. Standard cryptographic techniques require more resources than are available in most low cost RFID devices. [[RSA Security]] has patented a prototype device that locally jams RFID signals by interrupting a standard [[collision avoidance]] protocol, allowing the user to prevent identification if desired.<ref>{{cite web | url = http://www.rsasecurity.com/rsalabs/node.asp?id=2115 | title = RFID Privacy and Security | publisher = RSA Laboratories}}</ref> Various policy measures have also been proposed, such as marking RFID tagged objects with an industry standard label. |
||
=== Exploits === |
=== Exploits === |
||
[[Ars Technica]] Reported in March 2006 an RFID [[buffer overflow]] bug that could infect airport terminal RFID Databases for baggage, and also Passport databases to obtain confidential information on the passport holder.<ref>{{cite web|url=http://arstechnica.com/news.ars/post/20060315-6386.html|title=RFID chips can carry viruses|accessdate=2006-08-26|publisher=[[Ars Technica]]}}</ref> |
[[Ars Technica]] Reported in March 2006 an RFID [[buffer overflow]] bug that could infect airport terminal RFID Databases for baggage, and also Passport databases to obtain confidential information on the passport holder.<ref>{{cite web|url=http://arstechnica.com/news.ars/post/20060315-6386.html|title=RFID chips can carry viruses|accessdate=2006-08-26|publisher=[[Ars Technica]]}}</ref> |
||
=== Passports === |
=== Passports === |
||
In an effort to make passports more secure, several countries have implemented RFID in passports. However, the encryption on UK chips was broken in under 48 hours.<ref>{{cite web|url=http://blog.wired.com/sterling/2006/11/arphid_watch_fi.html|title=RFID Passports cracked. Easily, cheaply, and quickly|accessdate=2007-03-21|publisher=[[Wired (magazine)|wired]]}}</ref> Since that incident, further efforts have allowed researchers to clone passport data while the passport is being mailed to its owner. Where, previously, a criminal had to secretly open and then reseal the envelope, now it can be done without detection, adding some degree of insecurity to the passport system.<ref>{{cite web|url=http://www.theregister.com/2007/03/06/daily_mail_passport_clone/|title=RFID Passports cracked through the mail|accessdate=2007-03-21|publisher=[[the register]]}}</ref> |
|||
=== Protection against interception === |
|||
In an effort to make passports more secure, several countries have implemented RFID in passports. However, the encryption on UK chips was broken in under 48 hours.<ref>{{cite web|url=http://blog.wired.com/sterling/2006/11/arphid_watch_fi.html|title=RFID Passports cracked. Easily, cheaply, and quickly|accessdate=2007-03-21|publisher=[[Wired (magazine)|wired]]}}</ref> Since that incident, further efforts have allowed researchers to clone passport data while the passport is being mailed to its owner. Where a criminal used to need to secretly open and then reseal the envelope, now it can be done without detection, adding some degree of insecurity to the passport system.<ref>{{cite web|url=http://www.theregister.com/2007/03/06/daily_mail_passport_clone/|title=RFID Passports cracked through the mail|accessdate=2007-03-21|publisher=[[the register]]}}</ref> |
|||
Unencrypted tags can be read by any reader that is close enough. This may happen accidentally, but also as a preparation for various illegal activities, such as scanning shopping bags for expensive items. Various methods can be used to protect against RFID data interception:<ref>[[:de:Radio Frequency Identification#Potenzielle Angriffs- bzw. Schutzszenarien|Section translated from the German Wikipedia]]</ref> |
|||
* Most RFID chips can be disabled by physical means: for example the RFID chip inside RFID credit cards can be disabled by a sharp tap of a hammer.[http://www.wired.com/wired/archive/15.01/start.html?pg=9] |
|||
* An even simpler method, of use with passports for example, is wrapping the RFID-equipped item in aluminum foil.<ref>{{cite web | title = Can Aluminum Shield RFID Chips? | publisher = RFID Shield | url = http://www.rfid-shield.com/info_doesitwork.php}}</ref> (See [[#Shielding]] below about how aluminum foil may only make transmission more difficult and not completely block it.) |
|||
* One can prevent the RFID transponders from receiving power. This is accomplished by obstructing the power supply; one approach is to shield the RFID transponders in a [[Faraday cage]], intercepting the electromagnetic signal which normally powers them. UHF transponders can be shielded using an anti-static bag. LowFID and HighFID (inductively-coupled) transponders can be shielded with conventional aluminum foil.{{Fact|date=July 2008}} |
|||
* One can simply damage the antenna. With larger RFID transponders one can recognize the spirals of the antenna clearly by use of a [[radiograph]]. If one splits the antenna circuit, the effective range of the RFID transponder will be greatly reduced.{{Fact|date=July 2008}} |
|||
* An intense electromagnetic impulse applied to the transponders and antenna can induce high currents, interrupting the circuit and rendering the tag useless. A crude way to do this is putting the RFID tag in a [[microwave oven]]. Success may vary, depending on the frequency of the microwave and the shape of the antenna. A device built to destroy transponders is the [[RFID-Zapper]].{{Fact|date=July 2008}} |
|||
* The system can be blocked by sending a spurious signal in conjunction with the inquiry signal, preferably on the RFID frequency. This blocks the relatively weak signals of the RFID transponder.{{Fact|date=July 2008}} |
|||
* If a simple memory chip is used to confirm the authenticity of the inquiry, then one can record the inquiry and at a later time [[reverse engineer]] the signal, allowing replication. For the reader it appears as if the correct RFID transponder were in the field.{{Fact|date=July 2008}} |
|||
* Many RFID tags include a built-in 'kill' function. When provided with the correct pass-code, a tag can be either reprogrammed or told to 'self destruct', rendering it useless.{{Fact|date=July 2008}} |
|||
* Newer emerging RFID tags may include some sort of built in transfer-of-control and privacy enhancing technologies to ensure the owner can control and prevent linkage of RFID using silencing or non-linkable protocols.{{Fact|date=July 2008}} |
|||
=== Shielding === |
=== Shielding === |
||
A number of products are available on the market<ref>{{cite web | title = Products that shield RFID communication | publisher = Identity Stronghold | url = http://www.idstronghold.com/products.php?s=2}}</ref> that will allow a concerned carrier of RFID-enabled cards or passports to shield their data. In fact the United States government requires their new employee ID cards to be delivered with an approved shielding sleeve or holder.<ref>{{cite web | title = FIPS-201, Personal Identity Verification (PIV) of Federal Employees and Contractors | publisher = NIST | url = http://csrc.nist.gov/publications/fips/fips201-1/FIPS-201-1-chng1.pdf}}</ref> There are contradicting opinions as to whether aluminum can prevent reading of RFID chips. Some people claim that aluminum shielding, essentially creating a [[Faraday cage]], does work.<ref>{{cite web | title = Can Aluminum Shield RFID Chips? | publisher = RFID Shield | url = http://www.rfid-shield.com/info_doesitwork.php}}</ref> Others claim that simply wrapping an RFID card in aluminum foil, only makes transmission more difficult, yet is not completely effective at preventing it.<ref>{{cite web | title = Aluminum Foil Does Not Stop RFID | publisher = Omniscience is Bliss | url = http://www.omniscienceisbliss.org/rfid.html}}</ref> |
|||
Shielding is again a function of the frequency being used. [[Low frequency|Low-frequency]] LowFID tags, like those used in implantable devices for humans and pets, are relatively resistant to shielding, though thick metal foil will prevent most reads. [[High frequency]] HighFID tags (13.56 MHz — smart cards and access badges) are very sensitive to shielding and are difficult to read when within a few centimetres of a metal surface. [[Ultra high frequency|UHF]] Ultra-HighFID tags (pallets and cartons) are very difficult to read when placed within a few millimetres of a metal surface, although their read range is actually increased when they are spaced 2–4 cm from a metal due to positive reinforcement of the reflected wave and the [[incident wave]] at the tag. UHFID tags can be successfully shielded from most reads by being placed within an anti-static [[plastic bag]]. |
|||
A number of products are available on the market that will allow a concerned carrier of RFID-enabled cards or passports to shield their data. In fact the United States government requires their new employee ID cards to be delivered with an approved shielding sleeve or holder.<ref>{{cite web | title = FIPS-201, Personal Identity Verification (PIV) of Federal Employees and Contractors | publisher = NIST | url = http://csrc.nist.gov/publications/fips/fips201-1/FIPS-201-1-chng1.pdf}}</ref> There are contradicting opinions as to whether aluminum can prevent reading of RFID chips. Some people claim that aluminum shielding, essentially creating a [[Faraday cage]], does work.<ref>{{cite web | title = Can Aluminum Shield RFID Chips? | publisher = RFID Shield | url = http://www.rfid-shield.com/info_doesitwork.php}}</ref> Others claim that simply wrapping an RFID card in aluminum foil, only makes transmission more difficult, yet is not completely effective at preventing it.<ref>{{cite web | title = Aluminum Foil Does Not Stop RFID | publisher = Omniscience is Bliss | url = http://www.omniscienceisbliss.org/rfid.html}}</ref> |
|||
Shielding is again a function of the frequency being used. [[Low frequency|Low-frequency]] LowFID tags, like those used in implantable devices for humans and pets, are relatively resistant to shielding, though thick metal foil will prevent most reads. [[High frequency]] HighFID tags (13.56 MHz — smart cards and access badges) are sensitive to shielding and are difficult to read when within a few centimetres of a metal surface. [[Ultra high frequency|UHF]] Ultra-HighFID tags (pallets and cartons) are difficult to read when placed within a few millimetres of a metal surface, although their read range is actually increased when they are spaced 2–4 cm from a metal due to positive reinforcement of the reflected wave and the [[incident wave]] at the tag. UHFID tags can be successfully shielded from most reads by being placed within an anti-static [[plastic bag]].{{Fact|date=August 2008}} |
|||
== Controversies == |
== Controversies == |
||
[[Image:Stoprfid-logo.jpg|thumb|Logo of the anti-RFID campaign by German privacy group FoeBuD.]] |
[[Image:Stoprfid-logo.jpg|thumb|Logo of the anti-RFID campaign by German privacy group FoeBuD.]] |
||
=== Privacy === |
=== Privacy === |
||
''How would you like it if, for instance, one day you realized your underwear was reporting on your whereabouts?'' |
|||
— California State Senator [[Debra Bowen]], at a 2003 hearing.<ref>{{cite news | title = Privacy advocates call for RFID regulation | publisher = [[News.com]] | author = Alorie Gilbert | date = 18 Aug 2003}}</ref> |
|||
The use of RFID technology has engendered considerable controversy and even product [[boycott]]s by consumer privacy advocates. [[Katherine Albrecht]] and [[Liz McIntyre]] |
The use of RFID technology has engendered considerable controversy and even product [[boycott]]s by consumer privacy advocates. [[Katherine Albrecht]] and [[Liz McIntyre]] are two prominent Christian critics of the technology who refer to RFID tags as "[[spychips]]". The two main [[privacy]] concerns regarding RFID are: |
||
* Since the owner of an item will not necessarily be aware of the presence of an RFID tag and the tag can be read at a distance without the knowledge of the individual, it becomes possible to gather sensitive data about an individual without consent. |
* Since the owner of an item will not necessarily be aware of the presence of an RFID tag and the tag can be read at a distance without the knowledge of the individual, it becomes possible to gather sensitive data about an individual without consent. |
||
* If a tagged item is paid for by credit card or in conjunction with use of a [[loyalty card]], then it would be possible to indirectly deduce the identity of the purchaser by reading the globally unique ID of that item (contained in the RFID tag). |
* If a tagged item is paid for by credit card or in conjunction with use of a [[loyalty card]], then it would be possible to indirectly deduce the identity of the purchaser by reading the globally unique ID of that item (contained in the RFID tag). |
||
| Line 471: | Line 420: | ||
=== Human implantation === |
=== Human implantation === |
||
The [[Food and Drug Administration]] in the US has approved the use of RFID chips in humans.<ref>{{cite web | author=Greene, Thomas C. | year=2004| title=Feds approve human RFID implants | url=http://www.theregister.co.uk/2004/10/14/human_rfid_implants/ | accessdate=2007-03-01}}</ref> |
The [[Food and Drug Administration]] in the US has approved the use of RFID chips in humans.<ref>{{cite web | author=Greene, Thomas C. | year=2004| title=Feds approve human RFID implants | url=http://www.theregister.co.uk/2004/10/14/human_rfid_implants/ | accessdate=2007-03-01}}</ref> |
||
Some business establishments have also started to ''chip'' customers, such as the ''Baja Beach'' nightclub in [[Barcelona]]. |
Some business establishments have also started to ''chip'' customers, such as the ''Baja Beach'' nightclub in [[Barcelona]]. This has provoked concerns into privacy of individuals as they can potentially be tracked wherever they go by an identifier unique to them. There are concerns this could lead to abuse by an authoritarian government or lead to removal of freedoms.<ref>Monahan, Torin and Tyler Wall. 2007. Somatic Surveillance: Corporeal Control through Information Networks. Surveillance & Society 4 (3): 154-173.[http://www.surveillance-and-society.org/articles4(3)/somatic.pdf]</ref> |
||
On [[July 22]], [[2006]], Reuters reported that two hackers, Newitz and Westhues, at a conference in New York City showed that they could clone the RFID signal from a human implanted RFID chip, showing that the chip is not hack-proof as was previously believed.<ref>[http://blogs.reuters.com/2006/07/22/high-tech-cloning/ Reuters]</ref> |
On [[July 22]], [[2006]], Reuters reported that two hackers, Newitz and Westhues, at a conference in New York City showed that they could clone the RFID signal from a human implanted RFID chip, showing that the chip is not hack-proof as was previously believed.<ref>[http://blogs.reuters.com/2006/07/22/high-tech-cloning/ Reuters]</ref> |
||
=== RFID implant as the mark of the beast === |
=== RFID implant as the mark of the beast === |
||
A few critics, mostly conservative Evangelical [[Christians]], believe that RFID tagging could represent the [[mark of the beast]], which Revelation 13:16-17 says will be placed by the Antichrist in the right hands or foreheads of humans and necessary for commerce. |
|||
{{cquote|1=And he causeth all, both small and great, rich and poor, free and bond, to receive a mark in their right hand, or in their foreheads: |
|||
{{details3|[[eschatology]], [[dispensationalism]]}} |
|||
And that no man might buy or sell, save he that had the mark, or the name of the beast, or the number of his name.|4=Revelation 13:16-17}} |
|||
[[Katherine Albrecht]] and [[Liz McIntyre]], authors of ''Spychips: How Major Corporations and Government Plan to Track Your Every Move with RFID'', wrote a new book on the subject.<ref> Albrecht & McIntyre (2006). ''The Spychips Threat: Why Christians Should Resist RFID and Electronic Surveillance'', Tennessee: Nelson Current ISBN 1595550216 </ref> John Conner, leader of an organization called "The Resistance of Christ" also believes there is a strong connection. Related subjects include [[eschatology]] (last things) and [[dispensationalism]].<ref>{{cite web | author=Gilbert, Alorie| year=2006| title=is RFID the mark of the beast? | work=News.com| url=http://news.com.com/2061-10786_3-5579795.html | accessdate=2006-12-18}}</ref><ref>{{cite web | author=Brown, Jim| year=2005| title=Group Fears RFID Chips Could Herald 'Mark of the Beast' | work=Agape Press| url=http://headlines.agapepress.org/archive/3/292005f.asp | accessdate=2006-12-18}}</ref><ref>{{cite web | author=Baard, Mark| year=2006| title=RFID: Sign of the (End) Times? | work=Wired.com| url=http://www.wired.com/news/culture/0,70308-0.html | accessdate=2006-12-18}}</ref> Rev. Irvin Baxter Jr's Website www.endtime.com provides an in depth video analysis on the topic titled "mark of the beast." |
|||
{{cquote|1=He forced everyone, small and great, rich and poor, free and slave, to receive a mark on his right hand or on his forehead, |
|||
so that no man could buy or sell unless he had the mark, which is the name of the beast or the number of his name.|4=Revelation 13:16-17}} |
|||
[[Mark Dice| John Conner]], leader of an organization called [[The Resistance of Christ]] also believes there is a strong connection. |
|||
[[Katherine Albrecht]] and [[Liz McIntyre]], have authored books about this topic: |
|||
* ''Spychips: How Major Corporations and Government Plan to Track Your Every Move with RFID'' |
|||
* ''The Spychips Threat: Why Christians Should Resist RFID and Electronic Surveillance'' |
|||
Related subjects include [[eschatology]] (theology and philosophy concerned with the final events in the history of the world) and [[dispensationalism]] (which sees the past, present, and future as a number of successive administrations).<ref>{{cite web | author=Gilbert, Alorie| year=2006| title=is RFID the mark of the beast? | work=News.com| url=http://news.com.com/2061-10786_3-5579795.html | accessdate=2006-12-18}}</ref><ref>{{cite web | author=Brown, Jim| year=2005| title=Group Fears RFID Chips Could Herald 'Mark of the Beast' | work=Agape Press| url=http://headlines.agapepress.org/archive/3/292005f.asp | accessdate=2006-12-18}}</ref><ref>{{cite web | author=Baard, Mark| year=2006| title=RFID: Sign of the (End) Times? | work=Wired.com| url=http://www.wired.com/news/culture/0,70308-0.html | accessdate=2006-12-18}}</ref> |
|||
Rev. Irvin Baxter Jr's [http://www.endtime.com Website] provides his views in a video analysis on the topic titled "Mark of the Beast." |
|||
==See also== |
==See also== |
||
*[[Biometrics]] |
*[[Biometrics]] |
||
*[[Barcode]] |
*[[Barcode]] |
||
| Line 505: | Line 441: | ||
*[[Local Positioning Systems]] |
*[[Local Positioning Systems]] |
||
*[[High Capacity Color Barcode]] |
*[[High Capacity Color Barcode]] |
||
*[[Item-Attendant ICT]] |
|||
*[[Mass surveillance]] |
*[[Mass surveillance]] |
||
*[[Microchip implant (human)]] |
*[[Microchip implant (human)]] |
||
| Line 511: | Line 448: | ||
*[[Near Field Communication]] |
*[[Near Field Communication]] |
||
*[[Pharmacy informatics]] |
*[[Pharmacy informatics]] |
||
*[[Polymer electrolyte]] |
|||
*[[Proximity card]] |
*[[Proximity card]] |
||
*[[Identification friend or foe]] |
|||
*[[Real-time locating]] |
*[[Real-time locating]] |
||
*[[Smart cards]] |
*[[Smart cards]] |
||
*[[Supranet]] |
*[[Supranet]] |
||
*[[Tracking system]] |
*[[Tracking system]] |
||
*[[AS5678]] |
|||
== References == |
|||
== References == |
|||
{{reflist|2}} |
{{reflist|2}} |
||
== External links == |
== External links == |
||
{{commonscat|RFID}} |
{{commonscat|RFID}} |
||
* [http://www.rfidjournal.com RFID Journal] |
* [http://www.rfidjournal.com RFID Journal] |
||
* [http://www.rfid-model-project.blogspot.com RFID graduation project] |
|||
* {{HSW|rfid|How RFID Works}} |
* {{HSW|rfid|How RFID Works}} |
||
* [http://www.gs1.org/productssolutions/epcglobal/ EPCglobal] — standards for EPC |
* [http://www.gs1.org/productssolutions/epcglobal/ EPCglobal] — standards for EPC |
||
* |
* [http://www.dmoz.org/Society/Issues/Science_and_Technology/RFID/ dmoz Open Directory of RFID] — Human-edited RFID |
||
* |
*[http://www.rfid.gen.tr Rfid] - RFID Open Source RFID forums |
||
<!--===========================({{NoMoreLinks}})=============================== |
<!--===========================({{NoMoreLinks}})=============================== |
||
| PLEASE BE CAUTIOUS IN ADDING MORE LINKS TO THIS ARTICLE. WIKIPEDIA IS | |
| PLEASE BE CAUTIOUS IN ADDING MORE LINKS TO THIS ARTICLE. WIKIPEDIA IS | |
||
| Line 550: | Line 483: | ||
[[Category:Radio-frequency identification]] |
[[Category:Radio-frequency identification]] |
||
[[Category:Privacy]] |
[[Category:Privacy]] |
||
[[Category:Wireless]] |
|||
[[ar:التعرف بترددات الراديو]] |
[[ar:التعرف بترددات الراديو]] |
||
| Line 576: | Line 508: | ||
[[pl:RFID]] |
[[pl:RFID]] |
||
[[pt:RFID]] |
[[pt:RFID]] |
||
[[ro:RFID]] |
|||
[[ru:RFID]] |
[[ru:RFID]] |
||
[[sk:Vysokofrekvenčná identifikácia]] |
[[sk:Vysokofrekvenčná identifikácia]] |
||
Revision as of 10:51, 30 November 2008
This article needs additional citations for verification. (February 2008) |

Radio-frequency identification (RFID) is an automatic identification method, relying on storing and remotely retrieving data using devices called RFID tags or transponders.
An RFID tag is an object that can be applied to or incorporated into a product, animal, or person for the purpose of identification using radio waves. Some tags can be read from several meters away and beyond the line of sight of the reader.
Most RFID tags contain at least two parts. One is an integrated circuit for storing and processing information, modulating and demodulating a (RF) signal, and other specialized functions. The second is an antenna for receiving and transmitting the signal. Chipless RFID allows for discrete identification of tags without an integrated circuit, thereby allowing tags to be printed directly onto assets at a lower cost than traditional tags.
Today, RFID used is in enterprise supply chain management to improve the efficiency of inventory tracking and management. However, growth and adoption in the enterprise supply chain market is limited because current commercial technology does not link the indoor tracking to the overall end-to-end supply chain visibility. Coupled with fair cost-sharing mechanisms, rational motives and justified returns from RFID technology investments are the key ingredients to achieve long-term and sustainable RFID technology adoption [1].
History of RFID tags

In 1946 Léon Theremin invented an espionage tool for the Soviet Union which retransmitted incident radio waves with audio information. Sound waves vibrated a diaphragm which slightly altered the shape of the resonator, which modulated the reflected radio frequency. Even though this device was a passive covert listening device, not an identification tag, it has been attributed as a predecessor to RFID technology. The technology used in RFID has been around since the early 1920s according to one source (although the same source states that RFID systems have been around just since the late 1960s).[2][3][4][5]
Similar technology, such as the IFF transponder invented by the United Kingdom in 1939, was routinely used by the allies in World War II to identify aircraft as friend or foe. Transponders are still used by military and commercial aircraft to this day.
Another early work exploring RFID is the landmark 1948 paper by Harry Stockman, titled "Communication by Means of Reflected Power" (Proceedings of the IRE, pp 1196–1204, October 1948). Stockman predicted that "…considerable research and development work has to be done before the remaining basic problems in reflected-power communication are solved, and before the field of useful applications is explored."
Mario Cardullo's U.S. patent 3,713,148 in 1973 was the first true ancestor of modern RFID; a passive radio transponder with memory. The initial device was passive, powered by the interrogating signal, and was demonstrated in 1971 to the New York Port Authority and other potential users and consisted of a transponder with 16 bit memory for use as a toll device. The basic Cardullo patent covers the use of RF, sound and light as transmission media. The original business plan presented to investors in 1969 showed uses in transportation (automotive vehicle identification, automatic toll system, electronic license plate, electronic manifest, vehicle routing, vehicle performance monitoring), banking (electronic check book, electronic credit card), security (personnel identification, automatic gates, surveillance) and medical (identification, patient history).
A very early demonstration
A very early demonstration of reflected power (modulated backscatter) RFID tags, both passive and semi-passive, was done by Steven Depp, Alfred Koelle and Robert Freyman at the Los Alamos Scientific Laboratory in 1973[3]. The portable system operated at 915 MHz and used 12 bit tags. This technique is used by the majority of today's UHFID and microwave RFID tags.
The first patent to be associated with the abbreviation RFID was granted to Charles Walton in 1983 U.S. patent 4,384,288.
RFID tags
RFID tags come in three general varieties:- passive, active, or semi-passive (also known as battery-assisted). Passive tags require no internal power source, thus being pure passive devices (they are only active when a reader is nearby to power them), whereas semi-passive and active tags require a power source, usually a small battery.
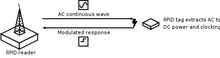
To communicate, tags respond to queries generating signals that must not create interference with the readers, as arriving signals can be very weak and must be differentiated. Besides backscattering, load modulation techniques can be used to manipulate the reader's field. Typically, backscatter is used in the far field, whereas load modulation applies in the nearfield, within a few wavelengths from the reader.
Passive
Passive RFID tags have no internal power supply. The minute electrical current induced in the antenna by the incoming radio frequency signal provides just enough power for the CMOS integrated circuit in the tag to power up and transmit a response. Most passive tags signal by backscattering the carrier wave from the reader. This means that the antenna has to be designed both to collect power from the incoming signal and also to transmit the outbound backscatter signal. The response of a passive RFID tag is not necessarily just an ID number; the tag chip can contain non-volatile, possibly writable EEPROM for storing data.
Passive tags have practical read distances ranging from about 10 cm (4 in.) (ISO 14443) up to a few meters (Electronic Product Code (EPC) and ISO 18000-6), depending on the chosen radio frequency and antenna design/size. Due to their simplicity in design they are also suitable for manufacture with a printing process for the antennas. The lack of an onboard power supply means that the device can be quite small: commercially available products exist that can be embedded in a sticker, or under the skin in the case of low frequency (LowFID) RFID tags.
In 2007, the Danish Company RFIDsec developed a passive RFID with privacy enhancing technologies built-in including built-in firewall access controls, communication encryption and a silent mode ensuring that the consumer at point of sales can get exclusive control of the key to control the RFID. The RFID will not respond unless the consumer authorizes it, the consumer can validate presence of a specific RFID without leaking identifiers and therefore the consumer can make use of the RFID without being trackable or otherwise leak information that represents a threat to consumer privacy.
In 2006, Hitachi, Ltd. developed a passive device called the µ-Chip measuring 0.15×0.15 mm (not including the antenna), and thinner than a sheet of paper (7.5 micrometers).[6][7] Silicon-on-Insulator (SOI) technology is used to achieve this level of integration. The Hitachi µ-Chip can wirelessly transmit a 128-bit unique ID number which is hard coded into the chip as part of the manufacturing process. The unique ID in the chip cannot be altered, providing a high level of authenticity to the chip and ultimately to the items the chip may be permanently attached or embedded into. The Hitachi µ-Chip has a typical maximum read range of 30 cm (1 ft). In February 2007 Hitachi unveiled an even smaller RFID device measuring 0.05×0.05 mm, and thin enough to be embedded in a sheet of paper.[8] The new chips can store as much data as the older µ-chips, and the data contained on them can be extracted from as far away as a few hundred metres. The ongoing problems with all RFIDs is that they need an external antenna which is 80 times bigger than the chip in the best version thus far developed. Further, the present costs of manufacturing the inlays for tags has inhibited broader adoption. As silicon prices are reduced and new more economic methods for manufacturing inlays and tags are perfected in the industry, broader adoption and item level tagging along with economies of scale production scenarios; it is expected to make RFID both innocuous and commonplace much like Barcodes are presently.
Alien Technology's Fluidic Self Assembly and HiSam machines, Smartcode's Flexible Area Synchronized Transfer (FAST) and Symbol Technologies' PICA process are alleged to potentially further reduce tag costs by massively parallel production[citation needed]. Alien Technology and SmartCode are currently using the processes to manufacture tags while Symbol Technologies' PICA process is still in the development phase. Symbol was acquired by Motorola in 2006. Motorola however has since made agreements with Avery Dennison for supply of tags, meaning their own Tag production and PICA process may have been abandoned.[9] Alternative methods of production such as FAST, FSA, HiSam and possibly PICA could potentially reduce tag costs dramatically, and due to volume capacities achievable, in turn be able to also drive the economies of scale models for various Silicon fabricators as well. Some passive RFID vendors believe that Industry benchmarks for tag costs can be achieved eventually as new low cost volume production systems are implemented more broadly. (For example, see [4])
Non-silicon tags made from polymer semiconductors are currently being developed by several companies globally. Simple laboratory printed polymer tags operating at 13.56 MHz were demonstrated in 2005 by both PolyIC (Germany) and Philips (The Netherlands). If successfully commercialized, polymer tags will be roll-printable, like a magazine, and much less expensive than silicon-based tags. The end game for most item-level tagging over the next few decades may be that RFID tags will be wholly printed – the same way that a barcode is today – and be virtually free, like a barcode. However, substantial technical and economic hurdles must be surmounted to accomplish such an end: hundreds of billions of dollars have been invested over the last three decades in silicon processing, resulting in a per-feature cost which is actually less than that of conventional printing.
Active
Unlike passive RFID tags, active RFID tags have their own internal power source, which is used to power the integrated circuits and to broadcast the response signal to the reader. Communications from active tags to readers is typically much more reliable (i.e. fewer errors) than from passive tags due to the ability for active tags to conduct a "session" with a reader.
Active tags, due to their on board power supply, also may transmit at higher power levels than passive tags, allowing them to be more robust in "RF challenged" environment with humidity and spray or with dampening targets (including humans/cattle, which contain mostly water), reflective targets from metal (shipping containers, vehicles), or at longer distances: Generating strong responses from weak reception is a sound approach to success. In turn, active tags are generally bigger, caused by battery volume, and more expensive to manufacture, caused by battery price. However, their potential shelf life is comparable, as self discharge of batteries competes with corrosion of aluminated printed circuits.
Many active tags today have operational ranges of hundreds of meters, and a battery life of up to 10 years. Active tags may include larger memories than passive tags, and may include the ability to store additional information received from the reader.
Special active RFID tags may include specialized sensors. For example, a temperature sensor can be used to record the temperature profile during the transportation and storage of perishable goods. Other sensor types used include humidity, shock/vibration, light, nuclear radiation, pressure and concentrations of gases like ethylene.
The United States Department of Defense (DoD) has successfully used active tags to reduce search and loss in logistics and improve supply chain visibility for more than 15 years (concept of in-transit-visibility ITV, [5]).
Semi-passive
Semi-passive tags are similar to active tags in that they have their own power source, but the battery only powers the microchip and does not power the broadcasting of a signal. The response is usually powered by means of backscattering the RF energy from the reader, where energy is reflected back to the reader as with passive tags. An additional application for the battery is to power data storage.
If energy from the reader is collected and stored to emit a response in the future, the tag is operating active
Whereas in passive tags the power level to power up the circuitry must be 100 times stronger than with active or semi-active tags, also the time consumption for collecting the energy is omitted and the response comes with shorter latency time. The battery-assisted reception circuitry of semi-passive tags leads to greater sensitivity than passive tags, typically 100 times more. The enhanced sensitivity can be leveraged as increased range (by one magnitude) and/or as enhanced read reliability (by reducing bit error rate at least one magnitude).
The enhanced sensitivity of semi-passive tags place higher demands on the reader concerning separation in more dense population of tags. Because an already weak signal is backscattered to the reader from a larger number of tags and from longer distances, the separation requires more sophisticated anti-collision concepts, better signal processing and some more intelligent assessment which tag might be where. For passive tags, the reader-to-tag link usually fails first. For semi-passive tags, the reverse (tag-to-reader) link usually collides first.
Semi-passive tags have three main advantages 1) Greater sensitivity than passive tags 2) Longer battery powered life cycle than active tags. 3) Can perform active functions (such as temperature logging) under its own power, even when no reader is present for powering the circuitry.
Extended capability
Extended capability RFID defines a category of RFID that goes beyond the basic capabilities of standard RFID as merely a “license plate” or bar-code replacement technology. Key attributes of extended capability RFID include, but are not limited to, the ability to read at longer distances and around challenging environments, to store large amounts of data on the tag, to integrate with sensors, and to communicate with external devices.
Examples of extended capability RFID tag technologies include EPC C1G2 with extended memory (e.g. 64Kb), battery-assisted passive, and active RFID. Battery-assisted passive, also known as semi-passive or semi-active, has the ability to extend the read range of standard passive technologies to well over 50 meters, to read around challenging materials such as metal, to withstand outdoor environments, to store an on-tag database, to be able to capture sensor data, and to act as a communications mechanism for external devices. Also, battery-assisted passive only transmits a signal when interrogated, thus extending battery life. Active RFID, which can have some of the features of battery-assisted passive, is commonly used for even longer distances and real-time locationing. It also actively transmits a signal, which often results in shorter battery life.
Common applications of extended capability RFID include Yard Management, Parts Maintenance and Repair Operations, Cold-Chain Management, Reusable Transport Items tracking, High Value/High Security Asset tracking, and other applications where extended capabilities are needed.
Antenna types
The antenna used for an RFID tag is affected by the intended application and the frequency of operation. Low-frequency is (30 kHz – 300 kHz). LFID or LowFID passive tags are normally inductively coupled, and because the voltage induced is proportional to frequency, many coil turns are needed to produce enough voltage to operate an integrated circuit. Compact LowFID tags, like glass-encapsulated tags used in animal and human identification, use a multilayer coil (3 layers of 100–150 turns each) wrapped around a ferrite core.
High frequency is (3 MHz - 30 MHz). At 13.56 MHz, a HFID or HighFID tag, using a planar spiral with 5–7 turns over a credit-card-sized form factor can be used to provide ranges of tens of centimeters. These coils are less costly to produce than LF coils, since they can be made using lithographic techniques rather than by wire winding, but two metal layers and an insulator layer are needed to allow for the crossover connection from the outermost layer to the inside of the spiral where the integrated circuit and resonance capacitor are located.
Ultra-high frequency or UHF is (300 MHz - 3 GHz). UHFID/Ultra-HighFID and microwave passive tags are usually radiatively-coupled to the reader antenna and can employ conventional dipole-like antennas. Only one metal layer is required, reducing cost of manufacturing. Dipole antennas, however, are a poor match to the high and slightly capacitive input impedance of a typical integrated circuit. Folded dipoles, or short loops acting as inductive matching structures, are often employed to improve power delivery to the IC. Half-wave dipoles (16 cm at 900 MHz) are too big for many applications; for example, tags embedded in labels must be less than 10 cm (4 inches) in extent. To reduce the length of the antenna, antennas can be bent or meandered, and capacitive tip-loading or bowtie-like broadband structures are also used. Compact antennas usually have gain less than that of a dipole — that is, less than 2 dBi — and can be regarded as isotropic in the plane perpendicular to their axis.
Dipoles couple to radiation polarized along their axes, so the visibility of a tag with a simple dipole-like antenna is orientation-dependent. Tags with two orthogonal or nearly-orthogonal antennas, often known as dual-dipole tags, are much less dependent on orientation and polarization of the reader antenna, but are larger and more expensive than single-dipole tags.
Patch antennas are used to provide service in close proximity to metal surfaces, but a structure with good bandwidth is 3–6 mm thick, and the need to provide a ground layer and ground connection increases cost relative to simpler single-layer structures.
HighFID and UHFID tag antennas are usually fabricated from copper or aluminum. Conductive inks have seen some use in tag antennas but have encountered problems with IC adhesion and environmental stability.
Tag attachment
There are three different kinds of RFID tags based on their attachment with identified objects, i.e. attachable, implantable and insertion tags [10]. In addition to these conventional RFID tags, Eastman Kodak Company has filed two patent applications for monitoring ingestion of medicine based on a digestible RFID tag[11].
Tagging positions
RFID tagging positions can influence the performance of air interface UHFID passive tags and related to the position where RFID tags are embedded, attached, injected or digested.
In many cases, optimum power from RFID reader is not required to operate passive tags. However, in cases where the Effective Radiated Power (ERP) level and distance between reader and tags are fixed, such as in manufacturing setting, it is important to know the location in a tagged object where a passive tag can operate optimally.
R-Spot or Resonance Spot, L-Spot or Live Spot and D-Spot or Dead Spot are defined to specify the location of RFID tags in a tagged object, where the tags can still receive power from a reader within specified ERP level and distance [12].
Tag environments
The proposed ubiquity of RFID tags means that readers may need to select which tags to read among many potential candidates, or may wish to probe surrounding devices to perform inventory checks or, in case the tags are associated to sensors and capable of keeping their values, question them for environmental conditions. If a reader intends to work with a collection of tags, it needs to either discover all devices within an area to iterate over them afterwards, or use collision avoidance protocols.

To read tag data, readers use a tree-walking singulation algorithm, resolving possible collisions and processing responses one by one. Blocker tags may be used to prevent readers from accessing tags within an area without killing surrounding tags by means of suicide commands. These tags masquerade as valid tags but have some special properties: in particular, they may possess any identification code, and may deterministically respond to all reader queries, thus rendering them useless and securing the environment.
Besides this, tags may be promiscuous, attending all requests alike, or secure, which requires authentication and control of typical password management and secure key distribution issues. A tag may as well be prepared to be activated or deactivated in response to specific reader commands.
Readers that are in charge of the tags of an area may operate in autonomous mode (as opposed to interactive mode). When in this mode, a reader periodically locates all tags in its operating range, and keeps a presence list with a persist time and some control information. When an entry expires, it is removed from the list.
Frequently, a distributed application requires both types of tags: passive tags are incapable of continuous monitoring and perform tasks on demand when accessed by readers. They are useful when activities are regular and well defined, and requirements for data storage and security are limited; when accesses are frequent, continuous or unpredictable, there are time constraints to meet or data processing (internal searches, for instance) to perform, active tags may be preferred.
Current uses
This article needs additional citations for verification. (August 2007) |
RFID is becoming increasingly prevalent as the price of the technology decreases. In January 2003 Gillette announced in that it ordered 500 million tags from Alien Technology. Gillette VP Dick Cantwell says the company paid "well under ten cents" for each tag. The Japanese HIBIKI initiative aims to reduce the price to 5 Yen (4 eurocent).
Passports
RFID tags are being used in passports issued by many countries, such as include Malaysia (early 2000), New Zealand (November 4, 2005), Belgium, The Netherlands (2005), Norway (November 2005)[13], Ireland (2006), Japan (March 1, 2006), Pakistan, Germany, Portugal, Poland (2006), The United Kingdom, and the United States (2007).
Standards for RFID passports are determined by the International Civil Aviation Organization (ICAO), and are contained in ICAO Document 9303, Part 1, Volumes 1 and 2 (6th edition, 2006). ICAO refers to the ISO 14443 RFID chips in e-passports as "contactless integrated circuits". ICAO standards provide for e-passports to be identifiable by a standard e-passport logo on the front cover.
The first RFID passports ("E-passport") were issued by Malaysia in 1998. In addition to information also contained on the visual data page of the passport, Malaysian e-passports record the travel history (time, date, and place) of entries and exits from the country.
In 2006, RFID tags were included in new US passports. The US produced 10 million passports in 2005, and it has been estimated that 13 million will be produced in 2006. The chips will store the same information that is printed within the passport and will also include a digital picture of the owner. The US State Department initially stated the chips could only be read from a distance of 10 cm (4 in), but after widespread criticism and a clear demonstration that special equipment can read the test passports from 10 meters (33 ft) away, the passports were designed to incorporate a thin metal lining to make it more difficult for unauthorized readers to "skim" information when the passport is closed. The department will also implement Basic Access Control (BAC), which functions as a Personal Identification Number (PIN) in the form of characters printed on the passport data page. Before a passport's tag can be read, this PIN must be entered into an RFID reader. The BAC also enables the encryption of any communication between the chip and interrogator [14]. Despite this precaution, the Center for Democracy and Technology has issued warnings that significant security weaknesses that could be used to track U.S. travelers are apparent in the specifications of the card design as outlined by the U.S. Department of State.[15]
Security expert Bruce Schneier has suggested that a mugger operating near an airport could target victims who have arrived from wealthy countries, or a terrorist could design an improvised explosive device which functioned when approached by persons from a particular country.
Some other European Union countries are also planning to add fingerprints and other biometric data, while some have already done so.[citation needed]
Transportation payments


- Throughout Europe, and in particular in Paris (system started in 1995 by the RATP), Lyon, Bordeaux and Marseille in France, Porto and Lisbon in Portugal, Milan, Turin, and Florence in Italy, and Brussels in Belgium, RFID passes conforming to the Calypso (RFID) international standard are used for public transport systems. They are also used now in Canada (Montreal), Mexico, Israel, Bogotá and Pereira in Colombia, Stavanger in Norway, etc.
- In Toronto, Ontario, Canada and surrounding areas, Electronic Road Pricing systems are used to collect toll payments on Highway 407.
- In Seoul, South Korea and surrounding cities, T-money cards can be used to pay for public transit. Some other South Korean cities have adopted the system, which can also be used in some stores as cash. T-money replaced Upass, first introduced for transport payments in 1996 using MIFARE technology.
- In Turkey, RFID has been used in the motorways and bridges as a payment system over ten years. Also the new electronic bus tickets in Istanbul
- In Hong Kong, mass transit is paid for almost exclusively through the use of an RFID technology, called the Octopus Card. Originally it was launched in September 1997 exclusively for transit fare collection, but has grown to be similar to a cash card, and can still be used in vending machines, fast-food restaurants and supermarkets. The card can be recharged with cash at add-value machines or in shops, and can be read several centimetres from the reader. The same applies for Delhi Metro, the rapid transit system in New Delhi, capital city of India.
- The Moscow Metro, the world's second busiest, was the first system in Europe to introduce RFID smartcards in 1998.
- The Washington, D.C. Metrorail became the first U.S. urban mass-transit system to use RFID technology when it introduced the SmarTrip card in 1999.
- JR East in Japan introduced SUICa (Super Urban Intelligent Card) for transport payment service in its railway transportation service in November 2001, using Sony's FeliCa (Felicity Card) technology. The same Sony technology was used in Hong Kong's Octopus card, and Singapore's EZ-Link card.
- In Singapore, public transportation buses and trains employ passive RFID cards known as EZ-Link cards. Traffic into crowded downtown areas is regulated by variable tolls imposed using an active tagging system combined with the use of stored-value cards (known as CashCards).
- RFID is used in Malaysia Expressways payment system. The name for the system is Touch 'n Go. Due to the name and design, one must touch the card for usage.
- Since 2002, in Taipei, Taiwan the transportation system uses RFID operated cards as fare collection. The Easy Card is charged at local convenience stores and metro stations, and can be used in Metro, buses and parking lots. The uses are planned to extend all throughout the island of Taiwan in the future.
- In the USA, The Chicago Transit Authority has offered the Chicago Card and the Chicago Card Plus for rail payments across the entire system since 2002 and for bus payments since 2005. The New York City Subway is conducting a trial during 2006, utilizing PayPass by MasterCard as fare payment. The Massachusetts Bay Transportation Authority introduced the use of a CharlieCard RFID as a fare payment system which is cheaper than its paper or cash equivalent. Six transit agencies in the King County region of Washington State are collaborating to introduce the Smart Card, or Orca Card.
- In the UK, op systems for prepaying for unlimited public transport have been devised, making use of RFID technology. The design is embedded in a creditcard-like pass, that when scanned reveals details of whether the pass is valid, and for how long the pass will remain valid. The first company to implement this is the NCT company of Nottingham City, where the general public affectionately refer to them as "beep cards". It has since then been implemented with great success in London, where "Oyster cards" allow for pay-as-you-go travel as well as passes valid for various lengths of time and in various areas.
- In Oslo, Norway, the upcoming public transport payment is to be entirely RFID-based. The system is to be put into production around spring 2007
- RFID tags are used for electronic toll collection at toll booths with Georgia's Cruise Card, California's FasTrak, Colorado's E-470, Illinois' I-Pass, Oklahoma's Pikepass, the expanding eastern states' E-ZPass system (including Massachusetts's Fast Lane,Delaware, New Hampshire Turnpike, Maryland, New Jersey Turnpike, West Virginia Turnpike, New York's Thruway system, Virginia, and the Maine Turnpike), Florida's SunPass, Various systems in Texas including D/FW's NTTA TollTag, the Austin metro TxTag and Houston HCTRA EZ Tag (which as of early 2007 are all valid on any Texas toll road), Kansas's K-Tag, The "Cross-Israel Highway" (Highway 6), Philippines South Luzon Expressway E-Pass, Brisbane's Queensland Motorway E-Toll System in Australia, Autopista del Sol (Sun's Highway), Autopista Central (Central Highway), Autopista Los Libertadores, Costanera Norte, Vespucio Norte Express and Vespucio Sur urban Highways and every forthcoming urban highway (in a "Free Flow" modality) concessioned to private investors in Chile, all toll tunnels in Hong Kong (Autotoll) and all highways in Portugal (Via Verde, the first system in the world to span the entire network of tolls), France (Liber-T system), Italy (Telepass), Spain (VIA-T), Brazil (Sem Parar - Via Fácil). The tags, which are usually the active type, are read remotely as vehicles pass through the booths, and tag information is used to debit the toll from a prepaid account. The system helps to speed traffic through toll plazas as it records the date, time, and billing data for the RFID vehicle tag. The plaza- and queue-free 407 Express Toll Route, in the Greater Toronto Area, allows the use of a transponder (an active tag) for all billing. This eliminates the need to identify a vehicle by licence plate.[citation needed]
- The Transperth public transport network in Perth, Western Australia uses RFID technology in the new SmartRider ticketing system.
- In Atlanta, MARTA (Metropolitan Atlanta Rapid Transit Authority) has transitioned its bus and rail lines from coin tokens to the new Breeze Card system which uses RFID tags embedded in disposable paper tickets. More permanent plastic cards are available for frequent users.
- In Rio de Janeiro, "RioCard" passes can be used in buses, ferries, trains and subway. There are two types, one you cannot recharge, the other one can be recharged if it's been bought by the company you work for, if they provided it (only in Brazil).
- A number of ski resorts, particularly in the French Alps and in the Spanish and French Pyrenees, have adopted RFID tags to provide skiers hands-free access to ski lifts. Skiers don't have to take their passes out of their pockets.
- In Santiago (Chile) the subway system Metro and the recently implemented public transportation system Transantiago uses an RFID card called Bip or Multivia.
- In Medellín (Colombia) the system Metro and the recently implemented card system uses an RFID card called Cívica.
- In Dubai, (United Arab Emirates) drivers through Sheikh Zayed Road and Garhoud Bridge pay toll tax using RFID tags called Salik (Road Toll).
- In Milano (Italy), the ATM "Azienda Trasporti Milanese" has implemented RFID tags for frequent users.
- In Mumbai, the busiest suburban rail transport in the world, which transports 3.5 million commuters per day, has also implemented the use of RFID ticket cards for the use in automatic ticket vending machines for hassle free and no need to stand in long queues.[citation needed]
- In Barcelona, it's used to identify users in a bike sharing system called Bicing to prevent bicycle theft and detect the periode of bicycle usage.
- In the Netherlands the new OV-chipkaart system will eventually replace current bus, tram, metro and train payment systems, allowing for both more accurate fares, access control to (train)stations and more accurate determination of government fees to the various public transportation companies.[citation needed]
Product tracking
- The Canadian Cattle Identification Agency began using RFID tags as a replacement for barcode tags. The tags are required to identify a bovine's herd of origin and this is used for tracing when a packing plant condemns a carcass. Currently CCIA tags are used in Wisconsin and by US farmers on a voluntary basis. The USDA is currently developing its own program.
- High-frequency RFID or HighFID tags are used in library book or bookstore tracking, jewelry tracking, pallet tracking, building access control, airline baggage tracking, and apparel and pharmaceutical items tracking. High-frequency tags are widely used in identification badges, replacing earlier magnetic stripe cards. These badges need only be held within a certain distance of the reader to authenticate the holder. The American Express Blue credit card now includes a HighFID tag. In Feb 2008, Emirates airline started a trial of RFID baggage tracing at London and Dubai airports. [16]
- BGN has launched two fully automated Smartstores that combine item-level RFID tagging and SOA to deliver an integrated supply chain, from warehouse to consumer.
- UHF, Ultra-HighFID or UHFID tags are commonly used commercially in case, pallet, and shipping container tracking, and truck and trailer tracking in shipping yards.
- In May 2007, Bear River Supply began utilizing ultra high frequency identification (UHFID) tags to help monitor their agricultural equipment. [17]
- In Colombia, "Federación Nacional de Cafeteros" uses an RFID solution to trace the coffee.
Lap scoring
Passive and active RFID systems are used in off road events such as Enduro and Hare and Hounds racing, the riders have a transponder on their person, normally on their arm. When they complete a lap they swipe or touch the receiver which is connected to a computer and log their lap time. The Casimo Group Ltd makes a system which does this.
Animal identification
Implantable RFID tags or transponders can be used for animal identification. The transponders are more well-known as passive RFID technology, or simply "Chips" on animals.[18]
Inventory systems
An advanced automatic identification technology such as the Auto-ID system based on the Radio Frequency Identification (RFID) technology has significant value for inventory systems. Notably, the technology provides an accurate knowledge of the current inventory. In an academic study[19] performed at Wal-Mart, RFID reduced Out-of-Stocks by 30 percent for products selling between 0.1 and 15 units a day. Other benefits of using RFID include the reduction of labor costs, the simplification of business processes, and the reduction of inventory inaccuracies.
In 2004, Boeing integrated the use of RFID technology to help reduce maintenance and inventory costs on the Boeing 787 Dreamliner. With the high costs of aircraft parts, RFID technology allowed Boeing to keep track of inventory despite the unique sizes, shapes and environmental concerns. During the first six months after integration, the company was able to save $29,000 in just labor.[20]
RFID mandates
Wal-Mart and the United States Department of Defense have published requirements that their vendors place RFID tags on all shipments to improve supply chain management. Due to the size of these two organizations, their RFID mandates impact thousands of companies worldwide. The deadlines have been extended several times because many vendors face significant difficulties implementing RFID systems. In practice, the successful read rates currently run only 80%, due to radio wave attenuation caused by the products and packaging. In time it is expected that even small companies will be able to place RFID tags on their outbound shipments.
Since January, 2005, Wal-Mart has required its top 100 suppliers to apply RFID labels to all shipments. To meet this requirement, vendors use RFID printer/encoders to label cases and pallets that require EPC tags for Wal-Mart. These smart labels are produced by embedding RFID inlays inside the label material, and then printing bar code and other visible information on the surface of the label.
Another Wal-Mart division, Sam's Club, has also moved in this direction. It sent letters dated Jan. 7, 2008, to all of its suppliers, stating that by Jan. 31, 2008, every full single-item pallet shipped to its distribution center in DeSoto, Texas, or directly to one of its stores served by that DC, must bear an EPC Gen 2 RFID tag. Suppliers failing to comply will be charged a service fee. [21]
Promotion tracking
Manufacturers of products sold through retailers promote their products by offering discounts for a limited period on products sold to retailers with the expectation that the retailers will pass on the savings to their customers. However, retailers typically engage in forward buying, purchasing more product during the discount period than they intend to sell during the promotion period. Some retailers engage in a form of arbitrage, reselling discounted product to other retailers, a practice known as diverting. To combat this practice, manufacturers are exploring the use of RFID tags on promoted merchandise so that they can track exactly which product has sold through the supply chain at fully discounted prices.[22]
Human implants


Implantable RFID chips designed for animal tagging are now being used in humans. An early experiment with RFID implants was conducted by British professor of cybernetics Kevin Warwick, who implanted a chip in his arm in 1998. Night clubs in Barcelona[23], Spain and in Rotterdam, The Netherlands, use an implantable chip to identify their VIP customers, who in turn use it to pay for drinks.
In 2004, the Mexican Attorney General's office implanted 18 of its staff members with the Verichip to control access to a secure data room. (This number has been variously mis-reported as 160 or 180 staff members.[24] [25])
Security experts have warned against using RFID for authenticating people due to the risk of identity theft. For instance a man-in-the-middle attack would make it possible for an attacker to steal the identity of a person in real-time. Due to the resource-constraints of RFIDs it is virtually impossible to protect against such attack models as this would require complex distance-binding protocols. [26][27][28][29]
Libraries

Among the many uses of RFID technologies is its deployment in libraries. This technology has slowly begun to replace the traditional barcodes on library items (books, CDs, DVDs, etc.). However, the RFID tag can contain identifying information, such as a book’s title or material type, without having to be pointed to a separate database (but this is rare in North America). The information is read by an RFID reader, which replaces the standard barcode reader commonly found at a library’s circulation desk. The RFID tag found on library materials typically measures 50 mm X 50 mm in North America and 50 mm x 75 mm in Europe. It may replace or be added to the barcode, offering a different means of inventory management by the staff and self service by the borrowers. It can also act as a security device, taking the place of the more traditional electromagnetic security strip [30] And not only the books, but also the membership cards could be fitted with an RFID tag.
While there is some debate as to when and where RFID in libraries first began, it was first proposed in the late 1990s as a technology that would enhance workflow in the library setting. Singapore was certainly one of the first to introduce RFID in libraries and Rockefeller University in New York may have been the first academic library in the United States to utilize this technology, whereas Farmington Community Library may have been the first public institution, both of which began using RFID in 1999. In Europe, the first public library to use rfid was the one in Hoogezand-Sappemeer, the Netherlands, in 2001, where borrowers were given an option. To their surprise, 70% used the RFID option and quickly adapted, including elderly people.
Worldwide, in absolute numbers, RFID is used most the United States (with its 300 million inhabitants), followed by the United Kingdom and Japan. It is estimated that over 30 million library items worldwide now contain RFID tags, including some in the Vatican Library in Rome.[31]
RFID has many applications in libraries that can be highly beneficial, particularly for circulation staff. Since RFID tags can be read through an item, there is no need to open a book cover or DVD case to scan an item. This would help alleviate injuries such as repetitive strain injury that can occur over many years if done by the library staff. Where the books have a barcode on the outside, there is still the advantage that borrowers can scan an entire pile of books in one go, instead of one at a time. Since RFID tags can also be read while an item is in motion, using RFID readers to check-in returned items while on a conveyor belt reduces staff time. But, as with barcode, this can all be done by the borrowers themselves, meaning they might never again need the assistance of staff. Next to these readers with a fixed location there are also portable ones (for librarians, but in the future possibly also for borrowers, possibly even their own general purpose readers). With these, inventories could be done on a whole shelf of materials within seconds, without a book ever having to be taken off the shelf.[32]. In Umeå, Sweden, it is being used to assist visually impaired people in borrowing audiobooks[33]. In Malaysia, Smart Shelves are used to pinpoint the exact location of books in Multimedia University Library, Cyberjaya[34]. In the Netherlands, handheld readers are being introduced for this purpose.
The Dutch Union of Public Libraries ('Vereniging van Openbare Bibliotheken') is working on the concept of an interactive 'context library', where borrowers gets a reader/headphones-set, which leads them to the desired section of the library (using triangulation methods, rather like GPS or TomTom) and which they can use to read information from books on the shelves with the desired level of detail (eg a section read out loud), coming from the book's tag itself or a database elsewhere, and get tips on alternatives, based on the borrowers' preferences, thus creating a more personalised version of the library. This may also lead them to sections of the library they might otherwise never have visited. Borrowers could also use the system to exchange experiences (such as grading books). This is already done by children in the virtual realm at mijnstempel.nl, but the same could be done in physical form. Borrowers might grade the book at the return desk.
However, as of 2008 this technology still remains cost prohibitive for many smaller libraries, and the conversion time has been estimated at 11 months for an average size library. A Dutch estimate in 2004 was that a library that lends out 100,000 books per year should count on an initial cost of 50,000 euro (borrow- and return-stations 12,500 euro each, detection porches 10,000 euro each and tags 0.36 euro each). RFID taking a large burden off staff could also mean that fewer staff will be needed, resulting in some of them getting fired,[31] but that has so far not happened in North America where recent surveys have not returned a single library that cut staff because of adding RFID. In fact, library budgets are being reduced for personnel and increased for infrastructure, making it necessary for libraries to add automation to compensate for the reduced staff size. Also, the tasks that RFID takes over are largely not the primary task of librarians. A finding in the Netherlands is that borrowers are pleased with the fact that staff are now more available for answering questions.
A concern surrounding RFID in libraries that has received considerable publicity is the issue of privacy. Because RFID tags can in theory be scanned and read from over 350 feet in distance, and because RFID utilizes an assortment of frequencies (both depending on the type of tag, though), there is some concern over whether sensitive information could be collected from an unwilling source. However, library RFID tags do not contain any patron information,[35] and the tags used in the majority of libraries use a frequency only readable from approximately ten feet.[30] Also, libraries have always had to keep records of who has borrowed what, so in that sense there is nothing new. One simple option is to only let the book transmit a code, that will only mean anything in conjunction with the library's database. Another step further is to give the book a new code every time it is returned. And if in the future readers become ubiquitous (and possibly networked), then stolen books could be traced even outside the library. Removing of the tags could be made difficult if they are so small that they fit invisibly inside a (random) page, possibly put there by the publisher.
Schools and universities
School authorities in the Japanese city of Osaka are now chipping children's clothing, back packs, and student IDs in a primary school.[36] A school in Doncaster, England is piloting a monitoring system designed to keep tabs on pupils by tracking radio chips in their uniforms.[37]
Museums
RFID technologies are now also implemented in end-user applications in museums. An example is the custom-designed application eXsport at the Exploratorium, a science museum in San Francisco. When the visitor enters the museum he receives an RF Tag that can be carried on a card or necklace. The eXspot system enables the visitor to receive information about the exhibit and take photos they can collect later at the giftshop. Later on they can visit their personal Web page on which specific information such as visit dates, the visited exhibits and the taken photographs can be viewed.[38]
Social retailing
When a customer enters a dressing room, the mirror reflects their image and also images of the apparel item being worn by celebrities on an interactive display. A webcam also projects an image of the consumer wearing the item on the website for everyone to see. This creates an interaction between the consumers inside the store and their social network outside the store. The technology in this system is an RFID interrogator antenna in the dressing room and Electronic Product Code RFID tags on the apparel item[39].
Miscellaneous
- In February 2008, ThingMagic announced a partnership with Dewalt and Ford to equip 2009 Ford F-150, F-Series Super Duty pickups and E-Series vans with an embedded RFID asset tracking system enabled by ThingMagic’s Mercury5e readers.
- In November 2007, French company Violet starts selling its RFID-enabled Nabaztag with children's books (from publisher Gallimard Jeunesse) that included RFID tags inside the front cover. When the book is passed in front of the Nabaztag, it downloads the audio book on the Internet and reads the book out loud.
- Some hospitals use Active RFID tags to perform Asset Tracking in Real Time.[40]
- In 2006, the Smart Conveyer Tunnel, designed by Blue Vector, was introduced. This allowed the pharmaceutical industry to track both UHF and HF tags. Rite Aid utilized the technology with some of McKesson's products.[41]
- The NEXUS and SENTRI frequent traveler programs use RFID to speed up landborder processing between the U.S. and Canada and Mexico. [42]
- NADRA has developed an RFID-based driver license that bears the license holder's personal information and stores data regarding traffic violations, tickets issued, and outstanding penalties. The license cards are designed so that driving rights can be revoked electronically in case of serious violations.[43]
- Sensors such as seismic sensors may be read using RFID transceivers, greatly simplifying remote data collection.
- In August 2004, the Ohio Department of Rehabilitation and Correction (ODRC) approved a $415,000 contract to evaluate the personnel tracking technology of Alanco Technologies. Inmates will wear wristwatch-sized transmitters that can detect attempted removal and alert prison computers. This project is not the first rollout of tracking chips in US prisons. Facilities in Michigan, California and Illinois already employ the technology.
- Transponder timing at mass sports events.
- Used as storage for a video game system produced by Mattel, "HyperScan".
- RFIQin, designed by Vita Craft, is an automatic cooking device that has three different sized pans, a portable induction heater, and recipe cards. Each pan is embedded with an RFID tag that monitors the food 16 times per second while an MI tag in the handle of the pans transmits signals to the induction heater to adjust the temperature.
- Slippery Rock University is using RFID tags in their students' ID cards beginning in the fall 2007 semester.
- 25 real world application case studies can be found in a 61 page free Ebook RFID Technology Applications
- RFID tags are now being embedded into playing cards that are used for televisied poker tournamnets, so commentators know exactly what cards has been dealt to whom, as soon as the deal is complete.
- The Iraqi army uses an RFID security card that contains a biometric picture of the soldier. The picture in the chip must match the picture on the card to prevent forgery.[44]
- Theme parks (such as Alton Towers in the United Kingdom) have been known to use RFID to help them identify users of a ride in order to make a DVD of their time at the park. This is then available for the user to buy at the end of the day. This is voluntary by the user by wearing a wristband given to them at the park.
- Access control - many places which employ traditional swipe cards for access control are slowly shifting towards RFID contactless based solutions in their cards.
- Meetings and conventions have also implemented RFID technology into attendee badges allowing the ability to track people at conferences. This provides data that can display what rooms people have enter and exited during the day. This data is available to show organizers to help them improve the content and design of the conference. RFID is also being used to improve the lead retrieval process for exhibitors at exhibitions.
- RFID transponder chips have been implanted in golf balls for the purposes of ball tracking. The uses of such tracking range from being able to search for a lost ball using a homing device, to a computerized driving range format that tracks shots made by a player and gives feedback on distance and accuracy.
- In 2007 artist couple artcoon starts their world project Kansa. Sirpa Masalins human like wooden sculptures carry an RFID inside. Hans-Ulrich Goller-Masalin created a New Media Art work which traces the individual sculptures of Kansa in the internet. Owners are asked to register the city where their sculpture is located. By comparing the RFIDs unique number referenced at artcoon the owner can identify his sculpture as the original one.
- Some casinos are embedding RFID tags into their chips. This allows the casinos to track the locations of chips on the casino floor, identify counterfeit chips, and prevent theft. In addition, casinos can use RFID systems to study the betting behavior of players.
Potential uses
Replacing barcodes
RFID tags are often a replacement for UPC or EAN barcodes, having a number of important advantages over the older barcode technology. They may not ever completely replace barcodes, due in part to their higher cost and the advantage of multiple data sources on the same object. The new EPC, along with several other schemes, is widely available at reasonable cost.
The storage of data associated with tracking items will require many terabytes. Filtering and categorizing RFID data is needed to create useful information. It is likely that goods will be tracked by the pallet using RFID tags, and at package level with Universal Product Code (UPC) or EAN from unique barcodes.
The unique identity is a mandatory requirement for RFID tags, despite special choice of the numbering scheme. RFID tag data capacity is large enough that each individual tag will have a unique code, while current bar codes are limited to a single type code for a particular product. The uniqueness of RFID tags means that a product may be tracked as it moves from location to location, finally ending up in the consumer's hands. This may help to combat theft and other forms of product loss. The tracing of products is an important feature that gets well supported with RFID tags containing a unique identity of the tag and also the serial number of the object. This may help companies to cope with quality deficiencies and resulting recall campaigns, but also contributes to concern about tracking and profiling of consumers after the sale.
It has also been proposed to use RFID for POS store checkout to replace the cashier with an automatic system which needs no barcode scanning. This is not likely without a significant reduction in the cost of tags and changes in the POS process. There is some research taking place, however, this is some years from reaching fruition.
An FDA nominated task force came to the conclusion after studying the various technologies currently commercially available, which could meet the pedigree requirements. Amongst all technologies studied including bar coding, RFID seemed to be the most promising and the committee felt that the pedigree requirement could be met by easily leveraging something that is readily available. (More details see RFID-FDA-Regulations)
Telemetry
Active RFID tags also have the potential to function as low-cost remote sensors that broadcast telemetry back to a base station. Applications of tagometry[citation needed] data could include sensing of road conditions by implanted beacons, weather reports, and noise level monitoring. CAZ
It is possible that active or semi-passive RFID tags used with or in place of barcodes could broadcast a signal to an in-store receiver to determine whether the RFID tag (product) is in the store.
Identification of patients and hospital staff
In July 2004, the US Food and Drug Administration issued a ruling that essentially begins a final review process that will determine whether hospitals can use RFID systems to identify patients and/or permit relevant hospital staff to access medical records. Since then, a number of U.S. hospitals have begun implanting patients with RFID tags and using RFID systems, more generally, for workflow and inventory management.[45] There is some evidence, as well, that nurses and other hospital staff may be subjected to increased surveillance of their activities or to labor intensification as a result of the implementation of RFID systems in hospitals.[46] The use of RFID to prevent mixups between sperm and ova in IVF clinics is also being considered [6].
In October 2004, the FDA approved USA's first RFID chips that can be implanted in humans. The 134 kHz RFID chips, from VeriChip Corp. can incorporate personal medical information and could save lives and limit injuries from errors in medical treatments, according to the company. The FDA approval was disclosed during a conference call with investors. Shortly after the approval, authors and anti-RFID activists Katherine Albrecht and Liz McIntyre discovered a warning letter from the FDA that spelled out serious health risks associated with the VeriChip. According to the FDA, these include "adverse tissue reaction", "migration of the implanted transponder", "failure of implanted transponder", "electrical hazards" and "magnetic resonance imaging [MRI] incompatibility."
In 2007 John Wiley & Sons published a guide to RFID use in the book RFID Applied (ISBN 978-0-471-79365-6)
Possible uses for medical field
Human tagging and tracking can be a great asset for use in hospitals, more importantly emergency rooms. One reason being a nurse or doctor can easily access patient history or concerning files, allergies, or any other complications from the incoming patient.
Yoking
It has been proposed to use a strong cryptography based scheme to generate forensic evidence that two RFID tags were in proximity at the time of scanning.[47]
Regulation and standardization
There is no global public body that governs the frequencies used for RFID. In principle, every country can set its own rules for this. The main bodies governing frequency allocation for RFID are:
- USA: FCC (Federal Communications Commission)
- Canada: CRTC (Canadian Radio-television and Telecommunications Commission)
- Europe: ERO, CEPT, ETSI, and national administrations (note that the national administrations must ratify the usage of a specific frequency before it can be used in that country)
- Malaysia: Malaysian Communications and Multimedia Commission (MCMC)
- Japan: MIC (Ministry of Internal Affairs and Communications)
- China: Ministry of Information Industry
- Taiwan: NCC (National Communications Commission)
- South Africa: ICASA
- South Korea: Ministry of Commerce, Industry and Energy
- Australia: Australian Communications and Media Authority.
- New Zealand: Ministry of Economic Development
- Singapore: Infocomm Development Authority of Singapore
- Brazil: Anatel (Agência Nacional de Telecomunicações)
Low-frequency (LF: 125 – 134.2 kHz and 140 – 148.5 kHz) (LowFID) tags and high-frequency (HF: 13.56 MHz) (HighFID) tags can be used globally without a license. Ultra-high-frequency (UHF: 868 – 928 MHz) (Ultra-HighFID or UHFID) tags cannot be used globally as there is no single global standard. In North America, UHF can be used unlicensed for 902 – 928 MHz (±13 MHz from the 915 MHz center frequency), but restrictions exist for transmission power. In Europe, RFID and other low-power radio applications are regulated by ETSI recommendations EN 300 220 and EN 302 208, and ERO recommendation 70 03, allowing RFID operation with somewhat complex band restrictions from 865–868 MHz. Readers are required to monitor a channel before transmitting ("Listen Before Talk"); this requirement has led to some restrictions on performance, the resolution of which is a subject of current research. The North American UHF standard is not accepted in France as it interferes with its military bands. For China and Japan, there is no regulation for the use of UHF. Each application for UHF in these countries needs a site license, which needs to be applied for at the local authorities, and can be revoked. For Australia and New Zealand, 918 – 926 MHz are unlicensed, but restrictions exist for transmission power.
These frequencies are known as the ISM bands (Industrial Scientific and Medical bands). The return signal of the tag may still cause interference for other radio users.
Some standards that have been made regarding RFID technology include:
- ISO 14223/1 – Radio frequency identification of Animals, advanced transponders – Air interface
- ISO 14443: This standard is a very popular HF (13.56 MHz) standard for HighFIDs which is being used as the basis of RFID-enabled passports under ICAO 9303.
- ISO 15693: This is also a very popular HF (13.56 MHz) standard for HighFIDs widely used for non-contact smart payment and credit cards.
- ISO/IEC 18000: Information technology — Radio frequency identification for item management:
- Part 1: Reference architecture and definition of parameters to be standardized
- Part 2: Parameters for air interface communications below 135 kHz
- Part 3: Parameters for air interface communications at 13,56 MHz
- Part 4: Parameters for air interface communications at 2,45 GHz
- Part 6: Parameters for air interface communications at 860 MHz to 960 MHz
- Part 7: Parameters for active air interface communications at 433 MHz
- ISO 18185: This is the industry standard for electronic seals or "e-seals" for tracking cargo containers using the 433 MHz and 2.4 GHz frequencies.
- EPCglobal – this is the standardization framework that is most likely to undergo International Standardisation according to ISO rules as with all sound standards in the world, unless residing with limited scope, as customs regulations, air-traffic regulations and others. Currently the big distributors and governmental customers are pushing EPC heavily as a standard well accepted in their community, but not yet regarded as for salvation to the rest of the world.
EPC Gen2
EPC Gen2 is short for EPCglobal UHF Class 1 Generation 2.
EPCglobal (a joint venture between GS1 and GS1 US) is working on international standards for the use of mostly passive RFID and the EPC in the identification of many items in the supply chain for companies worldwide.
One of the missions of EPCglobal was to simplify the Babel of protocols prevalent in the RFID world in the 1990s. Two tag air interfaces (the protocol for exchanging information between a tag and a reader) were defined (but not ratified) by EPCglobal prior to 2003. These protocols, commonly known as Class 0 and Class 1, saw significant commercial implementation in 2002–2005.
In 2004 the Hardware Action Group created a new protocol, the Class 1 Generation 2 interface, which addressed a number of problems that had been experienced with Class 0 and Class 1 tags. The EPC Gen2 standard was approved in December 2004, and is likely to form the backbone of passive RFID tag standards moving forward. This was approved after a contention from Intermec that the standard may infringe a number of their RFID related patents. It was decided that the standard itself did not infringe their patents, but it may be necessary to pay royalties to Intermec if the tag were to be read in a particular manner. The EPC Gen2 standard was adopted with minor modifications as ISO 18000-6C in 2006.
The lowest cost of Gen2 EPC inlay is offered by SmartCode at a price of 5 cents apiece in volumes of 100 million or more[48]. Nevertheless, further conversion (including additional label stock or encapsulation processing/insertion and freight costs to a given facility or DC) and of the inlays into usable RFID labels and the design of current Gen 2 protocol standard will increase the total end-cost, especially with the added security feature extensions for RFID Supply Chain item-level tagging.
Problems and concerns
Global standardization
The frequencies used for RFID in the USA are currently incompatible with those of Europe or Japan. Furthermore, no emerging standard has yet become as universal as the barcode.[49]
Security concerns
A primary security concern surrounding technology is the illicit tracking of RFID tags. Tags which are world-readable pose a risk to both personal location privacy and corporate/military security. Such concerns have been raised with respect to the United States Department of Defense's recent adoption of RFID tags for supply chain management.[50] More generally, privacy organizations have expressed concerns in the context of ongoing efforts to embed electronic product code (EPC) RFID tags in consumer products.
EPCglobal Network, by design, is also susceptible to DoS attacks. Using similar mechanism with DNS in resolving EPC data requests, the ONS Root servers become vulnerable to DoS attacks. Any organisation planning to embark on EPCglobal Network may cringe upon finding out that the EPCglobal Network infrastructure inherits security weaknesses similar to DNS'[51].
A second class of defense uses cryptography to prevent tag cloning. Some tags use a form of "rolling code" scheme, wherein the tag identifier information changes after each scan, thus reducing the usefulness of observed responses. More sophisticated devices engage in Challenge-response authentications where the tag interacts with the reader. In these protocols, secret tag information is never sent over the insecure communication channel between tag and reader. Rather, the reader issues a challenge to the tag, which responds with a result computed using a cryptographic circuit keyed with some secret value. Such protocols may be based on symmetric or public key cryptography. Cryptographically-enabled tags typically have dramatically higher cost and power requirements than simpler equivalents, and as a result, deployment of these tags is much more limited. This cost/power limitation has led some manufacturers to implement cryptographic tags using substantially weakened, or proprietary encryption schemes, which do not necessarily resist sophisticated attack. For example, the Exxon-Mobil Speedpass uses a cryptographically-enabled tag manufactured by Texas Instruments, called the Digital Signature Transponder (DST), which incorporates a weak, proprietary encryption scheme to perform a challenge-response protocol for lower cost.
Still other cryptographic protocols attempt to achieve privacy against unauthorized readers, though these protocols are largely in the research stage. One major challenge in securing RFID tags is a shortage of computational resources within the tag. Standard cryptographic techniques require more resources than are available in most low cost RFID devices. RSA Security has patented a prototype device that locally jams RFID signals by interrupting a standard collision avoidance protocol, allowing the user to prevent identification if desired.[52] Various policy measures have also been proposed, such as marking RFID tagged objects with an industry standard label.
Exploits
Ars Technica Reported in March 2006 an RFID buffer overflow bug that could infect airport terminal RFID Databases for baggage, and also Passport databases to obtain confidential information on the passport holder.[53]
Passports
In an effort to make passports more secure, several countries have implemented RFID in passports. However, the encryption on UK chips was broken in under 48 hours.[54] Since that incident, further efforts have allowed researchers to clone passport data while the passport is being mailed to its owner. Where, previously, a criminal had to secretly open and then reseal the envelope, now it can be done without detection, adding some degree of insecurity to the passport system.[55]
Protection against interception
Unencrypted tags can be read by any reader that is close enough. This may happen accidentally, but also as a preparation for various illegal activities, such as scanning shopping bags for expensive items. Various methods can be used to protect against RFID data interception:[56]
- Most RFID chips can be disabled by physical means: for example the RFID chip inside RFID credit cards can be disabled by a sharp tap of a hammer.[7]
- An even simpler method, of use with passports for example, is wrapping the RFID-equipped item in aluminum foil.[57] (See #Shielding below about how aluminum foil may only make transmission more difficult and not completely block it.)
- One can prevent the RFID transponders from receiving power. This is accomplished by obstructing the power supply; one approach is to shield the RFID transponders in a Faraday cage, intercepting the electromagnetic signal which normally powers them. UHF transponders can be shielded using an anti-static bag. LowFID and HighFID (inductively-coupled) transponders can be shielded with conventional aluminum foil.[citation needed]
- One can simply damage the antenna. With larger RFID transponders one can recognize the spirals of the antenna clearly by use of a radiograph. If one splits the antenna circuit, the effective range of the RFID transponder will be greatly reduced.[citation needed]
- An intense electromagnetic impulse applied to the transponders and antenna can induce high currents, interrupting the circuit and rendering the tag useless. A crude way to do this is putting the RFID tag in a microwave oven. Success may vary, depending on the frequency of the microwave and the shape of the antenna. A device built to destroy transponders is the RFID-Zapper.[citation needed]
- The system can be blocked by sending a spurious signal in conjunction with the inquiry signal, preferably on the RFID frequency. This blocks the relatively weak signals of the RFID transponder.[citation needed]
- If a simple memory chip is used to confirm the authenticity of the inquiry, then one can record the inquiry and at a later time reverse engineer the signal, allowing replication. For the reader it appears as if the correct RFID transponder were in the field.[citation needed]
- Many RFID tags include a built-in 'kill' function. When provided with the correct pass-code, a tag can be either reprogrammed or told to 'self destruct', rendering it useless.[citation needed]
- Newer emerging RFID tags may include some sort of built in transfer-of-control and privacy enhancing technologies to ensure the owner can control and prevent linkage of RFID using silencing or non-linkable protocols.[citation needed]
Shielding
A number of products are available on the market[58] that will allow a concerned carrier of RFID-enabled cards or passports to shield their data. In fact the United States government requires their new employee ID cards to be delivered with an approved shielding sleeve or holder.[59] There are contradicting opinions as to whether aluminum can prevent reading of RFID chips. Some people claim that aluminum shielding, essentially creating a Faraday cage, does work.[60] Others claim that simply wrapping an RFID card in aluminum foil, only makes transmission more difficult, yet is not completely effective at preventing it.[61]
Shielding is again a function of the frequency being used. Low-frequency LowFID tags, like those used in implantable devices for humans and pets, are relatively resistant to shielding, though thick metal foil will prevent most reads. High frequency HighFID tags (13.56 MHz — smart cards and access badges) are very sensitive to shielding and are difficult to read when within a few centimetres of a metal surface. UHF Ultra-HighFID tags (pallets and cartons) are very difficult to read when placed within a few millimetres of a metal surface, although their read range is actually increased when they are spaced 2–4 cm from a metal due to positive reinforcement of the reflected wave and the incident wave at the tag. UHFID tags can be successfully shielded from most reads by being placed within an anti-static plastic bag.
Controversies

Privacy
How would you like it if, for instance, one day you realized your underwear was reporting on your whereabouts? — California State Senator Debra Bowen, at a 2003 hearing.[62]
The use of RFID technology has engendered considerable controversy and even product boycotts by consumer privacy advocates. Katherine Albrecht and Liz McIntyre are two prominent Christian critics of the technology who refer to RFID tags as "spychips". The two main privacy concerns regarding RFID are:
- Since the owner of an item will not necessarily be aware of the presence of an RFID tag and the tag can be read at a distance without the knowledge of the individual, it becomes possible to gather sensitive data about an individual without consent.
- If a tagged item is paid for by credit card or in conjunction with use of a loyalty card, then it would be possible to indirectly deduce the identity of the purchaser by reading the globally unique ID of that item (contained in the RFID tag).
Most concerns revolve around the fact that RFID tags affixed to products remain functional even after the products have been purchased and taken home and thus can be used for surveillance and other purposes unrelated to their supply chain inventory functions.[63]
The concerns raised by the above may be addressed in part by use of the Clipped Tag. The Clipped Tag is an RFID tag designed to increase consumer privacy. The Clipped Tag has been suggested by IBM researchers Paul Moskowitz and Guenter Karjoth. After the point of sale, a consumer may tear off a portion of the tag. This allows the transformation of a long-range tag into a proximity tag that still may be read, but only at short range – less than a few inches or centimeters. The modification of the tag may be confirmed visually. The tag may still be used later for returns, recalls, or recycling.
However, read range is both a function of the reader and the tag itself. Improvements in technology may increase read ranges for tags. Having readers very close to the tags makes short range tags readable. Generally, the read range of a tag is limited to the distance from the reader over which the tag can draw enough energy from the reader field to power the tag. Tags may be read at longer ranges than they are designed for by increasing reader power. The limit on read distance then becomes the signal-to-noise ratio of the signal reflected from the tag back to the reader. Researchers at two security conferences have demonstrated that passive Ultra-HighFID tags, not of the HighFID type used in US passports, normally read at ranges of up to 30 feet, can be read at ranges of 50 to 69 feet using suitable equipment.[64][65]
In January 2004 privacy advocates from CASPIAN and the German privacy group FoeBuD were invited to the METRO Future Store in Germany, where an RFID pilot project was implemented. It was uncovered by accident that METRO "Payback" customer loyalty cards contained RFID tags with customer IDs, a fact that was disclosed neither to customers receiving the cards, nor to this group of privacy advocates. This happened despite assurances by METRO that no customer identification data was tracked and all RFID usage was clearly disclosed.[66]
During the UN World Summit on the Information Society (WSIS) between the 16th to 18th of November, 2005, founder of the free software movement, Richard Stallman, protested the use of RFID security cards. During the first meeting, it was agreed that future meetings would no longer use RFID cards, and upon finding out this assurance was broken, he covered his card with aluminum foil, and would only uncover it at the security stations. This protest caused the security personnel considerable concern, with some not allowing him to leave a conference room in which he had been the main speaker, and the prevention of him entering another conference room, where he was due to speak. [citation needed]
In 2004-2005 the Federal Trade Commission Staff conducted a workshop and review of RFID privacy concerns and issued a report recommending best practices.[67]
RFID was one of the main topics of 2006 Chaos Communication Congress (organized by the Chaos Computer Club in Berlin) and triggered a big press debate. Topics included: electronic passports, Mifare cryptography and the tickets for the FIFA World Cup 2006. Talks showed how the first real world mass application of RFID technology at the 2006 FIFA Soccer World Cup worked. Group monochrom staged a special 'Hack RFID' song.[68]
Human implantation
The Food and Drug Administration in the US has approved the use of RFID chips in humans.[69] Some business establishments have also started to chip customers, such as the Baja Beach nightclub in Barcelona. This has provoked concerns into privacy of individuals as they can potentially be tracked wherever they go by an identifier unique to them. There are concerns this could lead to abuse by an authoritarian government or lead to removal of freedoms.[70]
On July 22, 2006, Reuters reported that two hackers, Newitz and Westhues, at a conference in New York City showed that they could clone the RFID signal from a human implanted RFID chip, showing that the chip is not hack-proof as was previously believed.[71]
RFID implant as the mark of the beast
A few critics, mostly conservative Evangelical Christians, believe that RFID tagging could represent the mark of the beast, which Revelation 13:16-17 says will be placed by the Antichrist in the right hands or foreheads of humans and necessary for commerce.
And he causeth all, both small and great, rich and poor, free and bond, to receive a mark in their right hand, or in their foreheads: And that no man might buy or sell, save he that had the mark, or the name of the beast, or the number of his name.
— Revelation 13:16-17
Katherine Albrecht and Liz McIntyre, authors of Spychips: How Major Corporations and Government Plan to Track Your Every Move with RFID, wrote a new book on the subject.[72] John Conner, leader of an organization called "The Resistance of Christ" also believes there is a strong connection. Related subjects include eschatology (last things) and dispensationalism.[73][74][75] Rev. Irvin Baxter Jr's Website www.endtime.com provides an in depth video analysis on the topic titled "mark of the beast."
See also
- Biometrics
- Barcode
- Electronic Product Code
- E-ZPass
- Local Positioning Systems
- High Capacity Color Barcode
- Item-Attendant ICT
- Mass surveillance
- Microchip implant (human)
- Microchip implant (animal)
- Mobile RFID
- Near Field Communication
- Pharmacy informatics
- Proximity card
- Real-time locating
- Smart cards
- Supranet
- Tracking system
References
- ^ Tedjasaputra, Adi (2007-07-14). "Sustainable Growth of RFID Supply Chain Markets". RFID Asia. Retrieved 2007-08-03.
{{cite web}}: Check date values in:|date=(help) - ^ Dargan, Gaurav; Johnson, Brian; Panchalingam, Mukunthan; Stratis, Chris (2004). "The Use of Radio Frequency Identification as a Replacement for Traditional Barcoding". Retrieved 2006-05-31.
{{cite web}}: CS1 maint: multiple names: authors list (link) - ^ a b Landt, Jerry (2001). "Shrouds of Time: The history of RFID" (PDF). AIM, Inc. Retrieved 2006-05-31.
- ^ Intermec Education Services. "Understanding RFID – Educational Video". Retrieved 2006-08-26.
{{cite web}}: Cite has empty unknown parameter:|1=(help) - ^ Paolo Magrassi (2001). "A World Of Smart Objects: The Role Of Auto Identification Technologies". Retrieved 2007-06-24.
- ^ "News release: World's smallest and thinnest 0.15 × 0.15 mm, 7.5 µm thick RFID IC chip". Hitachi, Ltd. 2006-02-06. Retrieved 2007-01-26.
{{cite web}}: Check date values in:|date=(help) - ^ Hara, Yoshiko (2006-02-06). "Hitachi advances paper-thin RFID chip". EETimes. Retrieved 2007-01-26.
{{cite news}}: Check date values in:|date=(help) - ^ "World's tiniest RFID tag unveiled". BBC News. 23 Feb 2007.
- ^ "Motorola Taps Avery Dennison for RFID Tags". RFID Update. 01 May 2007.
{{cite news}}: Check date values in:|date=(help) - ^ Tedjasaputra, Adi (2006-12-18). "RFID Tag Attachments". RFID Asia. Retrieved 2007-08-03.
{{cite web}}: Check date values in:|date=(help) - ^ Tedjasaputra, Adi (2007-02-15). "Digestible RFID Tag: an Alternative for Your Internal Body Monitoring". RFID Asia. Retrieved 2007-08-03.
{{cite web}}: Check date values in:|date=(help) - ^ Tedjasaputra, Adi (2006-12-11). "The Art and Science of RFID Tagging". RFID Asia. Retrieved 2007-08-03.
{{cite web}}: Check date values in:|date=(help) - ^ Datatilsynet misfornøyd med nye pass - digi.no
- ^ "United States sets date for E-passports".
- ^ Lemos, Robert (2008-01-02). "Policy group warns over travel card". Security Focus. SecurityFocus. Retrieved 2008-01-06.
{{cite news}}: Cite has empty unknown parameter:|coauthors=(help) - ^ Webster (2008-02-13). "BAA and Emirates test new baggage tagging technology". Jetvine. Retrieved 2008-02-13.
{{cite web}}: Check date values in:|date=(help) - ^ Beth Bacheldor (2007-10-18). "Agricultural Company Tracks Equipment Loaned to Farmers". RFID Journal. Retrieved 2008-01-03.
{{cite web}}: Check date values in:|date=(help) - ^ *USDA Bets the Farm on Animal ID Program
- ^ RFID’s reduction of Out-of-Stock study at Wal-Mart, RFID Radio
- ^ RFID's Second Wave, BusinessWeek
- ^ Bacheldor, Beth (2008-01-11). "Sam's Club Tells Suppliers to Tag or Pay". Retrieved 2008-01-17.
- ^ "Keeping Track of Promotion Progress: How Marketing Will Become the Greatest Advocate of RFID". Retrieved 2008-04-10.
{{cite web}}: Unknown parameter|coauthers=ignored (help); Unknown parameter|publication=ignored (help) - ^ Barcelona clubbers get chipped. BBC News, 29 Sep 2004
- ^ "The Register, among others, inaccurately reports 160 staff members being chipped". The Register. Retrieved 2007-08-01.
- ^ "The Register publishes a correction to the number of staff being chipped". The Register. Retrieved 2007-08-01.
- ^ High-tech cloning
- ^ Vericip hacked press release, Spychips
- ^ "Demo: Cloning a Verichip". Retrieved 2007-02-03.
- ^ "VeriChips Implanted at CityWatcher.com". Compliance and Privacy. Retrieved 2007-02-03.
No one I spoke with at Six Sigma Security or at CityWatcher knew that the VeriChip had been hacked. They were also surprised to hear of VeriChip's downsides as a medical device. It was clear they weren't aware of some of the controversy surrounding the implant. (Liz McIntyre)
- ^ a b Radio Frequency Identification: An Introduction for Library Professionals. Alan Butters. Australasian Public Libraries v19.n4(2006) pp.2164–174. Cite error: The named reference "butters" was defined multiple times with different content (see the help page).
- ^ a b "The State of RFID Applications in Libraries." Jay Singh et al. Information Technology & Libraries no.1(Mar.2006) pp.24–32. Cite error: The named reference "singh" was defined multiple times with different content (see the help page).
- ^ "Radio Frequency Identification." Rachel Wadham. "Library Mosaics" v14 no.5 (S/O 2003) pg.22.
- ^ AudioIndex - the Talking Library, Retrieved on 2007-07-25
- ^ Rahman, Rohisyam (2007-07-23). "Case Study: Malaysian Smart Shelf". RFID Asia. Retrieved 2007-08-03.
{{cite web}}: Check date values in:|date=(help) - ^ "RFID Poses No Problem for Patron Privacy." "American Libraries" v34 no11 (D 2003) pg.86.
- ^ http://networks.silicon.com/lans/0,39024663,39122042,00.htm Schoolchildren to be RFID-chipped
- ^ Schoolkid chipping trial 'a success'
- ^ S. Hsi en H. Fait, “RFID enhances visitors Museum Experience at the Exploratorium,” Communications of the ACM 48, 9 (2005): 60
- ^ Social Shopping in a Fully Enabled RFID Store, RFID Radio
- ^ Making Business Sense of Real Time Location Systems (RTLS), RFID Radio
- ^ Rite Aid Embarks on Item-Level Tracking Pilot, RFID Journal
- ^ US Customs and Border Protection NEXUS websiteUS Customs and Border Protection SENTRI website
- ^ NADRA Driving LicenseNADRA Driving License
- ^ Some Hot North American RFID Applications, RFID Radio
- ^ Fisher, Jill A. 2006. Indoor Positioning and Digital Management: Emerging Surveillance Regimes in Hospitals. In T. Monahan (Ed), Surveillance and Security: Technological Politics and Power in Everyday Life (pp. 77–88). New York: Routledge.[1]
- ^ Fisher, Jill A. and Monahan, Torin. Tracking the Social Dimensions of RFID Systems in Hospitals. International Journal of Medical Informatics 77 (3): 176-183.[2]
- ^ "RFID security and privacy: a research survey" (PDF).
- ^ Roberti, Mark (2006-05-06). "A 5-Cent Breakthrough". RFID Journal. Retrieved 2007-01-26.
{{cite news}}: Check date values in:|date=(help) - ^ "Radio Silence". The Economist. 7 Jun 2007.
- ^ "What's New". Radio Frequency Identification (RFID). 4 April 2007.
- ^ Tedjasaputra, Adi (2006-12-11). "Putting RFID Network Security in Perspective". RFID Asia. Retrieved 2007-08-03.
{{cite web}}: Check date values in:|date=(help) - ^ "RFID Privacy and Security". RSA Laboratories.
- ^ "RFID chips can carry viruses". Ars Technica. Retrieved 2006-08-26.
- ^ "RFID Passports cracked. Easily, cheaply, and quickly". wired. Retrieved 2007-03-21.
- ^ "RFID Passports cracked through the mail". the register. Retrieved 2007-03-21.
- ^ Section translated from the German Wikipedia
- ^ "Can Aluminum Shield RFID Chips?". RFID Shield.
- ^ "Products that shield RFID communication". Identity Stronghold.
- ^ "FIPS-201, Personal Identity Verification (PIV) of Federal Employees and Contractors" (PDF). NIST.
- ^ "Can Aluminum Shield RFID Chips?". RFID Shield.
- ^ "Aluminum Foil Does Not Stop RFID". Omniscience is Bliss.
- ^ Alorie Gilbert (18 Aug 2003). "Privacy advocates call for RFID regulation". News.com.
- ^ Markus Hansen, Sebastian Meissner: Identification and Tracking of Individuals and Social Networks using the Electronic Product Code on RFID Tags, IFIP Summer School, Karlstad, 2007, Slides.
- ^ "Today at PC World".
- ^ "@DEFCON RFID World Record Attempt..."
- ^ Katherine Albrecht, Liz McIntyre. "The METRO "Future Store" Special Report". Spychips.
- ^ FTC "Radio Frequency Identification: Applications and Implications for Consumers" (March 2005) http://www.ftc.gov/os/2005/03/050308rfidrpt.pdf Retrieved 2008-01-29.
- ^ monochrom. "R F I D".
- ^ Greene, Thomas C. (2004). "Feds approve human RFID implants". Retrieved 2007-03-01.
- ^ Monahan, Torin and Tyler Wall. 2007. Somatic Surveillance: Corporeal Control through Information Networks. Surveillance & Society 4 (3): 154-173.[3]
- ^ Reuters
- ^ Albrecht & McIntyre (2006). The Spychips Threat: Why Christians Should Resist RFID and Electronic Surveillance, Tennessee: Nelson Current ISBN 1595550216
- ^ Gilbert, Alorie (2006). "is RFID the mark of the beast?". News.com. Retrieved 2006-12-18.
- ^ Brown, Jim (2005). "Group Fears RFID Chips Could Herald 'Mark of the Beast'". Agape Press. Retrieved 2006-12-18.
- ^ Baard, Mark (2006). "RFID: Sign of the (End) Times?". Wired.com. Retrieved 2006-12-18.
External links
- RFID Journal
- How RFID Works at HowStuffWorks
- EPCglobal — standards for EPC
- dmoz Open Directory of RFID — Human-edited RFID
- Rfid - RFID Open Source RFID forums
