OpenBSD
 "Free, Functional & Secure" | |
 OpenBSD 5.9 desktop. | |
| Developer | The OpenBSD Project |
|---|---|
| OS family | Unix-like (BSD) |
| Working state | Current |
| Source model | Open source |
| Initial release | 1 October 1996 |
| Latest release | 7.6 (8 October 2024) [±] |
| Repository | |
| Package manager | OpenBSD package tools and ports tree |
| Platforms | Alpha, x86-64, i386, MIPS64, PowerPC, SPARC 32/64, Zaurus and others[1] |
| Kernel type | Monolithic |
| Userland | BSD |
| Default user interface | Modified pdksh, FVWM 2.2.5 for X11 |
| License | BSD, ISC, ATU,[2] other custom licenses[3] |
| Official website | openbsd |
OpenBSD is a Unix-like computer operating system descended from Berkeley Software Distribution (BSD), a Research Unix derivative developed at the University of California, Berkeley. It was forked from NetBSD by project leader Theo de Raadt in late 1995. As well as the operating system, the OpenBSD Project has produced portable versions of numerous subsystems, most notably PF, OpenSSH and OpenNTPD, which are very widely available as packages in other operating systems.
The project is also widely known for the developers' insistence on open-source code and quality documentation, uncompromising position on software licensing, and focus on security and code correctness. The project is coordinated from de Raadt's home in Calgary, Alberta, Canada. Its logo and mascot is a pufferfish named Puffy.
OpenBSD includes a number of security features absent or optional in other operating systems, and has a tradition in which developers audit the source code for software bugs and security problems. The project maintains strict policies on licensing and prefers the open-source BSD licence and its variants. In the past this has led to a comprehensive license audit and moves to remove or replace code under licences found less acceptable.
As with most other BSD-based operating systems, the OpenBSD kernel and userland programs are developed together in one source code repository. OpenBSD's userland encompasses basic Unix tools such as the shell, cat, and ps, as well as more complex services including httpd and OpenSMTPD. Third-party software is available as binary packages or may be built from source using the ports tree.
The OpenBSD project maintains ports for many different hardware platforms, including the DEC Alpha, IA-32, MIPS64, Hewlett-Packard PA-RISC, SPARC, SPARC64, x86-64, Apple's PowerPC machines, and the Sharp Zaurus.[1]
Uses


Security
OpenBSD's security enhancements, built-in cryptography and the pf packet filter suit it for use in the security industry, for example on firewalls,[4] intrusion-detection systems and VPN gateways.
Proprietary systems from several manufacturers are based on OpenBSD, including devices from Armorlogic (Profense web application firewall), Calyptix Security, GeNUA mbH, RTMX Inc,[5] and .vantronix GmbH.[6] Later versions of Microsoft's Services for UNIX, an extension to the Windows operating system which provides some Unix-like functionality, use much OpenBSD code included in the Interix interoperability suite, developed by Softway Systems Inc., which Microsoft acquired in 1999.[7][8] Core Force, a security product for Windows, is based on OpenBSD's pf firewall.[9]
Desktop
OpenBSD ships with the X window system[10] and is suitable for use on the desktop.[11] Packages for popular desktop tools are available, including desktop environments GNOME, KDE, Lumina Desktop and Xfce; web browsers Konqueror, Mozilla Firefox and Chromium; and multimedia programs MPlayer, VLC media player and xine.[12] The Project also includes two minimalist window managers in the main distribution: cwm and FVWM.
Enterprise
Open source software consultancy "M:tier" has deployed OpenBSD on servers, desktops and firewalls in corporate environments of many Fortune 500 companies.[13]
Server
OpenBSD features a full server suite and is easily configured as a mail server, web server, FTP server, DNS server, router, firewall, or NFS file server. Software providing support for other server protocols are available as packages.
OpenBSD component projects
Despite the small team size and relatively low usage of OpenBSD, the project has successfully spun off widely available portable versions of numerous parts of the base system, including:
- LibreSSL, a free implementation of the Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols, forked from the OpenSSL 1.0.1g branch
- OpenBGPD, a free implementation of the Border Gateway Protocol 4 (BGP-4)
- OpenOSPFD, a free implementation of the Open Shortest Path First (OSPF) routing protocol
- OpenNTPD, a simple alternative to ntp.org's Network Time Protocol (NTP) daemon
- OpenSMTPD, a free Simple Mail Transfer Protocol (SMTP) daemon with IPv4/IPv6, PAM, Maildir and virtual domains support
- httpd, an HTTP server first included in the 5.6 release
- OpenSSH, a free implementation of the Secure Shell (SSH) protocol
- OpenIKED, a free implementation of the Internet Key Exchange (IKEv2) protocol
- Common Address Redundancy Protocol (CARP), a free alternative to Cisco's patented HSRP/VRRP server redundancy protocols
- PF, an IPv4/IPv6 stateful firewall with NAT, PAT, QoS and traffic normalization support
- pfsync, a firewall states synchronization protocol for PF firewall with High Availability support using CARP
- spamd, a spam filter with greylisting capability designed to inter-operate with the PF firewall
- sndio, a compact audio and MIDI framework
- Xenocara, a customized X.Org build infrastructure
- cwm, a stacking window manager
Some of the subsystems have been integrated into the core system of several other BSD projects, and all are available widely as packages for use in other Unix-like systems, and in some cases in Microsoft Windows.
Third-party components in the base system
- X.org, the X Window environment, with local patches.
- GCC, with OpenBSD-specific patches,[14] is included in the base system and used as the default compiler. It is optional but recommended. As of OpenBSD 5.8 (October, 2015), either 4.2.1 or 3.3.6 is shipped, depending on the platform.
- Perl with patches.
- SQLite with patches.
- NSD
- Unbound (DNS server)
- Ncurses
- Binutils with patches.
- gdb with patches.
- Awk
- tmux virtual console multiplexer.
In the past, OpenBSD included a fork of Apache 1.3 and later Nginx. In the 5.6 release, Nginx was replaced with httpd(8), an HTTP server with FastCGI and Transport Layer Security support based on the relayd(8) source code. Apache and Nginx are still available as ports.
Development and release process

Development is continuous, and team management is open and tiered. Anyone with appropriate skills may contribute, with commit rights being awarded on merit and de Raadt acting as coordinator.[15] Two official releases are made per year, with the version number incremented by 0.1,[16] and these are each supported for twelve months. Snapshot releases are also available at very frequent intervals. Maintenance patches for supported releases may be applied manually or by regularly updating the system against the patch branch of the CVS repository for that release.
Alternatively a system administrator may opt to upgrade using a snapshot release and then regularly update the system against the "current" branch of the CVS repository, in order to gain pre-release access to recently added features.
The standard GENERIC OpenBSD kernel, as maintained by the project, is strongly recommended for universal use, and customized kernels are not supported by the project, in line with the philosophy that 'attempts to customize or "optimize" the kernel cause more problems than they solve.'
Packages outside the main system build are maintained by CVS through a ports tree and are the responsibility of the individual maintainers (known as porters). As well as keeping the current branch up to date, the porter of a package is expected to apply appropriate bug-fixes and maintenance fixes to branches of the package for supported releases. Ports are not subject to the same continuous rigorous auditing as the main system because the project lacks the manpower to do this.
Binary packages are built centrally from the ports tree for each architecture. This process is applied for the current version, for each supported release, and for each snapshot. Administrators are recommended to use the package mechanism rather than build the package from the ports tree, unless they need to perform their own source changes.
OpenBSD's developers regularly come together from all around the world and organize a special event called "hackathon". In hackathons, the developers "sit down and code", emphasizing productivity.[17]
Every new release includes a song.[18]
The OpenBSD Foundation was accepted as a mentoring organization for Google Summer of Code 2014.[19][20]
History and popularity
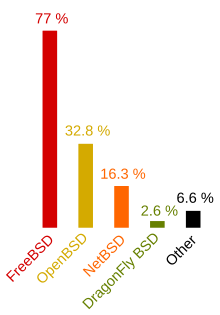
In December 1994, NetBSD co-founder Theo de Raadt was asked to resign from his position as a senior developer and member of the NetBSD core team.[22] The reason for this is not wholly clear, although there are claims that it was due to personality clashes within the NetBSD project and on its mailing lists.[22]
In October 1995, de Raadt founded OpenBSD, a new project forked from NetBSD 1.0. The initial release, OpenBSD 1.2, was made in July 1996, followed in October of the same year by OpenBSD 2.0.[23] Since then, the project has followed a schedule of a release every six months, each of which is maintained and supported for one year. The latest release, OpenBSD 5.9, appeared on 29 March 2016.
On 25 July 2007, OpenBSD developer Bob Beck announced the formation of the OpenBSD Foundation,[24] a Canadian not-for-profit corporation formed to "act as a single point of contact for persons and organizations requiring a legal entity to deal with when they wish to support OpenBSD."[25]
Just how widely OpenBSD is used is hard to ascertain: its developers neither publish nor collect usage statistics, and there are few other sources of information. In September 2005, the nascent BSD Certification Group performed a usage survey which revealed that 32.8% of BSD users (1420 of 4330 respondents) were using OpenBSD,[21] placing it second of the four major BSD variants, behind FreeBSD with 77% and ahead of NetBSD with 16.3%.[26]
Open-source and open documentation
The OpenBSD Project is noted for its high-quality user documentation, considered top among the BSD family operating systems, all of which have excellent documentation.[27][28] When OpenBSD was created, Theo de Raadt decided that the source should be easily available for anyone to read at any time, so, with the assistance of Chuck Cranor,[29] he set up the first public, anonymous CVS server. At the time, the tradition was for only a small team of developers to have access to a project's source repository.[30] Cranor and de Raadt concluded that this practice "runs counter to the open source philosophy" and is inconvenient to contributors. De Raadt's decision allowed "users to take a more active role", and signaled the project's belief in open and public access to source code.[30]
OpenBSD does not include closed source binary drivers in the source tree and will not allow non-disclosure agreements.[31]
Since OpenBSD is based in Canada, no United States export restrictions on cryptography apply, allowing the distribution to make full use of modern algorithms for encryption. For example, the swap space is divided into small sections and each section is encrypted with its own key, ensuring that sensitive data doesn't leak into an insecure part of the system.[32]
OpenBSD randomizes various behaviors of applications, making them less predictable and thus more difficult to attack. For example, PIDs are created and associated randomly to processes; the bind() system call uses random port numbers; files are created with random inode numbers; and IP datagrams have random identifiers.[33] This approach also helps expose bugs in the kernel and in userspace programs.
The OpenBSD policy on openness extends to hardware documentation: in the slides for a December 2006 presentation, de Raadt explained that without it "developers often make mistakes writing drivers", and pointed out that "the [oh my god, I got it to work] rush is harder to achieve, and some developers just give up".[34] He went on to say that vendor binary drivers are unacceptable to OpenBSD, that they have "no trust of vendor binaries running in our kernel" and that there is "no way to fix [them] ... when they break".[34]
Licensing
A goal of the OpenBSD project is to "maintain the spirit of the original Berkeley Unix copyrights", which permitted a "relatively un-encumbered Unix source distribution".[35] To this end, the Internet Systems Consortium (ISC) license, a simplified version of the BSD license with wording removed that is unnecessary under the Berne convention, is preferred for new code, but the MIT or BSD licenses are accepted. The widely used GNU General Public License is considered overly restrictive in comparison with these.[36]
In June 2001, triggered by concerns over Darren Reed's modification of IPFilter's license wording, a systematic license audit of the OpenBSD ports and source trees was undertaken.[37] Code in more than a hundred files throughout the system was found to be unlicensed, ambiguously licensed or in use against the terms of the license. To ensure that all licenses were properly adhered to, an attempt was made to contact all the relevant copyright holders: some pieces of code were removed, many were replaced, and others, including the multicast routing tools, mrinfo[38] and map-mbone,[39] which were licensed by Xerox for research only, were relicensed so that OpenBSD could continue to use them. Also removed during this audit was all software produced by Daniel J. Bernstein. At the time, Bernstein requested that all modified versions of his code be approved by him prior to redistribution, a requirement to which OpenBSD developers were unwilling to devote time or effort.[40][41][42]
The OpenBSD team has developed software from scratch, or adopted suitable existing software, because of license concerns. Of particular note is the development, after license restrictions were imposed on IPFilter, of the pf packet filter, which first appeared[43] in OpenBSD 3.0 and is now available in other major BSDs. OpenBSD developers have also replaced GPL licensed tools (such as diff, grep and pkg-config) with BSD licensed equivalents.[44]
Funding
Although the operating system and its portable components are widely used in commercial products, de Raadt says that little of the funding for the project comes from the industry: "traditionally all our funding has come from user donations and users buying our CDs (our other products don't really make us much money). Obviously, that has not been a lot of money."[16]
For a two-year period in the early 2000s, the project received DARPA funding, which "paid the salaries of 5 people to work completely full-time, bought about $30k in hardware, and paid for 3 hackathons."[16]
De Raadt has expressed some concern about the asymmetry of funding: "I think that contributions should have come first from the vendors, secondly from the corporate users, and thirdly from individual users. But the response has been almost entirely the opposite, with almost a 15 to 1 dollar ratio in favor of the little people. Thanks a lot, little people!"[16]
On 14 January 2014, Bob Beck issued a request for funding to cover electrical costs. If sustainable funding was not found, Beck suggested OpenBSD would shut down.[45] The project soon received a USD$20,000 donation from Mircea Popescu, the Romanian creator of the MPEx bitcoin stock exchange, paid in bitcoins.[46] The project raised USD$150,000[47] in response to the appeal, enabling it to pay its bills and securing its short-term future.[46]
The OpenBSD project had previously experienced another financial danger back in 2006.[48] The Mozilla Foundation[49] and GoDaddy[50] are among the organizations that helped the OpenBSD project to overcome its financial troubles.
Security and code auditing
Shortly after OpenBSD's creation, Theo de Raadt was contacted by a local security software company named Secure Networks, Inc. or SNI.[51][52] They were developing a "network security auditing tool" called Ballista (later renamed to Cybercop Scanner after SNI was purchased by Network Associates), which was intended to find and attempt to exploit possible software security flaws. This coincided well with de Raadt's own interest in security, so for a time the two cooperated, a relationship that was of particular usefulness leading up to the release of OpenBSD 2.3[53] and helped to define security as the focal point of the project.[54]
OpenBSD includes features designed to improve security, such as:
- secure alternatives to POSIX functions in the C standard library (e.g.
strlcatandstrlcpy[55]) - toolchain alterations, including a static bounds checker
- memory protection techniques to guard against invalid accesses, such as ProPolice and the W^X page protection feature
- strong cryptography and randomization.[56]
To reduce the risk of a vulnerability or misconfiguration allowing privilege escalation, some programs have been written or adapted to make use of privilege separation, privilege revocation and chrooting. Privilege separation is a technique, pioneered on OpenBSD and inspired by the principle of least privilege, where a program is split into two or more parts, one of which performs privileged operations and the other—almost always the bulk of the code—runs without privilege.[57] Privilege revocation is similar and involves a program performing any necessary operations with the privileges it starts with then dropping them. Chrooting involves restricting an application to one section of the file system, prohibiting it from accessing areas that contain private or system files. Developers have applied these features to OpenBSD versions of common applications such as tcpdump.[58]
OpenBSD developers were instrumental in the birth and development of OpenSSH, which is developed in the OpenBSD repositories. OpenSSH is based on the original SSH.[59] It first appeared in OpenBSD 2.6 and is now by far the most popular SSH client and server, available on many operating systems.[60]
The project has a policy of continually auditing code for problems, work that developer Marc Espie has described as "never finished ... more a question of process than of a specific bug being hunted". He went on to list several typical steps once a bug is found, including examining the entire source tree for the same and similar issues, "try[ing] to find out whether the documentation ought to be amended", and investigating whether "it's possible to augment the compiler to warn against this specific problem".[61]
Alleged FBI backdoor investigated
On 11 December 2010, Gregory Perry, a former technical consultant for the FBI, sent an email to Theo de Raadt alleging that the FBI had paid some OpenBSD ex-developers 10 years previously to insert backdoors into the OpenBSD Cryptographic Framework. Theo de Raadt made the email public on 14 December by forwarding it to the openbsd-tech mailing list and suggested an audit of the IPsec codebase.[62][63] De Raadt's response was skeptical of the report and he invited all developers to independently review the relevant code. In the weeks that followed, bugs were fixed but no evidence of backdoors was found.[64] Theo de Raadt states that "I believe that NetSec was probably contracted to write backdoors as alleged. If those were written, I don't believe they made it into our tree. They might have been deployed as their own product."[65]
Slogan
The OpenBSD website features a prominent reference to the security record of the default install. Until June 2002, the wording read "Five years without a remote hole in the default install!" An OpenSSH bug was then discovered that made it possible for a remote attacker to gain root in OpenBSD and in any of the many other systems running OpenSSH at the time. It was quickly fixed, as is normal with known security holes.[66][67] The slogan was modified to "One remote hole in the default install, in nearly 6 years!" In 2007 a network-related remote vulnerability was found, which was also quickly fixed.[68] The quote was subsequently altered to "Only two remote holes in the default install, in a heck of a long time!" This wording remains to this day.
The default install is quite minimal, but the project states that the default install is intentionally minimal to ensure novice users "do not need to become security experts overnight",[69] which fits with open-source and code auditing practices argued to be important elements of a security system.[70]
Portability
Since 2004, the New York City BSD Users Group database provides dmesg information from a collection of computers running OpenBSD.[71] The project itself collects dmesg information from users at dmesg@openbsd.org.
Distribution and marketing
The name OpenBSD refers to the fact that OpenBSD's source code is freely available through the Internet. It also refers to the wide range of hardware platforms the operating system supports.[72]
OpenBSD is available freely in various ways: the source can be retrieved by anonymous CVS,[73] and binary releases and development snapshots can be downloaded by FTP, HTTP, rsync, and AFS.[74] Prepackaged CD-ROM sets can be ordered online for a small fee, complete with an assortment of stickers and a copy of the release's theme song. These, with their artwork and other bonuses, are one of the project's few sources of income, funding hardware, Internet service, and other expenses.[75]
In common with other operating systems, OpenBSD provides a package management system for easy installation and management of programs which are not part of the base operating system.[76] Packages are binary files which are extracted, managed and removed using the package tools. On OpenBSD, the source of packages is the ports system, a collection of Makefiles and other infrastructure required to create packages. In OpenBSD, the ports and base operating system are developed and released together for each version: this means that the ports or packages released with, for example, 4.6 are not suitable for use with 4.5 and vice versa.[76]

OpenBSD at first used the BSD daemon mascot. A specialized version of the daemon, the haloed daemon was drawn by Erick Green. Green was asked by Theo de Raadt to create the logo for the 2.3 and 2.4 versions of OpenBSD. At first, it was planned to create a full daemon, including head and body, but Green was only able to complete the head part for OpenBSD 2.3. The body as well as pitchfork and tail was completed for OpenBSD 2.4.[77] Subsequent releases saw variations, such as Cop daemon by Ty Semaka,[78] but eventually settling on Puffy,[79] described as a pufferfish.[80] Since then Puffy has appeared on OpenBSD promotional material and featured in release songs and artwork. The promotional material of early OpenBSD releases did not have a cohesive theme or design but later the CD-ROMs, release songs, posters and tee-shirts for each release have been produced with a single style and theme, sometimes contributed to by Ty Semaka of the Plaid Tongued Devils.[18] These have become a part of OpenBSD advocacy, with each release expounding a moral or political point important to the project, often through parody.[81] Past themes have included: in OpenBSD 3.8, the Hackers of the Lost RAID, a parody of Indiana Jones linked to the new RAID tools featured as part of the release; The Wizard of OS, making its debut in OpenBSD 3.7, based on the work of Pink Floyd and a parody of The Wizard of Oz related to the project's recent work on wireless card drivers; and OpenBSD 3.3's Puff the Barbarian, including an 80s rock-style song and parody of Conan the Barbarian, alluding to open documentation.[18]
Bibliography
- Absolute OpenBSD, 2nd Edition by Michael W. Lucas. ISBN 978-1-59327-476-4
- The OpenBSD Command-Line Companion, 1st ed. by Jacek Artymiak. ISBN 83-916651-8-6.
- Building Firewalls with OpenBSD and PF: Second Edition by Jacek Artymiak. ISBN 83-916651-1-9.
- Mastering FreeBSD and OpenBSD Security by Yanek Korff, Paco Hope and Bruce Potter. ISBN 0-596-00626-8.
- Absolute OpenBSD, Unix for the Practical Paranoid by Michael W. Lucas. ISBN 1-886411-99-9 (online copy here)
- Secure Architectures with OpenBSD by Brandon Palmer and Jose Nazario. ISBN 0-321-19366-0.
- The OpenBSD PF Packet Filter Book: PF for NetBSD, FreeBSD, DragonFly and OpenBSD published by Reed Media Services. ISBN 0-9790342-0-5.
- Building Linux and OpenBSD Firewalls by Wes Sonnenreich and Tom Yates. ISBN 0-471-35366-3.
- The OpenBSD 4.0 Crash Course by Jem Matzan. ISBN 0-596-51015-2.
- The Book of PF A No-Nonsense Guide to the OpenBSD Firewall, 2nd edition by Peter N.M. Hansteen ISBN 978-1-59327-274-6 .
See also
- BSD Authentication
- BSD and GPL licensing
- Comparison of BSD operating systems
- Comparison of operating systems
- Comparison of operating system kernels
- Comparison of open source operating systems
- Hackathon
- KAME project
- OpenBSD Journal
- pfSense
- POSSE project
- Security-focused operating system
References
- ^ a b "Platforms", OpenBSD, retrieved 29 March 2016
- ^ E.g. Atmel firmware may be redistributed in object code only. atu-license OpenSBD CVS Repository
- ^ "CVS Repository". openbsd.org. Retrieved 13 October 2015.
- ^ McIntire, Tim (8 August 2006), "Take a closer look at OpenBSD", Developerworks, IBM, retrieved 13 December 2011,
Because OpenBSD is both thin and secure, one of the most common OpenBSD implementation purposes is as a firewall.
- ^ "RTMX O/S IEEE Real Time POSIX Operating Systems", RTMX Inc., retrieved 13 December 2011,
RTMX O/S is a product extension to OpenBSD Unix-like operating system with emphasis on embedded, dedicated applications.
- ^ ".vantronix secure system", Compumatica secure networks GmbH, retrieved 13 December 2011,
The Next Generation Firewall is not a standalone device, it is a Router for operation in security critical environments with high requirements for availability, comprehensive support as well as reliable and trusted systems powered by OpenBSD.
- ^ "Microsoft Acquires Softway Systems To Strengthen Future Customer Interoperability Solutions", Microsoft News Center, Microsoft, 17 September 1999
- ^ Dohnert, Roberto J. (21 January 2004), "Review of Windows Services for UNIX 3.5", OSNews, David Adams
- ^ "Core Force", Core Labs, retrieved 13 December 2011,
CORE FORCE provides inbound and outbound stateful packet filtering for TCP/IP protocols using a Windows port of OpenBSD's PF firewall, granular file system and registry access control and programs' integrity validation.
- ^ "About Xenocara", Xenocara, retrieved 13 December 2011
- ^ Tzanidakis, Manolis (21 April 2006), Using OpenBSD on the desktop, Linux.com, retrieved 9 March 2012
- ^ "The OpenBSD 4.9 Release", OpenBSD, retrieved 13 December 2011,
Over 6,800 ports...Gnome 2.32.1, KDE 3.5.10.
- ^ Jacoutot, Antoine (20 April 2011), "A Puffy in the corporate aquarium", OpenBSD Journal, Daniel Hartmeier
- ^ "OpenBSD gcc-local(1), OpenBSD's local modifications to compiler.", OpenBSD, retrieved 23 May 2015
- ^ Lucas, Michael W. (2003). Absolute OpenBSD, Unix for the Practical Paranoid (1st ed.). No Starch Press. ISBN 1-886411-99-9. Retrieved 15 June 2012.
{{cite book}}: Cite has empty unknown parameters:|lastn=,|laydate=,|coauthors=,|separator=,|laysummary=,|editorn-link=,|nopp=,|chapterurl=,|trans_chapter=,|trans_title=,|editorn-first=,|authorn-link=,|editorn-last=,|month=,|authormask=,|lastauthoramp=, and|firstn=(help) - ^ a b c d Andrews, Jeremy (2 May 2006), "Interview: Theo de Raadt", KernelTrap, Jeremy Andrews
- ^ "Interview: Theo de Raadt of OpenBSD". newsforge.com. 28 March 2006. Retrieved 31 March 2016.
- ^ a b c "Release Songs", OpenBSD FAQ, retrieved 13 December 2011
- ^ "'Google Summer Of Code 2014.' - MARC". Marc.info. 25 February 2014. Retrieved 4 March 2014.
- ^ "GSOC 2014 with the OpenBSD Foundation". Openbsdfoundation.org. Retrieved 4 March 2014.
- ^ a b 2005 BSD Usage Survey Report (PDF), The BSD Certification Group, 31 October 2005, retrieved 16 September 2012
- ^ a b Glass, Adam (23 December 1994). "Theo De Raadt". netbsd-users (Mailing list).
{{cite mailing list}}: Unknown parameter|mailinglist=ignored (|mailing-list=suggested) (help) - ^ de Raadt, Theo (18 October 1996). "The OpenBSD 2.0 release". openbsd-announce (Mailing list).
{{cite mailing list}}: Unknown parameter|mailinglist=ignored (|mailing-list=suggested) (help) - ^ "The OpenBSD Foundation", OpenBSD Foundation, retrieved 13 December 2011
- ^ Beck, Bob (25 July 2007). "Announcing: The OpenBSD Foundation". openbsd-misc (Mailing list).
{{cite mailing list}}: Unknown parameter|mailinglist=ignored (|mailing-list=suggested) (help) - ^ Multiple selections were permitted as a user may use multiple BSD variants side by side.
- ^ "BSD: The Other Free UNIX Family". InformIT. 20 January 2006. Archived from the original on 14 March 2014. Retrieved 18 January 2014.
- ^ Smith, Jesse (18 November 2013). "OpenBSD 5.4: Puffy on the Desktop". Archived from the original on 30 April 2014. Retrieved 4 April 2014.
- ^ Cranor, Chuck D., Chuck Cranor's Home Page, retrieved 13 December 2011,
I also hosted and helped create the first Anonymous CVS server on the Internet (the original anoncvs
.openbsd .org, which was also known as eap .ccrc .wustl .edu). {{citation}}: External link in|quote= - ^ a b Cranor, Chuck D.; de Raadt, Theo (11 June 1999), Opening the Source Repository with Anonymous CVS (PDF), USENIX, retrieved 13 December 2011
- ^ "OpenBSD Project Goals". openbsd.org. Retrieved 13 October 2015.
- ^ McIntire, Tim (8 August 2006). "Take a closer look at OpenBSD". IBM. Retrieved 31 March 2016.
- ^ de Raadt, Theo, Niklas Hallqvist, Artur Grabowski, Angelos D. Keromytis and Niels Provos (26 April 1999). "Randomness Used Inside the Kernel". USENIX. Archived from the original on 14 March 2014. Retrieved 1 February 2014.
{{cite web}}: CS1 maint: multiple names: authors list (link) - ^ a b de Raadt, Theo (5 December 2006), Presentation at OpenCON, retrieved 13 December 2011
- ^ "Copyright Policy", OpenBSD, retrieved 13 December 2011
- ^ Matzan, Jem (15 June 2005), "BSD cognoscenti on Linux", NewsForge, Linux.com, archived from the original on 7 February 2008
- ^ Gasperson, Tina (6 June 2001), "OpenBSD and ipfilter still fighting over license disagreement", Linux.com, archived from the original on 26 June 2008
- ^ "MRINFO(8)", OpenBSD Manual Pages, retrieved 13 December 2011
- ^ "MAP-MBONE(8)", OpenBSD Manual Pages, retrieved 13 December 2011
- ^ de Raadt, Theo (24 August 2001). "Re: Why were all DJB's ports removed? No more qmail?". openbsd-misc (Mailing list).
{{cite mailing list}}: Unknown parameter|mailinglist=ignored (|mailing-list=suggested) (help) - ^ Bernstein, DJ (27 August 2001). "Re: Why were all DJB's ports removed? No more qmail?". openbsd-misc (Mailing list).
{{cite mailing list}}: Unknown parameter|mailinglist=ignored (|mailing-list=suggested) (help) - ^ Espie, Marc (28 August 2001). "Re: Why were all DJB's ports removed? No more qmail?". openbsd-misc (Mailing list).
{{cite mailing list}}: Unknown parameter|mailinglist=ignored (|mailing-list=suggested) (help) - ^ Hartmeier, Daniel, "Design and Performance of the OpenBSD Stateful Packet Filter (pf)", Systor AG, retrieved 13 December 2011
- ^ OpenBSD CVS logs showing import of diff, grep and pkg-config. OpenBGPD and OpenNTPD man pages from OpenBSD.
- ^ Beck, Bob (14 January 2014), "Request for Funding our Electricity", openbsd-misc, openbsd-misc
- ^ a b Bright, Peter (20 January 2014), "OpenBSD rescued from unpowered oblivion by $20K bitcoin donation", Ars Technica, retrieved 20 January 2014
- ^ "The OpenBSD Foundation 2014 Fundraising Campaign". Openbsdfoundation.org. Retrieved 24 May 2014.
- ^ "OpenBSD Project in Financial Danger". Slashdot. 21 March 2006. Retrieved 12 December 2014.
- ^ "Mozilla Foundation Donates $10K to OpenSSH". Slashdot. 4 April 2006. Retrieved 12 December 2014.
- ^ "GoDaddy.com Donates $10K to Open Source Development Project". thehostingnews.com. Archived from the original on 11 November 2006. Retrieved 12 December 2014.
{{cite web}}: Unknown parameter|deadurl=ignored (|url-status=suggested) (help) - ^ Varghese, Sam (8 October 2004), "Staying on the cutting edge", The Age, retrieved 13 December 2011
- ^ Laird, Cameron; Staplin, George Peter (17 July 2003), "The Essence of OpenBSD", ONLamp, retrieved 13 December 2011
- ^ de Raadt, Theo (19 December 2005). "2.3 release announcement". openbsd-misc (Mailing list).
Without [SNI's] support at the right time, this release probably would not have happened
{{cite mailing list}}: Unknown parameter|mailinglist=ignored (|mailing-list=suggested) (help) - ^ Wayner, Peter (13 July 2000), "18.3 Flames, Fights, and the Birth of OpenBSD", Free For All: How Linux and the Free Software Movement Undercut the High Tech Titans (1st ed.), HarperBusiness, ISBN 978-0-06-662050-3, retrieved 13 December 2011
- ^ Todd C., Miller; de Raadt, Theo (6 June 1999), "strlcpy and strlcat – consistent, safe, string copy and concatenation", Proceedings of the 1999 USENIX Annual Technical Conference, USENIX, pp. 175–178, retrieved 13 December 2011
- ^ de Raadt, Theo; Hallqvist, Niklas; Grabowski, Artur; Keromytis, Angelos D.; Provos, Niels, Cryptography in OpenBSD: An overview (PDF), retrieved 13 December 2011
{{citation}}: Unknown parameter|lastauthoramp=ignored (|name-list-style=suggested) (help) - ^ Provos, Niels (9 August 2003), Privilege Separated OpenSSH, retrieved 13 December 2011
- ^ OpenBSD CVS logs showing addition of privilege separation to tcpdump and httpd man page describing the chroot mechanism.
- ^ "Project History and Credits", OpenSSH, retrieved 13 December 2011
- ^ "SSH usage profiling", OpenSSH, retrieved 13 December 2011
- ^ Biancuzzi, Federico (18 March 2004), "An Interview with OpenBSD's Marc Espie", ONLamp, retrieved 13 December 2011
- ^ de Raadt, Theo (14 December 2010). "Allegations regarding OpenBSD IPSEC". openbsd-tech (Mailing list).
{{cite mailing list}}: Unknown parameter|mailinglist=ignored (|mailing-list=suggested) (help) - ^ Holwerda, Thom (14 December 2010), "FBI Added Secret Backdoors to OpenBSD IPSEC", OSNews, retrieved 13 December 2011
- ^ Ryan, Paul (23 December 2010), "OpenBSD code audit uncovers bugs, but no evidence of backdoor", Ars Technica, Condé Nast Digital, retrieved 9 January 2011
- ^ "OpenBSD Founder Believes FBI Built IPsec Backdoor". InformationWeek. 22 December 2010. Archived from the original on 14 March 2014. Retrieved 22 January 2014.
- ^ "OpenSSH Remote Challenge Vulnerability", Internet Security Systems Security Advisory, Internet Security Systems, 26 June 2002, retrieved 13 December 2011
- ^ OpenSSH "Challenge-Response" authentication buffer overflow, Internet Security Systems, retrieved 13 December 2011
- ^ "OpenBSD's IPv6 mbufs remote kernel buffer overflow", Core Security Technologies – CoreLabs Advisory, Core Security Technologies, 13 March 2007, retrieved 13 December 2011
- ^ "Security", OpenBSD, retrieved 13 December 2011,
Secure by Default
- ^ Wheeler, David A. (3 March 2003), "2.4. Is Open Source Good for Security?", Secure Programming for Linux and Unix HOWTO, retrieved 13 December 2011
- ^ "dmesgd". dmesgd.nycbug.org. NYC*BUG. Retrieved 16 December 2015.
- ^ "New year's resolution No. 1: Get OpenBSD". InfoWorld. 29 December 2006. Archived from the original on 14 March 2014. Retrieved 14 March 2014.
- ^ "Anonymous CVS", OpenBSD, retrieved 13 December 2011
- ^ "Getting the OpenBSD distribution", OpenBSD, retrieved 13 December 2011
- ^ "Ordering OpenBSD products", OpenBSD, retrieved 13 December 2011,
The proceeds from sale of these products is the primary funding of the OpenBSD project.
- ^ a b "15 – The OpenBSD packages and ports system", OpenBSD FAQ, retrieved 13 December 2011
- ^ "OpenBSD". mckusick.com. Retrieved 12 December 2014.
- ^ de Raadt, Theo (19 May 1999). "OpenBSD 2.5 Release Announcement". openbsd-announce mailing list. Archived from the original on 14 March 2014. Retrieved 28 January 2014.
OpenBSD 2.5 introduces the new Cop daemon image done by cartoonist Ty Semeka
- ^ "The OpenBSD 2.7 Release", OpenBSD FAQ, retrieved 13 December 2011
- ^ Although in fact pufferfish do not possess spikes and images of Puffy are closer to a similar species, the porcupinefish.
- ^ Matzan, Jem (1 December 2006), "OpenBSD 4.0 review", Software In Review, retrieved 13 December 2011,
Each OpenBSD release has a graphical theme and a song that goes with it. The theme reflects a major concern that the OpenBSD programmers are addressing or bringing to light.
