Java virtual machine
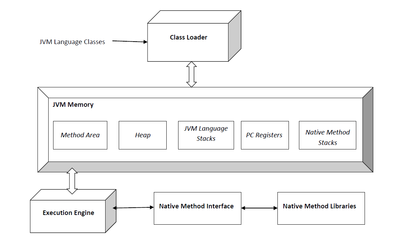
A Java virtual machine (JVM) is an abstract computing machine. There are three notions of the JVM: specification, implementation, and instance. The specification is a book that formally describes what is required of a JVM implementation. Having a single specification ensures all implementations are interoperable. A JVM implementation is a computer program that implements requirements of the JVM specification in a compliant and preferably performant manner. An instance of the JVM is a process that executes a computer program compiled into Java bytecode.
The Oracle Corporation, which owns the Java trademark, distributes the Java Virtual Machine implementation HotSpot together with an implementation of the Java Class Library under the name Java Runtime Environment (JRE).
JVM specification
The Java virtual machine is an abstract (virtual) computer defined by a specification. This specification omits implementation details that are not essential to insure interoperability. For example, the memory layout of run-time data areas, the garbage-collection algorithm used, and any internal optimization of the Java virtual machine instructions (their translation into machine code). The main reason for this omission is to not unnecessarily constrain implementors. Any Java application can be run only inside some concrete implementation of the abstract specification of the Java virtual machine.[1]
Starting with Java Platform, Standard Edition (J2SE) 5.0, changes to the JVM specification have been developed under the Java Community Process as JSR 924.[2] As of 2006[update], changes to specification to support changes proposed to the class file format (JSR 202)[3] are being done as a maintenance release of JSR 924. The specification for the JVM is published in book form,[4] known as blue book. The preface states:
We intend that this specification should sufficiently document the Java Virtual Machine to make possible compatible clean-room implementations. Oracle provides tests that verify the proper operation of implementations of the Java Virtual Machine.
One of Oracle's JVMs is named HotSpot, the other, inherited from BEA Systems is JRockit. Clean-room Java implementations include Kaffe and IBM J9. Oracle owns the Java trademark, and may allow its use to certify implementation suites as fully compatible with Oracle's specification.
Class loader
One of the organizational units of JVM bytecode is a class. A class loader implementation must be able to recognize and load anything that conforms to the Java class file format. Any implementation is free to recognize other binary forms besides class files, but it must recognize class files.
The class loader performs three basic activities in this strict order:
- Loading: finds and imports the binary data for a type
- Linking: performs verification, preparation, and (optionally) resolution
- Verification: ensures the correctness of the imported type
- Preparation: allocates memory for class variables and initializing the memory to default values
- Resolution: transforms symbolic references from the type into direct references.
- Initialization: invokes Java code that initializes class variables to their proper starting values.
In general, there are two types of class loader: bootstrap class loader and user defined class loader.
Every Java virtual machine implementation must have a bootstrap class loader, capable of loading trusted classes. The Java virtual machine specification doesn't specify how a class loader should locate classes.
Bytecode instructions
The JVM has instructions for the following groups of tasks:
The aim is binary compatibility. Each particular host operating system needs its own implementation of the JVM and runtime. These JVMs interpret the bytecode semantically the same way, but the actual implementation may be different. More complex than just emulating bytecode is compatibly and efficiently implementing the Java core API that must be mapped to each host operating system.
JVM languages
|
|
A JVM language is any languagh functionality that can be expressed in terms of a valid class file which can be hosted by the Java Virtual Machine. A class file contains Java Virtual Machine instructions (or bytecode) and a symbol table, as well as other ancillary information. The class file format, the hardware- and operating system-independent binary format used to represent compiled classes and interfaces.[6] Java 7 JVM implements JSR 292: Supporting Dynamically Typed Languages on the Java Platform, a new feature which supports dynamically typed languages in the JVM. This feature is developed within the Da Vinci Machine Project whose mission is to extend the JVM so that it supports languages other than Java.[7]
Bytecode verifier
A basic philosophy of Java is that it is inherently safe from the standpoint that no user program can crash the host machine or otherwise interfere inappropriately with other operations on the host machine, and that it is possible to protect certain methods and data structures belonging to trusted code from access or corruption by untrusted code executing within the same JVM. Furthermore, common programmer errors that often lead to data corruption or unpredictable behavior such as accessing off the end of an array or using an uninitialized pointer are not allowed to occur. Several features of Java combine to provide this safety, including the class model, the garbage-collected heap, and the verifier.
The JVM verifies all bytecode before it is executed. This verification consists primarily of three types of checks:
- Branches are always to valid locations
- Data is always initialized and references are always type-safe
- Access to private or package private data and methods is rigidly controlled
The first two of these checks take place primarily during the verification step that occurs when a class is loaded and made eligible for use. The third is primarily performed dynamically, when data items or methods of a class are first accessed by another class.
The verifier permits only some bytecode sequences in valid programs, e.g. a jump (branch) instruction can only target an instruction within the same method. Furthermore, the verifier ensures that any given instruction operates on a fixed stack location,[8] allowing the JIT compiler to transform stack accesses into fixed register accesses. Because of this, that the JVM is a stack architecture does not imply a speed penalty for emulation on register-based architectures when using a JIT compiler. In the face of the code-verified JVM architecture, it makes no difference to a JIT compiler whether it gets named imaginary registers or imaginary stack positions that must be allocated to the target architecture's registers. In fact, code verification makes the JVM different from a classic stack architecture, of which efficient emulation with a JIT compiler is more complicated and typically carried out by a slower interpreter.
The original specification for the bytecode verifier used natural language that was incomplete or incorrect in some respects. A number of attempts have been made to specify the JVM as a formal system. By doing this, the security of current JVM implementations can more thoroughly be analyzed, and potential security exploits prevented. It will also be possible to optimize the JVM by skipping unnecessary safety checks, if the application being run is proven to be safe.[9]
Secure execution of remote code
A virtual machine architecture allows very fine-grained control over the actions that code within the machine is permitted to take. This is designed to allow safe execution of untrusted code from remote sources, a model used by Java applets. Applets run within a VM incorporated into a user's browser, executing code downloaded from a remote HTTP server. The remote code runs in a restricted sandbox, which is designed to protect the user from misbehaving or malicious code. Publishers can purchase a certificate with which to digitally sign applets as safe, giving them permission to ask the user to break out of the sandbox and access the local file system, clipboard, execute external pieces of software, or network.
Bytecode interpreter and just-in-time compiler
For each hardware architecture a different Java bytecode interpreter is needed. When a computer has a Java bytecode interpreter, it can run any Java bytecode program, and the same program can be run on any computer that has such an interpreter.
When Java bytecode is executed by an interpreter, the execution will be always slower than the execution of the same program compiled into native machine language. This problem is mitigated by just-in-time (JIT) compilers for executing Java bytecode. A just-in-time compiler may translate Java bytecode into native machine language while executing the program. The translated parts of the program can then be executed much more quickly than they could be interpreted. This technique gets applied to those parts of a program frequently executed. This way a just-in-time compiler can significantly speed up the overall execution time.
There is no necessary connection between Java and Java bytecode. A program written in Java can be compiled directly into the machine language of a real computer and programs written in other languages than Java can be compiled into Java bytecode.
Java bytecode is intended to be platform-independent and secure.[10] Some JVM implementations do not include an interpreter, but consist only of a just-in-time compiler.[11]
JVM in the web browser
Since very early stages of the design process, Java (and JVM) has been marketed as a web technology for creating Rich Internet Applications.
Java applets
On the client side, web browsers may be extended with a NPAPI Java plugin which executes so called Java applets embedded into HTML pages. The applet is allowed to draw into a rectangular region on the page assigned to it and use a restricted set of APIs that allow for example access to user's microphone or 3D acceleration. Java applets were superior to JavaScript both in performance and features until approximately 2011, when JavaScript engines in browsers were made significantly faster and the HTML 5 suite of web technologies started enhancing JavaScript with new APIs. Java applets are not able to modify the page outside its rectangular region which is not true about JavaScript. Adobe Flash Player, the main competing technology, works in the same way in this respect. Java applets are not restricted to Java and in general can be created in any JVM language.
According to W3Techs, Java applets are currently (February 2015) being used on 0.1% of all web sites. Flash is being used on 11.8% and Silverlight on 0.1% of web sites.[12]
JavaScript JVMs and interpreters
JVM implementations in JavaScript do exist, but are mostly limited to hobby projects unsuitable for production deployment or development tools to avoid having to recompile every time the developer wants to preview the changes just made.
Compilation to JavaScript
With the continuing improvements in JavaScript execution speed, combined with the increased use of mobile devices whose web browsers do not implement support for plugins, there are efforts to target those users through compilation to JavaScript. It is possible to either compile the source code or JVM bytecode to JavaScript. Compiling the JVM bytecode which is universal across JVM languages allows building upon the existing compiler to bytecode.
Main JVM bytecode to JavaScript compilers are TeaVM,[13] the compiler contained in Dragome Web SDK,[14] Bck2Brwsr,[15] and j2js-compiler.[16]
Leading compilers from JVM languages to JavaScript include the Java to JavaScript compiler contained in Google Web Toolkit, Clojure script (Clojure), GrooScript (Groovy), Scala.js (Scala) and others.[17]
Java Runtime Environment from Oracle
The Java Runtime Environment (JRE) released by Oracle is a software distribution containing a stand-alone Java VM (HotSpot), browser plugin, Java standard libraries and a configuration tool. It is the most common Java environment installed on Windows computers. It is freely available for download at the website java.com.
Performance
The JVM specification gives a lot of leeway to implementors regarding the implementation details. Since Java 1.3, JRE from Oracle contains a JVM called HotSpot. It has been designed to be a high-performance JVM.
To speed-up code execution, HotSpot relies on just-in-time compilation. To speed-up object allocation and garbage collection, HotSpot uses generational heap.
Generational heap
The Java virtual machine heap is the area of memory used by the JVM for dynamic memory allocation.[18]
In HotSpot the heap is divided into generations:
- The young generation stores short-lived objects that are created and immediately garbage collected.
- Objects that persist longer are moved to the old generation (also called the tenured generation). This memory is subdivided into (two) Survivors spaces where are stored the objects that survived the first and next garbage collections.
The permanent generation (or permgen) was used for class definitions and associated metadata prior to Java 8. Permanent generation was not part of the heap.[19][20] The permanent generation was removed from Java 8.[21]
Originally there was no permanent generation, and objects and classes were stored together in the same area. But as class unloading occurs much more rarely than objects are collected, moving class structures to a specific area allowed significant performance improvements.[19]
Security
Oracle's JRE is installed on a large number of computers. Since any web page the user visits may run Java applets, Java provides an easily accessible attack surface to malicious web sites that the user visits. Kaspersky Labs reports that the Java web browser plugin is the method of choice for computer criminals. Java exploits are included in many exploit packs that hackers deploy onto hacked web sites.[22]
In the past, end users were often using an out-of-date version of JRE which was vulnerable to many known attacks. This lead to the wildly shared belief between users that Java is inherently insecure.[23] Since Java 1.7, Oracle's JRE for Windows includes automatic update functionality.
Toolbar controversy
Beginning in 2005, Sun's (now Oracle's) JRE included unrelated software which was installed by default. In the beginning it was Google Toolbar, later MSN Toolbar, Yahoo Toolbar and finally the Ask Toolbar. The Ask Toolbar proved to be especially controversial. There has been a petition asking Oracle to remove it. The signers voiced their belief that "Oracle is violating the trust of the hundreds of millions of users who run Java on their machines. They are tarnishing the reputation of a once proud platform".[24] Zdnet called their conduct deceptive, since after the user refuses the Toolbar the first time, the installer offers installing the toolbar during each update and relies on the user being too busy or distracted to install it by mistake. [25] Ask Toolbar activates itself 10 minutes after the Java update is complete, presumably to further confuse unsophisticated users.[26]
See also
- List of Java virtual machines
- Comparison of Java virtual machines
- Comparison of application virtual machines
- Automated exception handling
- Java performance
- List of JVM languages
- Java processor
- Common Language Runtime
Notes
- ^ Inside the Java Virtual Machine by Bill Venners, Chapter 5 http://www.artima.com/insidejvm/ed2/index.html
- ^ JSR 924, specifies changes to the JVM specification starting with J2SE 5.0
- ^ JSR 202, specifies a number of changes to the class file format
- ^ The Java Virtual Machine Specification (the first and second editions are also available online)
- ^ 1996, possibly the first new language specifically designed to run on the JVM)
- ^ The Java® Virtual Machine Specification Java SE 7 Edition http://docs.oracle.com/javase/specs/jvms/se7/jvms7.pdf
- ^ New JDK 7 Feature: Support for Dynamically Typed Languages in the Java Virtual Machine http://www.oracle.com/technetwork/articles/javase/dyntypelang-142348.html
- ^ "The Verification process". The Java Virtual Machine Specification. Sun Microsystems. 1999. Retrieved 2009-05-31.
- ^ Stephen N. Freund and John C. Mitchell. 1999. A formal framework for the Java bytecode language and verifier. In Proceedings of the 14th ACM SIGPLAN conference on Object-oriented programming, systems, languages, and applications (OOPSLA '99), A. Michael Berman (Ed.). ACM, New York, NY, USA, 147–166. DOI=10.1145/320384.320397 http://doi.acm.org/10.1145/320384.320397
- ^ http://math.hws.edu/javanotes/c1/s3.html Introduction to Programming Using Java, Seventh Edition, Version 7.0, August 2014 by David J. Eck Section 1.3 The Java Virtual Machine
- ^ http://docs.oracle.com/cd/E15289_01/doc.40/e15058/underst_jit.htm Oracle® JRockit Introduction Release R28 2. Understanding Just-In-Time Compilation and Optimization
- ^ http://w3techs.com/technologies/details/cp-javaruntime/all/all
- ^ http://teavm.org/
- ^ http://www.dragome.com/
- ^ http://wiki.apidesign.org/wiki/Bck2Brwsr
- ^ https://github.com/decatur/j2js-compiler
- ^ https://github.com/jashkenas/coffeescript/wiki/list-of-languages-that-compile-to-js
- ^ "Frequently Asked Questions about Garbage Collection in the Hotspot Java Virtual Machine". Sun Microsystems. 6 February 2003. Retrieved 7 February 2009.
- ^ a b Masamitsu, Jon (28 November 2006). "Presenting the Permanent Generation". Retrieved 7 February 2009.
- ^ Nutter, Charles (11 September 2008). "A First Taste of InvokeDynamic". Retrieved 7 February 2009.
- ^ "JEP 122: Remove the Permanent Generation". Oracle Corporation. 2012-12-04. Retrieved 2014-03-23.
- ^ http://www.kaspersky.com/about/news/virus/2013/Is_there_any_protection_against_Java_exploits
- ^ http://lifehacker.com/5988800/what-is-java-is-it-insecure-and-should-i-use-it
- ^ http://www.infoq.com/news/2013/02/Ask_Bar_Bundle_Petition
- ^ http://www.zdnet.com/article/a-close-look-at-how-oracle-installs-deceptive-software-with-java-updates/
- ^ http://www.benedelman.org/news/012213-1.html#java
References
- Clarifications and Amendments to the Java Virtual Machine Specification, Second Edition includes list of changes to be made to support J2SE 5.0 and JSR 45
- JSR 45, specifies changes to the class file format to support source-level debugging of languages such as JavaServer Pages (JSP) and SQLJ that are translated to Java

