Homebrew (video games)
This article has multiple issues. Please help improve it or discuss these issues on the talk page. (Learn how and when to remove these messages)
|

Homebrew is a term frequently applied to video games or other software produced by consumers to target proprietary hardware platforms (usually with hardware restrictions) not typically user-programmable or that use proprietary storage methods. This can include games developed with official development kits, such as Net Yaroze, Linux for PlayStation 2 or Microsoft XNA.[1]
Many homebrew games are offered as freeware, although others are offered for sale, and some can be quite costly.[1] One popular type of homebrew game is the fangame. In Japan, these games are usually called "Dōjin soft".
Homebrew games for older systems are typically developed using emulators for convenience, since testing them requires no extra hardware on the part of the programmer. Development for newer systems typically involves actual hardware given the lack of accurate emulators. Efforts have been made to use actual console hardware for many older systems, though. Atari 2600 homebrew developers use various methods, for example, burning an EEPROM to plug into a custom cartridge board or audio transfer via the Starpath Supercharger. Game Boy Advance homebrew developers have several ways to use GBA flash cartridges in this regard.
Along with the Dreamcast, Game Boy Advance, and PlayStation Portable, the most frequently used platforms for homebrew development are older generations of consoles, among them the Atari 2600 and Nintendo Entertainment System (NES). The Atari 2600 and NES use the 6502 instruction set, likely familiar to people who have programmed 8-bit home computers, such as the Commodore 64 or Apple II. Another factor in the popularity of older or portable systems for homebrew development, relative to modern consoles, is that their simplicity enables an individual or small group to develop acceptable games in a reasonable time frame.
All major sixth generation consoles enjoy some popularity with homebrew developers, but less so than earlier generations. This is mostly the case because software production requires more resources, accurate emulators do not exist yet, and the consoles themselves often employ rather complex systems to prevent the execution of unauthorized code. Homebrew developers must often exploit loopholes to enable their software to run.
Homebrewing is not only limited to games – there are numerous demos that have been released for most systems with a homebrew scene.
First- through fourth-generation consoles

Magnavox Odyssey
In 2009 the release of "Odball" ended the longest game drought on any console. The Magnavox Odyssey, the world's first home console, saw no new releases since 1973. It was produced by Robert Vinciguerra.[2]
On July 11, 2011 an Odyssey game called "Dodgeball" was published by Chris Read (aka Atari2600Land).[3]
On July 16, 2012 Vinciguerra published "Mentis Cohorts" for Magnavox Odyssey, which combines four games in one. The game has two modes that can be played like a board game or a puzzle game without and Odyssey, and it has a two player and a single player mode that can be played with the Odyssey, making it the first ever single player Odyssey game.[4]
On July 19, 2012 Vinciguerra released "Red vs. Blue" through RevRob.com as a free homebrew for Odyssey fans to commemorate the 40th anniversary of the Odyssey, and home video games in general.[5]
Fairchild Channel F
A handful of homebrew games have been programmed for the Channel F, the world's first programmable game console. The first known release is Sean Riddle's Lights Out that was released with instructions on how to modify the SABA#20 Chess game into a Multi-Cartridge.[6] There is also a version of Tetris and in 2008 "Videocart 27: Pac-Man" became the first full production homebrew for the Channel F.
Atari 2600
The Atari 2600, released in 1977, is a popular platform for homebrew projects. Games created for the Atari can be executed using either an emulator or directly when copied onto a blank cartridge making use of either a PROM or EPROM chip. Unlike later systems, the console does not require a modchip.
Although there is one high-level compiler available, batari Basic, most development for the Atari 2600 is still done in 6502 assembly language. Homebrews written in assembly are typically considered programming challenges.
The Atari 2600 lacks video memory, and programs run simultaneously with the television screen, updating graphical registers a fraction of a second before the television draws each scan line. For each scan line, the system's Television Interface Adapter can only draw two custom, eight-bit graphical objects, a twenty-bit "playfield", and three solid pixels: two "missiles" and one "ball".[7] Timing is critical in this environment. If a program takes too long to update the registers, the television will update the screen before the graphics are properly initialized, resulting in glitches or other video problems. In this respect, Atari 2600 programming could be considered a form of hard real-time computing.
Nintendo Entertainment System (NES)
Several compilers are available for the Nintendo Entertainment System, but like the Atari 2600, most development directly applies assembly language. One impediment to NES homebrew development is the relative difficulty involved with producing physical cartridges, although third party flash carts do exist, making homebrew possible on original NES hardware.[8] Several varieties of custom integrated circuits are used within NES cartridges to expand system capabilities; most are difficult to replicate except by scavenging old cartridges. The hardware lockout mechanism of the NES further complicates construction of usable physical cartridges. However, the NES-101 removed the 10NES lockout chip so any game, whether homebrew, unlicensed, or another region of an official game, can be played.[citation needed] The 10NES chip can eventually be permanently disabled by performing a minor change to the hardware.
Sega Mega Drive/Genesis and Master System

Both the Sega Genesis/Mega Drive and Sega Master System benefit from limited homebrew development, as there is no physical lockout mechanism, thereby easing the operation of software on these platforms. Homebrew efforts for the Mega Drive/Genesis have grown, as there are now several full games scheduled for release in physical form, such as Rick Dangerous 1 & 2 and a port of Teenage Queen. Pier Solar and the Great Architects and Frog Feast for the Mega Drive/Genesis and Mighty Mighty Missile for the Sega Mega-CD are examples of homebrew games already released for Sega consoles.
A QBASIC-like high level compiler named basiegaxorz exists for the Sega Genesis.
Neo-Geo MVS, Neo-Geo AES, and Neo-Geo CD
The Neo-Geo Home Cart and Arcade Systems can be tough candidates for homebrew development. Neo-Geo AES and MVS cartridges have two separate boards: one for video, and one for sound. If programming a cartridge for the system were to occur, it would involve replacing the old rom chips with your newly programmed ones as the cartridges are in a sense, Arcade boards. NGDevTeam who have released "Fast Striker and "Gunlord found a workaround with this. What they did was print out their own board, and soldered their own rom chips into them; this however can cause the Universe Bios logo to look corrupted if a custom bios were to be programmed. Programming for the Neo-Geo CD, however is easier than programming for cartridges. The CDs themselves can actually contain both sound and video respectively. Depending on the Megabit count for a game you program, load times will vary. A CD game with low Megabit counts will load only one time; whereas a CD game with higher Megabit counts could load in between scenes, or rounds. There are now some full games scheduled for release in physical form, such as "Neo Xyx" [9]
Super Nintendo Entertainment System (SNES)
After its discontinuation of games in 1998, and production in 1999, the fans of the Super Nintendo Entertainment System made homebrew ROM images, even without Nintendo's support for the console.
After the release of the SNES there was great interest in reverse engineering the system to allow for homebrew and backup play. Nintendo fitted the machine with various security measures such as the lock-out chip to prevent unauthorized code running on the machine.
Eventually the homebrew community figured out how games ran on the SNES hardware and were able to bypass its security mechanisms. Companies such as BUNG released hardware plugins such as the Game Doctor SF series. These allowed users to not only copy games but also to run homebrew developed games on the SNES hardware. Homebrew ROMs could be converted into the Game Doctor SF format and put onto a 3 1/2" floppy. Games as large as twelve megabits could be put on floppy disks formatted to 1.6 megabytes.
An alternative device was the Super Flash, by Tototek, which allowed for multiple games to be burned onto a flash memory chip of cartridge (allowing up to 48Mbits). This chip was the mask rom for the Super Flash development cartridge; it was easy to use and had a user interface on the computer end; simply plug in the Super Flash cartridge and upload the games one wanted. This allowed users to make a SNES game and play it in an actual cartridge rather than a floppy disk.
The legality of homebrew SNES game releases has not been tested in court, and it is debatable whether or not bypassing their security measures would fall afoul of modern reverse engineering laws. Presumably homebrew games can be produced legally for the SNES as long as no copyrighted material is included.
Previously in the 1990s, Nintendo sued Color Dreams for producing NES games without an official license. The outcome was an undisclosed settlement, but Color Dreams continued to produce unlicensed games. The strength of Color Dreams' position lies with that they worked around the 10NES lockout chip code rather than illegally duplicating it.
TurboGrafx-16/PC Engine
The TurboGrafx-16/PC Engine has a small but very dedicated homebrew scene. The first homebrew title released on CD was MindRec's Implode in 2002, a few years after the system's last official release (Dead Of The Brain I & II for the PC Engine in 1999). Two years later, MindRec released Meteor Blaster DX on CD-R. Official word was that it was unable to be pressed to CD proper due to the glass mastering software suddenly unable to handle the unorthodox style of CD layout that the system expects. Five years later, Aetherbyte Studios released Insanity, a Berzerk clone, on pressed CD, quelling the notion of unpressable CDs. Aetherbyte later went on to prototype and produce a new HuCard design called AbCARD that is 100% compatible with the console. Other homebrewers of note include Chris Covell (developer of Tongueman's Logic, released in 2007), Frozen Utopia (developer of Mysterious Song, released in 2012), and Cédric Bourse (aka Orion, developer of Ultimate Rally Club, released in 2011).
There is one dedicated C compiler for the console known as HuC. It has not been officially updated since 2005. The MagicKit assembler (pceas) is generally considered the de facto assembler for the console, and comes included with HuC. Additional libraries of note for HuC/MagicKit include Squirrel, a powerful MML-based sound engine developed by Aetherbyte Studios, and the SGX/ACD library, developed by Tomatheous, that gives the developer easy access to the SuperGrafx video hardware as well as the Arcade Card.
The cc65 C compiler is also noted to be compatible with the console, although there is no official development library support.
Fifth-generation consoles
Atari Jaguar
The Atari Jaguar was the last console produced by the Tramiel owned version of Atari. The console has an active homebrew development scene strongly facilitated by the release of the publishing rights for the console by one time owners Hasbro.[10] Prominent homebrews for the console have included Battlesphere and Frog Feast in addition to many other projects. In recent years the demo crew Reboot and members of the developer community Jagware have proven to be most active and released several full games. Coding for the console is predominantly done in assembly language and the Atari SDK has been made available. Since emulation of the console is still limited, coding is best conducted using a real Jaguar console with the official Jaguar 'Alpine' Devkit, a Skunkboard Flash Cart or a BJL uploader.
Another World, Black Out, Impulse X, Elansar, Kobayashi Maru, Degz and Rebooteroids can be considered now as some of the first professional homebrew games being released for the Jaguar.
PlayStation
Making games on the PlayStation is possible with any model of the system through the use of a modchip or the double 'Swap Trick'. Requirements consist of a PC (Personal Computer), SDK (Software Development Kit), and a 'Comms Link' device to upload and download files to and from the console.
Homebrew was originally promoted by Sony with the Net Yaroze, which had a large scene for quite some time. However, the official Net Yaroze site was shut down in mid-2009, and Sony stopped supporting the system as well as the users who still owned the console.
Sega Saturn
The Sega Saturn homebrew scene is small but active. As with the PlayStation, all models are capable of homebrew. Modchips for the Saturn Model 1 have been scarce for sometime now (as it seems that no one has produced any new modchips in years), so the only two options left are to either perform the easy swap trick or extensively modify a Saturn Model 2 modchip.
Running homebrew on the Model 2 is as easy as bridging two points on the modchip, soldering a wire from the modchip to the Saturn power supply, and inserting it where the CD-rom ribbon cable inserts. The swap trick is more difficult to pull off on this Model due to the lack of an access light.
Now there is the "PseudoSaturn" unlocking method. A program created by CyberWarrior2000 which installs in place of the original firmware of a "Pro Action Replay" cart. It unlocks region, frequency and CD protection of most Saturn models. Either a modded Saturn or a swap trick is required to run the installer, which loads the code in the FlashROM of the cartridge. Afterwards, the cartridge unlocks everything and most software can be run, from backups to homebrews.
Virtual Boy
Homebrew has been promoted for years by the site planet Virtual Boy since the system has no region lock but it was not until the flash cart FlashBoy and FlashBoy+ (that has save feature) was released that the homebrew scene grew. Although the Virtual Boy only lasted 8 months before being discontinued in March 1996, dedicated fans have been making a variety of homebrew games for years and even two previously unreleased games, Bound High and the Japanese version of Faceball (known as NikoChan Battle) have been released.
Nintendo 64
The Nintendo 64 homebrew scene is small, but homebrew can still be played and developed through the use of a Doctor V64, (Acclaim used a Doctor V64 to help develop Turok,[11]) the Everdrive 64[12] or 64drive.[13]
NEC PC-FX
There is only one homebrew development kit known for the PC-FX, which is based on the GNU Compiler Collection version 2.95.1. The Mednafen author began work on a library for the compiler called pcfxlib but it was discontinued due to lack of interest until trap15 started development of a new library called liberis. The toolchain is designed for a Linux environment, although it can also be used with cygwin. To date, no homebrew titles for the PC-FX have been released, although Aetherbyte Studios and Eponasoft have both expressed interest in developing new software for the console.
Sixth-generation consoles
Nuon
The Nuon was a game chip built into several DVD players. VM Labs, which made the system, released a homebrew SDK just before it went bankrupt. The graphical capabilities are on par with the PlayStation. Homebrew Nuon apps can only be played on Samsung DVD-N50x and RCA Nuon DVD players.
Dreamcast
Despite its short commercial lifespan of less than two years in North America, the Dreamcast benefits from an active homebrew scene even ten years after its discontinuation. Due to a flaw in the Dreamcast BIOS, which was intended for use with MIL-CD's, the console can run software from CD-R without the use of a modchip. Sega reacted by removing MIL-CD support from the BIOS of the later produced Dreamcast consoles manufactured from November 2000 onwards.
The console is especially notable for its commercial homebrew scene. One notable project was the Bleemcast! emulator, which was a series of bootdisks made to play PlayStation games on the system, featuring visual enhancements over the original console. Newer independent releases include Last Hope, released by RedSpotGames in 2007, and DUX,[14] both Shoot 'em up style games. These releases were written using the KallistiOS development system. A port of the freeware high-level development language Fenix and BennuGD is available for use in game development; many DIV Games Studio games have been ported and others were originally written for the system.
PlayStation 2
Early versions of the PlayStation 2 have a buffer overflow bug in the part of the BIOS that handles PS1 game compatibility; hackers found a way to turn this into a loophole called the PS2 Independence Exploit, allowing the use of homebrew software. Another option for homebrew development is the use of a modchip. Also, it is possible for developers to utilize a PS2 hard drive and HD Loader.
As of May 2008, there is a superior exploit called Free McBoot, which is applicable to all PS2s including Slimlines except for SCPH-9000x models with BIOS 2.30 and up, where the exploit was patched by Sony. Manufacturing of such homebrew-proof models started in the third quarter of 2008, which is denoted as date code 8C on the console, although some consoles of this line still have the old unpatched 2.20 BIOS.
Unlike the Independence Exploit, which requires a trigger disk, Free McBoot needs only a standard Memory Card, which allows it to be used on systems with broken optical drives. The installation is keyed to the Memory Card and will be usable on only the same version consoles that it was originally installed on, unless a Multi-Install is performed.
The drawback of this exploit is that it needs to be installed/compiled on each individual memory card. Simply copying the exploit is not possible; this means that an already modded or exploited system is required to install FMCB on a Memory Card.
After installing an exploit, unsigned executables (Executable and Linkable Format) may be launched from a Memory Card or an USB drive. Such programs include emulators, media players, hard drive management tools, and PC-based or NAS-based file shares. The exploit is also notable for allowing the user to copy PS1/PS2 save files from a Memory Card to a USB drive, a functionality normally only possible with tools such as a DexDrive.
Sony also released an official homebrew-development kit that allows PlayStation 2 to run Linux.
Nintendo GameCube
Homebrew development on the Nintendo GameCube tended to be difficult, since it uses a proprietary MiniDVD-based drive and media as opposed to the standard DVD drives of the PS2 and Xbox for piracy protection. Also, its connectivity is limited, as it does not feature a USB port or a HDD port like the PlayStation 2.
The barrier to burning Nintendo GameCube discs with a consumer DVD burner is the Burst Cutting Area, a "barcode" in the innermost ring of the disc, an area inaccessible to most burners and writeable only by very expensive disc pressing machines. For a long time the only way to run homebrew software on Nintendo GameCube was through a patching-system exploit of Phantasy Star Online Episode I & II, requiring users to find the game and a Broadband Adapter. Both of these are difficult to find because a follow-up has been released (under the name Phantasy Star Online Episode I & II Plus) and thus the original PSO was rarely sold after then, and because the Broadband Adapter was not often carried in stores due to the Nintendo GameCube's very limited selection of online games.
Currently the most common method is to use a special loader software, often using a modchip, and homebrew software can be loaded from DVD-R, SD card (with an SD card to memory card adapter and a SD Media Launcher), or over Ethernet. As the Nintendo GameCube's case does not fit a full-size DVD-R, third party replacement cases are available. Most of Nintendo GameCube homebrew software is developed to emulate other video game systems.
The once slow Nintendo GameCube scene is faring better than it was during its commercial lifespan thanks to bearing technical similarities with its popular successor, the Wii.
Xbox

The Xbox console uses several measures, including cryptographically signed code to obfuscate firmware. The primary method of executing homebrew code required installing a mod chip which could be flashed with a modified Microsoft BIOS. This BIOS allowed the system to boot unsigned executables (XBEs) and control several hardware variables, such as region coding and video mode. With the leak of Microsoft's official development kit (XDK) homebrew coders were able to write replacement Xbox GUIs (known as dashboards), games and applications for the Xbox.
A softmod which uses a commercial game such as 007: Agent Under Fire, Mech Assault or Splinter Cell to load up homebrew software has been discovered. This method utilizes modified font and sound files to cause the Xbox to intentionally crash and load one of the homebrew dashboards. Once in this condition, the Xbox is able to execute homebrew games and applications.
Because the Xbox uses standard PC libraries, writing homebrew games is relatively easy, as the vast majority of libraries available for a PC programmer are available to an Xbox homebrew programmer.
One of the more common type of homebrew games for the Xbox are ports of PC games whose source has been publicly released or leaked. Many classic PC games have been released for Xbox, but most are created with the XDK which limits their availability. The only places to find these ports are through IRC or peer-to-peer browsers.
The Xbox system is also very adept at running emulators which have been ported from PC. The Xbox is able to emulate systems up to the previous generation, including the Nintendo 64 and the PlayStation. For this reason, many different emulators have been created for the Xbox, and some of them have even more development support than their PC counterparts.
Recently, progress has been made in the creation of a legal development kit for the Xbox, known as OpenXDK. The OpenXDK is intended to allow coders to create new applications and games, as well as port existing source codes, without using illegally obtained Microsoft software. The games and applications created under the OpenXDK can be legally hosted on the net, and downloaded by users.
Even after the release of the Xbox 360, the Xbox homebrew scene remains extremely active, with new game ports, emulators, and applications coming out weekly. Microsoft is currently encouraging Xbox 360 homebrewed content with XNA, though at a charge of $99 per year.
Game Boy Advance
This section is empty. You can help by adding to it. (February 2014) |
Seventh-generation consoles
PlayStation Portable (PSP)
The PSP homebrew scene is very popular, since there are almost every week an updated, or a new homebrew game. PSP homebrew programs are available for download on various sites like "PSP Slim Hacks"[15] or "Wololo,"[16] "FouadtjuhMaster"[17] and "PSPCFW"[18]
Nintendo DS
Nintendo DS homebrew programs can be made with several methods usually built upon the devkitARM toolchain (provided by devkitPRO) and the libnds library. Additional utilities such as DS Game Maker provide an extra layer of services for homebrewers. Homebrew programs can be run on the Nintendo DS hardware by using Flashcards or FlashMe. They can also be run on a Nintendo DS emulator.
Xbox 360
Microsoft has released a version of its proprietary Software Development Kit (SDK) for free, to would-be homebrew programmers. This SDK, called XNA Game Studio, is a free version of the SDK available to professional development companies and college students. However, to create Xbox 360 games you must pay for a premium membership to the XNA Creators Club. Once the games are verified, the games written with XNA Studio can be made available for 80, 240, or 400 Microsoft Points to all Xbox 360 owners (through Xbox Live). This allows creators of homebrew content access to their target audience of Xbox 360 owners. This content is available under the Indie Games section of the New Xbox Experience.
On March 20, 2007, it was announced that a hack using the previously discovered hypervisor vulnerability in the Xbox 360 kernel versions 4532 and 4548 had been developed to allow users to run XeLL, a Linux bootloader. The initial hack was beyond the average user and required an Xbox serial cable to be installed and a flashed DVD Drive firmware. Felix Domke, the programmer behind XeLL, has since announced a live bootable Linux CD suitable for novice users, with the capabilities to be installed to the SATA hard drive of the Xbox 360. Despite the availability of such a distribution, the Xbox 360 still isn't considered a popular platform for homebrew development, given the dependence of the exploit on the DVD-ROM being able to load a burnt DVD game, a modified version of the game King Kong, and two older kernel revisions of the console itself.
A group independent of Microsoft is working on the means to run homebrew code, as part of the Free60 project.
Note: The hypervisor vulnerability in the Xbox 360 kernel versions 4532 and 4548 was addressed by Microsoft with the release of the NXE system and dashboard update in 2008.[citation needed]
Homebrew was since re-enabled on any Xbox 360 with dash 2.0.7371.0 or lower via an exploit referred to as the jtag / jtag smc hack but was promptly patched again by Microsoft with the 2.0.8495.0 update.
Homebrew has now become available on most if not all Xbox 360 consoles due to the Reset Glitch Hack. So far it works on all current dashboards up to as of now the latest 17489 dashboard. Although it can run unsigned code some hardware is required to do the hack/exploit. Also soldering skills are a necessity when attempting to use this exploit.
PlayStation 3
The PlayStation 3 was designed to run other operating systems from day one. Very soon after launch, the first users managed to install Fedora Core 5 onto the PlayStation 3 via the 'Install Other OS' option in the PlayStation 3's XMB (Xross Media Bar), which also allows configuring the PlayStation 3 to boot into the other OS installed by default.
So far, several Linux flavors have been successfully installed to the PlayStation 3, such as Fedora Core 5, Fedora Core 6, Gentoo, Ubuntu and Yellow Dog Linux (YDL). The latter comes installed with the Cell SDK by default, allowing programmers a low cost entry into Cell programming. See also: Linux for PlayStation 3
Originally, graphics support was limited to framebuffer access only (no access to the PlayStation 3's graphics chip RSX), yet some access to the RSX graphics processor was achieved (but Sony blocked this with firmware release 2.10).
As of firmware release 3.21, consumers are no longer able to access the 'Other OS' due to Sony removing the facility[19] from the software in an update. Sony said this was in response to several 'security concerns'.
Homebrew developers do have access to the Cell microprocessor, including 6 of its 7 active Synergistic Processing Elements (SPEs). The Game OS resides under a hypervisor and prevents users from taking full control of the PlayStation 3's hardware. This is a security measure which helps Sony feel secure enough to allow users to install other operating systems on the PS3.
The Sixaxis controller has also been exposed to Linux and Windows,[20] but no driver seems to have been successfully created yet that exposes its accelerometer functionality, except for Motioninjoy. However other drivers have successfully used it as a controller for gaming etc.
In May 2008, a vulnerability was found in the PlayStation 3 allowing users to install a partial debug firmware on a regular console. However, the debug functionality is disabled, so neither homebrew applications nor backup games can be run yet.
Another exploit was found on August 14, 2008, allowing users to boot some backup games from the PlayStation 3's HDD, although the exact instructions on how to do this were not released at that time. However, a different person posted instructions 10 days later, which explained the exploit.[21]
On January 6, 2009 a hacking ring known as the "Sh4d0ws" leaked the jig files needed to launch the PlayStation 3 into service mode. Although the PlayStation 3 can be triggered into service mode, it is not yet of any use because the files needed to make changes to the console have not been leaked.[22]
On August 31, 2010 PSGroove, an exploit for the PS3 through the USB port, was released and made open source. This exploit works on all of the PS3 models released up until then.[23] A guide for the creation of the PSGroove is available through several online sources.[24]
George Hotz, better known under his nickname "geohot", has recently appeared on Attack of the Show because he released the PlayStation 3's encryption keys, therefore any homebrew or custom firmware can be signed. Once signed, homebrew can be natively run. It would be difficult for Sony however to fix this because it would most likely require a voluntary recall and the most expensive parts would have to be replaced.[25] In 2011, Sony, with help from law firm Kilpatrick Stockton, sued Hotz and associates of the group fail0verflow for their jailbreaking activities. Charges included violating the DMCA, CFAA, Copyright law, and California's CCDAFA, and for Breach of Contract (related to the PlayStation Network User Agreement), Tortious interference, Misappropriation, and Trespass.[26]
Wii

In advance of the Wii's release, WiiCade was the first site to host Adobe Flash homebrew games specifically designed for the Wii and its remote.[27] The Wii was hacked via a custom serial interface in December 2007.[28] Though Nintendo would attempt to patch the console, the Wii Homebrew Channel could be installed to let users play homebrew games on the console. Its first full release was in December 2008.[29] The Wii Opera software development kit let developers make their own games in JavaScript.[30] The console's controller was also a popular target for modification.[31]
GP32
The GP32 by GamePark could run homebrew software through a special firmware which required the user to register on Gamepark's website, which also hosted some homebrew software.
GP2X
The GP2X, GP2X Wiz, and Caanoo by Gamepark Holdings are fully dedicated to running homebrew software, and require no modification to do so.
Pandora
The Pandora is able to run homebrew software from almost any source, such as SD cards, USB hard disks and flash drives, and wireless shares. It is also capable of compiling its own software internally using the GNU compiler collection.
Gizmondo
The Gizmondo was cracked in early 2006. Because Tiger Telematics, the creator of Gizmondo, is bankrupt, a small fan base provided a fair amount of homebrew applications and emulators.
Eighth-generation consoles
Nintendo 3DS
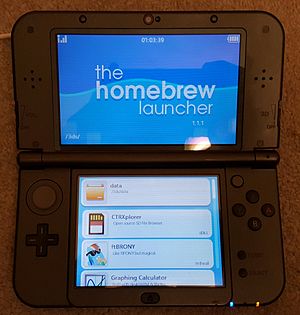
Several different exploits for running unsigned software exist. The first public exploit, Ninjhax (developed by smealum), allows the user to scan a QR Code to exploit the game Cubic Ninja. The first version of this exploit called Ninjhax 1 was able to run unsigned userland code on system versions 4.0 to 9.2 with the Homebrew Launcher being able to be loaded through the exploit on system versions 9.0 to 9.2.[32][33] This version uses a system exploit that was patched in system version 9.3 called rohax. The second version of the exploit called Ninjhax 2 works on system versions 9.0 and above and uses a different exploit than Ninjhax 1 that has less system permissions but still grants userland access.[34] However, Ninjhax 2 was patched in system version 11.0, as the update booted the game in a PALSR (physical address layout space randomization) mode and revoked the game's access to the system's http:C and soc:U services, which are required by the exploit itself to download the necessary payload files required to run the Homebrew Launcher.[35] A new version of Ninjhax 2 has been announced by Smea that will bypass these patches, and as a result it will work on system versions 11.0 and above. However, the new exploit will require scanning 13 QR codes instead of 1 QR code and has not been released yet.[36] Later exploits use the games The Legend of Zelda: Ocarina of Time 3D and the Deluxe edition of Freakyforms: Your Creations, Alive! and currently work on the current system version.[37] Both of these exploits were temporarily patched in 11.0 and 11.1 respectively due to the updates booting these games into a PASLR mode.[35][38] However, both of these exploits now work on system versions 11.0 or higher due to exploit updates that bypassed the PASLR mode. A few other exploit games include VVVVVV,[39] Citizens of Earth,[40] Pokémon Super Mystery Dungeon,[41] and Pokémon Omega Ruby and Alpha Sapphire,[42] however all of these games were changed to launch in a PASLR mode in the 11.1 system update and as such they no longer work on current firmware.[38] If these exploits are updated to bypass the ASLR they will continue to work as exploit games on current firmware. A New 3DS exclusive homebrew exploit was found in the 3DS version of Super Smash Bros. for Nintendo 3DS and Wii U that works on current firmware but it is one of the most inconsistent and difficult to set up exploits, as it requires Linux, an older cartridge version of the game without game update 1.1.3 or higher preinstalled, and the ability to broadcast raw wi-fi beacons.[43] Exploits were also found and developed for the free downloadable game IronFall: Invasion, the web browser and the downloadable YouTube application,[44] but these exploits were later patched, with the browser exploit in particular being patched in the 10.6 and later the 11.1 system update, and the IronFall: Invasion exploit called Ironhax patched for good in the 10.4 system update. Another exploit used a BASIC interpreter application called SmileBASIC (a sequel to the DSiWare and DS game Petit Computer) that could be downloaded from the 3DS eShop. The exploit could be used on versions 3.2.1[45] and 3.3.1[46] of the application. SmileBASIC was briefly taken down from the North American eShop between July 11, 2016 and August 10, 2016 due to the exploit.[47] The exploit was patched in version 3.3.2 of the application,[47] but was fully patched in system version 11.1 as the application in this system version and above is not allowed to launch unless it is updated to 3.3.2 or above, thereby patching the exploit for good.[38] One exploit can use the 3DS Home Menu itself as an exploit to run homebrew,[48] but this was patched in the 10.6 system update and again in the 11.1 system update. The most recent exploits that have been released are steelhax, a homebrew exploit using the game Steel Diver: Sub Wars,[49] and Stickerhax, a homebrew exploit in the game Paper Mario: Sticker Star.[50] Both of these exploits work on current firmware. Unsigned software can be launched from the SD card by using a program that takes advantage of these exploits known as "The Homebrew Launcher," similar to the Homebrew Channel on the Wii. The Homebrew Launcher itself can only be launched on system versions 9.0 or above. However, only custom software can be launched this way and only with limited permissions, meaning this software cannot be installed or run on the 3DS system menu or used to install or run unsigned native 3DS software. There are exploits that can bypass these limitations, but they require specific versions of the 3DS firmware that are no longer distributed.
In December 2015, a new exploit (memchunkhax2) was developed that allows downgrading the 3DS firmware from version 10.3 or lower to an earlier, more vulnerable version without requiring a hardware modification or a NAND dump.[51] An updated version of the exploit (memchunkhax2.1 or svchax) was released in March 2016 that also works on system versions 10.4-10.7. The downgrade is typically accomplished using one of several modified versions of the sysUpdater homebrew application that incorporates the exploit to gain the requisite access. The process can result in bricking due to the inherently dangerous nature of modifying the core system software and the relative complexity of the process. However, the downgraded firmware has access to exploits that allow launching emulated, patched versions of the 3DS system software from the SD card instead of from system memory. This custom firmware can be used to install and run unsigned homebrew content or native software titles (signed or unsigned) directly on the 3DS home menu. However, this exploit was patched in the 11.0 system update for the 3DS, so for updated systems on 11.0 or higher, either a hardware modification or a software exploit called a DSiWare downgrade must be used to downgrade the NATIVE_FIRM of the console to 10.4 so svchax can be used to downgrade the system to the desired system version. Currently, via software means, the system can be downgraded via the usage of Fieldrunners, Legends of Exidia, or Guitar Rock Tour - all of which utilize an exploit in Nintendo DSi software , which allows the ability to read and write anywhere to the NAND (the system memory). This is exploited via a process in which a legitimately purchased copy of these DSiWare games is system transferred along with a hacked save from a hacked console to an unhacked console. When the system transfer is complete, the hacked save of the DSiWare game can be used on the unhacked console to dump and downgrade the NATIVE_FIRM of the stock console to 10.4, which allows software downgrading. The console will then be able to downgrade to the desired system version through usage of a version of the sysupdater homebrew application that is able to run via the Homebrew Launcher. Guitar Rock Tour and The Legend of Zelda: Four Swords Anniversary Edition, which both can be used for this exploit, have not been available for purchase on the eShop for a long period of time. However, Fieldrunners, the cheapest DSiWare game that can utilize this exploit, was taken down from the eShop in all regions on November 22, 2016. However, Legends of Exidia is still available for purchase on the eShop and can still be used as an exploitable DSiWare game.
Wii U
The Wii U currently has homebrew execution in both the PowerPC kernel and the ARM9 kernal (nicknamed IOSU by the community). The most common way to execute code on the Wii U is through vulnerabilities in the Wii U's built in web browser app. Other exploits, such as haxchi, launch PowerPC and/or ARM9 kernel homebrew directly from launching a specific DS Virtual Console game with the exploit installed. It is essentially the first "coldboot" exploit on the Wii U, because the only thing required to run homebrew launcher or launch specific applications typically booted from the Homebrew Launcher (such as CFWBooter, a redNAND launcher), is to launch a DS game with the haxchi exploit installed from the HOME menu. There is a dedicated homebrew launcher for the Wii U that can be loaded through an exploit in the internet browser or via haxchi. Many homebrew applications that run via the homebrew launcher have been collected and hosted on wiiubru.com, which has a layout similar to that of the Wii U's own menu. These hosted applications can be downloaded sirectly on the Wii U using the HB App Store app in the repository.
On system firmware versions between 2.0.0 and 5.3.2 (inclusive), C language code is compiled using devkitPPC and embedded in a webpage with JavaScript code that triggers a bug allowing the C code to be run.[52] This exploit only allows user-land permissions, meaning that only basic games and software can be created. This is because the code is running within the confines of the web browser, which doesn't use the SD Card port or filesystem, and as such the homebrew running in the browser cannot use those features either.
On system firmware versions 5.4.0, 5.5.0 and 5.5.1, an exploit is available that allows a specially-crafted MP4 video file to run code within the browser.[53] Once again, this only allows user-land permissions, and does not allow access to any hardware that the browser doesn't use. Due to the nature of this exploit, a developer can only use up to 21.5kB of code in an MP4 file, otherwise the browser will crash trying to execute it. An ELF loading mechanism has been released,[54] which allows the code to be stored in a dedicated file (which can be of a much larger size) and loaded separately.
Firmware versions 5.5.1 and lower also have access to a PowerPC kernel exploit that runs inside the browser. It uses a race attack to install a custom driver on the Wii U, in turn allowing access to basic backup launchers, game modifications and cheat code handlers. It does not allow full access to the system, as the IOSU security processor is not compromised as part of this process. A PowerPC kernel exploit for firmware versions 5.5.0 and 5.5.1 has been developed, it was leaked and was subsequently released.[55] Before the kernel exploit for 5.5.0 and 5.5.1, the only way to get kernel access on a Wii U was to have a console on 5.3.2 and utilize the osdriver exploit present on that system version. However, since the new 5.5.0 and 5.5.1 kernel exploit is much more reliable than the old osdriver exploit, the new exploit is always used, even on older system versions.
An exploit against the Wii U's IOSU security co-processor has been officially released by the Wiiubru team,[56] and allows unrestricted access to the system, such as the dumping of the Wii U console unique OTP file, which contains unqiue console encryption keys and Wii U Common Keys stored in the ARM9 kernel. A boot-time exploit that allows custom firmware and operating systems on the Wii U to run immediately on console boot has been announced.[57] However, the function of creating and booting a redNAND is already possible by using a NAND dumper to dump the Wii U NAND to the SD card and then using a file called fw.img and CFWBooter to launch redNAND from the NAND backup. A redNAND is able to install any title, including unofficial titles and titles without valid signatures. However, there are some disadvantages to redNAND, as the vWii mode does not currently work in redNAND, and it is unknown how a future system update could affect redNAND, as it does not currently emulate the SEEPROM save chip in the Wii U. As a result, an alternative to redNAND has been created to accomplish the same exact results on sysNAND called CFW sysNAND. This is launched the same way as redNAND (boot fw.img from the SD card using CFWbooter), but it uses a different fw.img than the one used for booting redNAND. This actually allows more features than redNAND, such as the installation of vWii games through unofficial means. All of the current fw.img files commonly used also allow editing of files stored on the Wii U via an internet connection and a client called wupserver or wupclient. This server connection allows the installation of haxchi and allows allows the changing of the console region to make a Wii U region free. However, since this has full access to the console, it also can brick the console easily if not carefully used.
The Wii U's built-in Wii emulator (often nicknamed vWii) is capable of running Wii homebrew, and also allows installation of the Homebrew Channel.[58] However, the virtual Wii is much more fragile than a classic Wii console and has a higher chance of being bricked if dangerous software is used. Also, due to the updated patches, previous exploits that utilized the HOME menu itself to load the HackMii Installer, such as Letterbomb, do not work on vWii. However, exploits that launch the HackMii Installer via a game still work on vWii. The only way to hack vWii without one of the exploit games is using IOSU, using an exploit called wuphax. Wuphax uses the same client used to install Wii U exploits such as haxchi to temporarily load the HackMii Installer from the SD card when loading the Mii Channel. Users can then run the HackMii Installer to install the Homebrew Channel to their vWii. After installing the Homebrew Channel to the vWii, the modification to the Mii Channel is no longer needed and can be restored back to normal using a client script.[59]
See also
References
- ^ a b Winterhalter, Ryan (April 29, 2011). "31 Homebrew Games Worth Playing". 1UP.com. Retrieved December 12, 2013.
- ^ "Odball for Magnavox Odyssey Official Page". Revrob.com. 2010-08-04. Retrieved 2012-04-03.
- ^ "Dodgeball – Magnavox Osyssey". Atari2600Land.com. 2012-07-17. Retrieved 2012-07-17.
- ^ "Mentis Cohorts – A Board Game and Video Game All-In-One for Magnavox Odyssey". Revrob.com. 2012-07-16. Retrieved 2012-07-17.
- ^ "Free Magnavox Odyssey Homebrew – Red vs. Blue". AtariAge. 2012-07-19. Retrieved 2012-07-19.
- ^ "Sean Riddle's Home Page – Channel F info". Seanriddle.com. 2004-06-16. Retrieved 2012-04-03.
- ^ "AtariAge – Atari 2600 Programming". AtariAge.com. Retrieved December 27, 2007.
- ^ "PowerPak – RetroZone". Retrousb.com. Retrieved 2012-04-03.
- ^ NGDevTeam.com
- ^ "Hasbro release Jaguar Publishing Rights".
- ^ http://dextrose.64scener.com/0428turok3dev.htm
- ^ EverDrive 64
- ^ "64drive by Retroactive".
- ^ Agnello, Anthony John (November 19, 2013). "Back from the dead: 9 modern games for obsolete consoles". The A.V. Club. Retrieved December 12, 2013.
- ^ "PSPSLIMHACKS". PSPSLIMHACKS.com. Retrieved 2007-08-17.
- ^ "/Download". Wololo.net. Retrieved 2008-08-03.
- ^ "My free PSP, VITA and DS homebrews!". FouadtjuhMaster. Retrieved 2013-01-03.
- ^ "Weekly PSP homebrew news". pspcustomfirmware.com. Retrieved 2008-06-19.
- ^ "Sony blocks OtherOS in firmware 3.21". Retrieved 2012-04-14.
- ^ "Sixaxis driver for Windows XP".
- ^ "How to run a PS3 game backup".
- ^ "PlayStation 3 Service Mode JIG Set-Up Files Leaked!".
- ^ "Open Source PS JailBreak Clone "PSGroove" Available Now! | PS3-Hacks :: Hack your PlayStation 3". PS3-Hacks. Retrieved 2012-04-03.
- ^ "Web hosting, domain name registration and web services by 1&1 Internet". Howtohackps3.com. Retrieved 2012-04-03.
- ^ "Geohotz Page".
- ^ Sony follows up, officially sues Geohot and fail0verflow over PS3 jailbreak. Nilay Patel, Engadget (2011-01-12). Retrieved on 2011-02-16.
- ^ "For your enjoyment: WiiCade".
- ^ Wilson, Mark. "Nintendo Wii Hacked, The Video".
- ^ "Wii Homebrew Channel turns 1.0".
- ^ "Revolutionary: Web Wii Wares".
- ^ Brophy-Warren, Jamin (29 April 2007). "Magic Wand: How Hackers Make Use Of Their Wii-motes" – via Wall Street Journal.
- ^ "smealum/ninjhax".
- ^ https://web.archive.org/web/20160511191439/http://smealum.net/ninjhax/
- ^ "ninjhax 2.7 - 3DS homebrew loader".
- ^ a b "11.0.0-33 - 3dbrew".
- ^ "smea on Twitter".
- ^ "Homebrew Exploits - 3dbrew".
- ^ a b c "11.1.0-34 - 3dbrew".
- ^ "SALT - (v*)hax".
- ^ "SALT - humblehax".
- ^ "SALT - supermysterychunkhax".
- ^ "basehaxx".
- ^ "yellows8/3ds_smashbroshax".
- ^ "The Homebrew Launcher - 3DS".
- ^ "BASICSploit by MrNbaYoh".
- ^ "smilehax - 3DS homebrew exploit".
- ^ a b "What's New".
- ^ "yellows8/3ds_homemenuhax".
- ^ "Sup".
- ^ "yellows8/stickerhax".
- ^ "Console Hacking".
- ^ "Build system and examples for running C code on the Wii U". 4 March 2015. Retrieved 20 February 2015.
- ^ "Wii U libstagefright exploits". 13 January 2016. Retrieved 20 February 2016.
- ^ "5.5.X ELF Loader". 12 February 2016. Retrieved 20 February 2016.
- ^ "Wii U Hacking & Homebrew Discussion". 13 January 2016. Retrieved 20 February 2016.
- ^ "Wiiubru on GBATemp". 22 October 2016. Retrieved 17 November 2016.
- ^ "wii u: coldboothax, redNAND, homebrew (WIP)". 8 February 2016. Retrieved 20 February 2016.
- ^ "WiiMode". 3 February 2016. Retrieved 20 February 2016.
- ^ http://gbatemp.net/threads/wuphax-hacking-vwii-with-iosuhax.446786/
