Wikipedia:Reference desk/Computing
of the Wikipedia reference desk.
Main page: Help searching Wikipedia
How can I get my question answered?
- Select the section of the desk that best fits the general topic of your question (see the navigation column to the right).
- Post your question to only one section, providing a short header that gives the topic of your question.
- Type '~~~~' (that is, four tilde characters) at the end – this signs and dates your contribution so we know who wrote what and when.
- Don't post personal contact information – it will be removed. Any answers will be provided here.
- Please be as specific as possible, and include all relevant context – the usefulness of answers may depend on the context.
- Note:
- We don't answer (and may remove) questions that require medical diagnosis or legal advice.
- We don't answer requests for opinions, predictions or debate.
- We don't do your homework for you, though we'll help you past the stuck point.
- We don't conduct original research or provide a free source of ideas, but we'll help you find information you need.
How do I answer a question?
Main page: Wikipedia:Reference desk/Guidelines
- The best answers address the question directly, and back up facts with wikilinks and links to sources. Do not edit others' comments and do not give any medical or legal advice.
June 23
Running program for Unix-based OS
Can I run softwares for Unix-based operating system on Windows?125.235.100.105 (talk) 01:07, 23 June 2011 (UTC)
- That's a complicated question.
- The short version is that most unix-only software will not run natively on Windows, however if the software you're looking to use is open-source, it's very likely that someone has made a windows version of it.
- And, in a worst case scenario, you could probably install linux within a "virtual machine" on your windows machine, though that would probably be more trouble than it was worth.
- If you can tell us what software you're specifically interested in we may be able to help. APL (talk) 03:35, 23 June 2011 (UTC)
- It's not that difficult to install a linux distribution as a virtual machine in Windows. I think it's possible with the Microsoft Virtual PC and I know it's possible with Oracle VirtualBox. I have 3 Ubuntu virtual machines running on VirtualBox.--Phil Holmes (talk) 08:08, 23 June 2011 (UTC)
- The software I looking for use is a platform that run Unix-based softwares on Windows, like Wine that run Windows software on Unix-based operating systems. 125.235.100.158 (talk) 09:23, 23 June 2011 (UTC)
- That's co-linux. You can download a compressed image of a 1GB file system running Ubuntu for it. Extending the image is a bit of a pain - you are probably better off creating a second image for storing your documents (/home). You should also install an X-server if you want to run graphical programs. cygwin's or mingw's ones is probably the easiest. Ask here again if you need advice to set it up. CS Miller (talk) 12:07, 23 June 2011 (UTC)
- The software I looking for use is a platform that run Unix-based softwares on Windows, like Wine that run Windows software on Unix-based operating systems. 125.235.100.158 (talk) 09:23, 23 June 2011 (UTC)
- It's not that difficult to install a linux distribution as a virtual machine in Windows. I think it's possible with the Microsoft Virtual PC and I know it's possible with Oracle VirtualBox. I have 3 Ubuntu virtual machines running on VirtualBox.--Phil Holmes (talk) 08:08, 23 June 2011 (UTC)
There's always Cygwin. It provides a Unix-basd compatibility layer on top of Windows. You can start Cygwin as a normal Windows program, and it presents you with a Unix shell. It's not an emulator - that shell is running directly on Windows. You can traverse your own Windows file system through the Unix shell interface, to read and write files. You cannot run Unix binaries from "real" Unix distributions like Linux, Mac OSX or Solaris, but you can get Unix-based source code and compile it in Cygwin, which will then result in completely native Windows binaries that can be run from inside Cygwin. JIP | Talk 19:15, 23 June 2011 (UTC)
Ubuntu: Command + ` OSX equivalent?
On the Mac, I use Command + ` (the tilda) to cycle through windows in the current application (eg terminal or chrome). It's like alt + tab except only for the current application's windows. I also don't want any flashy graphics like exposee or anything. Is there anyway to do this on Ubuntu (possibly on compiz?)? Thanks! — Preceding unsigned comment added by Legolas52 (talk • contribs) 04:35, 23 June 2011 (UTC)
- Try CTRL+TAB, CTRL+SHIFT+TAB, CTRL+PGDN, CTRL+PGUP. You can make ⌘+` mapped to any of these. ¦ Reisio (talk) 06:57, 23 June 2011 (UTC)
- On my Ubuntu set up: CTRL+ALT+LEFT or CTRL+ALT+RIGHT cycles through the workspaces; ALT+TAB cycles through the windows in the current workspace (minimised windows stay minimised but still have a place in the cycle); CTRL+TAB cycles through the tabs on the currently active window. Astronaut (talk) 12:38, 23 June 2011 (UTC)
Torrents
My torrent is apparantly downloading, but olny 6.5% has been done and it isn't making any progress after that. Its ETA displays the infinity symbol. Do I have to wait some more or move to a different location or country to get more data? What are ways to speed up a torrent download, or at least not make its ETA be infinity? 72.235.230.227 (talk) 05:35, 23 June 2011 (UTC)
- Usually indicates that the only person/s who were seeding it are not presently online or available. If you leave it attempting to download eventually they'll probably get back online, though eventually many torrents do "die" (lose all seeders). Most likely the same time tomorrow you'll get similar download speeds. ¦ Reisio (talk) 07:00, 23 June 2011 (UTC)
- Depending on your torrent program, you can usually tell how many complete copies there are on the network by clicking around a bit. If it is less than 1, you won't be able to complete the download unless more seeders come online. Starting up torrents that have very low numbers of seeders is a recipe for stalled torrents. --Mr.98 (talk) 14:26, 23 June 2011 (UTC)
- Maybe your peers or peer don't have the complete film either, and will never have, since new downloaders just pass around the pieces that they have. No need to speed torrents up, just go for healthy torrents; they'll give you at least 200 kb/s download rate. Wikiweek (talk) 14:37, 23 June 2011 (UTC)
MS Outlook 2007
I have just bought a new home computer and installed Outlook 2007. I have set up mail accounts exactly as they are already set up on my office computer. This seems to work perfectly well in terms of receiving incoming mail. However, whenever I try to send an email it immediately bounces back to me as undeliverable. I get the following error message: 553 sorry, that domain isn't in my list of allowed rcpthosts. I am hopelessly non-technical. Can anyone explain in words of one syllable how I can fix this problem? Thanks for any help. Maid Marion (talk) 09:38, 23 June 2011 (UTC)
- If (as seems likely) you're using your work's email servers then they may be configured so as only to allow mail to be sent from certain IP addresses, so as to prevent spammers and other evildoers using them as SMTP relays. I'd suggest asking your IT department for advice on how to get around this. Edit: Thinking about it a bit more, the details of my answer may be wrong, but I still think the advice of asking the IT dept is valid. AndrewWTaylor (talk) 10:01, 23 June 2011 (UTC)
- Thanks for trying Andrew, but there is no IT department. I am just a solitary individual, working sometimes from home, sometimes from a tiny office. The server that hosts my email and website is provided by a third party - I just pay an annual rental for this. Does your answer mean that I need to contact the outside third party? Problem with this is that I am not a high priority for them and I may get no response. Any simpler solution possible? Maid Marion (talk) 10:21, 23 June 2011 (UTC)
- Googling an error message is normally a good way to get answers. You could have a look at these[1][2][3][4][5] There are a variety of possible causes, and it will depend on your mail server and other settings. One common cause is that you may have configured your email settings incorrectly in Outlook.
- Most ISPs and web hosting company provide extensive online help pages or forums that you can search or post to. You should certainly try emailing them; many use semi-automated systems to respond to emails, so they may reply by pointing you to their website or other useful information, even if you do not get a response from a human being. --Colapeninsula (talk) 10:56, 23 June 2011 (UTC)
- Many thanks Cola. Those links provide a mine of information. I will try their suggestions when I get home this evening. If they don't work, I'll be on my knees again asking for further help tomorrow! Maid Marion (talk) 11:09, 23 June 2011 (UTC)
- In my experience the majority of Outlook outgoing e-mail problems come from issues with the outgoing server port or SSL settings. First thing I'd try is to set the outgoing server port to 587 or 465 (try both). Accounts>Your email account>more settings. Depends on if your account needs SSL or not but many ISP's are blocking port 25 these days. That setting can be affected by who you are using for an ISP. The SSL less so, but it will still be worth trying to adjust the outgoing SSL settings as well. RxS (talk) 13:50, 23 June 2011 (UTC)
- Many thanks Cola. Those links provide a mine of information. I will try their suggestions when I get home this evening. If they don't work, I'll be on my knees again asking for further help tomorrow! Maid Marion (talk) 11:09, 23 June 2011 (UTC)
- Given the fact that you get a proper error message, firewall or port filtering does not seem to be an issue. You can try setting the SMTP port to 587 and to enable authentication, but this will only help if your work ISP has actually configured their outgoing email server (SMTP) to accept authenticated cnnections from users that are not directly connected to them. A lot of ISPs will not bother setting things up that way. As a spam prevention measure, most SMTP servers only allow IP addresses of their own customers to send mail through them. So when at work, you should use the work SMTP server. At home, you should set the SMTP server to the one provided by your home ISP. Unilynx (talk) 06:12, 24 June 2011 (UTC)
- Many thanks to all of you - the usual fantastic Wikipedia response. The problem is now solved. I followed one of the suggestions in Cola's links and simply checked a box on my outgoing server settings saying 'Use same settings as incoming server'. It worked like a charm. Thanks again everyone. Maid Marion (talk) 10:03, 24 June 2011 (UTC)
Secure VPN + Insecure (W)LAN
If you want to connect to the Internet using a (W)LAN that you don't trust, would a secure VPN make it considerably secure? Or would it always be possible for an attacker controlling the (W)LAN (or some link above that) to pretend he is your VPN - forwarding all traffic passing through him? Wikiweek (talk) 14:34, 23 June 2011 (UTC)
- When you sign up for a VPN they send you their cryptographic certificate and on subsequent connections your VPN client verifies the identity of the VPN using that. With that working properly, a man-in-the-middle attack wouldn't succeed. The danger point is that initial key exchange. For that you most often rely on public SSL certificates which your browser verifies against the SSL certificate authorities that it knows about a priori. Good VPN providers go to great lengths to make sure you get the correct certificate and not one that's been altered in transit - if memory serves the last time I signed up for a VPN they read the certificate fingerprint to me (in hex) over the phone. This isn't foolproof (certificate authorities can, in theory, be compromised, for example) but it's much more elaborate than simply putting a fake VPN inline between you and the real internet. -- Finlay McWalter ☻ Talk 14:42, 23 June 2011 (UTC)
BrowserChoice.eu - does it really work like this?
This isn't really a problem as such: more a peculiar thing that I wonder if I've understood correctly.
I've recently had to completely wipe my hard-drive and start again from scratch. So, I've got my old copy of Windows XP and am slowly going through the many, many critical updates in sequential order. One of these is the Browser Choice thing, and I make my browser choices, none of which are Internet Explorer. All seems well, and all trace of Internet Explorer seems to be gone.
But then, I go to clean my start-up folder (it comes preloaded with things like Messenger), and notice BrowserChoice.exe, which I unselect. When my computer restarts, all the Internet Explorer shortcuts are back and an Internet Explorer folder containing (among other things) the connection wizard and Internet Explorer itself has appeared. The folder cannot be deleted, because something in it is too important. If Internet Explorer is deleted, it recreates itself by the time you look in the folder again. The shortcuts can be redeleted, but are put back in all their places when you restart. When I reselect BrowserChoice.exe in the start-up folder, this behaviour stops and Internet Explorer again appears to have gone. Except that, when the only browsers I had chosen were Firefox and Opera, if I click on the 'check for updates' thing in the Security Centre, it uses Internet Explorer (which it otherwise pretends has been removed) to open the webpage. Once I installed Maxthon 3 (which uses the same engine (?) as Internet Explorer), it used that instead.
So, my understanding is that, in order to comply with the directive on provided browser choice, rather than providing a patch which deleted Internet Explorer in any way, Microsoft wrote a patch that put an exe in my start-up folder, which runs every single time I start my computer, to supress Internet Explorer from restoring all the shortcuts, and somehow hides Internet Explorer, while leaving it installed and available to the system to open a specific webpage. Is this accurate? Is it actually impossible to delete Internet Explorer from Windows XP?
And, if Internet Explorer is somehow completely embedded into the system, am I opening myself up to any problems if I don't download and install the various patches for Internet Explorer which the system keeps offering me, even after I selected not to be told about them again? I'd assumed I wouldn't need them, since I don't have or use Internet Explorer, but if it's inextricably twisted into everything else, I wonder if there will be unfortunate consequences of not updating it. 86.164.66.52 (talk) 18:44, 23 June 2011 (UTC)
- The bulk of Microsoft's web browser is a GUI widget that can be used by any application. It is technically possible to delete it, but not useful because it breaks too much software. You can probably delete iexplore.exe, which is a wrapper around the widget, but you'll save hardly any disk space that way. It makes more sense to just delete the shortcuts and forget that it's there, just like the the hundreds of other small utility programs that you never use. You do need to install security updates to "Internet Explorer" because they are really updates to the browser widget.
- I've never encountered BrowserChoice.exe, which is apparently a fairly new, Europe-only thing. I've never noticed IE shortcuts being automatically recreated, but I'm not sure I've ever tried to delete them. -- BenRG (talk) 00:04, 24 June 2011 (UTC)
- This Technet blog entry from Microsoft explains what it does. It doesn't say it uninstalls Internet Explorer. Astronaut (talk) 11:43, 24 June 2011 (UTC)
Thank you, these were helpful answers that told me what I needed to know. I'm glad I poked around! I don't quite understand how Internet Explorer is a wrapper on a GUI widget, given what our article on GUI widget seems to describe, but I can understand it being a generic bit of software used by lots of programs. So, thanks muchly. 86.164.66.52 (talk) 16:20, 25 June 2011 (UTC)
Restarting the display in Linux
Hello. I have two questions:
- I'm running Debian Linux 6.0 on one of my computers. I have it set to not run gdm on bootup, so I boot right to the terminal and then run
startxif I want to work in Gnome. That's been working fine until recently; now when I run$startx, it cuts to a screen that is completely blank except for a cursor and doesn't display anything no matter how long I wait. Even odder: I ran#gdmas root, which is supposed to bring up a login screen (but the same thing: blank screen with a cursor). Without seeing anything, I typed in my username, password, and hit enter, Alt+F1'd back to the terminal, ranps aux, and saw that all the processes where running in Gnome under my uid indicating a successful login, even though the screen is blank. Is this problem easily corrected? It seems that everything is working okay except actually displaying the desktop on the screen. - Since I couldn't logout of the desktop since I could not see it, I killed all the processes affiliated with Gnome at the terminal. When I Alt-F7'd to check that the mouse had disappeared and that there was no trace of Gnome, the screen froze. It's frozen on the old
ps auxlisting and won't let me change terminals (or do anything, for that matter). I connected with PuTTY over SSH, logged in, and everything is working fine. I logged out my frozen session through PuTTY, but the screen is still frozen. I tried Alt+F'ing to a different terminal, and even though it was frozen, I typed my username and password, and calledps auxon PuTTY and it confirmed the login—despite the frozen screen—was successful. So, is there any way to restart or resynchronize whatever is responsible for displaying the terminal to screen?
PS I'm running some lengthy processes on my Linux box that I'd rather not have to shut it down and re-run them. That would be okay if it's necessary, but I figured I'd take the time to learn a little more about Linux, too, since it seems the only problems I'm having are with the display, which may be easily fixable. Thanks!--el Aprel (facta-facienda) 21:52, 23 June 2011 (UTC)
- http://webchat.freenode.net/?nick=brokenX&channels=#debian ¦ Reisio (talk) 22:58, 23 June 2011 (UTC)
Samsung Galaxy S II release date in China?
Can someone help me find the Galaxy S2's China release date? I'm having some trouble... The Masked Booby (talk) 22:30, 23 June 2011 (UTC)
Laptop design
Hello, why is it that new laptops tend not to have a screen that locks into the keyboard when closed ? The screen just sits loosely on it. — Preceding unsigned comment added by 41.141.77.57 (talk) 23:55, 23 June 2011 (UTC)
- It isn't clear to me what value such a lock would have -- and if you had one and it jammed, you'd have a problem. Looie496 (talk) 00:39, 24 June 2011 (UTC)
- Apple's design aesthetic is the actual answer to your question. ("why is it that new laptops tend to not have a screen that locks into the keyboard when closed".) --188.29.15.168 (talk) 01:20, 24 June 2011 (UTC)
- Because without a lock, or some sort of springy firmness the two halves rattle against each other when closed.
- I don't know know why they don't have latches anymore, but I suspect that it's a combination of better hinges and style. APL (talk) 01:29, 24 June 2011 (UTC)
- Eh, in my experience, the hinges tend to be so bad you don't need the lock - you have to use more than one hand to open them regardless. The answer is, of course, that it is the current trend. The bulk of electronics are not designed to consumers' wants, but to consumers' present expectations (which trend low). ¦ Reisio (talk) 02:55, 24 June 2011 (UTC)
- The hinges aren't "bad", they're intentionally stiff, so the laptop will stay as opened or closed as you left it. StuRat (talk) 05:03, 24 June 2011 (UTC)
- Yeah, they're bad. ¦ Reisio (talk) 05:22, 25 June 2011 (UTC)
- The hinges aren't "bad", they're intentionally stiff, so the laptop will stay as opened or closed as you left it. StuRat (talk) 05:03, 24 June 2011 (UTC)
- From my laptop owning experience the latch-mechanism is one of the weaker/less reliable parts of the construction. My current laptop uses magnets to hold the lid closed. This works extremely well and is (in my eyes at least) 100% better than any latch mechanism. ny156uk (talk) 05:04, 24 June 2011 (UTC)
- Just to illustrate this, Apple's iBook G4s had hinge locks which, if broken, necessitated replacing the entire top frame of the laptop, which was neither a cheap nor an easy piece to replace. (Or using velcro or other ersatz solutions.) --Mr.98 (talk) 12:50, 24 June 2011 (UTC)
June 24
2 x 500 GB (WD) or 1 x 1 TB (Toshiba)
Either option costs the same. Which is a better choice as external HD? Wikiweek (talk) 22:03, 24 June 2011 (UTC)
- I would go for the two 500GB drives; that way if one fails you only lose half your data, instead of losing everything if the 1TB fails. AvrillirvA (talk) 22:23, 24 June 2011 (UTC)
- Note that there are probably other factors here — specific models have better failure rates than other, different rotational speeds mean different data access, etc. A pro-tip is to check each specific model on newegg.com first; they're a very reliable place, and you can usually tell which drive models are lemons pretty quickly. --Mr.98 (talk) 22:26, 24 June 2011 (UTC)
- I'll check newegg, although I believe both WD and Toshiba are serious manufacturers. I thought also that the formating of the two smaller HDs will occupy more space than of the bigger HD, right? Wikiweek (talk) 23:29, 24 June 2011 (UTC)
- In the USA, 2TB externals can currently be had for the same price as 1TB externals (I assume retailers overestimated how long it would be before cheap 2TB externals flooded the market). As AvrillirvA said, I wouldn't suggest getting one disk unless you already have a backup plan (another disk with enough space for data you care about), and I wouldn't suggest getting a 1TB because the 2TB models are the same price. ¦ Reisio (talk) 00:18, 25 June 2011 (UTC)
- My experience on newegg is that even with serious manufacturers, certain models have significantly different ratings than others. It's worth a check. --Mr.98 (talk) 23:40, 24 June 2011 (UTC)
- Different models can definitely have different failure rates even from the better manufacturers. The manufacturers know and probably large scale OEMs and other large companies with a lot of HDDs like Google but us peons don't tend to get access to such data. I'm not convinced looking at NewEgg is much use even more so if you can't buying from NewEgg so may have a completely different supply chain (particularly when it comes to internal HDDs a big reason for failures is probably damage in transport which depends on the supply chain). I don't know much about their methodology for calculating reliability but since it's rather unlikely we're talking about a random sampling here but instead a lot of self selection and user bias I'd suggest 10k minimum sample size per model before you get anything close to useful data which I'm not convinced they have. (I presume we're talking about some sort of NewEgg provided RMA rate not simply random user reviews which are typically next to useless for quantitative data particularly on things like reliability. Even the StorageReview reliability database is IMHO somewhat questionable and they at least try to turn user submissions into something approaching useful quantitative data on reliability.) Nil Einne (talk) 15:07, 25 June 2011 (UTC)
- I'm not claiming it is empirically rigorous. I'm just saying that when you get lots and lots and lots of people on Newegg saying "this thing blew up after two months" it tends to stand out, especially when there are also instances with lots and lots and lots of people saying, "have been using this for ages without any problems." I trust the Neweggers on the whole more than I do your typical Yelpers or Amazoners or whomever. --Mr.98 (talk) 23:18, 29 June 2011 (UTC)
- Different models can definitely have different failure rates even from the better manufacturers. The manufacturers know and probably large scale OEMs and other large companies with a lot of HDDs like Google but us peons don't tend to get access to such data. I'm not convinced looking at NewEgg is much use even more so if you can't buying from NewEgg so may have a completely different supply chain (particularly when it comes to internal HDDs a big reason for failures is probably damage in transport which depends on the supply chain). I don't know much about their methodology for calculating reliability but since it's rather unlikely we're talking about a random sampling here but instead a lot of self selection and user bias I'd suggest 10k minimum sample size per model before you get anything close to useful data which I'm not convinced they have. (I presume we're talking about some sort of NewEgg provided RMA rate not simply random user reviews which are typically next to useless for quantitative data particularly on things like reliability. Even the StorageReview reliability database is IMHO somewhat questionable and they at least try to turn user submissions into something approaching useful quantitative data on reliability.) Nil Einne (talk) 15:07, 25 June 2011 (UTC)
Onboard video card
I want to stop using the video card I brought some years ago, as I suspect it's malfunctioning, and use the onboard video card instead. However, if I connect the monitor to it, nothing happens (neither in windows nor while loading, as if the monitor was not connected to the PC). Do I have to actually remove the video card from the motherboard for the onboard video card to work, isn't there a way to shut it off and activate the other? Cambalachero (talk) 22:20, 24 June 2011 (UTC)
- I'm sure there's a way, but I can't think of a better way to stop using a malfunctioning card (or even help rule out whether it's that particular card that's malfunctioning) than physically removing it. ¦ Reisio (talk) 00:19, 25 June 2011 (UTC)
- You first make sure that the on-board video chips are turned on (access your BIOS, they might be disabled there for energy saving reasons, I
believehave now made sure that mine does have this option, I can switch for the onboard VGA adapter betweenonoff and auto; just for reference reasons, my BIOS is a PhoenixBIOS and the machine is some kind of Fujitsu-Siemens Scenic something... which I like by the way) and second make sure that you at least downloaded the necessary drivers for Windows to run on the on-board chips. Check back with us after you try this. --Ouro (blah blah) 07:17, 25 June 2011 (UTC) (Ouro (blah blah) 07:26, 25 June 2011 (UTC))
- You first make sure that the on-board video chips are turned on (access your BIOS, they might be disabled there for energy saving reasons, I
- You can often change the settings in the motherboard on whether to init the IGP or the external video card first. You may be able to use the IGP in Windows without changing this but it would be hard to do if you can't see anything. In any case I agree with Reisio, just remove the malfunctioning video card Nil Einne (talk) 14:54, 25 June 2011 (UTC)
Looking for an audio media player SOFTWARE
Which could let me play PLAYLISTS in FASTER playing rates. i tried with VLC media player and even asked the VLC support team, but in the current version, there is no working way to do so in a playlist (fasten) rather, only in single media files.
as mentioned, i look for a program WHO WILL (!) let me the option to do so (Fasten a playlist), for i could hear lot's of files faster than they originally played...
many thanks and blessings, would dear much for me!.
Beni. — Preceding unsigned comment added by 79.179.8.59 (talk) 22:54, 24 June 2011 (UTC)
- With MPlayer, the command would be
mplayer -speed 2 -playlist path/to/playlist/file. I checked SMPlayer for a convenient pref to pass-speedbut didn't see any place in a cursory examination; I'd be surprised if it weren't there, though (and actually I'd be surprised if you couldn't make VLC do it). The simplest way I know of using commandline mplayer on Windows is downloading this, and inside itscodecsdirectory, placing the contents of this. You can then add the directory to your path (or just dump it all intoC:\Windows\System32\) if you wish to, to be able to access it from acmdwindow at any location. ¦ Reisio (talk) 00:46, 25 June 2011 (UTC)
June 25
A Software which SEPERATES refrences from the main text of a scientific paper?
does anybody knows such a software?
blessings.
- there's hardware. or you could be more specific. --188.28.47.94 (talk) 00:15, 25 June 2011 (UTC)
grep, perl ¦ Reisio (talk) 00:49, 25 June 2011 (UTC)
- The questioner may be thinking about reference management software, such as Reference manager. --NorwegianBlue talk 11:20, 25 June 2011 (UTC)
Hello, indeed, i mean for the bibilography... if referance manager is the software who can separate the REF's from the paper than it is the software for me.
thanks. — Preceding unsigned comment added by 79.179.8.59 (talk) 12:47, 25 June 2011 (UTC)
disappearing link
I posted the following link on my web page, tested it, had several other people also test it, and it worked fine.
<a target="_blank" href="https://www.securedata-trans14.com/ap/stjohnthebaptistcatholicchurch5/index.php?page=10">
<img border="0" src="images/onlinebutton_2.jpg" width="156" height="111"></a>
Next thing I knew, people were calling in saying they clicked on the image and nothing happened. It was easy enough to fix, but what could have possibly caused the link to disappear (as shown on a cached version of the page)? --Halcatalyst (talk) 01:17, 25 June 2011 (UTC)
- What was it you did to "fix" it? ¦ Reisio (talk) 01:28, 25 June 2011 (UTC)
- Incidentally,
imgelements should not be used this way, you should use a CSS background image instead; and JPEG is for photographs (the 'P' stands for 'Photographic'). [andtarget="_blank"is just annoying] ¦ Reisio (talk) 01:33, 25 June 2011 (UTC)- I use a web editor, so I simply put the link address back in. I understand HTML well enough to inspect the code but not to employ it originally. --Halcatalyst (talk) 03:59, 25 June 2011 (UTC)
If the link wasn't there, then someone or something removed it. ¦ Reisio (talk) 05:24, 25 June 2011 (UTC)
- That's what I would think. However, it wasn't me, and no one else has access to the site. Can pages displayed on the Web be altered directly? I suppose it would be possible for a cracker, but I wouldn't think they would attack my little site. What about something mechanized? --Halcatalyst (talk) 19:32, 25 June 2011 (UTC)
PHP regular expression
How could i formulate a PHP regular expression to ensure that that there are no control characters in a string? Magog the Ogre (talk) 03:16, 25 June 2011 (UTC)
Addendum: silly me, I forgot to specify it's unicode. Magog the Ogre (talk) 03:32, 25 June 2011 (UTC)
Nevermind, I got this one. Magog the Ogre (talk) 07:16, 25 June 2011 (UTC)
Enquiry about purchase of Monitor Inverter
Hi all,
Currently I have experienced a number of monitor-error issues from my Toshiba laptop, of which the monitor backlight appearance is very blur, faded, and sometimes, discoloured. I wonder whether the primary problem lies either at the Monitor Inverter or at the monitor itself. As I want to try to get a displacement of the Monitor Inverter first rather than the more expensive TFT monitor, I'm about to order one at batterysupport.com.
So this is my doubt: is there any one here having experienced such a monitor-error relating issue like mine before? if yes, how have you been dealing with it? I can get the order online straightaway from batterysupport.com, but to the best of my knowledge, this company is based in China (maybe it's a Chinese company itself) which in turn gives me a second thought about making purchase from the site. Hence, I write here seeking more information regarding to the issue. Thanks in advance. — Preceding unsigned comment added by Predestination (talk • contribs) 03:57, 25 June 2011 (UTC)
- I've had problems with my laptop back-light going out entirely, so I use an external monitor now. This obviously reduces the portability somewhat, but will definitely fix the problem quickly, and, if you choose, you can get a larger and better monitor than you had. StuRat (talk) 17:11, 25 June 2011 (UTC)
Safe Mode in Windows XP
1) Does it make sense that a computer would run a LOT faster in safe mode than in regular?
2) I understand that some "functionality" is not available in safe mode. But if the computer is doing what I need done, is there any reason I could not or should not use safe mode all the time? Does it cause later problems for example?
Thanks, Wanderer57 (talk) 04:49, 25 June 2011 (UTC)
- unfortunately, Safe Mode is not designed for regular-utilization purpose, but for solving hardware or software conflicts instead. You can temporarily use it for urgent issues; however, in the long term you expose will yourself to vulnerabilitiesPredestination (talk) 05:19, 25 June 2011 (UTC)
- Some WP:OR... In my experience, safe mode is not always faster. One of the bits of "functionality" that may be disabled is disk caching, and that can have a serious impact on performance, depending on what you are doing. Mitch Ames (talk) 09:00, 25 June 2011 (UTC)
- Safe mode disables a lot, a lot of functionality for compatibility purposes, basically so that there is as little reason for the PC to crash as possible (hence the designation 'safe') so you can get your stuff together to fix it. It would probably be a lot of algos in the buttocks to use it long-term. If there's a specific problem you're encountering which hinders your ability to run Windows in normal (contrary to safe - unsafe?) mode, why not describe it here? --Ouro (blah blah) 13:25, 25 June 2011 (UTC)
- Thank you all. My naive assumption was that "safe mode" was called that because it was less suspectible to viruses and other malware from outside. Am I wrong about this?
- I went to safe mode while trying to find malcode (and the search programs did find Trojans).
- The computer has become slower over time. I found that in safe mode, the computer runs noticably faster. Does this speed difference give any clues as to why the computer has become slower? (aside from the effect of the Trojans of course). Thanks, Wanderer57 (talk) 15:12, 25 June 2011 (UTC)
- Short answer: not really. Something is slowing it down, but with this little information it's hard to say what it is. But it does suggest that safely backing up your data and reinstalling the OS would be something to consider if you happen to have a weekend free some time. --Ouro (blah blah) 18:26, 25 June 2011 (UTC)
- Addendum, because I was thinking over and over about this: there's too much default-loaded software hogging your PC's resources (system memory, CPU time, disk usage), that could be why it's slower when booted normally. It's just a guess though. --Ouro (blah blah) 19:57, 25 June 2011 (UTC)
- Safe mode disables a lot, a lot of functionality for compatibility purposes, basically so that there is as little reason for the PC to crash as possible (hence the designation 'safe') so you can get your stuff together to fix it. It would probably be a lot of algos in the buttocks to use it long-term. If there's a specific problem you're encountering which hinders your ability to run Windows in normal (contrary to safe - unsafe?) mode, why not describe it here? --Ouro (blah blah) 13:25, 25 June 2011 (UTC)
- Every PC I've ever had has slowed down with time. Reinstalling Windows and the programs you use, then waiting all day for endless updates to be downloaded and installed, will make your PC faster. It is also a good way to be sure you have got rid of any malware. Of course, it is a big step so you should make sure you can find all the install disks and back up your documents, photos, music, emails etc. before starting. Astronaut (talk) 09:30, 26 June 2011 (UTC)
remote processor networks
Question withdrawn. --DeeperQA (talk) 14:43, 25 June 2011 (UTC)
If routers have 192.168.1.1 as IP...
...how do I know that I am connecting to my router (in a building with many WLANs). I know that I can connect to my network and go to my 192.168.1.1, but what if I cannot connect to my network Wikiweek (talk) 13:20, 25 June 2011 (UTC)
- ...because you are connected to a specific SSID. It is the SSID you see when you choose the wireless "connect to a network" option from your PC. The 192.168.x.x addresses are internal to the network of your access point and your computers that are connected to it, whether wired or wireless. Network address translation (NAT) is used by the access point to translate the external IP address (which is given to the access point by your ISP), into a 192.168.x.x address on the internal network. Many access points assign 192.168.1.1 to themselves. You may think there are many 192.168.1.1 addresses, but you can only get to the one access point that you are currently connected to. If you are not connected to a network, then you cannot go to the 192.168.1.1 IP address. Astronaut (talk) 09:08, 26 June 2011 (UTC)
Economical side of torrent
How do torrent creators earn? It seems that some have so many that you can exclude for sure a private exchange; it looks much more like a full-time job. 88.9.209.112 (talk) 14:47, 25 June 2011 (UTC)
- Nope, essentially they do it for "glory". It's like how some people can publish hundreds of youtube videos. Lots of free time, and a desperate need for attention drives torrent-makers. i kan reed (talk) 13:41, 27 June 2011 (UTC)
Making a torrent and adding it to a tracker from data you already have connected to a computer takes a couple minutes, and that's if you don't have it automated. ¦ Reisio (talk) 17:28, 28 June 2011 (UTC)
filesystem
Is there a type of filesystem or something which automatically adds data redundancy and error correction to files? 77.197.196.159 (talk) 15:35, 25 June 2011 (UTC)
- There are distributed filesystems that do this, such as Freenet and Google File System. It would probably be pointless on a (single) local drive, since they commonly fail outright before developing any bad blocks. -- BenRG (talk) 21:25, 30 June 2011 (UTC)
secure against file corruption
I want to secure a file against the worst type of damage and corruption. What free software does this? 77.197.196.159 (talk) 15:35, 25 June 2011 (UTC)
- If this file doesn't change, then all you need to do is copy it to a safe place, say a CD or memory stick, with no special software required. Store the copy off site, in case of fires, etc. StuRat (talk) 17:02, 25 June 2011 (UTC)
- Sound advice. No file on rewritable media connected permanently to a live system is completely, fully safe. For security make a few copies and store them at different locations. --Ouro (blah blah) 19:44, 25 June 2011 (UTC)
- You could also create a draft e-mail in (e.g.) G-Mail and attach the file to this draft e-mail. This will create a copy of the file on g-mail's servers.
- Or you could try something like SkyDrive or DropBox, but that may require installing extra software.
- See also RAID. 93.95.251.162 (talk) 10:27, 28 June 2011 (UTC) Martin.
parchive
If I have a file which got corrupted, would making a Parchive AFTER it got corrupted be able to restore the corrupted parts? If not, what other methods might be able to salvage a corrupted file? 77.197.196.159 (talk) 15:35, 25 June 2011 (UTC)
- The Parchive would help you be able to recover the data to the state it was when you created the Parchive file/s. For example if you later found the original data and deleted the corrupted data you could then use the Parchive file/s to try to get back the corrupted copy of the data. Nil Einne (talk) 16:08, 25 June 2011 (UTC)
- What about AFTER the data was corrupted? The article says parchive uses good data around broken / missing data to guess what the broken / missing data should be. Would that work? 77.197.196.159 (talk) 16:23, 25 June 2011 (UTC)
- No. It may be possible to recover some of the data, depending on the file type and the nature of the corruption, but not using parchive. -- BenRG (talk) 08:04, 26 June 2011 (UTC)
- Repeating what I said above in a different way, if you create Parchive file/s after the data was corrupted they will be useful if you ever want to recover the corrupted data precisely as it was when you create the Parchive files. They will not recover the original data. For example, if you ever retrive the original data you could then use the Parchive files to try to convert the original data to the corrupted data. Nil Einne (talk) 14:55, 26 June 2011 (UTC)
- What about AFTER the data was corrupted? The article says parchive uses good data around broken / missing data to guess what the broken / missing data should be. Would that work? 77.197.196.159 (talk) 16:23, 25 June 2011 (UTC)
Storing 15GB of data in my garden for 50 years
If I wanted to store 15GB of data in a waterproof box buried several feet beneath the surface in my back garden for 50 years, what storage medium would be most likely to survive? Assume that in 50 years I'll have a perfect working computer able to read any of todays storage mediums. 77.197.196.159 (talk) 15:35, 25 June 2011 (UTC)
- Paper is the best storage medium for you. — Preceding unsigned comment added by 88.9.209.112 (talk) 16:26, 25 June 2011 (UTC)
- Not really, that would be a huge amount of paper, maybe 3 million pages. Two DVDs (or one double-sided) sounds like the best option to me. Note that you'd need to bury it below the frost line, or the freeze/frost cycle might break through the box in that time period. StuRat (talk) 16:55, 25 June 2011 (UTC)
- And how can you know that DVD-Readers will be available in 50 years? Indeed, no digital device that we use today will probably be available in 50 years. But, just imagine that you print little dots (=bits) on a sheet of paper. In the future, you'll have to scan/take pictures of the sheets and convert that to information. It is probably a lot of paper, but not the 3 million pages that you suggest above.It's probably something like 1 MB/page.88.9.209.112 (talk) 00:14, 26 June 2011 (UTC)
- Why not bury a DVD-Drive with it? Or a Mac Mini. --24.249.59.89 (talk) 21:44, 28 June 2011 (UTC)
- And how can you know that DVD-Readers will be available in 50 years? Indeed, no digital device that we use today will probably be available in 50 years. But, just imagine that you print little dots (=bits) on a sheet of paper. In the future, you'll have to scan/take pictures of the sheets and convert that to information. It is probably a lot of paper, but not the 3 million pages that you suggest above.It's probably something like 1 MB/page.88.9.209.112 (talk) 00:14, 26 June 2011 (UTC)
- You can't but the OP has already said it's not part of the question. It's a silly question and premise one of the reasons why I didn't try answering it but according to the question you aren't supposed to be worrying about whether you can actually read the media. Nil Einne (talk) 15:01, 26 June 2011 (UTC)
- Unfortunately our article section CD-R#Expected_lifespan says a CD-R disc is expected to last about 10 years only; see Disc rot. Different longevity numbers are scattered in 3 of our articles; Optical disc recording technologies#Longevity says that Mitsui claims its discs will last 100 years (which is obviously an extrapolation and not empirical); but Compact disc#Recordable CD says the design life is 20 to 100 years but discs can die in 18 months. A major reason that 88.9 mentioned paper is its demonstrated longevity of hundreds of years over the right traditions; plus paper is immune to obsolescence. (My old Apple II floppy disks, even if they survived physically, would be very difficult to read just because of the difficulty of obtaining a system that had the hardware to read a good disk.) Comet Tuttle (talk) 17:24, 25 June 2011 (UTC)
- Most of those forms of disc rot would either automatically be prevented by storing them in a locked box (deterioration from UV exposure and scuffing), or could be prevented with proper measures (like storing them in nitrogen to prevent oxidation). The delamination problem I'm not as sure about, but quality discs probably won't do that, if stored as described.
- As for being able to read a DVD 50 years from now, that doesn't seem completely impossible to me. DVD is a major format, so many people will continue to have readers/players years after they stop being made. Compare with LP records or the earlier 78s. Many people have record players that support those, even though the format goes back well over 50 years. I'd have less faith that a format which never really caught on, like 8-Track, Betamax, Digital Audio Tape or HD-DVD, would be readable 50 years later. StuRat (talk) 03:00, 27 June 2011 (UTC)
- This. But really, LOCKSS is a better strategy than burying stuff in your garden. 24.6.39.50 (talk) 03:01, 26 June 2011 (UTC)
I'm curious about how confident our OP is about having access to the same garden in 50 years time. (Not a Computing question, I know.) HiLo48 (talk) 03:10, 26 June 2011 (UTC)
- Considering the OP is confident they'll have a wonder computer capable of accessing any of today's storage media it seems only one minor risk. Nil Einne (talk) 15:01, 26 June 2011 (UTC)
Any digital archive must be continiously maintained. The file format and media technology used must be kept up to date, you can't bury it in the garden. The best place to keep it is in your computer with adequate backups using current technology. Right now your options include DVD, external hard drive, or flash memory. Roger (talk) 10:00, 26 June 2011 (UTC)
- PErhaps a solid state drive? Make sure that you keep a computer that will be bale to read SSD's General Rommel (talk) 01:46, 27 June 2011 (UTC)
- An SSD won't do because flash memory cells slowly leak charge. According to [this white paper] an unused Flash memory device will be unreadable after 10 years. This is not a problem in normal usage because the flash controller does static wear leveling to refresh little-used memory cells, but obviously that doesn't work without a power source. 130.188.8.12 (talk) 14:17, 27 June 2011 (UTC)
- Dodger67, you're (heh,heh) dodging the question entirely. He specifically said to assume he will have a computer from this time period to view the files. The question is clearly simply about the endurance of the storage material and not data-archiving best-practices in general. APL (talk) 07:08, 27 June 2011 (UTC)
- Build a digital archive in your garden; hire a chief archivist, an archivist, and a couple of archival assistants. Fund it for 50 years. Data retention will be high. Long term information storage means having experts at information storage, who attend to the maintenance and format of the data. Fifelfoo (talk) 01:50, 27 June 2011 (UTC)
- Storing it on sheets of rust-proof metal as text or numbers, with the characters deforming the metal rather than just ink which could decay. A more practical solution is that some microfiches are probably processed to survive a long time. According to the article 500 years if you can keep them dry, otherwise 20 years. Ozymandias managed to preserve data for thousands of years. 92.29.127.234 (talk) 08:58, 27 June 2011 (UTC)
- I agree, use microfiches. All you need to read it in 50 years is a magnifying glass. Or even a water drop would work if civilisation has gone pear-shaped and they don't have magnifying glasses anymore. 93.95.251.162 (talk) 14:45, 28 June 2011 (UTC) Martin.
What is the weird little separator in my Firefox 5 tabs?
There's this weird little animated separator between one tab and another when I use the recently downloaded Firefox 5. I thought at first it just delineated the last tab open so that you could see which one it was when you had many open and the last might be scrolled to the right off the screen but that's not it. I have 8 tabs open now and It's between the fourth and fifth. It's hard to describe so let me see if I can find a text symbol that looks like it.Well not exactly but it's like a vertical line that has a circle at the top--like a pipe "|" with an "o" resting on top, and it's blue and it's between two tabs and stretches a bit below where the tabs end, meaning it overhangs the window a bit. What is that? I tried googling "new features" and "firefox 5" but didn't find anything, and I also looked at Wikipedia's article without luck.--108.54.17.250 (talk) 16:41, 25 June 2011 (UTC)
- Sounds like a bug. I downloaded Firefox 5.0 and created over 8 tabs, but couldn't reproduce it, so it's not a universal bug. StuRat (talk) 16:48, 25 June 2011 (UTC)
- Hi, not an answer as such, but, I have found FF5 to be a little bit buggy - On mine, the tabs across the top of the browser currently obscure the "full screen/not full screen" option and the "x" option to close the browser. I think FF5 may have some issues that need to be resolved. I could of course be entirely wrong :s Darigan (talk) 16:56, 25 June 2011 (UTC)
- Hmm. It looks like a feature. Glitches don't usually look so purposeful, neatly placed, but maybe it is. I took a screenshot. Let me try to upload it.--108.54.17.250 (talk) 17:47, 25 June 2011 (UTC)
- Hi, not an answer as such, but, I have found FF5 to be a little bit buggy - On mine, the tabs across the top of the browser currently obscure the "full screen/not full screen" option and the "x" option to close the browser. I think FF5 may have some issues that need to be resolved. I could of course be entirely wrong :s Darigan (talk) 16:56, 25 June 2011 (UTC)
- Interesting, it may very well be a feature - I'll check back in a bit to see if you have managed to upload a picture. Darigan (talk) 17:58, 25 June 2011 (UTC)
- Here it is:
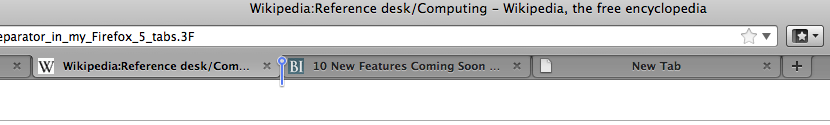 --108.54.17.250 (talk) 18:07, 25 June 2011 (UTC)
--108.54.17.250 (talk) 18:07, 25 June 2011 (UTC)
- Here it is:
- Interesting, it may very well be a feature - I'll check back in a bit to see if you have managed to upload a picture. Darigan (talk) 17:58, 25 June 2011 (UTC)
- I thing it's a feature of one of the extensions you have added. Try running firefox in safe mode (firefox -safe-mode) which should disable all the extensions and should confirm that it's not a standard Firefox mac feature. Looking at it I'd suspect it's from some tab-group extension, and it wants you to drag or toggle that blue thing somehow. -- Finlay McWalter ☻ Talk 21:00, 25 June 2011 (UTC)
- I'll try the safe mode thing. I don't think I have any extensions though. When I first saw that thing after I downloaded Firefox 5 I tried to access it, drag it, toggle it—it's just static.--108.54.17.250 (talk) 02:02, 26 June 2011 (UTC)
- Note that Firefox 5 attempts to maintain earlier extensions from previous version of Firefox, so perhaps an old extension has some incompatibility with V5. StuRat (talk) 22:53, 28 June 2011 (UTC)
A device doesn't "support" .txt files?
This is a new one to me. Windows Vista, and I connected a digital camera via its USB cable. When I try dragging a .txt file to any folder within the digital camera's windows, I get a "Cannot Copy File" error dialog which explains: "The file 'thisfile.txt' is not supported on this device. Although this device supports document files, it does not support .txt files." What? Googling some of this error text hasn't helped. Any ideas why this error is being displayed, and what it really means? Comet Tuttle (talk) 17:16, 25 June 2011 (UTC)
- Digital camera’s windows? You’re trying to use a camera as a storage device? ¦ Reisio (talk) 18:46, 25 June 2011 (UTC)
- Take out the storage medium (memory card?) from the camera and access it via a memory card reader connected to your computer. You'll be able to store the text file then (but of course the camera itself will not be able to read it). --Ouro (blah blah) 19:51, 25 June 2011 (UTC)
- Yeah, I need to add something (a bit in the dark because not a Windoze user any more, but there's enough left between my ears to figure it out). Well, if you plugged the camera via a USB cable directly to the computer, Win recognised the equipment as a digital camera, and I suppose that is the reason it doesn't allow you to copy a text file onto it - because, simply put, a digital camera is not supposed to support text files, but store images. Try different file formats. It doesn't matter in this setup that there's a run-of-the-mill memory card inside the device - the connection had been established to a digital camera. Now, what I described earlier, putting the card into a memory card reader and plugging it into the PC is a completely different story - because now the PC will recognise a card reader with a memory card - ergo, a storage device, the interface (driver? logic?) of which is to accept and support any and all file types and formats as you please. I hope this helps further. And sorry for posting two answers, I just had a bit more time to think about this issue. Cheers, Ouro (blah blah) 21:33, 25 June 2011 (UTC)
- Most newer cameras are not mounted as block devices, but by way of Picture Transfer Protocol (PTP). The camera itself may limit what you can transfer to/from it by means of that protocol (and actually I don't know whether text files are even supported by the protocol itself, but my guess would be that they are; why would you build in a limitation to the kinds of files at the level of the protocol?). For example I can mount my camera using PTP under Linux, and list directories with
lsand everything, but the Digital Negative (DNG) files don't show up, even though they are definitely there. --Trovatore (talk) 21:41, 25 June 2011 (UTC)
- Most newer cameras are not mounted as block devices, but by way of Picture Transfer Protocol (PTP). The camera itself may limit what you can transfer to/from it by means of that protocol (and actually I don't know whether text files are even supported by the protocol itself, but my guess would be that they are; why would you build in a limitation to the kinds of files at the level of the protocol?). For example I can mount my camera using PTP under Linux, and list directories with
- Thanks for the answers; this is the first I'd really heard of PTP, and it's the first I'd seen a camera (or similar device) mounted as anything other than a regular FAT or FAT32 or NTFS volume. Plugging the memory card itself into a PC did work, of course, and as predicted the .txt file does not show up when plugging the whole camera into the PC again. Comet Tuttle (talk) 20:44, 27 June 2011 (UTC)
Windows stable work
I haven't had problems with malware since 1990's, but a less fortunate and much less computer literate friend of mine just caught a scareware/malware called Windows stable work. It's a fake (and fairly convincing looking) "anti"virus that launches on startup, prevents running any programs (giving a great choice, between "NO, I don't want to run" and "YES, I want to block this program!") and offers a paid version of the software to remove these threats. Being a bit more experienced with Universal Calculators, I told him how to reach safe mode: now it appears that CLI safe mode doesn't allow the malware to run, allowing us to execute programs without it interfering. However, I'm clueless on how to actually remove that thing, as my friend's installed antivirus/malware programs (I think it was Avira and MalwareBytes) failed to notice the programa non grata. Any help is appreciated. Zakhalesh (talk) 20:30, 25 June 2011 (UTC)
- I did do a Google search, yes, but most of the stuff that came up seemed outdated (eg. the registry keys said to be used by the malware weren't present on my friend's machine) and so on. I was wondering if anyone has removed the particular malware recently. Zakhalesh (talk) 13:57, 26 June 2011 (UTC)
- I'd suggest you Boot in Safe Mode with networking, download the Malwarebytes definitions and then scan for any viruses. — Preceding unsigned comment added by General Rommel (talk • contribs) 01:39, 27 June 2011 (UTC)
- I did do a Google search, yes, but most of the stuff that came up seemed outdated (eg. the registry keys said to be used by the malware weren't present on my friend's machine) and so on. I was wondering if anyone has removed the particular malware recently. Zakhalesh (talk) 13:57, 26 June 2011 (UTC)
- My process
- boot into save mode. This prevents the virus from starting with your pc.
- start->run->regedit
- Navigate to hkey_localmachine/software/microsoft/windows/currentversion/run
- Remove ANYTHING you don't recognize, record the paths so you can find the files
- Repeat for hkey_local_machine/software/microsoft/windows/currentversion/runonce
- repeat for hkey_current_user/software/microsoft/windows/currentversion/run and runonce
- Navigate to hkey_localmachine/software/microsoft/windows/currentversion/run
- delete any of the files you recorded before making backups in zip files(so they can't be executed)
- check the startup folder of the start menu, remove anything there
- restart computer, verify program didn't start with task manager
There are lots of other places that malware can use to start up, but the vast majority uses those 2 locations. This is essentially the same thing malware scanners check for, except they only remove KNOWN threats which constantly evolve for the sake of avoiding that. If you want a more comprehensive list of what boots when your computer starts, microsoft distributes a wonderful tool called "sysinternals autoruns". Google that. I simply don't trust anti-malware tools anymore and do my removals manually. i kan reed (talk) 13:59, 27 June 2011 (UTC)
Wireless
Any insights help-deskers can offer on this would be gratefully received since, as usual whenever I encounter IT, it is driving me up the wall.
Until now my home has got by with one computer connected via a USB cable to a modem which in turn is connected by an ADSL cable to a signal splitter which plugs into a broadband-enabled phone socket in the wall.
However, this summer we have students staying with us so clearly a wireless network will be needed for their benefit.
I had an old router and I plugged it in to find that it was broken, so I trundled to the shops to buy a new one.
Now, the new router, it turns out, after I opened the box, doesn't contain an internal modem like my old one did, but needs connection, via ethernet cable, to an existing modem which in turn connects to the wall.
But, as mentioned above, my existing modem has neither an ethernet cable nor an ethernet port to plug one into: just a USB cable.
So where do I go with this? Is the answer:
- Take the new router back to the shop and replace it with a different one with a modem built in?
- Buy a new modem of the variety required by the new router?
I suppose it is worth adding that:
- I'd prefer a solution which is quite cheap over one which is brilliant; but
- Too much loss of connection speed would probably really annoy. AndyJones (talk) 20:37, 25 June 2011 (UTC)
- Yeah, take it back and get an integrated one. That's the simplest thing to have, and shouldn't cost much (most UK ISPs just give you one, or sell you one at a knockdown price, when you sign up). -- Finlay McWalter ☻ Talk 20:58, 25 June 2011 (UTC)
- I'm surprised you were easily able to get a router without a modem. Most "wireless routers" sold in the UK have a built-in modem. This page from the website of a popular UK retailer lists 23 of the devices, only one of which appears to have no built-in modem. Be careful though: the hard to find technical specification for that one product says it does have a modem, which calls into doubt the accuracy of the information on the website (in my experience with that retailer's website, the only thing you can trust is the price and image of the product). It is probably better to verify technical specs with the manufacturer's website. Astronaut (talk) 08:28, 26 June 2011 (UTC)
- The page you linked is a list of "BT Wireless Routers", and "BT" appears to mean "ADSL" (yes, I know what it really stands for). If standalone modems are routers are hard to find now, that's a pretty recent phenomenon, isn't it? In my admittedly limited experience with UK and US home broadband, they were always separate. -- BenRG (talk) 08:50, 26 June 2011 (UTC)
- The OP self-identifies as British, and I have assumed they are still resident in the UK. It is not really a recent phenomenon. In my experience in the UK, when you go to buy a wireless router from a retail store like PC World, or get one for free when you sign up with an ISP, they will nearly always come with a built-in modem. In the box, you usually get the combined modem-router device, the power brick, a phone filter, a RJ-11 modem cable and maybe an ethernet cable, along with a small manual and a driver disk (some of this is shown in this image). On the rear panel, the device itself usually has the power port, four ethernet ports and one RJ-11 port for the modem cable. If you have a cable router instead, you get slightly different package contents but it is essentially the same device. Back in the early days of broadband provision in the UK, before ISPs considered people might want to connect wirelessly or connect multiple internet-enable devices, ISPs supplied a free USB modem to replace your dial-up modem; this is probably the kind if thing the OP currently has. From what I have read (here on the ref desks and elsewhere) the situation seems to be slightly different in the US, where it seems to be more common to have separate devices. Astronaut (talk) 12:41, 26 June 2011 (UTC)
- The page you linked is a list of "BT Wireless Routers", and "BT" appears to mean "ADSL" (yes, I know what it really stands for). If standalone modems are routers are hard to find now, that's a pretty recent phenomenon, isn't it? In my admittedly limited experience with UK and US home broadband, they were always separate. -- BenRG (talk) 08:50, 26 June 2011 (UTC)
- I'm surprised you were easily able to get a router without a modem. Most "wireless routers" sold in the UK have a built-in modem. This page from the website of a popular UK retailer lists 23 of the devices, only one of which appears to have no built-in modem. Be careful though: the hard to find technical specification for that one product says it does have a modem, which calls into doubt the accuracy of the information on the website (in my experience with that retailer's website, the only thing you can trust is the price and image of the product). It is probably better to verify technical specs with the manufacturer's website. Astronaut (talk) 08:28, 26 June 2011 (UTC)
Great advice from all. Followed Finlay's advice and all now working as hoped. Many thanks as ever. AndyJones (talk) 19:15, 26 June 2011 (UTC)
Zero-byte files in WinXP
Using Duplicate Cleaner, I find I have a large number of zero-byte files on my computer. Is it safe to delete them? How much space do they take up? Thanks. 92.29.120.186 (talk) 21:27, 25 June 2011 (UTC)
- They're probably just junk and it's probably safe to delete them (but it'd be safer moving them to a special folder for a while, so you can restore them if they do mean something). Some programs might make zero-size files as a little reminder they can store in the filesystem - sometimes as a lock file and sometimes as a little note to subsequent runs of the program that something has happened (e.g. some programs might create an "initialisation performed okay" zero-size file after their first run, so they don't show the "please input initial setup parameters" screen every time you run it). There are preferred methods for doing some of this (the ATOM table, the registry, the LockFile API) but some programs may make zero-size files anyway. If I understand the NTFS filesystem layout properly (which I definitely don't) then a zero-size file should take up a small-file-record in the MFT; so "not much space", but I don't know exactly how little. -- Finlay McWalter ☻ Talk 22:00, 25 June 2011 (UTC)
- MFT entries are almost always 1K, so a file small enough to fit there (up to maybe 600–700 bytes) takes roughly 1K (and a little more for the copy of the filename in the parent directory index). But unused MFT entries are not reported as free space, so you won't see any obvious space gain if you delete the files. -- BenRG (talk) 08:31, 26 June 2011 (UTC)
Tooltips In System Tray
When I mouse over the icons in my status bar, tooltips come up telling me what each icon represents. In most cases, these tootips cover up some of the other icons, forcing me to move the mouse (and be greeted by further tooltips covering up other icons). How do I switch off this feature? --KägeTorä - (影虎) (TALK) 21:42, 25 June 2011 (UTC)
- I don't think you can remove the feature, but you can remove the icon altogether. General Rommel (talk) 01:37, 27 June 2011 (UTC)
Which top-level domains are limited as far as who can own them?
I know that certain top-level domains like .gov and .mil are not allowed to be privately owned. What about .edu? Could I purchase a .edu site for personal use? (in the same manner that I can purchase a .org site, even if it's not for an organization) ... What other TLDs are limited where they cannot be purchased for personal use? ~ Mesoderm (talk) 23:21, 25 June 2011 (UTC)
- Our article .edu answers the question, I think: no. Looie496 (talk) 00:30, 26 June 2011 (UTC)
- Indeed, "no", but only insofar as you'd have to first purchase something passable as an educational institution. ¦ Reisio (talk) 03:58, 26 June 2011 (UTC)
- More than that, it has to be an accredited college/university (etc) in United States (actually, accredited by an agency approved to accredit by the US DOE). Paul (Stansifer) 21:11, 26 June 2011 (UTC)
- Indeed, "no", but only insofar as you'd have to first purchase something passable as an educational institution. ¦ Reisio (talk) 03:58, 26 June 2011 (UTC)
- See sponsored top-level domain. Gobonobo T C 07:04, 26 June 2011 (UTC)
Thanks folks! ~ Mesoderm (talk) 17:58, 26 June 2011 (UTC)
An existing .edu domain certainly doesn't have to be in the US: uofk.edu is the University of Khartoum (Sudan). Also, I think I've encountered at least one small and obscure US "creationist" institution that's not accredited by any agency taken at all seriously yet has an .edu domain. -- Hoary (talk) 00:03, 1 July 2011 (UTC)
June 26
Saving passwords on Android apps
Is there a way to save the passwords for Android apps I use, so I don't have to type them in every time? Like Wells Fargo app. I have the HTC EVO. CTJF83 00:29, 26 June 2011 (UTC)
- Do you feel good about a person who steals your EVO having access to your bank account? Looie496 (talk) 00:32, 26 June 2011 (UTC)
- ....Well Wells Fargo covers it, but is it possible? It's a pain typing in long complicated passwords on a phone. CTJF83 00:35, 26 June 2011 (UTC)
- I have an Android, and I've worked in the computer support departments of a bank before. I am 95% sure this isn't possible; banks would make sure to not to include the capability from the app, and I don't know of any apps which can manipulate other apps. You might find one that can automatically paste a given piece of text, but that's probably more effort than it's worth.
- ....Well Wells Fargo covers it, but is it possible? It's a pain typing in long complicated passwords on a phone. CTJF83 00:35, 26 June 2011 (UTC)
- If you're really worried about it, you might try using the web interface and saving the password. I do not recommend this unless you have decent security on your phone already, and frankly, not even then. But if you do implement it, make sure that if you ever lose your phone, that you immediately check your online banking that your password hasn't changed, that your address hasn't been changed, that you haven't sent any secure messages to your bank. Your bank may or may not have a note upon sign in telling you of your most recent sign in time. Magog the Ogre (talk) 01:02, 26 June 2011 (UTC)
- Oh, ok, thanks. And actually now that you mention it, even on Firefox and Chrome it won't let me save any of the 3 banks I use to log in. Like you said, they must have something to prevent it. It makes sense...ok, I'll just be non-lazy and type it in. Thanks to both of you! CTJF83 01:07, 26 June 2011 (UTC)
- If you're really worried about it, you might try using the web interface and saving the password. I do not recommend this unless you have decent security on your phone already, and frankly, not even then. But if you do implement it, make sure that if you ever lose your phone, that you immediately check your online banking that your password hasn't changed, that your address hasn't been changed, that you haven't sent any secure messages to your bank. Your bank may or may not have a note upon sign in telling you of your most recent sign in time. Magog the Ogre (talk) 01:02, 26 June 2011 (UTC)
- It can be done, but it's probably not worth the trouble. ¦ Reisio (talk) 03:55, 26 June 2011 (UTC)
- RoboForm isn't free, but it has an Android application in the market that can do this. It protects all the passwords with a master password, but it will also (as part of how it works) synchronise the passwords to an online RoboForm account as well as any other computers you have connected to the account. Whether you want it to do all this or not I don't know, but the product itself does what you ask and may be worth a look (I use it myself). ZX81 talk 18:37, 26 June 2011 (UTC)
adding automatic subtitles for VLC videos?
is this possible?
is there another player who does that if not VLC?.. — Preceding unsigned comment added by 79.179.8.59 (talk) 02:45, 26 June 2011 (UTC)
- What do you mean automatic? VLC will play embedded subtitles, and subtitles of certain formats that have the same filename as the video being played, and are in the same directory. It doesn't find subtitles automatically, but it wouldn't be that hard to make a script or two to, for example, check the entire tree of a directory for subtitles files (even in archives), and use them, or even to find subtitles from sites such as opensubtitles.org. ¦ Reisio (talk) 03:57, 26 June 2011 (UTC)
Hello. what i need is a plug-in or maybe another player how could automaticly show subtitles to my videos, whatever this will be?.
is there such a thing today?.
thanks. 79.179.8.59 (talk) 13:24, 26 June 2011 (UTC)
- I doubt there is (any public/official support for that), but the data (the subtitles) and the technology (it'd only take a simple shell script or batch file) is all there for someone willing to put in the time. ¦ Reisio (talk) 14:41, 27 June 2011 (UTC)
Tracking down a group of hackers
I'm talking about a notorious group of hackers who have a significant presence on Twitter. I'm curious as to why they haven't been tracked down already by law enforcement. The VPN they use (by their own account) is HideMyAss which keeps logs for 30 days, and for at least 7 on US territory. Its a US based company too. Judging by their IRC conversations, they only use the VPN, and not any shells or such. Why haven't they been tracked down then? — Preceding unsigned comment added by Temptre.22 (talk • contribs) 10:55, 26 June 2011 (UTC)
- You are referring to LulzSec. The identity of the main players were posted online by a group of kids who admitted to having no real hacker skills. Very quickly, one was arrested, a few quickly left the group, and the rest decided (yesterday) to shut down LulzSec. They are probably busy trying to erase every computer they've used while they wait for the slooooooow arm of the law to knock on their door. (Damn laws - require real evidence to arrest someone.) -- kainaw™ 13:02, 26 June 2011 (UTC)
- I know who I'm referring to; I avoided naming them. But that's just the thing. Their identity was posted online, but not due to their VPN. Those who quickly left the group left because the group attacked the FBI. And I don't pretend to know why they disbanded, I'm just curious as to why they would choose a VPN that logs, and why the FBI hasn't used the Patriot act to seize logs. Temptre.22 (talk) 13:06, 26 June 2011 (UTC)
- The Patriot Act will do nothing more than speed a warrant request through the court system. That is only useful when trying to get a warrant for logs kept on a computer inside the United States. Where are the HideMyAss servers located? If they are in Virginia, that may explain why the FBI stormed a data center and took all the servers - even those that didn't have anything to do with HideMyAss or LulzSec. -- kainaw™ 13:19, 26 June 2011 (UTC)
- [6] suggests they used more then HideMyAss. BTW Telecommunications data retention#Commercial data retention and National Security Letter suggests the Patriot Act expanded the scope for NSLs which don't have to be issued by the court and which can be used to demand some non content info, from the sound of it probably including stuff like who was using IP X at time A (see also [7]). Although whether they could be used in this case and the FBI would risk it even if they could I don't know. Nil Einne (talk) 18:06, 26 June 2011 (UTC)
- Thanks for the link, Nil, it was an interesting read. They mention on that forum that the group might have used SSH to carry out the hack. I see the group also discussed a few VPNs, but they all recommended HMA, and at least one of them was using it. This is all hypothetical, but since they were so good with networks and such, why would they use a VPN that logs? What am I missing here? (and don't say they were dumb or something... they might have been many things, but dumb is not one of them) Also, to be clear, NSLs are much faster than typical search warrants. They're issued almost immediately. Temptre.22 (talk) 18:38, 26 June 2011 (UTC)
- Most obvious reason... a friend worked there. -- kainaw™ 23:01, 26 June 2011 (UTC)
I don't know about LulzSec, but any serious technophile will have no trouble at not being located by anyone. ¦ Reisio (talk) 14:39, 27 June 2011 (UTC)
Cat5e crosstalk
Would the reduced crosstalk in cat5e compared to cat5 cable, over about 2 metres, be enough to see an increased bandwidth/speed between a 100mbps router and a pc? Would type of telephone cable between a router and phone socket also make a difference? Bahr456 (talk) 14:55, 26 June 2011 (UTC)
- Do you have any reason to believe the bandwidth of your connection is actually affected by the cable? For a 2 metre cable I doubt it. Bear in mind many of the cheaper network adapters often don't actually achieve the maximum speed particularly if the computer is slow which if it still has only a 100mb adapter it may be. Intel adapters are usually considered the best I believe although 3coms are also considered not bad and nowdays even the Marvell and RealTek GbE aren't too bad (RealTek fast ethernet adapters were often considered rather crap).
- Also I'm confused about your setup. Are you referring to a LAN? If so what does the router or phone socket have to do with it? If you are referring to an internet connection using the phone line, I guess some sort of DSL, I quite doubt you have anything close to a 100mbit connection so there is very likely no point worrying about the connection between the router and PC.
- Improving the household cabling for the phone line may help a bit, you'd first want to install a dedicated DSL splitter at the point of entry of the phone line, if one isn't already installed rather then using microfilters on each phone jack. Using cat5 between the splitter and xDSL router may also help. But don't expect miracles, there's a fair chance the difference won't be much if anything [8]. Also are you sure your bandwidth is not being limited by your ISP whether at the DSLAM or the IP level? If it is then and you're getting the advertised speed then there is likely no way you can improve bandwidth other then to upgrade plan.
- Nil Einne (talk) 15:17, 26 June 2011 (UTC)
- Thanks for your answer. Im referring to a DSL line. My router is profiled for an 18mbps download speed but speed test results only give a result of about 15mbps. 18mbps was what the ISP set the line speed to, saying its the best the line can handle, guaranteeing a reliable connection. So I assumed the drop in speed was either the internal wiring or the router? Bahr456 (talk) 17:40, 26 June 2011 (UTC)
- Is the router actually syncing at 18mbps? If it is, then there's probably not much you can do about the speed. It's quite unlikely to be the connection between the router and PC. And if the router is syncing at 18mbps and your ISP is only willing to let you sync at that speed then there's probably not much you can do. Bear in mind Asynchronous Transfer Mode has about a 10% overhead so if DSL router is syncing at 18mbps you will only expect about 16mbps via any sort of TCP speed test (I think you should actually use about 13% to take in to account TCP/IP overhead). Nil Einne (talk) 17:50, 26 June 2011 (UTC)
- Thanks for your answer. Im referring to a DSL line. My router is profiled for an 18mbps download speed but speed test results only give a result of about 15mbps. 18mbps was what the ISP set the line speed to, saying its the best the line can handle, guaranteeing a reliable connection. So I assumed the drop in speed was either the internal wiring or the router? Bahr456 (talk) 17:40, 26 June 2011 (UTC)
Most error correcting file compression?
Is there any file compression type that is better at error correction than others? Given the same recording medium, what archive formats are better at reconstructing missing/damaged data? I read about [RAR]'s recovery volume (.rev) option, but I can't find any Mac RAR client that can read/write these files. --68.102.167.95 (talk) 18:13, 26 June 2011 (UTC)
- Have you tried Parchive? 118.96.163.71 (talk) 13:18, 27 June 2011 (UTC)
Right to left encoding
Hello, I keep having problems with copying right to left encoded text , eg from this page http://www.mapnaec.com/persian/ I got شرکت مهندسی و ساخت برق و کنترل مپنا which has curious properties when I try to select it with a mouse from end to end (I assume others will get this too).
Can someone explain what is happening to cause this, is it standard behaviour, and is it unavoidable on a computer set up for left to right text. Or whatever you want to tell me. Thanks.Imgaril (talk) 19:23, 26 June 2011 (UTC)
- It is complex behaviour but I don't think entirely unintentional. It's just that you are trying to mix two systems (LTR and RTL). It assumes you want to copy a passage in order. Imagine the following example in Latin text (since the character set has nothing to do with it): "lufrednow si taht, yM", Mr Backwards exclaimed. Now, selecting from right to left, your browser assumes you want to move backwards through the prose, in which case the order is exclaimed - Backwards - Mr - lufrednow- si - taht - yM. The browser "Helps" you select it in that order, which is weird but makes perfect sense for many usages. - Jarry1250 [Weasel? Discuss.] 20:41, 26 June 2011 (UTC)
- Yes thanks - I'm starting to understand it now - I haven't check but it seems obvious that the byte order and display order are swapped in the persian text, causing the odd looking behaviour. I supposed there must be some sort of control character in their, or perhaps that's inferred simply because of characters coming from the "right to left" unicode code space. It suprised me that even notepad does it...Imgaril (talk) 18:33, 27 June 2011 (UTC)
June 27
Thermal efficiency of FPGAs vs. conventional CPUs
How do field-programmable gate arrays compare to conventional CPUs in the amount of heat produced per operation, and in the amount produced in the process of loading a program versus reconfiguring an FPGA? NeonMerlin 07:43, 27 June 2011 (UTC)
Excel: Date Calculation
I've been sat here for a while trying to figure out the best solution or even an easy solution but I can't seem to find one to a calculation related with dates.
I have an Excel spreadsheet which has a column with =today() so it displays todays date. I also have a column which includes the start and end date or a project as well as other columns for amount of days between and working days etc. Basically the issue is I would like to work out the percentage of time elapsed for each section. So using the date 27/06/2011 - if the start date was the 26/06/11 and end date - 27/06/08 it would say it was 100% complete. Is this even possible?
Many Thanks 195.49.180.85 (talk) 08:10, 27 June 2011 (UTC)
- (I presume you mean 27/06/11 for the end date.) The basic formula would be =(TODAY()-StartDate)/(EndDate - StartDate) (and then format the cell as a percentage), but you'd have to be careful if it was possible for Start date and end date to be the same - maybe =IF(StartDate=EndDate, 1, <formula as before>). If you used NOW() instead of TODAY() you'd get a more precise figure - using TODAY() will give very coarse results if the start and end are a small number of days apart. AndrewWTaylor (talk) 08:19, 27 June 2011 (UTC)
- Yes you are right 27/06/11, Have no idea why I used 08. I will give that a try. Thank you :) 195.49.180.85 (talk) 08:25, 27 June 2011 (UTC)
- Of course, you need to decide what you want to be displayed if EndDate is earlier than Today(). If in this case you want to see 100% (rather than a figure that is greater than 100%) then you need to code another exception e.g.:
- =IF ( OR ( TODAY() >= EndDate, StartDate = EndDate), 1, <formula as before>)
- Gandalf61 (talk) 09:09, 27 June 2011 (UTC)
- Of course, you need to decide what you want to be displayed if EndDate is earlier than Today(). If in this case you want to see 100% (rather than a figure that is greater than 100%) then you need to code another exception e.g.:
- Yes you are right 27/06/11, Have no idea why I used 08. I will give that a try. Thank you :) 195.49.180.85 (talk) 08:25, 27 June 2011 (UTC)
- Better to use enddate-startdate+1 for the denominator and not say it is finished till the day after the end. Anyway such dates just give how much should be completed rather than is completed. I'd advise getting a project planning tool if you start doing much of this, they can deal with dependencies and suchlike things nicely. Dmcq (talk) 11:22, 27 June 2011 (UTC)
- Second that -- depending on what you "expect" to see, date conversion in project planning software is a fairly significant piece of the code.
- The convention is normally that the beginning of a task starts at the beginning of a day, and the end of a task at the end of the day. In this manner, you get what you expect for a one-day task, i.e., it starts and ends on the same day. The task which immediately follows that task, though, can't start until the next day, even though it might logically be only one minute later.
- Trying to work around weekends and holidays in Excel will give you an even bigger headache. It really is a case where specialized software is worth it. DaHorsesMouth (talk) 00:17, 28 June 2011 (UTC)
Desktop speaker volume detection?
How does my computer "know" my desktop speaker's volume (dial) setting? If I issued the "ECHO Ctrl+G" command from the Command Prompt and the speaker is turned up, the beep will be played from the speaker. However, if the speaker is turned down (or off), the beep will be played from the internal (PC) speaker instead. How does the computer do this? The only thing that connects the speaker and the computer is a TRS audio cable connected to the speaker's "Input" jack and the computer's "Front Output" audio jack. Many thanks. 118.96.163.71 (talk) 13:14, 27 June 2011 (UTC)
- Completion (or not) of an electrical circuit, I’d imagine. (
if [is completed] { use speakers } else { do something else }) ¦ Reisio (talk) 14:46, 27 June 2011 (UTC)
Remote file system manipulation without FTP
Sorry for the confusion subject — I couldn't quite think of a pithier way to describe this.
I'm working on a project where I need to be able to put and remove files to a remote server.
The problem: the remote server only supports Secure WebDAV (WebDAV with HTTPS/SSH) as its mode of access. No FTP, no SFTP.
So it's easy for me to manually put files onto said server. But I'd like to be able to do it with PHP. PHP doesn't natively support WebDAV. There is only one PHP WebDAV class on the web that I've found, and it doesn't support secure connections. You can compile PHP to have WebDAV support, but the server I'm hosting the PHP on does not have it compiled into their version of PHP and it doesn't seem likely that I can convince them to do so.
So for the moment I'm trying to brainstorm other options. The remote server can run PHP. So I've been thinking about using some sort of script on the server itself which would receive the file data, e.g. through some sort of secure connection. I don't really know what this would be called. It's not the sort of thing I have experience with, but presumably you could have one that would act as kind of a mini-FTP server. Is this a possibility? Does something like this have a name? Would it work?
Any other ideas? --Mr.98 (talk) 15:37, 27 June 2011 (UTC)
- One other (odd) idea: the "incoming" files to the remote server are all coming from one source, which does have FTP access. I could imagine a script on the remote server that would receive (encrypted?) instructions from the source telling it to connect via FTP (using PHP's built-in FTP functions) and download files to various locations. Kind of a hassle, though.
- Another idea is to try and drop into a shell and use rsync or something like that. (Though now that I look at it, it doesn't look like rsync natively supports secure WebDAV either. Damn!) --Mr.98 (talk) 15:48, 27 June 2011 (UTC)
- If you're on Linux (and the like) you can use davfs2 to mount the remote filesystem locally, over WebDAV. The manual page shows examples of it being mounted with an https URL. With the filesystem mounted locally, you can use whatever you like to manipulate the files, as if they were really stored locally. I've never personally used this (nor WebDAV at all) - I'd be interested to know how you get on. -- Finlay McWalter ☻ Talk 16:02, 27 June 2011 (UTC)
- The problem is that I'm not doing this locally. Ideally the "local" aspects of this would all be hosted on another (different) remote server. I doubt that the Bluehost server which will be hosting the scripts in question will be able to mount drives. This whole thing is such a mess because the main (academic) webservers have been apparently configured by monkeys, and are apparently not meant to be useful to anyone, hence having to do ten thousand work-arounds for what ought to be a simple CMS... --Mr.98 (talk) 16:09, 27 June 2011 (UTC)
- Ah yes, I remember you suffering the last time with this setup. Are you utterly attached to PHP? The PyDAV Python library supports https connections, and the example enclosed with it suggest that to put a single file you'd do nothing fancier than:
#!/usr/bin/python
from WebDAV import client
res = client.Resource('https://crappyserver.annoying.edu', username='mr98', password='oBsCuRa')
data = open('myfile.html').read() # read a local file and...
res.put(file=data) # push it to the WebDAV server
- Yeah, I'm pretty attached to PHP — both because it's what I know the best, and because this whole thing is going to be paired up with WordPress one way or another, alas... Blargh. I am not quite paid enough to deal with this idiotic server. --Mr.98 (talk) 16:50, 27 June 2011 (UTC)
- You can use a command-line tool easily in PHP. For example, you can use cadaver (if you are on Linux) with popen.
I would use $pf=popen("cadaver https://your.server.info", "w"); so you can then pump commands to it with fputs($pf, "YourPassword"); or fputs($pf, "put YourNewFile");Then, wrap that up in a function like function my_cool_secure_webdav($filename). -- kainaw™ 18:28, 27 June 2011 (UTC)
- You can use a command-line tool easily in PHP. For example, you can use cadaver (if you are on Linux) with popen.
- I checked cadaver and it is a bit finicky, so I'd use proc_open instead with read/write to interact with it properly. -- kainaw™ 18:45, 27 June 2011 (UTC)
Robots.txt
Somebody on the NTSB added robots.txt to the website. This means that the arhcived content at http://www.ntsb.gov is now unavailable
Has anyone found a way to bypass robots.txt so that one can look at the content on http://web.archive.org/*/http://www.ntsb.gov ? What arguments could I use if I was corresponding with NTSB officials and asking them to remove robots.txt from the site?
The US government documents are in the public domain, and stuff on the public website is not classified, so I do not know why the NTSB added robots.txt. WhisperToMe (talk) 18:10, 27 June 2011 (UTC)
- Adding robots.txt reduces load on the server from search engine spiders. Because information is free, does not mean it must be available in the specific manner that you want to receive it. They could place it on file in a file cabinet in the basement of an old missile silo in a corn field in Kansas and still claim it is free - you are free to go and find it. So, any argument you make is going to be seen as, "I want you to change how you do things because I don't want to change how I do things and I'm offering nothing in return." -- kainaw™ 18:30, 27 June 2011 (UTC)
- Responding to that argument, I would say "you already did things X way, so why are you changing it now?" (the documents had been on the NTSB website for years) - It would be far easier for the NTSB to leave the old content up than to remove it and then face inquiries asking for the NTSB to restore the material.
- And my point of view is "The agency works for the American people, so it must continue to offer the same level of access to this information unconditionally"
- WhisperToMe (talk) 18:42, 27 June 2011 (UTC)
- (edit conflict)They probably won't give you a (decent) answer as to why they changed it. I'm not aiming this at you personally, but I wouldn't, it's none of anyones business how I run my webservers. But what we do know is they have intentionally tried to blocked respectable crawlers which could be either because they didn't like the resources they used up trawling the site, they didn't like the idea of someone else caching the site or easily copying everything or they just simply want people to enter the site and search it using their own tools (or any other reason). ZX81 talk 18:52, 27 June 2011 (UTC)
- If this was a private webserver, I could totally understand "but I wouldn't, it's none of anyones business how I run my webservers" - However in this case I have a different attitude because the NTSB is an agency of the US government, and I am a US citizen and I believe the agency's job is to serve the American people by continuing to provide the information on old accidents. I could potentially ask my federal representatives to look into the matter. WhisperToMe (talk) 19:58, 27 June 2011 (UTC)
- Sorry I meant no offence, but from what I now understand (based purely on the text above/below), they've already removed that information from their site and basically you were just using archive.org to view it because it wasn't on the real site anymore? I have no idea about US laws or what they're required to do with public information (I live in the UK), but I'm guessing that like Kainaw said right at the top the information is probably still available, just not in the way you want to retrieve it. But it certainly wouldn't hurt to ask them, I was just trying to say I don't think you'll get a very helpful reply back. ZX81 talk 20:45, 27 June 2011 (UTC)
- It's okay - I understand that the argument above was just a devil's advocate response :) - Anyway, the information was taken down from the previous locations and the NTSB has not stated if there were any new locations for the data - the site search I used did not find the public docket info I was looking for. I have sent e-mails to the NTSB, and I am hoping to receive responses.
- It's possible that the NTSB could charge a fee if it asks me to order CDs of the information, while when it was on the NTSB website it was free.
- WhisperToMe (talk) 21:46, 27 June 2011 (UTC)
- Sorry I meant no offence, but from what I now understand (based purely on the text above/below), they've already removed that information from their site and basically you were just using archive.org to view it because it wasn't on the real site anymore? I have no idea about US laws or what they're required to do with public information (I live in the UK), but I'm guessing that like Kainaw said right at the top the information is probably still available, just not in the way you want to retrieve it. But it certainly wouldn't hurt to ask them, I was just trying to say I don't think you'll get a very helpful reply back. ZX81 talk 20:45, 27 June 2011 (UTC)
- If this was a private webserver, I could totally understand "but I wouldn't, it's none of anyones business how I run my webservers" - However in this case I have a different attitude because the NTSB is an agency of the US government, and I am a US citizen and I believe the agency's job is to serve the American people by continuing to provide the information on old accidents. I could potentially ask my federal representatives to look into the matter. WhisperToMe (talk) 19:58, 27 June 2011 (UTC)
- (edit conflict)They probably won't give you a (decent) answer as to why they changed it. I'm not aiming this at you personally, but I wouldn't, it's none of anyones business how I run my webservers. But what we do know is they have intentionally tried to blocked respectable crawlers which could be either because they didn't like the resources they used up trawling the site, they didn't like the idea of someone else caching the site or easily copying everything or they just simply want people to enter the site and search it using their own tools (or any other reason). ZX81 talk 18:52, 27 June 2011 (UTC)
- I don't think there's a way to bypass it. According to the faq page "When a URL has been excluded at direct owner request from being archived, that exclusion is retroactive and permanent." That seems to imply that they destroy all previous archived snapshots of a site if robots.txt is added. This page also states that adding robots.txt to a site "will remove all documents from [the] domain from the Wayback Machine." Whether they actually delete the previous archives or just block them from public view I don't know; it would be a huge loss if they really did just delete them all. AvrillirvA (talk) 18:49, 27 June 2011 (UTC)
- From my understanding they just block them from view. There was a case where a website once had robots.txt (Sosoliso Airlines website) - See this revision - but when that went away, lo and behold, all of the documents became visible again, and now Wikipedia links to websites on that website's archive. WhisperToMe (talk) 19:52, 27 June 2011 (UTC)
- (After e/c)
- To answer the basic question : No. There is no way to fool Archive.org into thinking a site has different permissions than it really has.
- Of course robots.txt has no technical power. It's based entirely on the honor system, but Archive.org honors it. And with good reason. If they became known as a malicious spider it would severely hamper their ability to do their job. APL (talk) 18:53, 27 June 2011 (UTC)
- In that case, I may have to wait maybe 10-15 years (or however much time until robots.txt is removed?) - Or see if the NTSB will re-upload the content, or see if my federal representatives could ask the agency to restore the materials in the public docket related to accidents in the late 1990s and early 2000s. WhisperToMe (talk) 20:01, 27 June 2011 (UTC)
- This CRS document may be of use; the Obama administration has declared that they want the US government to be more transparent than ever before. You should be able to talk someone at the NTSB into agreeing with you that the new robots.txt addition has made it less transparent, even though, if I understand the above correctly, this has to do with organizations outside of the control of the NTSB; and therefore it's at odds with the government's goals as expressed in this document and the directives it cites. Comet Tuttle (talk) 20:40, 27 June 2011 (UTC)
- Thanks for finding that, Comet Turtle! That's really helpful.
- If there were outside agencies that asked for robots.txt, I'm not sure who it could be. The file could be reconfigured so that only material from the outside agencies would be affected.
- WhisperToMe (talk) 21:49, 27 June 2011 (UTC)
- What I meant was: The impact upon you (of adding the robots.txt file) was entirely at archive.org, if I understand correctly, so from the point of view of the NTSB webmaster, you're complaining about some external website he has no control over. I think a useful angle, when discussing this with anyone at the NTSB, would be to discuss how archive.org helps disseminate this information, which is totally within the Obama administration's transparency mandate discussed in that linked document; so if they can help out archive.org by modifying one file, they oughta do it. Comet Tuttle (talk) 22:14, 27 June 2011 (UTC)
- In this case the webmaster does have control. Web.archive.org does not display archived pages on a particular domain if a robots.txt file is on the current domain. The NTSB just recently included a robots.txt file with its new website, so all of the old archives are blocked. If the NTSB modified or removes the robots.txt file, web.archive.org will display the archives again. WhisperToMe (talk) 22:35, 27 June 2011 (UTC)
- Yes, I understand all of that. But the NTSB webmaster doesn't control that behavior over at archive.org. It's not his fault that they behave the way they do. Comet Tuttle (talk) 00:23, 28 June 2011 (UTC)
- In this case the webmaster does have control. Web.archive.org does not display archived pages on a particular domain if a robots.txt file is on the current domain. The NTSB just recently included a robots.txt file with its new website, so all of the old archives are blocked. If the NTSB modified or removes the robots.txt file, web.archive.org will display the archives again. WhisperToMe (talk) 22:35, 27 June 2011 (UTC)
- What I meant was: The impact upon you (of adding the robots.txt file) was entirely at archive.org, if I understand correctly, so from the point of view of the NTSB webmaster, you're complaining about some external website he has no control over. I think a useful angle, when discussing this with anyone at the NTSB, would be to discuss how archive.org helps disseminate this information, which is totally within the Obama administration's transparency mandate discussed in that linked document; so if they can help out archive.org by modifying one file, they oughta do it. Comet Tuttle (talk) 22:14, 27 June 2011 (UTC)
- If information is not available on the NTSB website, you can pleasantly write to the NTSB web administrator and ask them to please provide a link to the content you want. If you are certain that the NTSB is withholding documents from you, you can file a Freedom of Information Act request at http://www.foia.gov/ - and your government representatives will mail, email, fax, or otherwise transmit any documents that they have. FOIA is administered by a separate Federal agency, with the intent that FOIA representatives will not collaborate with any "coverup" by any particular agency. There are certain legal requirements that documents, if they exist, must be delivered in a certain amount of time; but of course, specific documents that don't exist can not be delivered! And you must trust the administrator of your FOIA request is diligently looking for the information you have requested. If, even after a FOIA request, you still feel that the Federal Government is withholding information, you can pursue civil and legal actions, under the advice of an attorney, to sue the Federal Government for access to the information you are requesting; and a judge will decide what the best course of action is. But let's be clear: just because something used to be on the public website does not mean that the Federal Government is required to host it on the internet in perpetuity. Furthermore, just because the Federal Government is legally obligated to provide access to documents does not mean that they must provide access via any particular internet website. Nimur (talk) 22:30, 27 June 2011 (UTC)
- Thank you for letting me know about the FOIA, Nimur. In this case, all of the documents have existed. I'm going to see what the NTSB says when it e-mails me back. Honestly, I would be okay if I got all of the contents from those public dockets, so the contents can be re-published on wikisource and/or the Commons. WhisperToMe (talk) 22:39, 27 June 2011 (UTC)
- Just a correction to what is otherwise correct in Nimur's post: FOIA is not administered by a separate federal agency. It is administered by FOIA divisions within the agencies in question. They are very much "in house," which becomes very clear if you file a lot of them. (In my experience, paradoxically, the more "closed" the agency, the better they are at handling FOIA requests. Give me FBI and CIA processing my requests any day — they know what they're doing. NARA, not so much.) There is FOIA oversight for guidelines, procedures, etc., but they are very much administered by the individual agencies. --Mr.98 (talk) 00:17, 28 June 2011 (UTC)
- My error. "Each federal agency processes its own records in response to FOIA requests." Thanks for the correction. Nimur (talk) 03:32, 28 June 2011 (UTC)
- Just a correction to what is otherwise correct in Nimur's post: FOIA is not administered by a separate federal agency. It is administered by FOIA divisions within the agencies in question. They are very much "in house," which becomes very clear if you file a lot of them. (In my experience, paradoxically, the more "closed" the agency, the better they are at handling FOIA requests. Give me FBI and CIA processing my requests any day — they know what they're doing. NARA, not so much.) There is FOIA oversight for guidelines, procedures, etc., but they are very much administered by the individual agencies. --Mr.98 (talk) 00:17, 28 June 2011 (UTC)
- http://www.amtonline.com/article/article.jsp?siteSection=1&id=8331 says that beginning in 2009 all public dockets should be released to the NTSB website in accordance with the FOIA plan... - I'm checking to see if the older dockets will still be online, though... WhisperToMe (talk) 16:50, 28 June 2011 (UTC)
Guys, http://web.archive.org/web/20070321223455/http://www.ntsb.gov/events/KAL801/ is working now! Robots.txt seems to have been altered to let us see old archives. YES! WhisperToMe (talk) 17:00, 28 June 2011 (UTC)
Swedish IPRED Law - keeping logs mandatory
The law / directive implemented by Sweden named IPRED (or somesuch) prompted several ISPs to start destroying their logs, to prevent the authorities from getting their hands on them. This was a while back. Has this law been changed, or have any new laws been passed, that force ISPs and other service providers to keep logs of all activity? I know of at least 2 (Swedish) VPNs (one of which is the Pirate Bay's webhost) that claim that they don't log anything, so I'm not sure what to make of this. Temptre.22 (talk) 19:11, 27 June 2011 (UTC)
- To the best of my knowledge, and from my reading of , the law has not been changed. It should be noted, however, that
- (...) Rättighetsinnehavare har dock möjlighet att begära att tingsrätten, med stöd av 26 § i lagen (1996:242) om domstolsärenden, förbjuder internetoperatörer att radera informationen, i väntan på att utredningen om ett eventuellt informationsförläggande har slutförts (...)
- Meaning roughly, that a court of law may at its discretion prohibit ISPs from deleting logs after a plaintiff has brought a request for information before it, until the case has concluded, as this could constitute spoliation of evidence. See also WP:IANAL. Regards,
decltype(talk) 07:16, 28 June 2011 (UTC)
firefox
how to backup favorites in firefox 5 ? — Preceding unsigned comment added by Tsp12345 (talk • contribs) 19:46, 27 June 2011 (UTC)
- Ctrl+Shift+B should bring up the bookmarks library, then click "import and backup" AvrillirvA (talk) 20:54, 27 June 2011 (UTC)
- Backing up your profile will get all your prefs and bookmarks and other goodies. To use with a new/different installation, you can just copy the contents into another profile dir (over the existing), or use Firefox's
-ProfileManageroption. ¦ Reisio (talk) 17:51, 28 June 2011 (UTC)
Wikipedia content automatically posted on Facebook
Apparently someone is using a bot to automatically create Facebook pages for Wikipedia articles. E.g this page.
Initially I thought someone had added it manually but I heard that it happens more often. Is it someone who wants to promote Wikipedia who does it or some search engine spammer?
I know it must be some bot because I improved said article a bit a while back and the lead picture changed on Facebook soon after I changed it on WP. SpeakFree (talk) 21:06, 27 June 2011 (UTC)
- I don't use facebook but it looks like they're hosting a mirror of Wikipedia. Wikipedia:Mirrors_and_forks/Def#Facebook has some information. AvrillirvA (talk) 21:15, 27 June 2011 (UTC)
- Well they are welcome to do so as they cite the license and link to the contributors. I guess Zuck & co. do it to generate more traffic to their site. SpeakFree (talk) 21:23, 27 June 2011 (UTC)
- I've been aware of this for sometime, maybe a year - it appears to be fairly systematic.
- Additionally I've noticed that two versions of articles are often created, one truncated article eg http://www.facebook.com/pages/MaK-G1206/110205232364409?sk=info and one full article eg http://www.facebook.com/pages/MaK-G1206/110205232364409?sk=wiki
- It's not clear if this is a facebook official effort, or if someone is using a bot. OR WHY ??83.100.186.201 (talk) 21:26, 27 June 2011 (UTC)
- If you look at a Facebook page that has a Wikipedia article, in my experience you'll see that there's not much else there. It's probably done so that these pages actually have some content. Wabbott9 (talk) 15:22, 28 June 2011 (UTC)
The only thing which is a bit iffy in a legal way is their use of images from Wikimedia Commons without citing the creators per the CC licence. But I guess they don't care, there must be millions of copyright infringing images on Facebook. SpeakFree (talk) 21:33, 27 June 2011 (UTC)
- Edit: If you click on the image on the page it takes you to the Wikimedia Commons page. Don't know if that's enough though for citing the creators. SpeakFree (talk) 18:29, 28 June 2011 (UTC)
Transferring DVDs to computer
My dad recently got our old home videos transferred from the original cassettes onto DVD. Now I want to put those files onto Windows Movie Maker to edit out all the boring junk like dance recitals and keep all the cute and funny stuff. But Movie Maker doesn't recognize that there's anything on the disc, and Windows Media Player doesn't recognize there's anything to rip. When I play the DVD on PowerDVD it works fine, but when I try to play on Media Player there's no sound... What can I do to be able to import these videos into Movie Maker? If it makes a difference, when I open up the DVD drive in Windows Explore, it shows the files on the DVD as having VOB, IFO, and BUP file extensions. I've never heard of those before. (When replying, please bear in mind that I have a good working knowledge of computers, but no clue about technical stuff. So when in doubt, dumb it down! :) Thanks.) Cherry Red Toenails (talk) 21:31, 27 June 2011 (UTC)
- I don't think Windows Movie Maker understands VOB files, so you will need to convert them into a format which it does understand. Windows Movie Maker#Importing footage lists the formats it will understand. You can use free programs like Handbrake, MEncode, AutoGK or Avidemux to convert them into a suitable format, probably .avi would be best. Here's a guide for converting with Avidemux. In addition, Avidemux offers limited editing capability so depending on how complex the task is that might be good enough AvrillirvA (talk) 21:49, 27 June 2011 (UTC)
- The VOB, BUP, and IFO files are the normal format for commercial movie DVDs (not Blu-Ray). Note that there may be region codes with this format which only allow them to (legally) played in certain geographic areas. There is a lot of software out there to rip those, but the one I use is Linux, so I'll let others make suggestions for Windows. StuRat (talk) 22:03, 27 June 2011 (UTC)
- Of the software suggested by AvrillirvA, the easiest to use is probably Handbrake. It's super easy to turn DVD files into AVI files. --Mr.98 (talk) 23:16, 27 June 2011 (UTC)
- I tried Handbrake, but could only get it to make m4v files (which Movie Maker still doesn't recognize). How do I get it to convert to avi? Cherry Red Toenails (talk) 05:34, 28 June 2011 (UTC)
- I just checked and .avi support was removed in version 0.9.4, sorry. Version 0.9.3 is available here AvrillirvA (talk) 09:33, 28 June 2011 (UTC)
- I tried Handbrake, but could only get it to make m4v files (which Movie Maker still doesn't recognize). How do I get it to convert to avi? Cherry Red Toenails (talk) 05:34, 28 June 2011 (UTC)
- Thanks AvrillirvA! I got it as an avi file now. My new problem is that Movie Maker recognizes it as an audio track, not video. And even when I put it in the audio line, there's still no audio. Just a silent black screen... If anybody knows how to fix that, I'd sure appreciate it :) Cherry Red Toenails (talk) 19:07, 28 June 2011 (UTC)
- I take it back--I do have audio. But still no video. Cherry Red Toenails (talk) 19:08, 28 June 2011 (UTC)
It has been ages since I last used Movie Maker (back on my old Windows ME edition!) but I always got the impression that Microsoft made it as difficult as possible to import anything other than Windows Media Video, so that customers were forced into using that proprietary video format. 213.102.128.195 (talk) 22:17, 28 June 2011 (UTC)
June 28
Computing clouds
It appears that all of the commercially available cloud computers like Amazon's and Microsoft's, etc. are devoted mostly to files and data movement rather than to processing. Is there such a thing as a processor cloud that offers enormous numbers of processors as opposed to file space and data manipulation? I'm referring to processors capable of performing distributed functions and/or subroutines which for example might count duplicates in a generated list of numbers and then return a sum of squares such that the amount of stored data is to small to be an issue whereas the generated numbers might grow exponentially and take a long, long time to process. --DeeperQA (talk) 00:24, 28 June 2011 (UTC)
- Probably not, as storage is cheap. Also, for most problems that need parallel computing, a lot of storage space is needed. The example you give doesn't need a lot of space, but it doesn't need a lot of time, either: counting duplicates and summing squares should be doable in around time (depending on implementation). Algorithm sketch: walk the list, putting each member into a search tree (a hash table would usually work fine, too), noticing collisions. You'd probably need to use bignums, but the overhead in this case should be logarithmic, which is cheap. It should be possible to process a list with a few billion elements in not much more time than it takes to read it off the disk in the first place. I suspect that most algorithms that parallelize well need to have large data sets, so you can break them up in the first place. (The DPLL algorithm, for example, takes exponential time, and doesn't use much space, but I don't think it's very fruitful to try to parallelize it.) Paul (Stansifer) 01:03, 28 June 2011 (UTC)
- See distributed computing; for lots of existing projects, see Category:Distributed computing projects. Two famous examples are SETI@Home and Folding@Home. --Mr.98 (talk) 02:39, 28 June 2011 (UTC)
- It sounds like you are saying that a cloud acts just like a single computer only with a much larger capacity that can handle enormous values and do so very fast, which is the point of splitting an algorithm into pieces so they can relieve a single computer of the need to have such great capacity and in need of dissembling the algorithm in the first place and reassembling the results from each making the use of more than one computer unnecessary.
- In fact the algorithm I'm working with is designed to only begin splitting tasks when the values exceed single computer memory and speed limitations which necessitates processing in pieces distributed among the servers.
- If the cloud did begin to slow down is there a way to assign pieces of the task to another cloud in the same manner as a Beowulf Cluster client sending pieces to the servers? --DeeperQA (talk) 09:39, 28 June 2011 (UTC)
- A collection of computers is not just one big computer. A cloud environment is not a way to get a larger address space or word size or (usually) more memory. Sometimes (in fact, most of the time), getting "the cloud" involved is not the fastest solution, since a single computer will have come up with the answer by the time that you've finished farming out the initial input data to the cloud that you're using...
- If the cloud did begin to slow down is there a way to assign pieces of the task to another cloud in the same manner as a Beowulf Cluster client sending pieces to the servers? --DeeperQA (talk) 09:39, 28 June 2011 (UTC)
- ...provided that you are using a fast algorithm! If the input is large, the difference between an algorithm with a good big-O and an algorithm with a bad big-O is the difference between getting the answer immediately, and dying of old age before you get the answer. Example: If you come up with a (i.e., exponential) algorithm to solve a problem, there is no supercomputer in existence that can get you the answer for an input of size 300 before the heat death of the universe. But if you change the algorithm to one that takes time (and sometimes this is a small change!), your netbook will spit out an answer for an input of size 300 before you can blink. Change the algorithm to take time, and your netbook will be able to process an input of size 6,000 in in less time. Tweaking algorithms for big-O is far more powerful than just throwing more computer resources at the problem.
- If you don't understand big-O notation, just ask. It's absolutely essential knowledge for any computer scientist, and you can't write fast programs without thinking about it. Paul (Stansifer) 11:46, 28 June 2011 (UTC)
- Yes, I ran into big-O when I was writing the Check Sort routine but have not gotten that deeply back into logic or mathematical programming since.
- I posted the server side code here but withdrew the question. The algorithm is in fact based on the Check Sort in that it counts duplicates the same way by using the values in the list as an array index whose content value is incremented each time an index value is read from the list. If it is the first time for a particular value then the value in the array at the indexed location become one. If it is the 11th time then the stored value becomes 11. Basically: n(x)=n(x)+one where n is the indexed array and x is the value for which duplicates are being counted.
- Doing this in assembler or binary is what I would expect to be the next step to improve speed rather than using a cloud but still staying with a Beowulf when single computer limits would require digging up your bones and reburying with a note that the job had finally completed.. About big-O, I'm all ears, go for it. --DeeperQA (talk) 12:48, 28 June 2011 (UTC)
Ubuntu keyboard restart
Is there a way to restart my keyboard functionality, without restarting Ubuntu? — Preceding unsigned comment added by 88.9.106.0 (talk) 12:57, 28 June 2011 (UTC)
- Not quite sure what you mean. Has your OS stopped responding to your keyboard inputs? --Aspro (talk) 13:15, 28 June 2011 (UTC):
- yes everything Is working except the keyboard88.9.106.0 (talk
- Which version of Ubuntu are you using? --Aspro (talk) 13:32, 28 June 2011 (UTC)
- 8.04, and the problem happens every now and then.. :( — Preceding unsigned comment added by 88.9.106.0 (talk) 13:43, 28 June 2011 (UTC)
- Try ctrl+alt+f3 then type some stuff, then ctrl+alt+f7. That might fix it. -- Finlay McWalter ☻ Talk 13:33, 28 June 2011 (UTC)
- How can I type that, if the keyboard is not working? — Preceding unsigned comment added by 88.9.106.0 (talk) 13:35, 28 June 2011 (UTC)
- Just do it. -- Finlay McWalter ☻ Talk 13:51, 28 June 2011 (UTC)
- Finlay McWalter's suggestion is based on the (pretty good) hunch that something is broken with your X server and/or your desktop-manager. A common problem might be a bug in your X server's HID drivers. By pressing those key sequences, you'll swap out and back in (without restarting X), and hopefully "kick" the server back into normal operation. This doesn't really "fix," as much as "work around," the bug. Let us know if that actually worked; if not, we can try to diagnose other possible causes. Hardware or driver failure in your USB system is the next most probable culprit after your X server, in my opinion. Nimur (talk) 15:53, 28 June 2011 (UTC)
- Time to update to the current LTS version. Although you can't see the keyboard doing anything, it doesn't mean the keyboard can't open a terminal. Hence the suggestion Ctrl + Alt + f3 Also, it helps to check that you have still have sufficient free disc space. Empty trash ect. I think a bad bit of RAM might also cause intermittent faults like this.--Aspro (talk) 14:06, 28 June 2011 (UTC)
- Just do it. -- Finlay McWalter ☻ Talk 13:51, 28 June 2011 (UTC)
- OK, I'll try next time the keyboard gets blocked. And update to the new version of Ubuntu (although I suppose it's a hardware problem). 88.9.106.0 (talk) 14:20, 28 June 2011 (UTC)
- Also, note that if you're completely stuck, you can hold down Alt and Sys Rq (the same key as Print Screen), and then hit S, U, and then B (while still holding Alt-Sys Rq down). This will tell the computer to reboot in a slightly gentler fashion than simply hitting the power button does. (see Magic SysRq key, which also includes a slightly longer and even better sequence of commands) Paul (Stansifer) 16:18, 28 June 2011 (UTC)
- Worth trying
+kfirst. ¦ Reisio (talk) 17:48, 28 June 2011 (UTC)
- Worth trying
Full access to an iPod's file system
Is there anyway that I gain full file system access to a regular iPod be it software on the iPod itself or from my desktop? --Melab±1 ☎ 14:50, 28 June 2011 (UTC)
- Sure. The music is in a hidden folder. On a Windows machine it's a matter of going to "Show hidden folders"; on a Mac it's a little trickier but it can be done. (You can easily access the hidden folders through the Terminal, for example. Getting the Mac OS to show hidden folders involves some Terminal trickery but it can be done.) --Mr.98 (talk) 15:00, 28 June 2011 (UTC)
- You have full access to the file system. However, you might not be familiar with the type of file-system on your iPod: see How to determine your iPod's disk format from Apple's support page. If your iPod is formatted with HFS+, you may need to use the extended file attributes commands and utilities. You can read about these tools, in the public developer documentation, at listxattr on the Mac OS X Developer library. The xattr utility program is very helpful. Bear in mind that even though the iPod can register itself as a USB mass-storage device class when connected over USB, your iPod is a full-featured small computer, not a hard-disk-on-a-stick; so if you're trying to access its file-system, you should be aware that its operating system is on and in control of the storage-medium at all times, even when it is mounted as a USB "disk." Nimur (talk) 15:41, 28 June 2011 (UTC)
- If I had full filesystem access I would think that I could see the kernel, plists, etc. --Melab±1 ☎ 20:32, 28 June 2011 (UTC)
- You want access to the iPod firmware? That is kept in a read-only area. You can hack it (Google "hack iPod firmware" — this howstuffworks page gives a nice overview) but it's not a straightforward thing, because the iPod is not a straightforward computer. --Mr.98 (talk) 21:07, 28 June 2011 (UTC)
- If it is updated then it is not read-only. --Melab±1 ☎ 22:49, 28 June 2011 (UTC)
'Run As Admin' Option Not Appearing
I've been grinning and bearing this for a couple of weeks, but now it's just beginning to annoy me. I am finding that with some programs, the 'Run As Admin' option is not even present in the context menu - it used to be there for practically every executable, as far as I can remember. Sometimes, if I make a shortcut for these programs where the option has disappeared, the option now actually is present in the shortcut, but not in the original. Anyway, this is not normal. I should have the 'Run As Admin' option present in all executables (except one or two exceptions, which are beyond the scope of this question). In these same executables where this option is not present, they also lack the 'Properties' option, meaning I can't do anything from that dialogue box. Can anyone guess what has happened and how can I fix this? - EDIT - My UAC is turned on. Win Vista, Home Premium, 32 Bit. --KägeTorä - (影虎) (TALK) 15:43, 28 June 2011 (UTC)
what format are rackspace cloud images in?
I took a server image (maybe "snapshot"), it's just lilsted as (name I gave it)cloudserver(numbers).tar.gz.0 at about 2 GB and another 171 byte file called (name I gave it)cloudserver(same numbers as above).yml - what format would these two files be in? Could I download them and run them in a VM on my desktop, if so which one? Thanks. --188.28.242.234 (talk) 21:00, 28 June 2011 (UTC)
- answering own question... apparently http://communities.vmware.com/thread/312288?tstart=0 says: " Rackspace solution seems to be based on XEN servers. So you should be able to extract VM's files from the tar archive and use VMware Converter to import it to your ESXi." --188.28.242.234 (talk) 21:26, 28 June 2011 (UTC)
How do you get a PDF to work on Word 2010?
Please help, every time i try to open a pdf with Word 2010 it says it is not a valid Win32 application. — Preceding unsigned comment added by 98.71.62.95 (talk) 21:36, 28 June 2011 (UTC)
- MS Office applications like Word can't open .pdf files, even though they are able to create them. You should use a .pdf reader, like Adobe Acrobat Reader or Foxit or suchlike. --KägeTorä - (影虎) (TALK) 22:42, 28 June 2011 (UTC)
PHP MyAdmin help
When i try to export a database, i get it PARTLY, never mind if it's ZIPPED\GZIPPED or a single file, it's always partly, but always 25% partly, it's seems the exportation stops before it really ended the procedure.., and it's always stops in the same point... it's more than a week like that, so annoying!!.. thanks, Beni.




